What Exactly Is End To End Encryption?
 Ronnie Atuhaire
Ronnie Atuhaire
In many messaging systems, including email and many chat networks, messages pass through intermediaries and are stored by a third party, from which they are retrieved by the recipient.
Even if the messages are encrypted, they are only encrypted 'in transit, and are thus accessible by the service provider, regardless of whether server-side disk encryption is used. Server-side disk encryption simply prevents unauthorized users from viewing this information. It does not prevent the company itself from viewing the information, as they have the key and can simply decrypt this data.
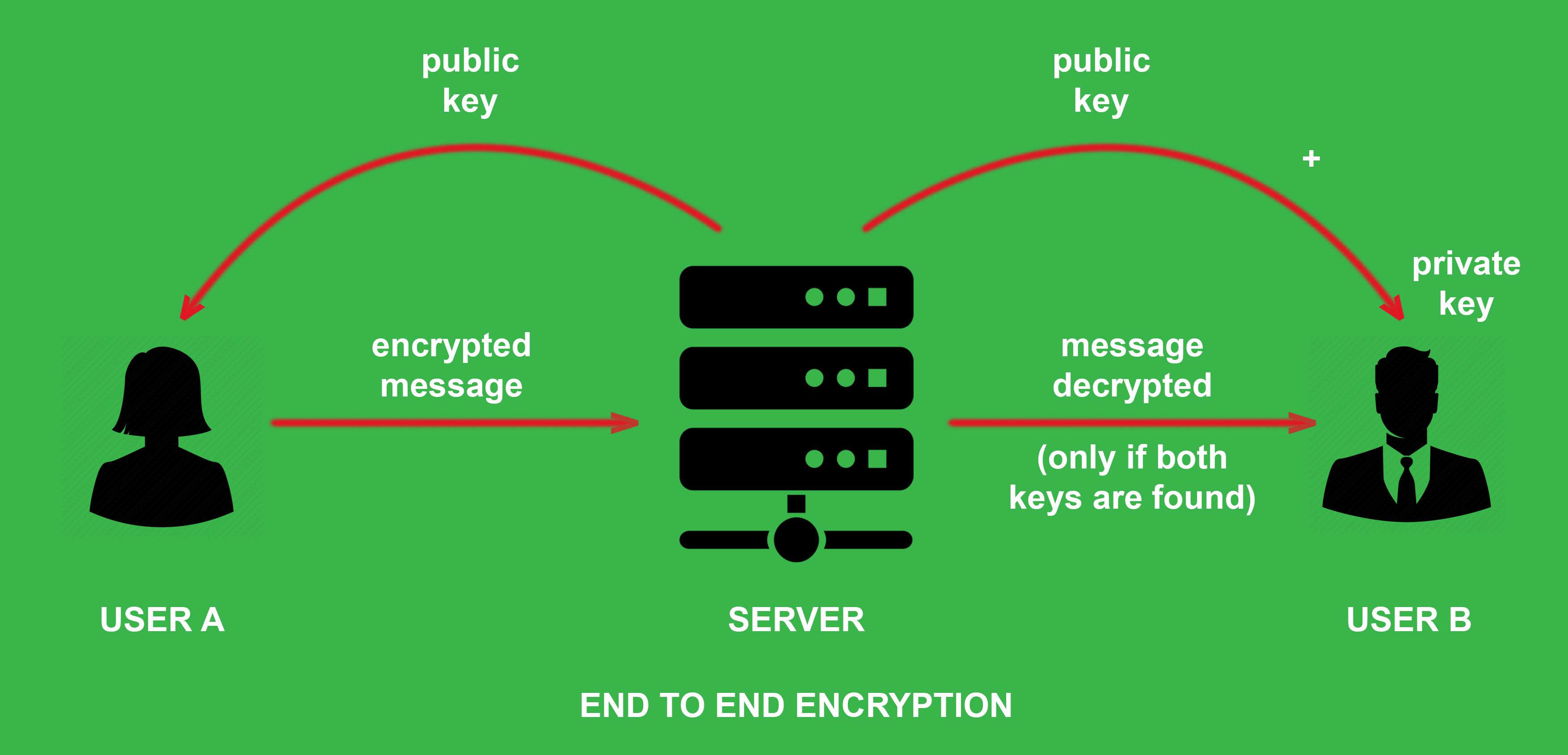
E2EE (End-to-End Encryption) removes the possibility of these service providers, companies and other intermediaries from accessing or reading your data while in transit.
🌟 What is Encryption?
Encryption is the process by which a readable message is converted to an unreadable form to prevent unauthorized parties from reading it.
🌟 What is Decryption?
Decryption is the process of converting an encrypted message back to its original (readable) format.
🌟 Now, What exactly is E2EE?
End-to-end encryption (E2EE) is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system or device to another. In E2EE, the data is encrypted on the sender's system or device, and only the intended recipient can decrypt it.
🌟 An example of E2EE
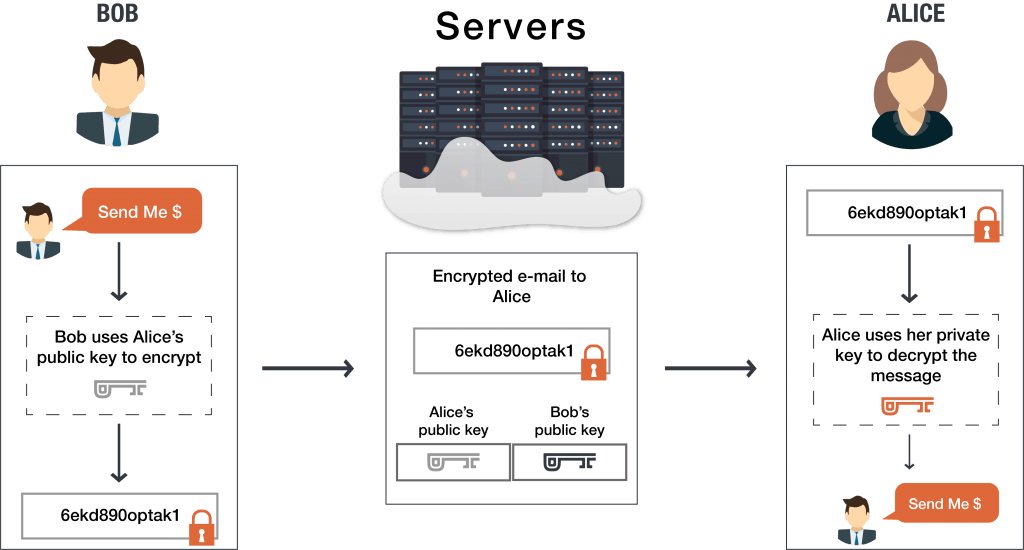
An example of The end-to-end encrypted system provides each with a public-private key pair, whereby their public keys are stored on the server and their private keys are stored on their device.
Bob wants to send Alice an encrypted message. He uses Alice's public key to encrypt his message to her. To understand E2EE, we need to clearly define these keys before we continue.
🌟 Public key Vs Private key
Asymmetric encryption involves a public key and a private key. The public key is public and open to anyone in the system. The private key however is private, only stored on the user's device, and is used to decrypt data.
For example, when you install WhatsApp, your public key is sent to WhatsApp's servers, and your private key stays on your phone. WhatsApp never sees your private key. When someone else starts a conversation with you, they get your public key from WhatsApp's server if they have your phone number.
🌟 How does E2EE Work?
To understand how E2EE works, I will use the same analogy above;
Bob wants to say hello to Alice in private. Alice has a public key and a private key, which are two mathematically related encryption keys. The public key can be shared with anyone, but only Alice has the private key.
First, Bob uses Alice’s public key to encrypt the message, turning “Hello Alice” into something called ciphertext — scrambled, seemingly random characters.
Bob sends this encrypted message over the public internet. Along the way, it may pass through multiple servers, including those belonging to the email service they’re using and to their internet service providers.
Although those companies may try to read the message (or even share them with third parties), it is impossible for them to convert the ciphertext back into readable plaintext.
Only Alice can do that with her private key when it lands in her inbox, as Alice is the only person that has access to her private key. When Alice wants to reply, she simply repeats the process, encrypting her message to Bob using Bob’s public key.
Before I end this article, let me answer some questions that might arise from sharing this with you.
🌟 Is WhatsApp really end-to-end encrypted?
WhatsApp has no ability to see the content of messages or listen to calls that are end-to-end encrypted. That's because the encryption and decryption of messages sent and received on WhatsApp occur entirely on your device.
🌟 Is VPN end-to-end encryption?
Data is encrypted in transit and won't be decrypted until it gets to the recipient for end-to-end encryption, while with a VPN, data is encrypted when it is sent and then gets decrypted when it arrives at the VPN server.
While E2EE can offer privacy benefits that make it desirable in consumer-grade services, many businesses have to balance these benefits with their regulatory requirements. For example, many organizations are subject to mandates that require them to be able to decrypt any communication between their employees or between their employees and third parties.
🌟 Summary
End-to-end encryption is the most secure way to communicate privately and securely online but It is important to note that E2EE alone does not guarantee privacy or security. For example, data may be held unencrypted on the user's own device, or be accessible via their own app, if their login is compromised.
In principle, it prevents potential eavesdroppers – including telecom providers, Internet providers, malicious actors, and even the provider of the communication service – from being able to access the cryptographic keys needed to decrypt the conversation.
🌟 Conclusion
Once again, hope you learned something today from my little closet.
Please consider subscribing or following me for related content, especially about Tech, Python & General Programming.
You can show extra love by buying me a coffee to support this free content and I am also open to partnerships, technical writing roles, collaborations and Python-related training or roles.
📢 You can also follow me on Twitter : ♥ ♥ Waiting for you! 🙂
Subscribe to my newsletter
Read articles from Ronnie Atuhaire directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ronnie Atuhaire
Ronnie Atuhaire
My name is Ronnie & a fellow geek like you😎. I am passionately tech curious. I blog, tweet, write, code, vlog, discuss and eat anything about tech. 😍 Feel Free To Connect 😍
