WEP(Wired Equivalent Privacy)
 Imran Zaheer
Imran ZaheerTable of contents
WEP(Wired Equivalent Privacy) is the wireless security protocol using the RC4 algorithm.
Wired Equivalent Privacy (WEP) is a security protocol and encryption algorithm that secures wireless and Wi-Fi networks. This is not preferred today because of its vulnerabilities that's why its also called Worst Ever Privacy
WEP
Important components of WEP are
- Initialization Vector (IV)
- KEY (Password)
- RC4
- Key Stream
So to encrypt each packet WEP uses the RC4 algorithm which generates a keystream that is used to encrypt the package.
Keystream XOR “plain data to encrypt” = CipherText
Remember the keystream is generated using the RC4 algorithm.
RC4
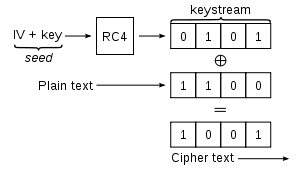
RC4 uses Initialization Vector (IV) + KEY(Password) to make a keystream that gonna encrypt the package. The reason IV is used here is that if RC4 uses the Key only then all the packets gonna have the same keystream which is not good.
So in order to generate a different keystream for each packet IV is introduced.
WEP Working
So Initializing vector nothing but a random 24bit number is produced so that every packet has a unique keystream to decrypt it.
Device Side
- IV + KEY (Password) → RC4 → keystream
IV + KEY is also known as seed (64/128 bit)
Seed is converted to keystream using the RC4 algorithm - Keystream xor “data to send to the router” = Cipher Text
-Data is encrypted using a simple XOR function
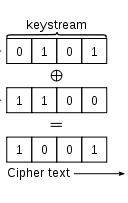
Using Keystream to generate CypherText
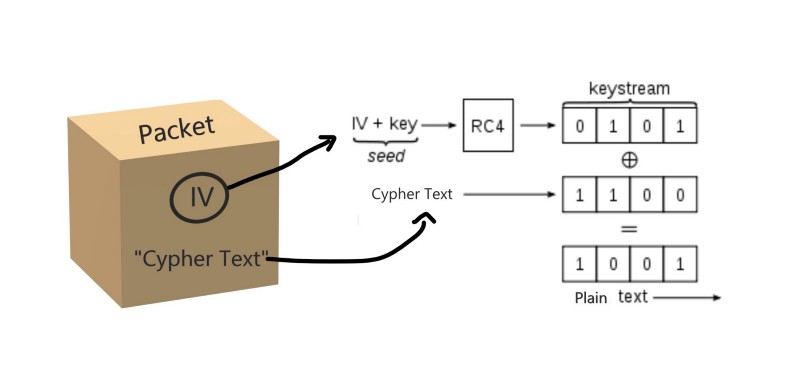
- The packet is sent to the router and now the packet contains two components
IV (initialization vector)
Cypher Text

Packet
IV is added to the packet because AP (Access Point) only has the pre-shared KEY (password). AP doesn’t know which random number (IV) is used with the KEY to generating the Keystream.
Access Point (AP) Side
Ap cannot simply decrypt the package using the KEY only because the packet’s encryption key (keystream) is generated using a random number (IV).
- So router gets this random number (IV) from the packet, generates the keystream (encryption key) using the same RC4 algorithm
IV (Obtained from the packet) + KEY(Password) --> RC4 --> Keystream
Now AP can use this key stream to decrypt data
Keystream . XOR . “Cypher Text” = “Plain Text”
Decrypting Packet
Originally published at theundersurfers.netlify.app
Subscribe to my newsletter
Read articles from Imran Zaheer directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Imran Zaheer
Imran Zaheer
Programmer | Tech enthusiast | Gamer 🌱 Learning new topics: Web, Ai, Cybersecurity 📝 I regularly write articles on https://theundersurfers.netlify.app