Securing a Web Application in Azure Leveraging the Cisco NextGen Firewall.
 Syed Mansoor Hashmi
Syed Mansoor Hashmi
Securing a Web Application in Azure Leveraging the Cisco NextGen Firewall.
In this blog we are going to learn how to secure the web application in Azure leveraging Cisco NextGen firewall and IDS/IPS.
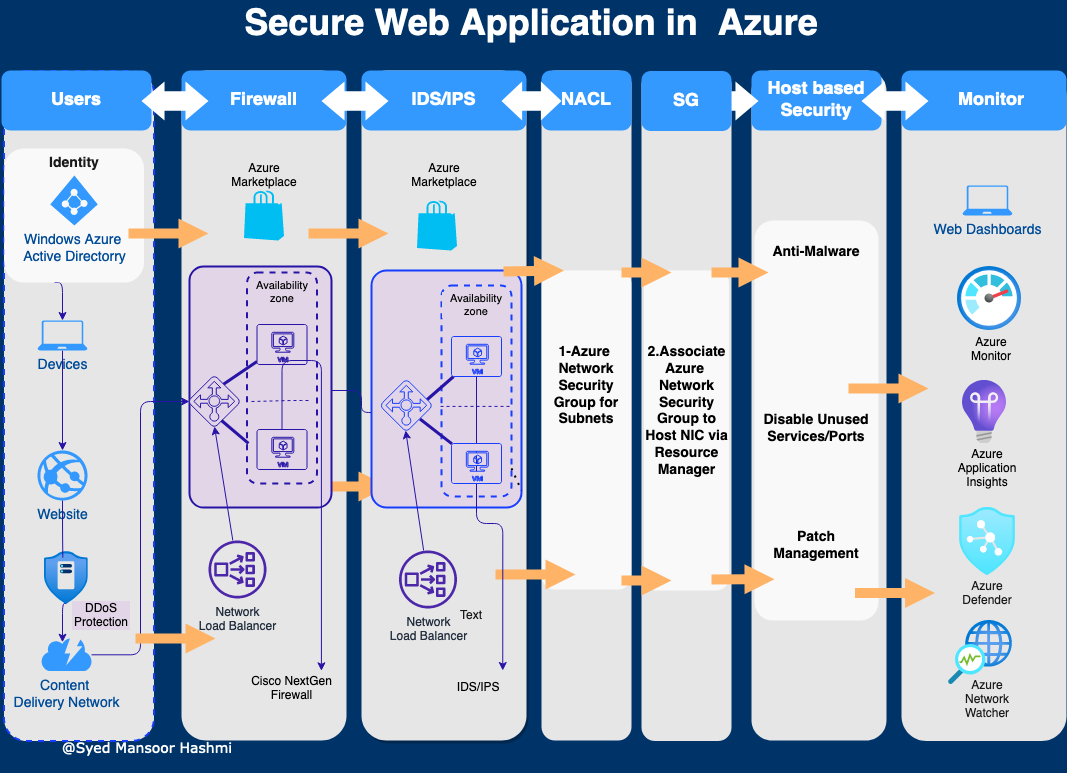
When you think about security in the cloud, always consider the multi-layer approach. It defines the multiple layers of security controls in the cloud to ensure that if a security attack is not caught in one layer, it will most likely be caught in the next. The multiple layers increase the overall security score of the environment and reduce the probability of a security breach by a huge margin. We’ll discuss the different measures for Azure web application security best practices by leveraging Cisco NextGen Firewall.
Identity & Access Management: It is crucial to determine the user's identification, the capabilities that the user can perform on the system, and tracking the user’s access. This is performed with Identity and Access management. Identity and access management can be summarized below:
- Authentication – Who are you? (Identification)
- Authorization – What can you do? (Capabilities)
- Accounting – What have you done? (Tracking) Identity and access management gives us the ability to provide the right level of access to our users. What is the right level of access? The minimal amount of access necessary for people to perform their jobs.
All Azure resources are governed and controlled through Azure Active Directory, which is also known as the central identity plane. Azure Active Directory (AD) is Microsoft's cloud-based identity and access management (IAM) service; it can be used to manage secure user sign-in to thousands of external services, such as Microsoft Office 365, the Azure portal, and other SaaS applications. Furthermore, you can control access to your Azure resources using Role-based access control (RBAC). Users can be granted higher privileges just-in-time using Azure Privileged Identity Management.
DDos Protection Service This cloud service provides the protection from distributed denial of services (DDoS) attacks. It minimizes application downtime and latency. Distributed denial of service, or DDoS, is a type of attack where an attacker sends more requests to an application than the application is capable of handling. The resulting effect is resources being depleted, affecting the application’s availability and ability to service its customers. DDoS attacks can be targeted at any endpoint that is publicly reachable through the Internet.
Azure Content Delivery Network: Content Delivery Network is a group of servers spread out over many locations that deliver your content to the nearest user, as opposed to one server location, which can take time to deliver the content. The Azure Content Delivery Network is designed to send audio, video, apps, photos, and other files to your customers faster and more reliably, using the servers closest to each user. Acceleration Data Transfer provides dynamic site acceleration of non-cacheable, dynamic content that is generated by your web application. CDN provides protection against Network and Application Layer attacks.
Cisco Virtual Appliances (NGFWv) on Azure: You can deploy the Cisco NGFWv (Next Generation Firewall Virtual) on Azure. At a high level, you will need to deploy the device on Azure and then configure the internal "network" of the Cisco device to allow it to route traffic properly on your Virtual Network (VNet) in Azure.
You can deploy Cisco Firepower NGFW (Threat Defense Virtual) on Azure:
Cisco Firepower NGFW (Threat Defense Virtual): Cisco NGFWv virtual firewalls deliver advanced threat defense options including next generation IPS (NGIPS), security intelligence (SI), advanced malware protection (AMP), URL filtering, application visibility and control (AVC), and flexible VPN connectivity. By leveraging Azure Traffic Manager, Cisco virtual firewalls deliver a highly scalable solution for remote access VPN (RA-VPN). It also integrates with Azure Transit VNet for scalable inter-VNet traffic. Cisco NGFWv automatically scales up/down to meet the needs of dynamic environments and high availability provides resilience.
Source: https://github.com/CiscoDevNet/cisco-ftdv/tree/master/deployment-templates/azure https://github.com/cisco/firepower-ngfw https://www.cisco.com/c/en/us/td/docs/security/firepower/quick_start/consolidated_ftdv_gsg/ftdv-gsg/m-ftdv-azure-gsg.html
You can deploy from the Azure Marketplace: https://azuremarketplace.microsoft.com/en-us/marketplace/apps/cisco.cisco-firepower-threat-defense-appliance?tab=Overview). You can also use the ARM template or leveraging Terraform.
Intrusion Prevention System / Intrusion Detection System IPS/IDS: is a device or software application that monitors a network or systems for malicious activity or policy violations. They can look at behaviors, and they adapt and stop the activity as needed. It will create rules on demand. It is very useful to have intrusion detection, intrusion prevention in your systems. NextGen Firewall mostly has Intrusion Prevention System capabilities, but you can deploy dedicated IPS/IDS on virtual machine on Azure from Azure marketplace which gives an extra layer of security.
Network Access Control List: This is a virtual router function that blocks traffic in and out of the subnets. It is stateless, that is both the inbound and outbound traffic must be stated. More so, the virtual device is stateless because it does not watch the way the traffic is coming, it’s only creating some packet inspection rules that allow or deny. All network ACLs have a default policy, which is to deny all traffic. As a result, when building policies, one must specify the source and the destination address (allowed before the deny policy). There can be some wildcards in there as well, the protocol and the port number.
A network security group (NSG), in Azure, is the way to activate a rule or access control list (ACL), which will allow or deny network traffic to your virtual machine instances in a virtual network. NSGs can be associated with subnets or individual virtual machine instances within that subnet. When an NSG is associated with a subnet, the ACL rules apply to all Virtual Machine instances of that subnet.
Security Group: This is a virtual firewall that keeps traffic out of the Instance (Virtual machine), or service it is stateful: that is once it allows inbound traffic, the corresponding outbound traffic is allowed.
In Azure, you can restrict traffic to an individual virtual machine by associating an NSG directly to that virtual machine.You can filter network traffic to and from Azure resources in a virtual network through Network Security Groups which contains security rules allowing or denying traffic.
Host-Based Security: It is essential to secure the host, you can enable host based firewall. Azure Firewall is a cloud-native and intelligent network firewall security service that provides the best of breed threat protection for your cloud workloads running in Azure. It's a fully stateful, firewall as a service with built-in high availability and unrestricted cloud scalability.
Also disable unnecessary ports and services on virtual machines/host.
Patch Management You can leverage patch management which assure all the virtual machines/hosts are patched.
Azure Update management center: Update management center is a unified service to help manage and govern updates for all your machines. Monitor Windows and Linux update compliance across your deployments in Azure, on-premises, and on other cloud platforms from a single dashboard. Make updates in real time or schedule them within a defined maintenance window.
Secure data in transit and at rest: Regarding securing your data in transit and at rest please review my last blog.
Monitoring:
Azure Monitor: Provides comprehensive solution for collecting, analyzing, and acting on telemetry from your cloud and on-premises environments.
Azure Application Insight: A feature of Azure Monitor, Application Insights is an extensible Application Performance Management (APM) service for developers and DevOps professionals, which provides telemetry insights and information, in order to better understand how applications are performing and to identify areas for optimization.
Microsoft Defender for Cloud: is a great tool that can help in strengthening your security posture in Azure. It provides advanced threat protection across hybrid workloads. It protect your multi-cloud and hybrid environments.
Azure Network Watcher: Azure Network Watcher allows you to monitor, diagnose, and analyze the traffic in Azure Virtual Network.
Conclusion: In this blog we learn how to secure a web application by leveraging Cisco NextGen Firewall in the Azure cloud with the multi-layer approach.
Subscribe to my newsletter
Read articles from Syed Mansoor Hashmi directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Syed Mansoor Hashmi
Syed Mansoor Hashmi
I am energetic and obsessed with helping and guiding our customers so that they can achieve their business objectives. I always look for the big picture. I am extremely passionate about technology and a continues learner.