Use OCI To Access Your APEX Applications #JoelKallmanDay
 Matt Paine
Matt Paine
Introduction
APEX Authentication schemes can be used to allow sign-on using a variety of methods, e.g. APEX Accounts, Social Sign On, or even no sign-on at all!
If you've provisioned ATP or APEX service on Oracle Cloud Infrastructure, you can link your APEX apps to OCI for sign-on. There are some advantages of doing this:
- Your APEX applications can use the same username/password credentials as OCI.
- OCI allows MFA, for example using the Oracle Mobile Authenticator app, email, DUO or SMS.
- OCI allows access controls using network perimeters.
- OCI has inbuilt reports auditing sign-on.
- OCI can link to one or more third-party identity providers (e.g. Azure AD, Okta, etc). APEX can do that too (see
http://dgielis.blogspot.com/2018/06/facebook-google-and-custom.html)- but OCI can display all enabled providers/methods on a single sign-on screen and seamlessly handles switching between them without additional code.
A couple of disadvantages:
- Your APEX app becomes less portable - it will be hard to move to on-premise or AWS RDS hosting without making adjustments to the way users sign on. If you're all-in on APEX on OCI, that may be less of an issue.
- Social Sign-on does not work behind a simple reverse proxy - you have to run customer-managed ORDS so that APEX sends the right callback URL to the identity provider, in this case OCI.
This blog entry shows you how to link your APEX applications to OCI.
OCI Configuration
Navigate to Identity & Security -> Domains and open the default Domain.
Click on Applications and create a new Confidential application representing your APEX application.
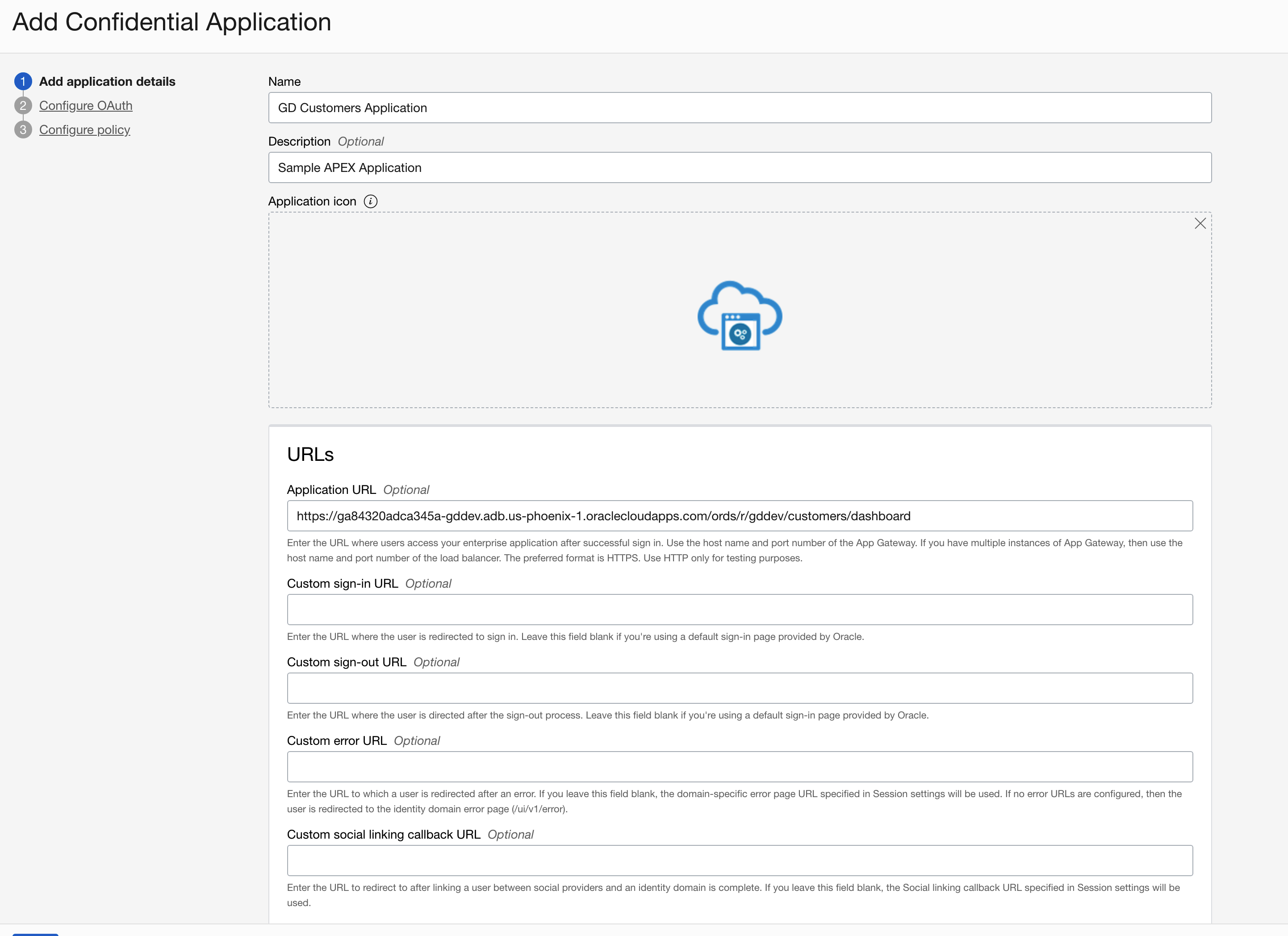
https://ga84320adca345a-gddev.adb.us-phoenix-1.oraclecloudapps.com/ords/r/gddev/customers/dashboard is the URL for my APEX application.
Configure the Client as follows:
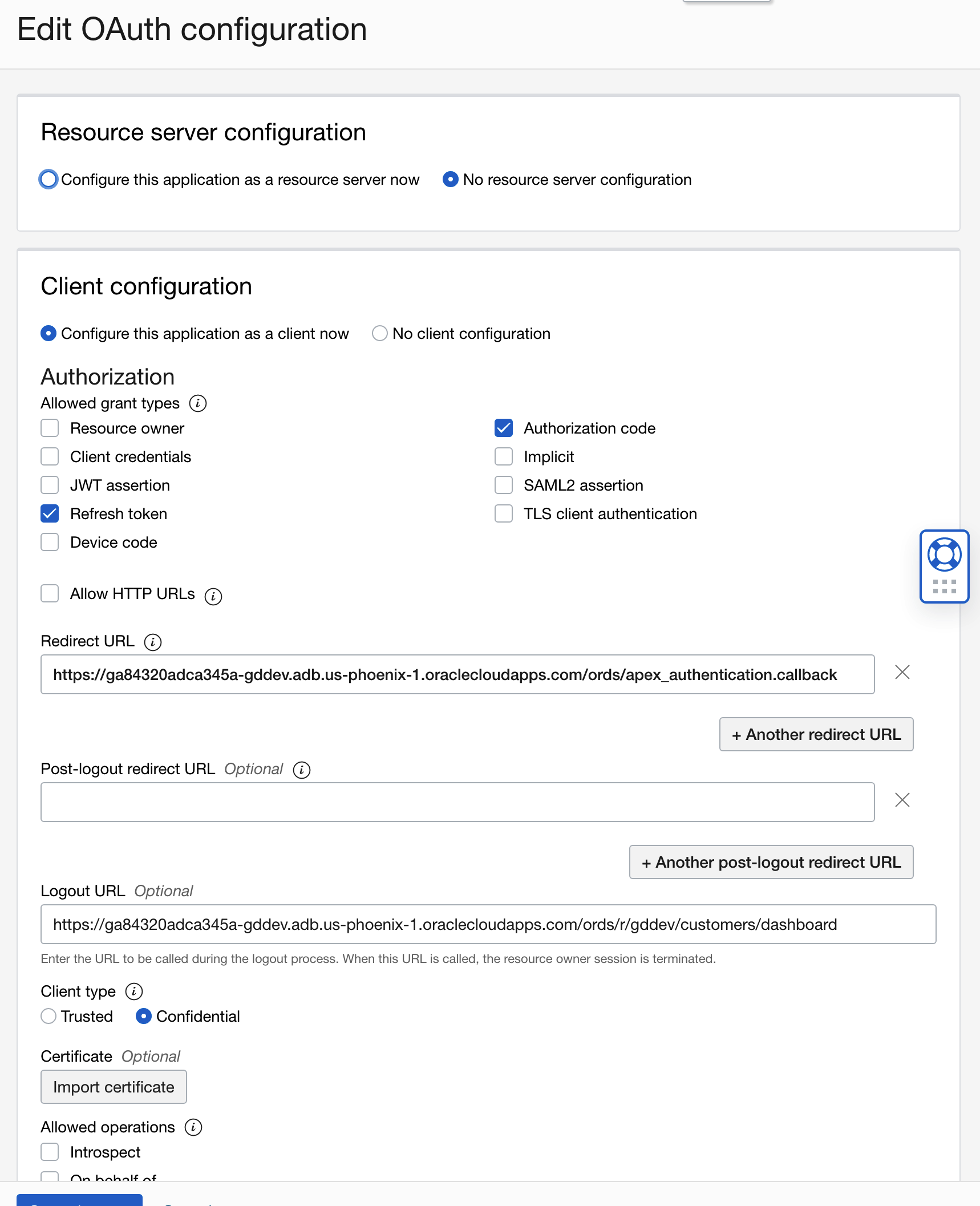
https://ga84320adca345a-gddev.adb.us-phoenix-1.oraclecloudapps.com/ords/apex_authentication.callbackis the callback URL for APEX.https://ga84320adca345a-gddev.adb.us-phoenix-1.oraclecloudapps.com/ords/r/gddev/customers/dashboardis the URL for my APEX application.
Skip Web Tier Policy and click on Finish.
Activate the Application and note the Client ID and Client Secret - they will be needed in Oracle APEX.
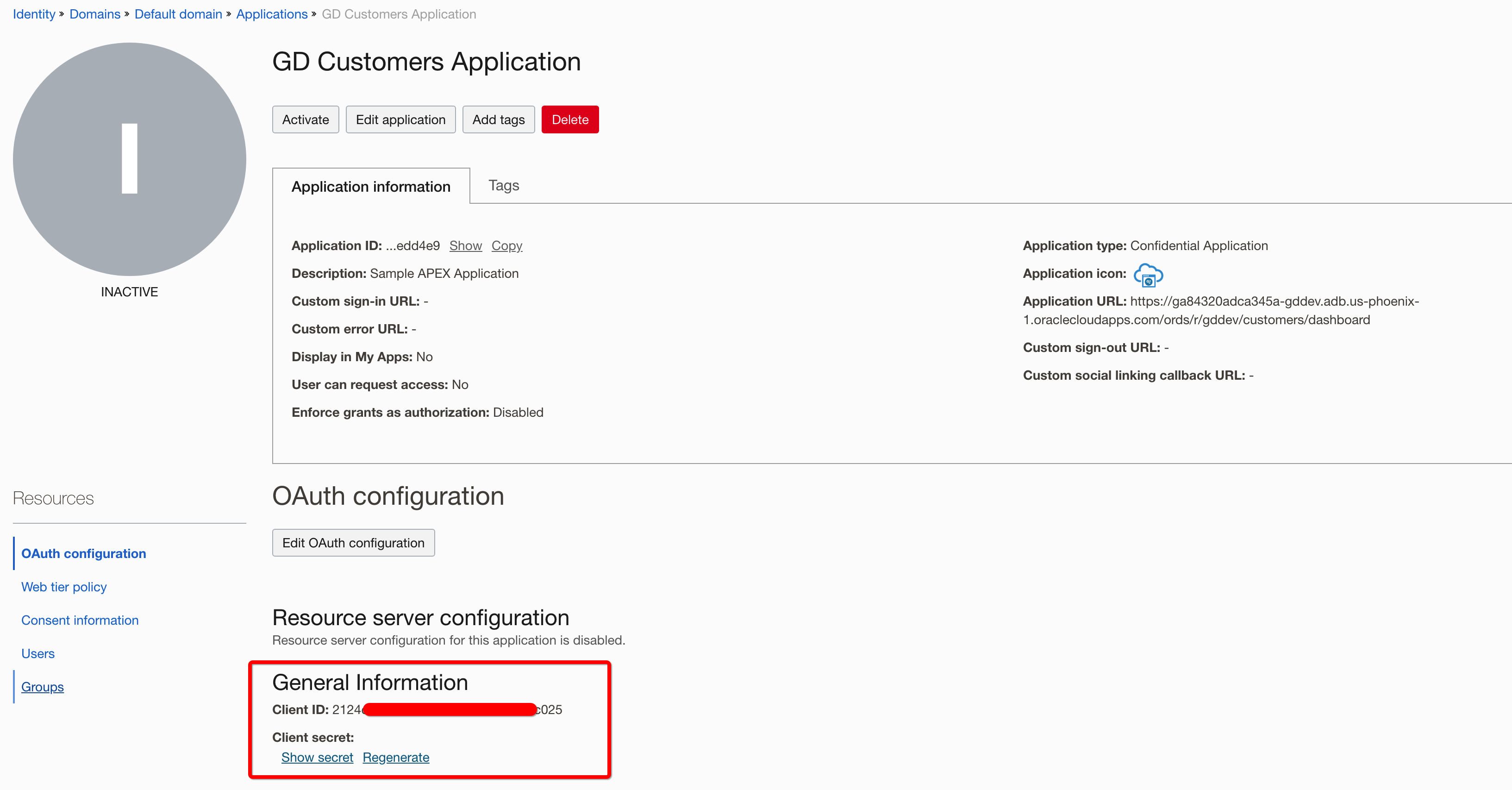
Navigate to the Domain and note the IDCS URL
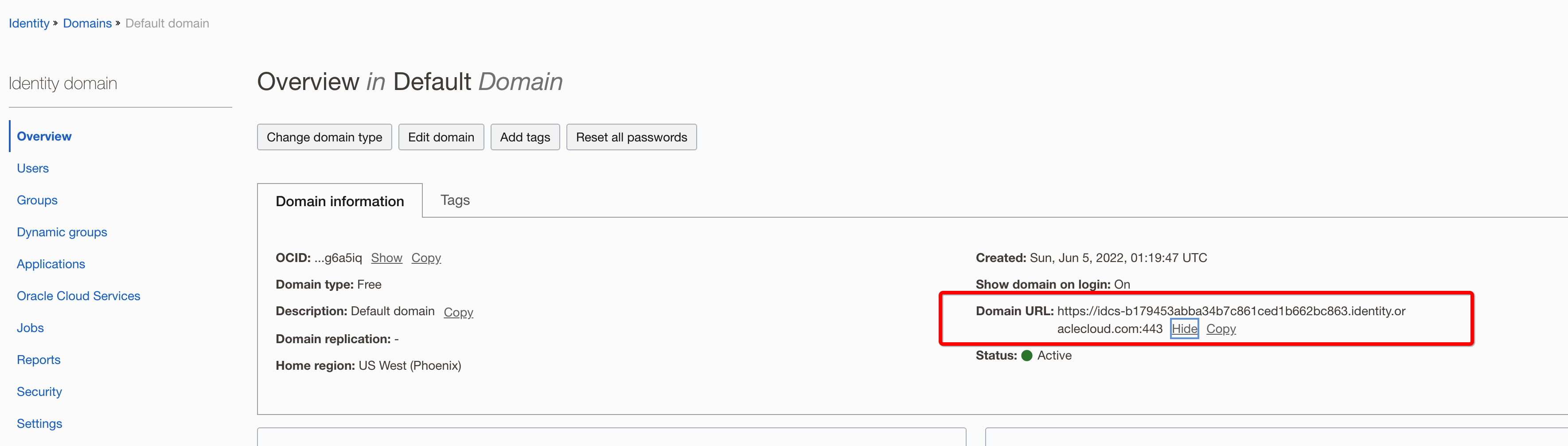
e.g. https://idcs-b179453abba34b7c861ced1b662bc863.identity.oraclecloud.com:443
APEX Configuration
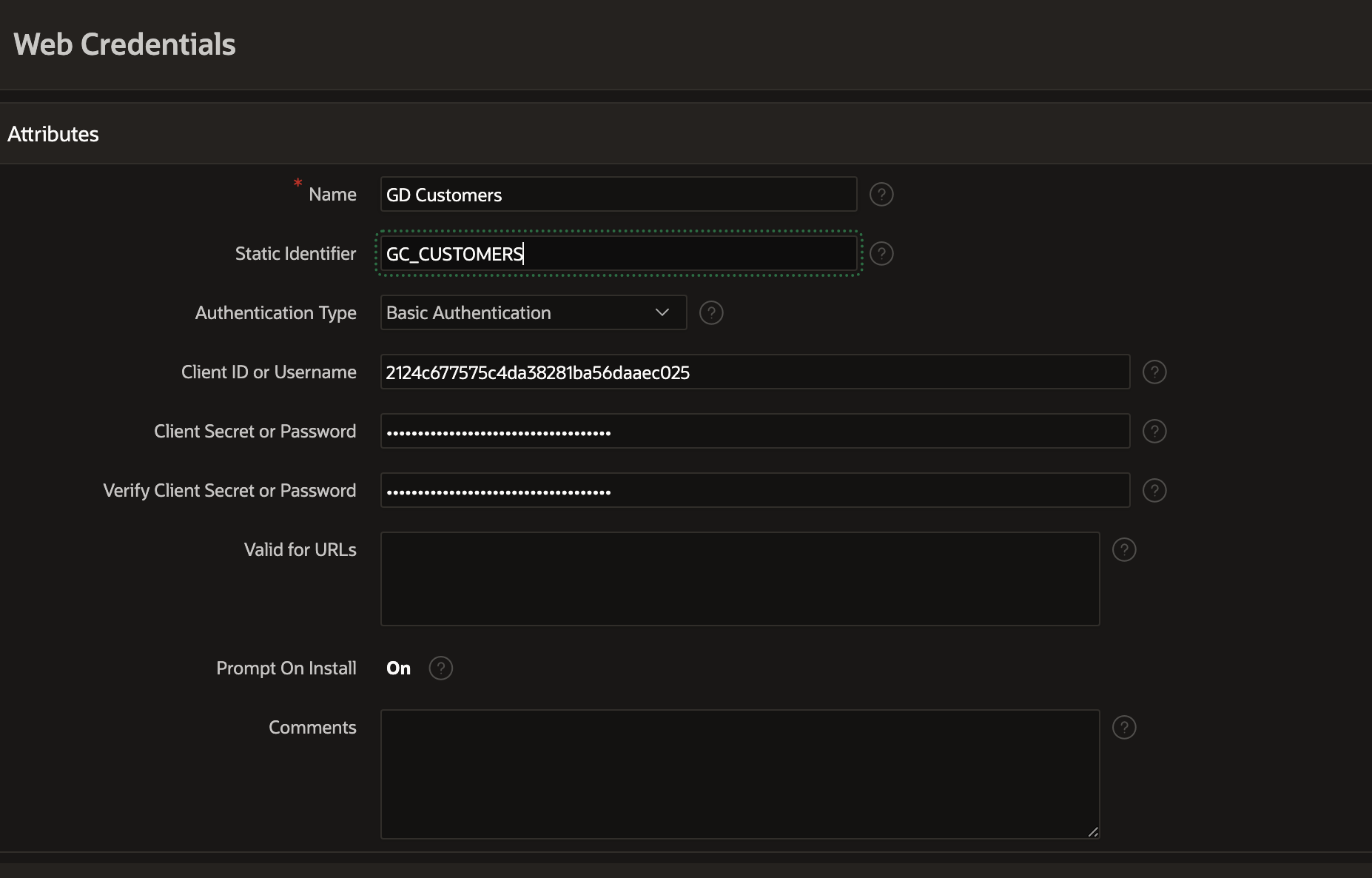
APEX Web Credentials
Create a new Web Credentials under Workspace Utilities - Web Credentials. Use the Client ID and Client Secret you saved earlier.
APEX Authentication Scheme
Create a new Authentication scheme under Shared Components.
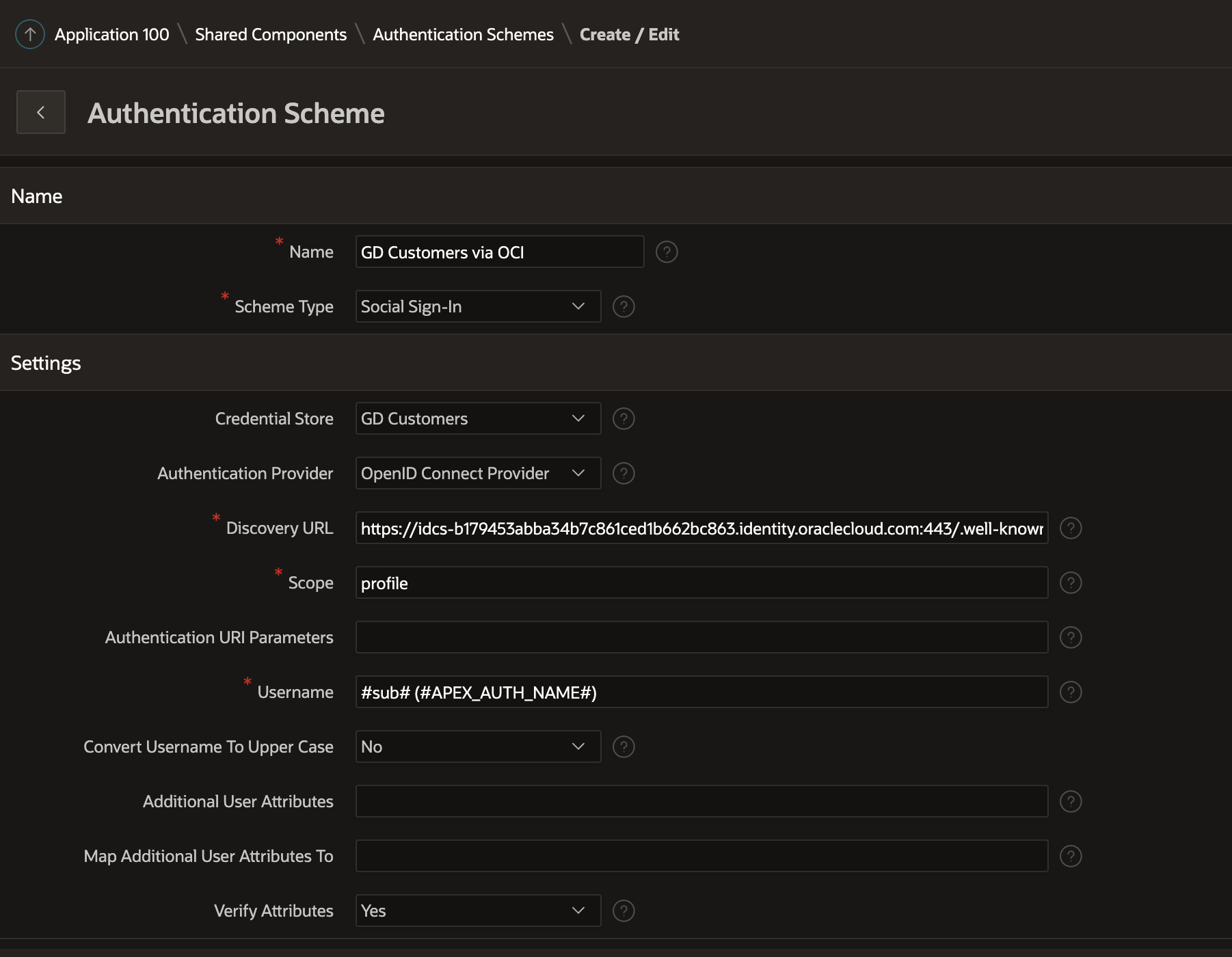
The Discovery URL is built from the IDCS URL you found earlier:
e.g. 'https://idcs-b179453abba34b7c861ced1b662bc863.identity.oraclecloud.com:443/.well-known/openid-configuration'
Create the Authentication Scheme and ensure it is current.
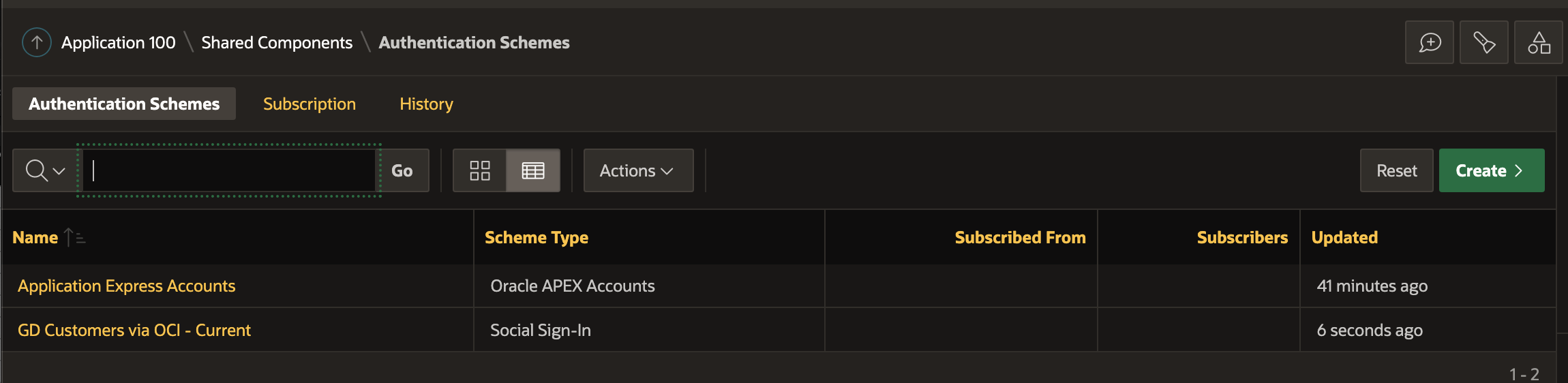
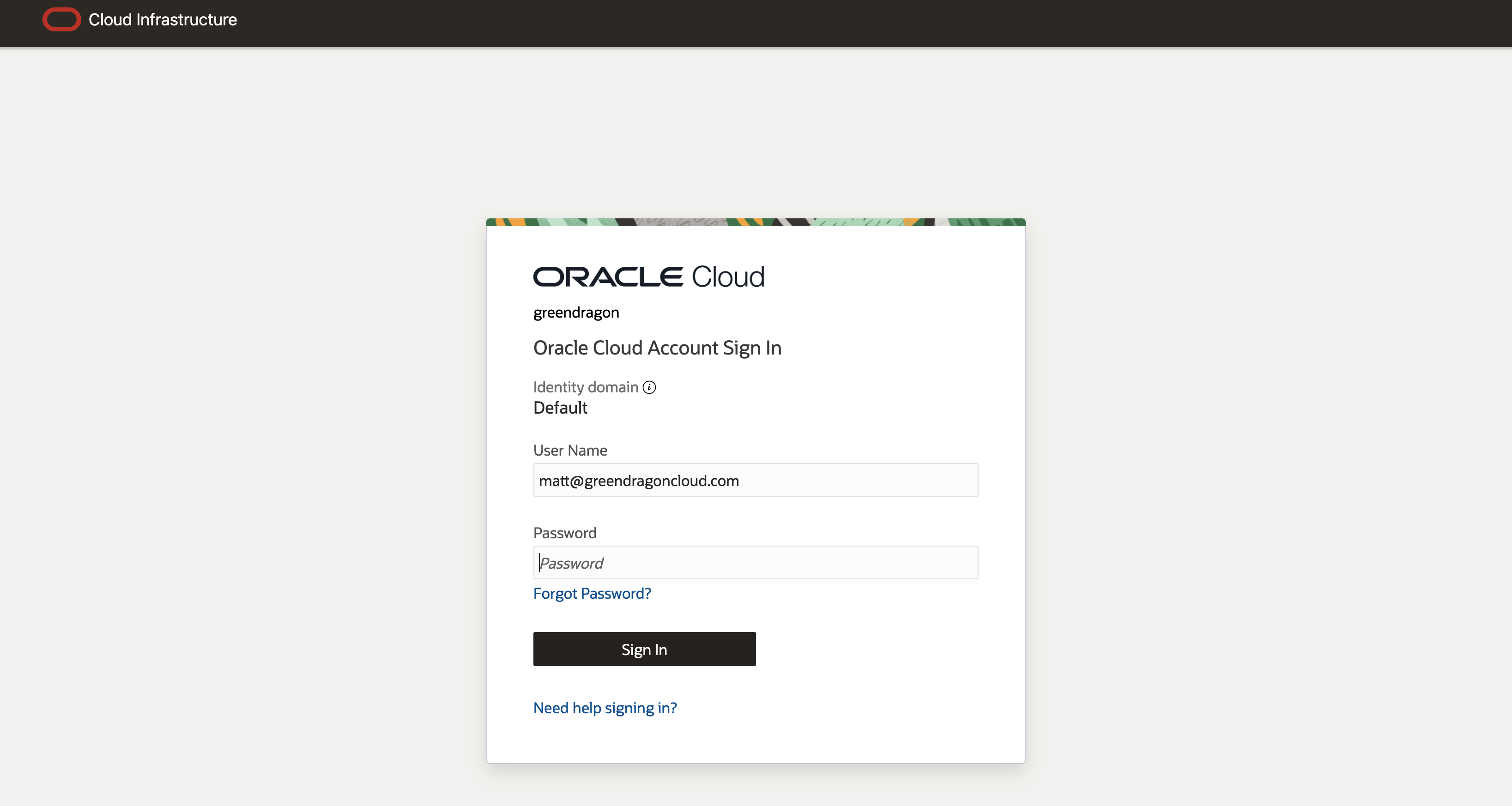
Test Sign On
Run your APEX application, sign on, navigate MFA (if you have this enabled), and approve access to your profile. You should be in!

Reporting
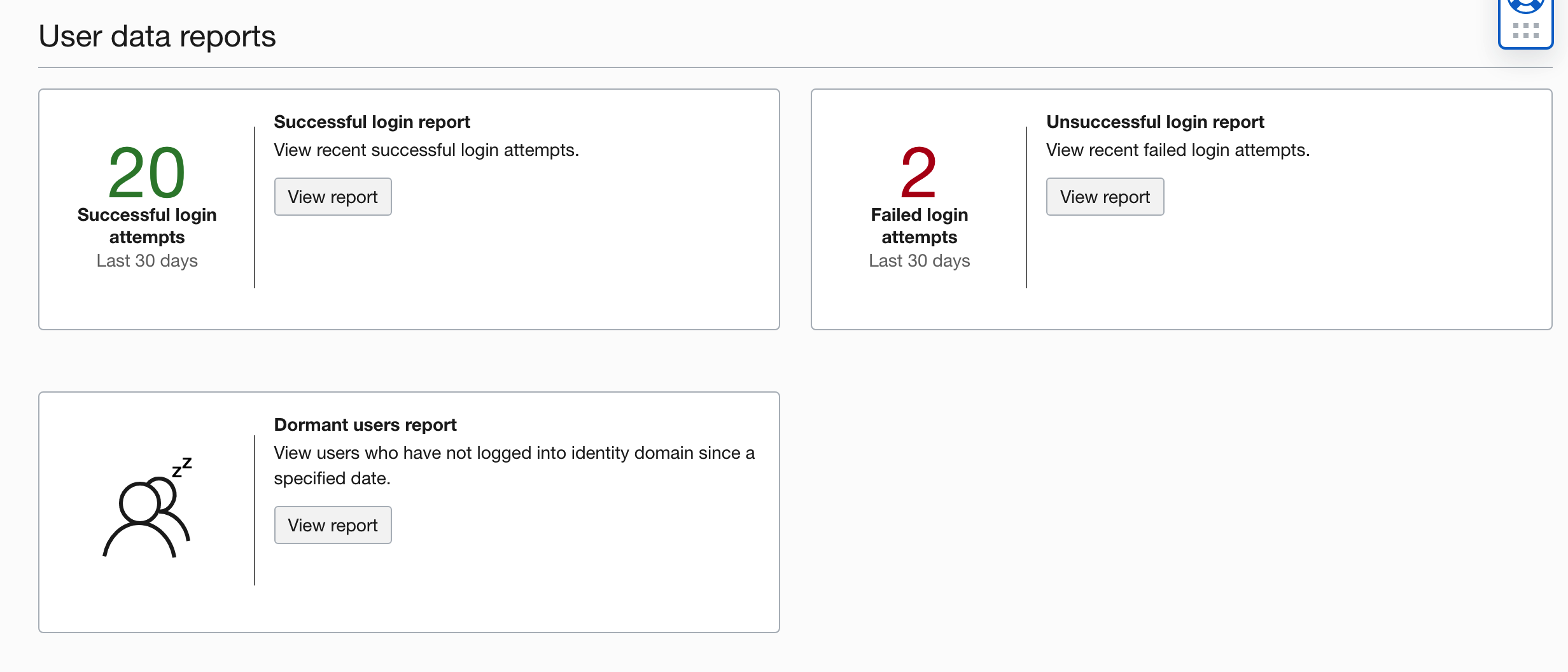
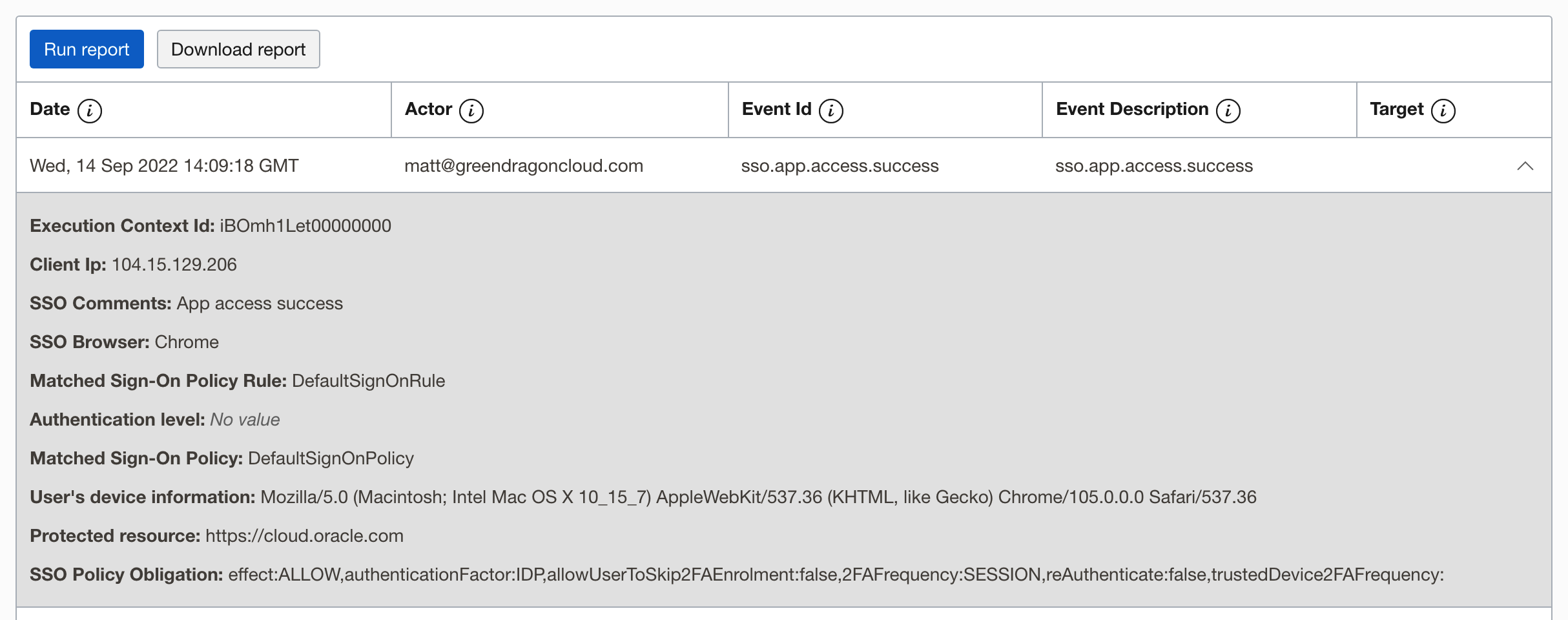
You can start to review the OCI reports showing who logged in to your applications:
Summary
It doesn't take long to get the APEX authentication scheme up and running. Once this is complete, you can extend the OCI side to add additional security, for example:
- A Network Perimeter can be configured against the Client Application, enforcing sign-on rules around your local PC, VPN, or network.
- You can add Azure, Google, or Okta into OCI as Identity Providers and use these against different applications.
- You can use OCI to control access to the APEX Builder as well as APEX applications.
In conclusion - this is a quick and simple way to add MFA, network security, and SSO to your APEX environment - all for free ready and waiting for you as soon as you have an OCI account.
Subscribe to my newsletter
Read articles from Matt Paine directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
