False-positive PGP spoofing

Talk of the Cicada PGP message still continues today.
But this post isn't specifically about the Cicada PGP message or anything to do with Cicada 3301.
It's only related because the idea for this post come from discussion on Twitter.
Before you continue reading, I must point out that what I am publishing here is nothing new and has been talked about before, probably extensively.
I am simply presenting it in simple terms so it can be understood by anyone and so that anyone can try for themselves by following the same steps.
Admittedly, PGP is a real weak spot for me so I did get some help with this from Twitter user @dean_emmet.
I am using Kleopatra.
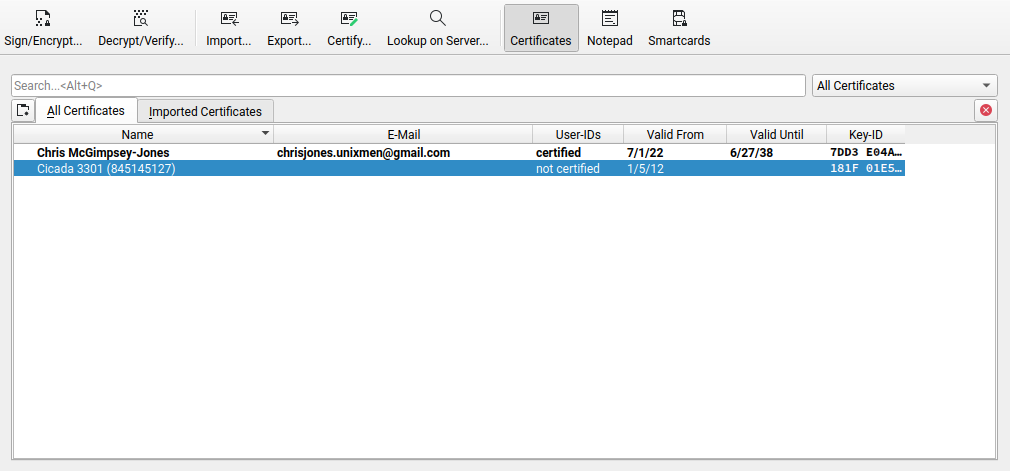
The first thing you need to do is import the Cicada 3301 PGP public key.
I have dumped it here https://pastebin.com/a1ZcAGmE
Import the key into Kleopatra.
Once imported you should see it in your list.
Now create an empty file and dump the following message into it:
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA512
Beware false paths. Always verify PGP signature from 7A35090F.
3301
-----BEGIN PGP SIGNATURE-----
Version: CicadaPG v.3301
iQIcBAEBCgAGBQJY5CrwAAoJEBgfAeV6NQkPFvMQAJa3W1K1gFcxFPk90fMFFKKx
oEd7wt26sMYE+FIQmaiC/4Eswmys52+joTUft4oSfHuxT79gg84EhSPSfyn4IpPD
aJivM4DAbh456bTq3Jk2ZUw97fTBLAHLPQFr/2sY6bmhncTHlx/hRUp2DKXcBccI
Zxl/0SuBiEAfFZuIW3hOS7gnoT409z9f7yKsrw+WrLjKiqziOle5Ck7u+EBJn75y
XyKEtRmzaMt/OvQGUV2WNErqZgnoq54/WZwTvlglIeTrK9t8q5KE80ybWthbdLpK
qtaIgPNN/mvX12Xbnhr6dqN1s7VHOZvjLzFu7j/9RrT90XHHTWo9P6GfNTzJkIWC
X+pakY2y+QJXcZhGk3Y7asWX/GGOvbhWnlHIpVsESK2JH5e2YFKusjyW2wTzaNQ6
aBSC+3QwxYVVSsETXR8cC4AaCueRmhmOOGC7gDYFLyKroEFbX4Ii9TllDV6z67Os
hFE3fhGDcoGdi4Hcs4mFUIgGE1TeD9XpogMSi2uXiZylUEaOKsg4spzuiuqI+YLi
8JqcuZ6rQVJ4j1MH95uGuwFzdIIupFLXAZ4NGLz+2Lia+nmq5e08FjVZ+0zb8cnw
17rLIBMwEgEyu2r5pq4ObToGuWvRIcaFOe7bhBNm9ZYR1DUVzD+hJ4XQa5jhi23C
s2bdlE5mbHOLUuNuOm50
=6zQ2
-----END PGP SIGNATURE-----
Now verify the message.
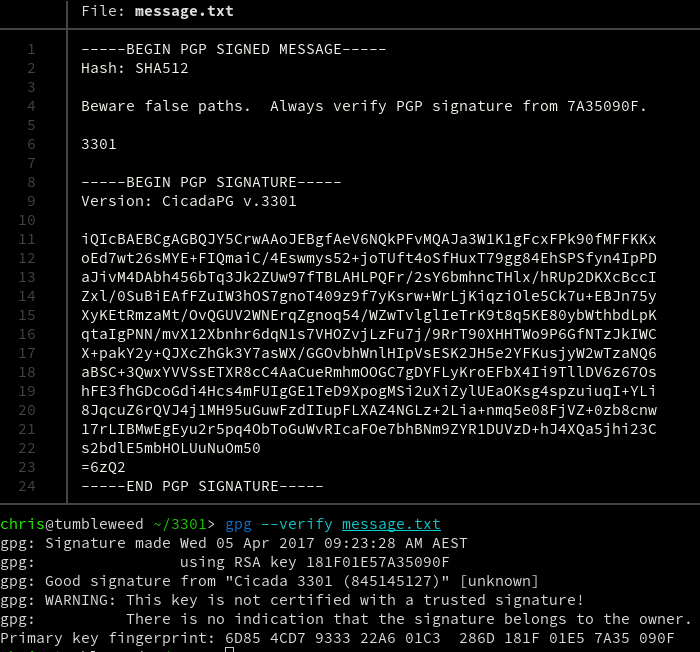
As you can see, the message has been verified with the Cicada 3301 key we imported – April 5, 2017.
Note, the original Cicada PGP message was posted April 4, 2017, however the date presented for verification will vary depending on your timezone.
Moving on.
To show how a message that has been tampered with may fail verification, we will add some random text into the message.
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA512
Beware false paths. Always verify PGP signature from 7A35090F.
THIS
TEXT
SHOULD
NOT
BE
HERE
SIGNED
Cicada 3301
-----BEGIN PGP SIGNATURE-----
Version: CicadaPG v.3301
iQIcBAEBCgAGBQJY5CrwAAoJEBgfAeV6NQkPFvMQAJa3W1K1gFcxFPk90fMFFKKx
oEd7wt26sMYE+FIQmaiC/4Eswmys52+joTUft4oSfHuxT79gg84EhSPSfyn4IpPD
aJivM4DAbh456bTq3Jk2ZUw97fTBLAHLPQFr/2sY6bmhncTHlx/hRUp2DKXcBccI
Zxl/0SuBiEAfFZuIW3hOS7gnoT409z9f7yKsrw+WrLjKiqziOle5Ck7u+EBJn75y
XyKEtRmzaMt/OvQGUV2WNErqZgnoq54/WZwTvlglIeTrK9t8q5KE80ybWthbdLpK
qtaIgPNN/mvX12Xbnhr6dqN1s7VHOZvjLzFu7j/9RrT90XHHTWo9P6GfNTzJkIWC
X+pakY2y+QJXcZhGk3Y7asWX/GGOvbhWnlHIpVsESK2JH5e2YFKusjyW2wTzaNQ6
aBSC+3QwxYVVSsETXR8cC4AaCueRmhmOOGC7gDYFLyKroEFbX4Ii9TllDV6z67Os
hFE3fhGDcoGdi4Hcs4mFUIgGE1TeD9XpogMSi2uXiZylUEaOKsg4spzuiuqI+YLi
8JqcuZ6rQVJ4j1MH95uGuwFzdIIupFLXAZ4NGLz+2Lia+nmq5e08FjVZ+0zb8cnw
17rLIBMwEgEyu2r5pq4ObToGuWvRIcaFOe7bhBNm9ZYR1DUVzD+hJ4XQa5jhi23C
s2bdlE5mbHOLUuNuOm50
=6zQ2
-----END PGP SIGNATURE-----
Now try to verify the message.
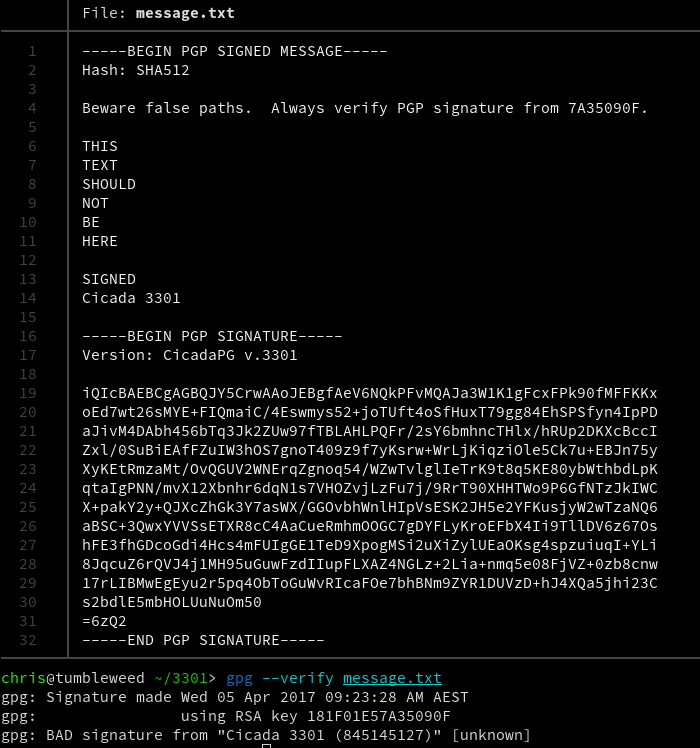
You can see the verification now fails because the original signed message has been tampered with.
So how do you spoof the verification?
If you edit only the third line of the message it will create a false-positive spoof.
-----BEGIN PGP SIGNED MESSAGE-----
Hash: SHA512
THIS TEXT SHOULD NOT BE HERE SIGNED Cicada 3301
Beware false paths. Always verify PGP signature from 7A35090F.
3301
-----BEGIN PGP SIGNATURE-----
Version: CicadaPG v.3301
iQIcBAEBCgAGBQJY5CrwAAoJEBgfAeV6NQkPFvMQAJa3W1K1gFcxFPk90fMFFKKx
oEd7wt26sMYE+FIQmaiC/4Eswmys52+joTUft4oSfHuxT79gg84EhSPSfyn4IpPD
aJivM4DAbh456bTq3Jk2ZUw97fTBLAHLPQFr/2sY6bmhncTHlx/hRUp2DKXcBccI
Zxl/0SuBiEAfFZuIW3hOS7gnoT409z9f7yKsrw+WrLjKiqziOle5Ck7u+EBJn75y
XyKEtRmzaMt/OvQGUV2WNErqZgnoq54/WZwTvlglIeTrK9t8q5KE80ybWthbdLpK
qtaIgPNN/mvX12Xbnhr6dqN1s7VHOZvjLzFu7j/9RrT90XHHTWo9P6GfNTzJkIWC
X+pakY2y+QJXcZhGk3Y7asWX/GGOvbhWnlHIpVsESK2JH5e2YFKusjyW2wTzaNQ6
aBSC+3QwxYVVSsETXR8cC4AaCueRmhmOOGC7gDYFLyKroEFbX4Ii9TllDV6z67Os
hFE3fhGDcoGdi4Hcs4mFUIgGE1TeD9XpogMSi2uXiZylUEaOKsg4spzuiuqI+YLi
8JqcuZ6rQVJ4j1MH95uGuwFzdIIupFLXAZ4NGLz+2Lia+nmq5e08FjVZ+0zb8cnw
17rLIBMwEgEyu2r5pq4ObToGuWvRIcaFOe7bhBNm9ZYR1DUVzD+hJ4XQa5jhi23C
s2bdlE5mbHOLUuNuOm50
=6zQ2
-----END PGP SIGNATURE-----
Now try to verify the message.
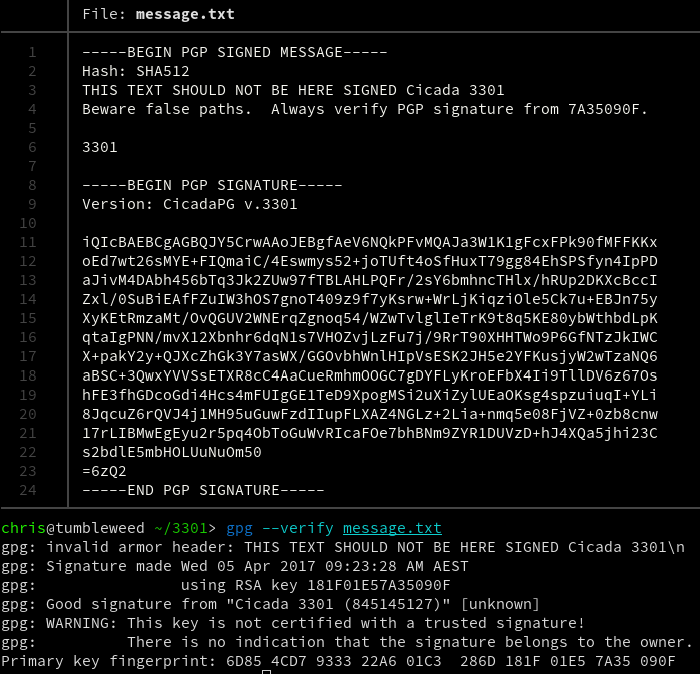
The key to understanding what is really happening is found inside the verbose output.
The verbose output suggests that the message may actually be authentic and has passed verification.
But look closer at the line that says:
gpg: invalid armor header: THIS TEXT SHOULD NOT BE HERE SIGNED Cicada 3301\n
This single line could easily go unnoticed.
However, it is significant because it’s actually the key indicator which is telling you that the original signed message has been tampered with, despite the verbose output that follows the warning which falsely indicates that it has passed verification.
Most people do not know or understand this and will only see the output which says it has passed verification.
This, generally speaking, will be being enough for most people to be satisfied the message is authentic.
This is false-positive spoofing.
One might ask, how is this even important?
It's important, in my view, because if any PGP message was intercepted prior to distribution it could theoretically be spoofed as a false-positive and then the spoofed message distributed in its place.
To most people who really don't know any different, it would simply be interpreted as authentic.
Subscribe to my newsletter
Read articles from Chris McGimpsey-Jones 🏴☠️👻 (@cipheranarchist) directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
