Alpha Recon: The solution to security risk management
 Maxwell Onyeka
Maxwell Onyeka
Enterprise Security Risk Management (ESRM) is a strategic approach to security management that uses widely acknowledged risk management principles to link an organization's security practice to its overall strategy. With a focus on protective measures that aid in the organization's ability to achieve its overall mission, the goal of ESRM is to discover, assess, and reduce the potential and/or impact of security threats to the organization. With the aid of ESRM, security professionals can serve as asset owners' trusted advisors while they make decisions on security risk management.
The organization's overall strategy, including its goal and vision, fundamental values, operating environment, and stakeholders, should continue to be understood by security experts, according to ESRM. Security professionals will be better able to assist and align with the organization's strategic goals if they are aware of this background.
What Drives the ESRM?
ESRM is a collaboration:
Although business leaders are ultimately responsible for all final security decisions, ESRM acknowledges that security duties are shared by both security and business leadership. With the organization's leaders in charge of such assets, the security leader's job in an ESRM is to manage security vulnerabilities to enterprise assets in a risk-decision-making collaboration.
ESRM is comprehensive and open to all.
A mature ESRM program covers all aspects of security risk mitigation methods in order to reduce the company's security risk repercussions.Value exists as a result of the company owning the security risk. As a result, we are now offering business deliverables.
Participation is mandatory.
Educating business partners on their risk exposures is a requirement for managing the security decision-making process. presenting potential security measures to safeguard resources Putting the choice of the business leader into practice preserving a record of the ongoing danger and educating your business partners.
The ESRM cycle is based on the new ESRM guidelines from ASIS1, which were created based on internationally recognized and accepted risk management principles. These principles are implemented by locating, assessing, and reducing security risk areas within an organization in order to achieve business objectives. An organization's security process can become more mature by engaging in ESRM practice. Once the context of an enterprise is understood, this cycle can be started. Understanding the context entails being aware of the stakeholders, operating environment (physical, nonphysical, and logical), mission, vision, and fundamental values. This aids security experts in locating risk areas that prevent the organization from attaining its aims and goals. There are four processes in the ESRM cycle:
I. Identifying and ranking assets: An asset is something that adds value to the organization. Asset owners are in charge of reducing risk areas on their possessions to an acceptable level for the firm. Based on the goals and objectives of the company, assets should be appraised and prioritized. The asset's value may be determined by its purchase price, its replacement cost, or the operational and reputational consequences of its unavailability.
II. Identifying and prioritizing risk entails carrying out an asset risk assessment by selecting potential threats using the enterprise risk assessment methodology. Determine the risk level using the following criteria: threats, vulnerabilities, impact, probability, and asset value. The risk level for the identified risk is determined, and the acceptable risk value is matched. High-risk zones are those where the risk exceeds the acceptable value, while low- or acceptable-risk areas are those where the risk matches or falls below the acceptable value. Prioritizing risk is the process of locating high-risk areas and ranking them for mitigation.
III. Diminishing the Priority Risk: High-risk controls must be lowered to a level that is acceptable. Risk mitigation is the method involved in this. One form of risk management is risk minimization; the other three are acceptance, avoidance, and transfer. According to an organization's risk appetite and tolerance level, risk scenarios are approved in risk acceptance. Insurance and outsourcing can be used to transfer risk. By altering or stopping some procedures, risk can be avoided. In risk mitigation, more controls are added to lower the probability or impact of risk until it is at an acceptable level. Electronic access restrictions, video monitoring, security awareness training, and data loss prevention (DLP) are a few examples of risk mitigation techniques.
IV. Continuous improvement of the security program: The ESRM cycle is based on an iterative strategy of assessment, mitigation, and monitoring to continuously enhance the four processes. This leads to an improvement in the security program. Continuous improvement is aided by investigations, analysis, information sharing, and event response. The process of responding to incidents and following them up until they are resolved in accordance with established timetables is known as "incident response." By documenting issues throughout time and comparing the occurrences that happened and the time it took for them to be resolved with the previous cycle, continuous improvement can be examined. Lessons learned from incidents ought to be included in the security program's procedure for ongoing improvement.
Emerging risks can be determined through investigation and analysis. In this process, root causes are identified, mitigation controls are devised and prioritized and response time is monitored.
A COMPANY CAN IMPROVE THE MATURITY OF ITS SECURITY PROCESS WITH ESRM.
The method of continuous improvement includes distributing security information to stakeholders and asset owners. This facilitates communication between security professionals and asset owners and supports ongoing improvement.
Physical security, cybersecurity, information security, loss prevention, organizational resilience, brand protection, travel risk, supply chain security, business continuity, crisis management, threat management, fraud risk management, and workplace violence prevention are all topics covered by ESRM.
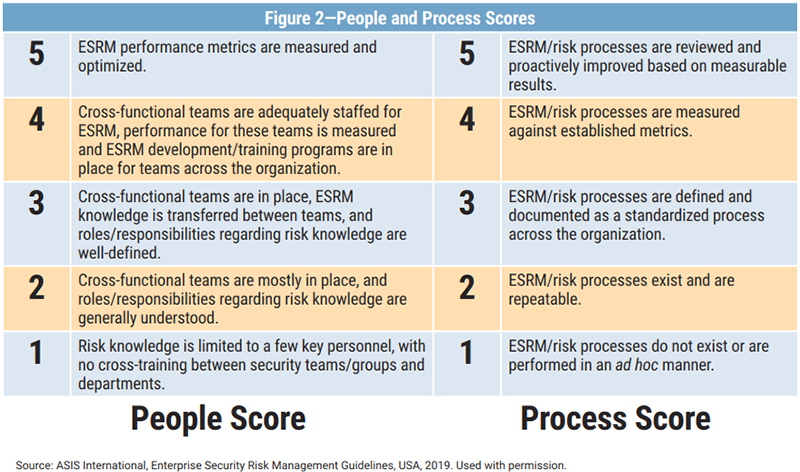
The ASIS ESRM maturity assessment tool, which rates multiple categories based on the present people, process, and governance scores, can be used to assess the readiness of an organization's ESRM program. The current people and process scores are shown in figure (1).
Subscribe to my newsletter
Read articles from Maxwell Onyeka directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Maxwell Onyeka
Maxwell Onyeka
Technical Writing || Web3 || Marketing