Nmap Network Scanner
 Varkey Thomas
Varkey Thomas
Introduction:
The Nmap scanner is a powerful open-source port scanner that is used for network discovery and security auditing.It is mainly used for reconnaissance and footprinting in order to gather information about a target. While it is originally designed to scan large networks rapidly, it works as well for single host systems.
Process of scanning:
In order to scan hosts in a network, it uses raw ip packets to determine various information about the hosts including:
- The hosts available on the network
- The Services (app name & version) that the hosts are running
- The Operating System
- Types of packet filters/firewalls setup on the system, and many more characteristics
Purpose of Nmap:
Nmap has a very diverse set of functionalities that enable it to obtain a variety of information from its scans. With these functionalities, its main purpose is in security audits where it looks for vulnerabilities in networks of a company or organization.
That being its main purpose, it is also used by system and network administrators in order to perform routine tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.
Types of port states:
Before diving into types of port states, a bit of background regarding the TCP handshake. In order to communicate with a TCP service, a 3 way TCP handshake must be established.
This involves a SYN to the TCP open port of the server, which responds with a SYN ACK to the client. Finally the client responds with an ACK.
- Open: This means that applications on the target machine is listening for connections on that port
Filtered: Indicates that a firewall or similar software is blocking the port, rendering nmap incapable of determining the port state.
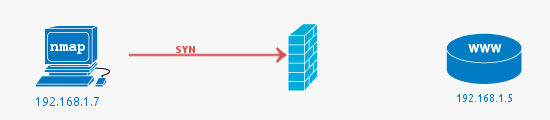
Closed: No application is listening, therefore port could be open.
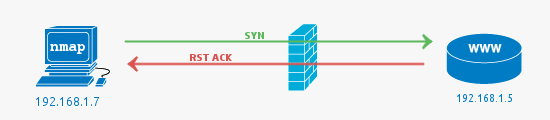
Unfiltered: Nmap gives this classification to ports when it cannot determine the state of the port i.e open or closed
Nmap reports the state combinations open|filtered. and closed|filtered. when it cannot determine which of the two states describe a port.
Types of Flags:
As with any function, in order to use the diverse functionality of Nmap, a number of flags are provided. Using these flags, we can utilize the different functions within Nmap in order to gather information about the target system.
Scanning Techniques:
- -sS - TCP syn port scan
- -sT - TCP connect port scan
- –sU - UDP port scan
- –sA - TCP ack port scan
- -Pn - Port only scan
- -sn - Host only scan
- -PR - arp discovery of local network
Port Specification Scan:
- -p - To specify port range
- -p- - To scan all ports
- -F - Fast port scan
Service version and OS detection:
- -sV - detect the version of services running
- -A - aggressive scan
- -O - detect operating system of the target
Subscribe to my newsletter
Read articles from Varkey Thomas directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
