A Byte of Blockchain - Week 42 Keys, Address & Signature..a deep dive
 Anand N
Anand NTable of contents

Image by Bastian Riccardi from Pixabay
Recap
Last week we discussed about wallets and why it is an integral part of the Blockchain ecosystem. Wallets are like browsers through which people can access Blockchain ecosystem and maintain control over their crypto assets like browsers facilitate access to internet.
Wallets are software applications that serve as the primary user interface to Ethereum
Wallets control access to a user's cryptocurrency, manage keys & addresses, creates & signs transactions & tracks balances of cryptocurrency corresponding to that address.
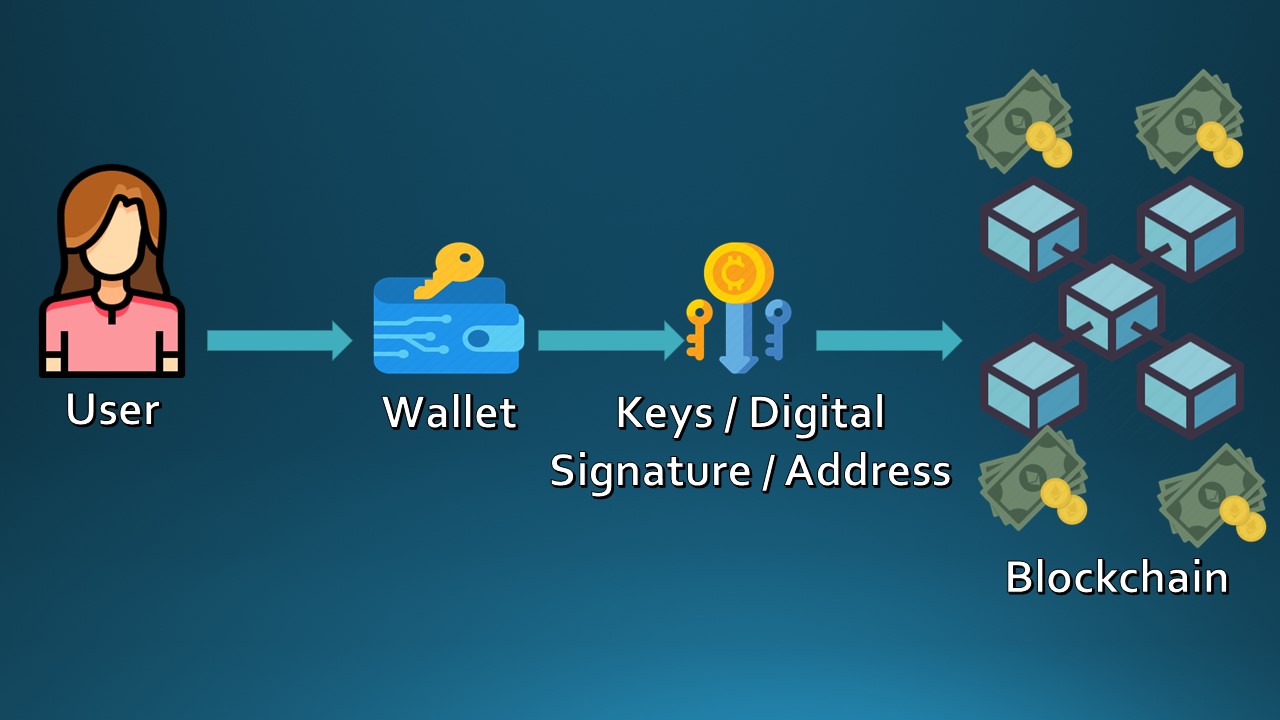
We also defined External Owned Accounts (EoAs) as accounts from where a transaction is initiated using a wallet.
What exactly are keys, addresses & signatures? Read on.....
Keys

Without getting into the underlying mathematics, let us understand how a wallet generates private or public keys & addresses.
Private Key
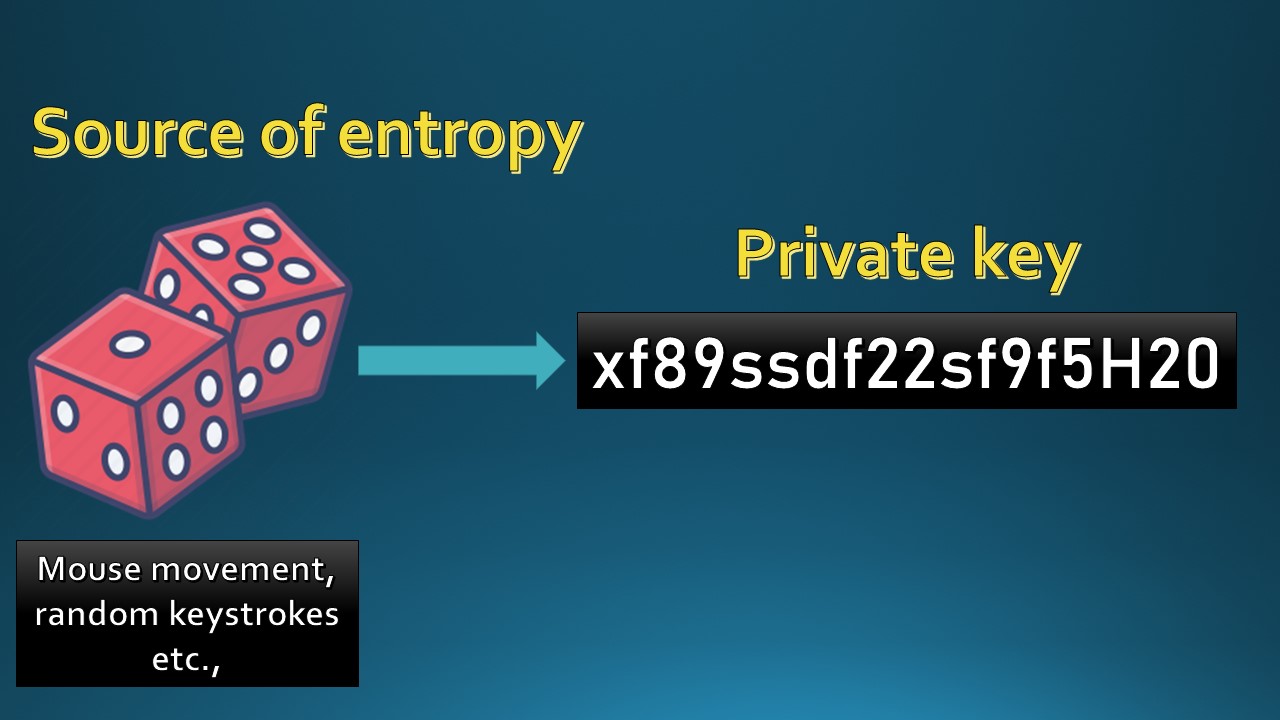
It all starts with the private key. In very simple terms, a private key is just a random number - generated in the range from 1 to 2256. This represents the total number of private keys that can be generated.
Randomness or entropy is important when generating a private key. What is entropy? As per wikipedia, entropy is defined as:
In computing, entropy is the randomness collected by an operating system or application for use in cryptography or other uses that require random data. This randomness is often collected from hardware sources (variance in fan noise or HDD), either preexisting ones such as mouse movements or specially provided randomness generators.
For example, there are features in some encryption software like Veracrypt where we are asked to move our mouse to create randomness or entropy to generate an encryption key. The mouse should be moved randomly and not in an ordered fashion.
The above in simple terms means that a private key generated should be truly random & this randomness is created from various sources (as described above). If it is not random, then key collision will occur which means the same private key will be generated for two different wallets which cannot be allowed to happen.
This randomness is generated by an operating system. Ethereum uses the underlying operating system for randomness. A great explanation for entropy can be found here.
Public Key
The first step is generation of the random private key. Then, the public key is generated from the private key using an algorithm known as ECDSA which means Elliptical Curve Digital Signature Algorithm.
The ECDSA (Elliptical Curve Digital Signature Algorithm) is a cryptographically secure digital signature scheme, based on the elliptic-curve cryptography(ECC) (Source : here)
Using the above algorithm, the public key is generated. In very simple terms, there is an equation called elliptical curve equation and the point on the elliptical curve (x & y coordinates) along with the private key which solves this equation is the public key.
Ethereum Address
After creation of the private & public keys, the next step is to generate Ethereum Address which are derived from public keys by hashing the public keys. We discussed hashing in Week 12. To recap,
As per wikipedia, a hash function is any function that can be used to map data of arbitrary size to fixed-size values. The output returned by a hash function are called hash values, hash codes, digests or simply hashes. (which is the output on the right hand side of our diagram below).
To put it simply, hashing is the process of having an input of any length but getting an output of a fixed length. This means the output length is independent of the length of the input & remains constant.
The below diagram makes it more clear
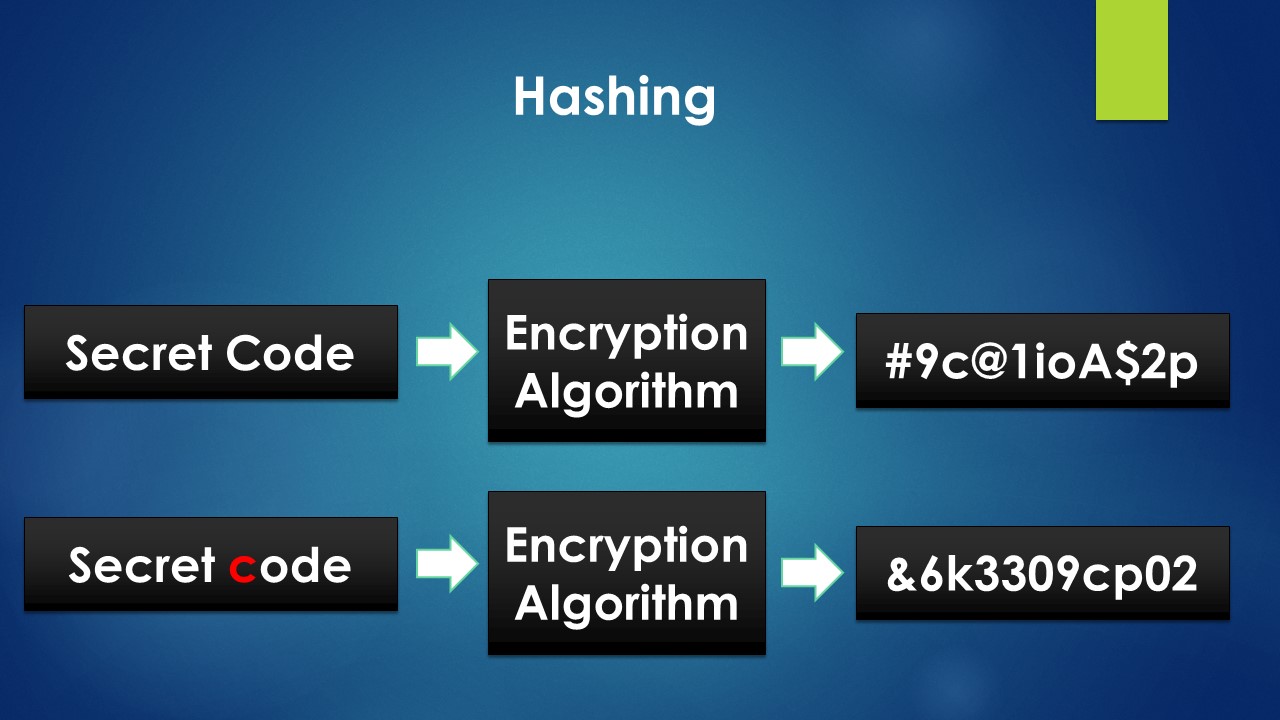
A hash function is one - way meaning it is almost impossible to recompute the input source figures from which the hash output is derived.
Signature
The ECDSA signing algorithm takes as input
a. The Transaction &
b. The private key
to generate a signature as output.
Thus, transaction + private key = Signature
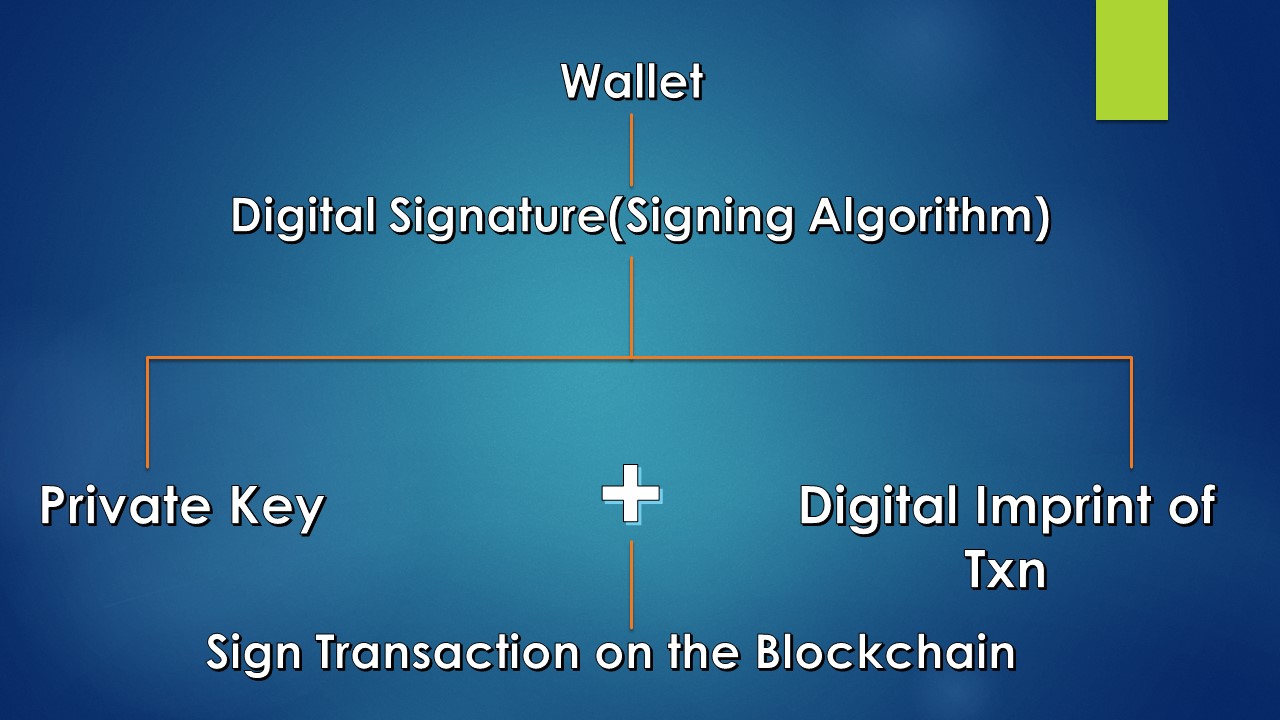
The private keys are only stored in wallets & never used in the Ethereum Blockchain. Any access to crypto funds or ether is done through signatures.
Seed Phrase
Now that we know how private keys, public keys & addresses are generated and also how through signatures, the keys access the tokens or crypto funds, let us understand something known as seed phrase.
When you are using a wallet for the first time, it will give a set of random words which you have to note down & keep it safe. Why should we keep it safe?
A seed phrase is like a recovery password. It allows you to regain access to your wallet in case it is broken (hardware wallet) or in case you lose your phone (mobile wallet). As I mentioned in one of my blogs earlier, crypto empowers us to be our own bank. Hence, as Spider man said - 'With great power comes great responsibility". Hence, it is the responsibility of the wallet holder to ensure safety of his or her funds. There is no bank or fire-walled security measures to protect your funds.
A seed phrase is just group of random words like "lake", "city", "water", "iron", "matter". The words must be entered exactly the same way they are shown when generated.
There are best practices to store your seed phrase which can be found online. Now, why do we need a seed phrase?
These random words in the exact same order is used to generate the user's private key. There is a standard called BIP-39 followed by wallets which is used to generate these random words.

Subscribe to my newsletter
Read articles from Anand N directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by