Pay-to-Public-Key-Hash Script in Bitcoin.
 lumunge
lumungeTable of contents
In this article, we learn about the Pay-to-Public-Key-Hash script, the most commonly used locking script for the majority of transactions processed on the bitcoin network.
Bitcoin script is a stack-based turing-incomplete programming language used by the Bitcoin blockchain to program transactions. In the article on locking and unlocking scripts, we learn about the two most important transaction scripts. Locking scripts are used to specify a condition that is to be met before funds can be spent by the recipient. On the other hand, unlocking scripts are used to satisfy the condition specified by the locking scripts. These are used on the blockchain to validate transactions by participants.
In this article, we will learn about a specific type of transaction script used in the Bitcoin network. It is referred to as the P2PKH(Pay-To-Public-Key-Hash). This is the most commonly used locking script for the majority of transactions processed on the bitcoin network. Outputs that have been locked by this script are unlocked using a public key and a digital signature created by the corresponding private key.
Before P2PKH, we had P2PK(Pay-to-Public-Key). This however was changed for two reasons, the first was because of the possibility of quantum computers being able to retrieve a private key from a public one. This is solved by publishing the public key only when coins are spent, this of course assumes that addresses are not reused. In this case, it becomes impossible to derive the private key. The second reason is due to the size of the predecessors, P2PKH made the size smaller(20 bytes). Now it is possible to embed it in a medium such as QR codes or print.
In general, both transactions are similar in that they use complex cryptography to implement similar logic whereby a recipient has to prove that he/she is the owner of the public key that receives the sent bitcoins and the private key that is able to spend the sent bitcoins. The only major feature that distinguishes the two is that P2PKH does not require a user to provide their full public key to the locking script. This improved Bitcoins' security against future vulnerabilities.
How a P2PKH Script Works.
Let's consider the following scenario to get a better understanding of a P2PKH Bitcoin transaction. We have two blockchain users A and B. A wants to send B some bitcoins. For this A creates a new transaction with the appropriate data. This leads to the use of the bitcoin script programming language to generate a script that will be part of P2PKH referred to as scriptSig. This script is to make sure that A owns the bitcoins he/she intends to send to B. This is done by taking A's public key which received the bitcoins and verifying that it has the required private key that can spend the bitcoins. If A can indeed spend the bitcoins, the next step is to generate a P2PKH script. We now generate a locking script, that specifies conditions to be met for the bitcoins to be spent. By combining the locking and unlocking scripts we have a complete P2PKH.
This process is summarized as follows; User A can only send bitcoins he/she owns. For user B to be able to spend the amount received he/she must prove that the address that is embedded in the transaction data is indeed his/hers. For this, B provides the correct public and private keys to be able to spend the amount.
Commonly used script OP_CODES with P2PKH script include;
OP_DUP - Copies the value at the top of the stack.
OP_HASH160 - Performs a SHA-256 and RIPEMD-160 double hashing of the copied value.
OP_DATA_X - Pushes the address onto the stack.
OP_EQUALVERIFY - Verifies that the hash of the copied value matches the expected hash pushed onto the stack.
OP_CHECKSIG - Verifies that stack has a public key and a signature and verifies the signature is valid for the corresponding public key.
An example
Consider the following P2PKH transaction script;
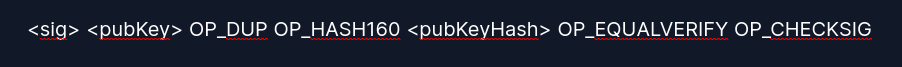
The steps of exectution are as follows;
- First the original public key is duplicated using the OP_DUP OP_CODE.
- After duplication, it is hashed using the OP_HASH160 OP_CODE.
- The hashed value is compared with the hashed public key in the locking script(scriptPubKey) using the OP_EQUALVERIFY OP_CODE. This makes sure that they are similar.
- If it is a match, the script proceeds to check the digital signature against the public key using the OP_CHECKSIG OP_CODE.
Pros and Cons of P2PKH.
pros
- A pro of the P2PKH transaction script is that it is reliable in transactions as users can share their public keys in order to exchange value with each other.
- Public keys are hashed into a fixed-size string that is much smaller. This means that it can be stored in mediums such as QR codes.
- Also smaller keys mean fewer mistakes and network bandwidth used compared to P2PK addresses.
- This script is simpler compared to its counterparts and therefore easier to use.
cons
- A con of P2PKH is the additional complexity that goes into generating such addresses.
- This script was implemented before SegWit therefore, legacy addresses are incompatible with wallets that use this script. Users can send a transaction from a P2PKH address to a SegWit address however, the fees for such a transaction are very high.
Summary
A P2PKH transaction is the most commonly used transaction type on the Bitcoin network. P2PKH was implemented for two reasons, the first is to make it easier for transaction parties to be able to share their public keys for any transaction between them. The public key is hashed to a fixed-size string which is much smaller. Secondly, ECDSA is vulnerable to a modified Shor algorithm in that using a quantum computer the private key can be derived from the public key.
References
Subscribe to my newsletter
Read articles from lumunge directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by