Security in Crypto, Hardware Wallets and Pseudonymity - Part 6/7
 MetaversityOne
MetaversityOne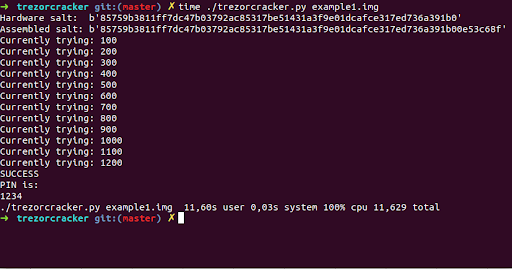
In Part 6 we will contrast and compare Ledger Nano X and Trezor Model T, and look at the security vulnerabilities that have been exploited in them in the past.
The most popular top-of-the-line hardware wallets are Ledger Nano X and Trezor Model T [1]. Ledger and Trezor both have models that are a bit cheaper than their top-of-the-line models.
Ledger Nano X
Ledger Nano X stores the private key on an encrypted chip, and this chip is custom built for doing this task. The firmware of this secure chip is not public, and is under NDA between Ledger and their manufacturer. But Ledger claims that the rest of the Nano X device design is public. It comes with a companion software called Ledger Live, that must be installed on a desktop/laptop computer to update the firmware of your hardware wallet. Since this is an ultra-critical step, you must take great care to go to the correct website and download the legitimate version of Ledger Live [2,3]: https://www.ledger.com/ledger-live
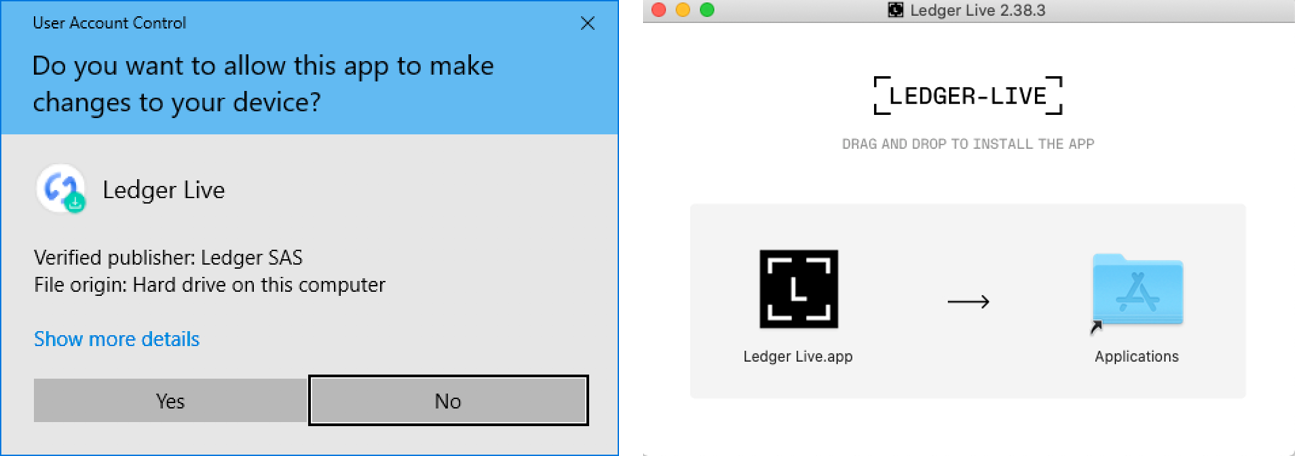 Great care needs to be taken to install the legitimate version of Ledger Live [4]
Great care needs to be taken to install the legitimate version of Ledger Live [4]
Ledger Live will allow you to install utility apps corresponding to each blockchain for which you wish to create a wallet – an app for Bitcoin, one for Ethereum, one for Cardano, and so on. If you purchase the Ledger Nano S, which is ~$80 cheaper than the Ledger Nano X, you will have little space on your device, and it will only support 3-5 blockchain wallets at any one time. If you are a power user, it is better to pay extra and purchase a Ledger Nano X. Ledger Nano X comes with both USB and Bluetooth connectivity. Apple devices like iPad/iPhones forbid USB connections, and you must use Bluetooth to connect. Windows Desktops and Laptops will ask you to use the wired USB and cause problems with Bluetooth. Ledger Nano S only has USB support and no Bluetooth support – thus if you need to use the Ledger with both Apple and Windows, it rules out the Ledger Nano S [5]. (N.B.: Ledger Nano S Plus is a new device that improves memory on the Nano S. From a security standpoint it is better to avoid this device for now as it is just a few months old, and could have unknown vulnerabilities.)
Trezor Model T
Trezor does not use a specific encryption chip to store the private key/user PIN. It uses a general-purpose STMicroelectronics microcontroller to use a portion of its non-volatile memory (NVM) to store the user PIN. Though Trezor has several additional features like Shamir Key Splitting (a.k.a Shamir Backup) and Multi-sig features [6,7] – features that Ledger doesn’t have, I discovered a startling fact.
The Kraken Security Lab was able to find a serious vulnerability in Trezor Model T and Model One. The chip used in Trezor Model T is not a chip specifically made to encrypt data. It is a general purpose microcontroller with several dozen features, one among which include on board NVM memory (a.k.a. Flash memory, as used in pen drives). Kraken Security Lab were able to override the normal boot sequence by doing something called Fault Injection, by applying very high voltages. This disrupted the NVM read, and made it possible to snoop into the NVM contents by repeated brute force fault injection attacks. They were able to read out the user-defined PIN out of the device, in as little as 15 minutes of physical contact with the device. Since this PIN is what encrypts the seed phrase of the wallets restored on the hardware wallet, once they had the PIN, they were effectively able to access the wallets as well, thereby gaining full access to the wallets.
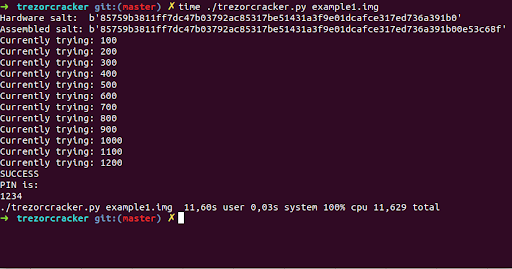 Kraken Security using fault injection based brute forcing to extract a 4 digit PIN on Trezor [8]
Kraken Security using fault injection based brute forcing to extract a 4 digit PIN on Trezor [8]
This is an unacceptable design flaw, and cannot be fixed unless Trezor does a complete redesign of the device. Trezor for their part claims that the solution of this problem is to have the customer set a 25th word, in addition to the 24 word seed phrase. This is called the pass phrase. Since this 25th word is not stored on the Trezor Model T, the company claims that wallets used by using this 25th word are safe – since they cannot be brute forced out of the device, as the 25th word is not present in the first place. You can read more about the Trezor Model T hack here [8]: https://blog.kraken.com/post/3662/kraken-identifies-critical-flaw-in-trezor-hardware-wallets/
I encourage the reader to definitely do their own research. And to find their own acceptable trade-offs. However should you choose the Trezor Model T, you must use a 15+ character long alphanumeric passphrase (i.e. 25th word) - since the seed phrase is rendered moot [9]. Similar to Ledger Live, ensure that you are careful in obtaining legitimate Trezor Suite software [10]: https://suite.trezor.io/
For Ledger’s part, while the Ledger Nano X device has not been known to be hacked thus far; Ledger did suffer a data breach and customer data was stolen from their e-commerce partner Shopify in July 2020. This is the official Ledger response on the data hack and leak online [11]: https://www.ledger.com/message-ledgers-ceo-data-leak
Stolen customer data was used to target customers who had purchased Ledger devices [12,13], we need to prepare for the case that this can happen again. Unfortunately, this type of customer information database hack was repeated with Trezor’s email solution provider MailChimp between Feb-April 2022 [14,15]. Thus try as far as possible to remove personally identifying information while ordering your Ledger/Trezor. We cannot guarantee this will be enough, but it should be mostly sufficient from being targeted in the future. This means:
- Use a burner email address with no real name and no profile picture.
- Use a delivery address that is not your residence. Maybe it could be a PO Box, or an office address, or a temporary address or a shop’s address.
- Don’t provide your mobile phone number.
- Try paying for the wallet purchase using cryptocurrencies/avoid credit or debit cards.
One final idea for this section is to order Hardware wallets in multiples of 2 (or maybe 3 for power users). This will ensure that any hardware or firmware issues taking one device down, can be immediately replaced by a backup physical device on which the seed phrase can be used to restore the required wallets.
Next: In Part 7 we will discuss the steps on how to properly use a hardware wallet.
References:
- Jenkins, M. (2021). 5 BEST Crypto Wallets in 2022! Top Hardware Wallets! [online] Coin Bureau. Available at: https://www.coinbureau.com/analysis/best-hardware-wallets/ [Accessed 3 Jul. 2022].
- CryptoSec (2020). 6 Ledger Wallet Scams That You Should Know About. [online] CryptoSec. Available at: https://cryptosec.info/ledger-scams/ [Accessed 3 Jul. 2022].
- Ledger (2022). Ongoing phishing campaigns. [online] Ledger. Available at: https://www.ledger.com/phishing-campaigns-status [Accessed 3 Jul. 2022].
- Ledger Support (2022). Download And Install Ledger Live. [online] support.ledger.com. Available at: https://support.ledger.com/hc/en-us/articles/4404389606417-Download-and-install-Ledger-Live [Accessed 3 Jul. 2022].
- Gedeon, K. (2022). Ledger Nano S vs. X: Which crypto hardware wallet is best for you? [online] LaptopMag. Available at: https://www.laptopmag.com/au/features/ledger-nano-s-vs-x [Accessed 3 Jul. 2022].
- Satoshi Labs (Trezor.io) (2021). Multisig and split backups: two ways to make your bitcoin more secure. [online] Trezor.io. Available at: https://blog.trezor.io/multisig-and-split-backups-two-ways-to-make-your-bitcoin-more-secure-7174ba78ce45 [Accessed 3 Jul. 2022].
- Costea, V. (2021). 4 Step Shamir Backup Guide on Trezor Model T. [online] privacypros.io. Available at: https://privacypros.io/trezor/shamir-backup/ [Accessed 3 Jul. 2022].
- Kraken Security Labs (2020). Kraken Identifies Critical Flaw in Trezor Hardware Wallets. [online] Kraken Blog. Available at: https://blog.kraken.com/post/3662/kraken-identifies-critical-flaw-in-trezor-hardware-wallets/ [Accessed 3 Jul. 2022].
- Trezor.io (n.d.). Passphrase. [online] Trezor Wiki. Available at: https://wiki.trezor.io/Passphrase [Accessed 3 Jul. 2022].
- Trezor.io (2022). Trezor Suite - Managing crypto just got safer and easier. [online] Trezor.io. Available at: https://suite.trezor.io/ [Accessed 4 Jul. 2022].
- Gauthier, P. (2020). Message by LEDGER’s CEO - Update on the July data breach. Despite the leak, your crypto assets are safe. [online] Ledger. Available at: https://www.ledger.com/message-ledgers-ceo-data-leak [Accessed 3 Jul. 2022].
- Namcios Bitcoin Magazine (2021). Inside The Scam: Victims Of Ledger Hack Are Receiving Fake Hardware Wallets. [online] Nasdaq.com. Available at: https://www.nasdaq.com/articles/inside-the-scam%3A-victims-of-ledger-hack-are-receiving-fake-hardware-wallets-2021-06-17 [Accessed 3 Jul. 2022].
- Abrams, L. (2021). Criminals are mailing altered Ledger devices to steal cryptocurrency. [online] BleepingComputer. Available at: https://www.bleepingcomputer.com/news/cryptocurrency/criminals-are-mailing-altered-ledger-devices-to-steal-cryptocurrency/ [Accessed 3 Jul. 2022].
- Satoshi Labs (trezor.io) (2022). Details of the Mailchimp data breach. [online] Trezor.io. Available at: https://blog.trezor.io/details-of-the-mailchimp-data-breach-a06872caa1fd [Accessed 3 Jul. 2022].
- Coin Bureau News Desk (2022). Trezor Warns Customers of Phishing Scam After MailChimp Gets Hacked. [online] Coin Bureau. Available at: https://www.coinbureau.com/news/trezor-warns-customers-of-phishing-scam-after-mailchimp-gets-hacked/ [Accessed 3 Jul. 2022].
The author holds a M.S. in Engineering from Columbia University, and has a decade of research and industry experience in software and hardware design. He has been researching crypto security since early 2021. He can be followed on Twitter: @MetaversityOne and also his Hashnode Blog: https://cryptosecurity.hashnode.dev/
Subscribe to my newsletter
Read articles from MetaversityOne directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by