Practical Network Penetration Tester (PNPT)
 Evan Ottinger
Evan Ottinger
I recently had the pleasure of taking TCM Security's Practical Network Penetration Tester (PNPT) exam. Since PNPT is the new kid on the block, change is scary, and a relatively small number of folks have had the opportunity to take (let alone complete) PNPT, I wanted to make my thoughts available for interested parties.
Full-Disclosure: I am a participant in the TCM Academy Partner Program . I will receive a 25% commission from sales generated using the affiliate links in this post.
My Background
For the sake of transparency, I want to share my background going into the exam. I have a B.S. in Computer Information Systems. My degree incorporated a double concentration in Systems Development and Information Assurance and Security. I also hold an upper-division undergraduate certificate in Applied Cybersecurity from the SANS Institute. The red team certifications that I've completed before PNPT are Pentest+, eJPT, and GPEN. Professionally, I've been a software developer for just under two years, most recently at a full-spectrum cybersecurity company.
I consider myself to be an early-career software developer, as that's what pays my bills. That aside, I am an offensive security enthusiast. As it's related to information technology, if I'm not studying and practicing software development, I'm sharpening my red team skills.
Edit 8/10/2022: I am currently employed at TCM Security as a Senior Security Engineer. I began working here in April of 2022. I completed the PNPT exam in December of 2021, before beginning my work on the new exam platform.
Edit 10/11/2024: I am no longer employed with TCM Security as of August 2024.
Why Take PNPT?
I opted to take PNPT for a few reasons:
The exam is 100% practical--I've never personally been on a penetration test and wanted to gain hands-on experience if I ever am asked to cover down on an engagement.
PNPT rapidly appears on job listings.
I'm a fan of TCM Security's mission of making education affordable and wanted to support them.
It's affordable. Especially compared to most certifications available in the industry.
Preparing for the PNPT
Edit 8/18/2023: TCM Security's Academy adopted a subscription model in July of this year. For $29.99 a month, students gain access to the entire library of courses available. Access to courses purchased before the subscription model remains unchanged.
Per the recommendations of TCM Security, I prepared for the exam by completing the following courses:
I initially took Practical Ethical Hacking (PEH) on Udemy roughly a year ago. Since then, Heath Adams (CEO of TCM Security) revamped the mid-course capstone and updated much of the course material. As a result, I opted to refresh myself on the new course material.
Edit 8/10/2022: Since I took the PNPT, the preparation roadmap for the exam has been updated to include the Windows Privilege Escalation for Beginners and Linux Privilege Escalation for Beginners courses. See the infographic below.
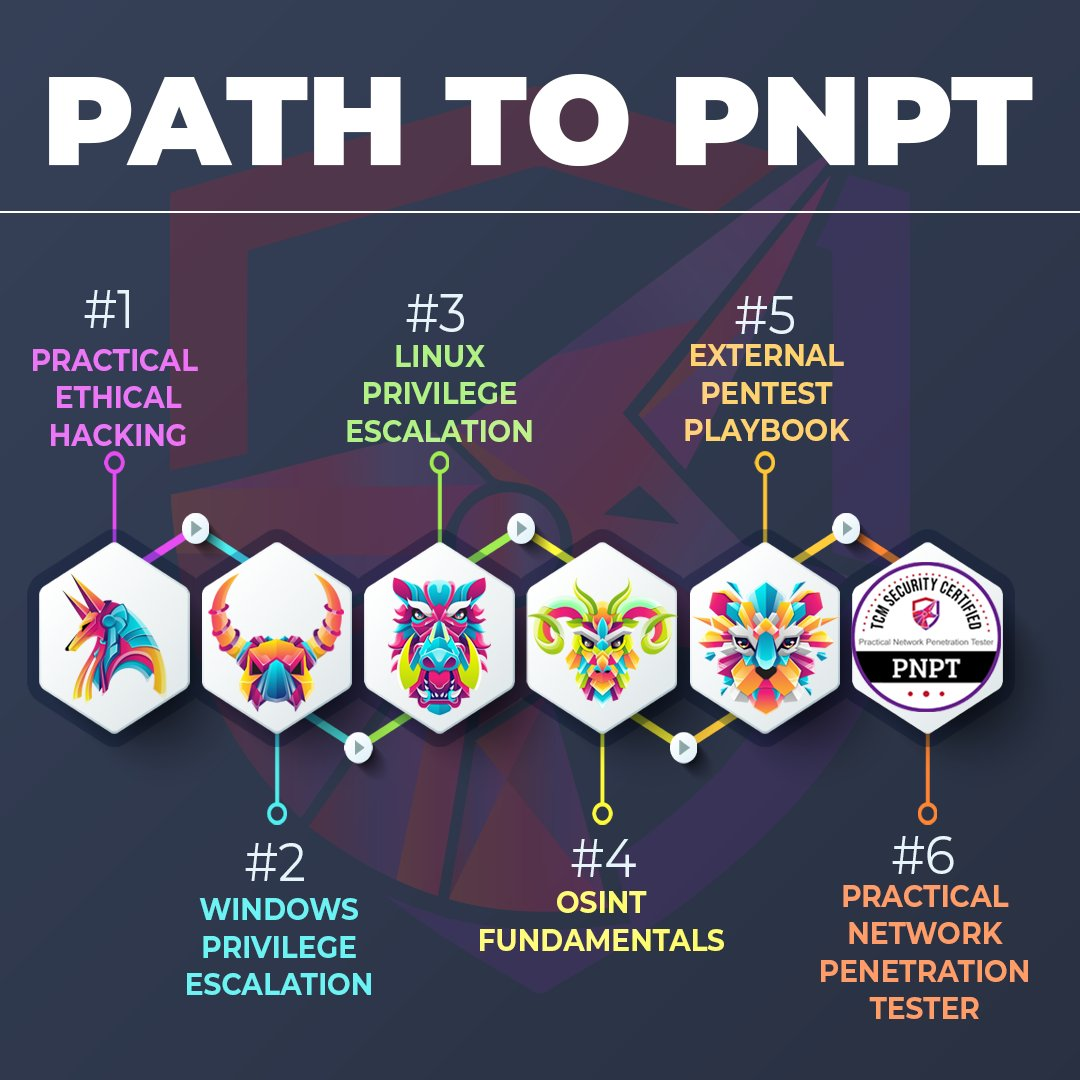
The Exam Experience
All PNPT candidates are obligated to keep information about the exam confidential. As such, I can't discuss specifics outside of what is publicly available on TCM Security's website.
That aside, I found the experience notable compared to other industry standard exams. Students are provided an individual (read: non-shared) network environment. They are given five days to complete a penetration test within the scope defined in the rules of engagement. The goal is to 1) compromise the domain controller (DC) and 2) achieve persistent access to the DC.
The student is allotted five days in the environment and two more days to complete a professional penetration test report. Students who do not achieve domain admin can submit a report with their progress and receive a hint for their retake. Once the DC is compromised and the report is submitted and approved, the student has to debrief a panel of senior penetration testers from TCM Security on their methodology and findings. Students who satisfactorily complete all of these requirements are awarded the PNPT certification.
Aspects of the exam that stood out to me:
It is definitively a penetration test in a simulated environment based on real-world penetration tests. There is no multiple choice, and it is not a CTF.
Support was responsive and helpful. Per the student's request, the environment could be reset quickly as needed.
There was no proctor requirement.
All tools, techniques, and procedures were fair game. The only limitation was that the student was expected to complete the exam without outside assistance.
At the time of this writing, and GPEN aside, this is the only junior-level penetration tester certification exam I've taken that includes Active Directory components.
I never once experienced any service interruptions with the exam environment.
In sum, it does exactly what it says on the can.
The Retake Policy
TCM Security's retake policy is particularly interesting. TCM Security offers a free retake with a voucher. For complete transparency, I failed PNPT on my first attempt. Per the retake policy, I could submit a report with my current progress in exchange for a nudge and a second attempt.
Herein lies my only gripe with the PNPT experience--the nudge I was given did not matter as my retake environment differed from my original environment.
Unfortunately, this is unavoidable as folks have attempted to grift off the no-proctor policy and sell exam secrets. This has required TCM Security to abandon compromised environments. As such, a student will unlikely see the same environment on a retake.
The Report
The report is an oft-dreaded component of penetration tests, but I didn't find it too cumbersome. I attribute this mainly to the advice given by Tim Medin in SEC560 at SANS--work on your report while you're testing. On my second attempt, I knocked over the DC by day three and finished my report before the time in the environment expired. This was due in no small part to my note-taking and screenshotting throughout the exam.
PEH outlines the expectations of a professional penetration test report, and Heath makes a template available in a repository on his Github. I highly recommend taking advantage of these resources.
There's also an External Penetration Test checklist available on Heath's GitHub. I found it helpful during my initial approach to the environment.
The Debrief
For the debrief, I spoke with Heath directly. He asked me to walk him through the attack chain and explain the recommended mitigations. The process took about ten minutes, and he immediately released the certificate to me at the end of the call.
Conclusion
In conclusion, I recommend PNPT. Of all of the other entry-level penetration testing certifications out there, this is the only one that requires you to complete a penetration test, write a report, and present your findings--just like in a real penetration test.
Beyond that, the price is unbeatable. The standalone exam is $299, while the bundle with training is $399. The only more affordable option is the eLearnSecurity eJPT--$200 for the voucher and free training with the INE Starter Pass (and includes a free retake). The next most affordable option is CompTIA PenTest+ at $349 without training--and the exam is little more than hacker trivia.
The one major drawback to PNPT is that it is new. Because of this, the current job listings are sparse (7 listings on LinkedIn as of the time of this writing). That said, the fact that it has any listings within the year of its debut is rather promising (considering that eJPT only has 11 listings and has been around for years). As it gains a foothold in the industry, I would expect to see the recognition and demand grow.
Edited 12/28/2021: This post originally stated that TCM Academy was the only education company in the industry to provide a free retake with an exam voucher. This is incorrect. eLearnSecurity also provides a free retake with the eJPT voucher.
Edit 12/4/2022: Grammar. Added affiliate link to purchase PNPT.
Subscribe to my newsletter
Read articles from Evan Ottinger directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Evan Ottinger
Evan Ottinger
As an experienced cybersecurity professional with a full-stack development and software engineering background, I am committed to building secure and reliable software solutions. I am passionate about leveraging my expertise in Python, React.js, Django, and other technologies to design and develop cutting-edge applications that meet the highest security and functionality standards.