Password Reset Token Leak via X-Forwarded-Host
 Saajan Bhujel
Saajan Bhujel
Hi everyone,
I am Saajan Bhujel.
Student of Bachelor of Commerce(B.Com) and also I am a Bug Bounty Hunter.
This is my 1st blog, if you find any spelling mistakes, so please bear with me for the next few minutes. And this blog is about a vulnerability that, I was able to find in the Hackerone’s private program which allows me to take over any user’s account. But before starting this blog I would like to give a piece of small basic information about the Host header.
What is the HTTP Host header?
The HTTP Host header is a mandatory request header as of HTTP/1.1. It specifies the domain name that the user wants to access.
For example, if a user visits https://example.com, then their browser will make a request containing a Host Header as below:
GET / HTTP/1.1
Host: example.com
Now let’s start the blog…

Some days ago I got a notification in Hackerone that said that I had been invited into a private program. So I accept that invitation and start hunting on that Private Program. And in the starting of hunting on that private program, I spend 5–6 days finding Cross-Site-Scripting(XSS), IDOR, SQL injection, Flaw on the login page, Information Disclosure, and Subdomain takeover but still, I was not able to find anything.

After taking some hours of break, again I start hunting on that domain but this time I got an interesting functionality which I did not saw at last time. And that interesting functionality is Password Reset functionality. So I thought to myself let's play with this Password Reset functionality.

I can’t disclose the name of the target because it's a private program. So, Let’s suppose that the target is site.com. And their password reset functionality is something like this:
And I noticed that whenever we enter our email and click on reset password. we got an email for changing the password with a password reset token link.
Password Reset Token link looks like this:
https://site.com/action-token?key=eyJhbGciOiJIUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICIzZWM2ODU2Z
This time I decided to intercept the password reset request and I also started my ngrok server.
The original request is something that looks like this:
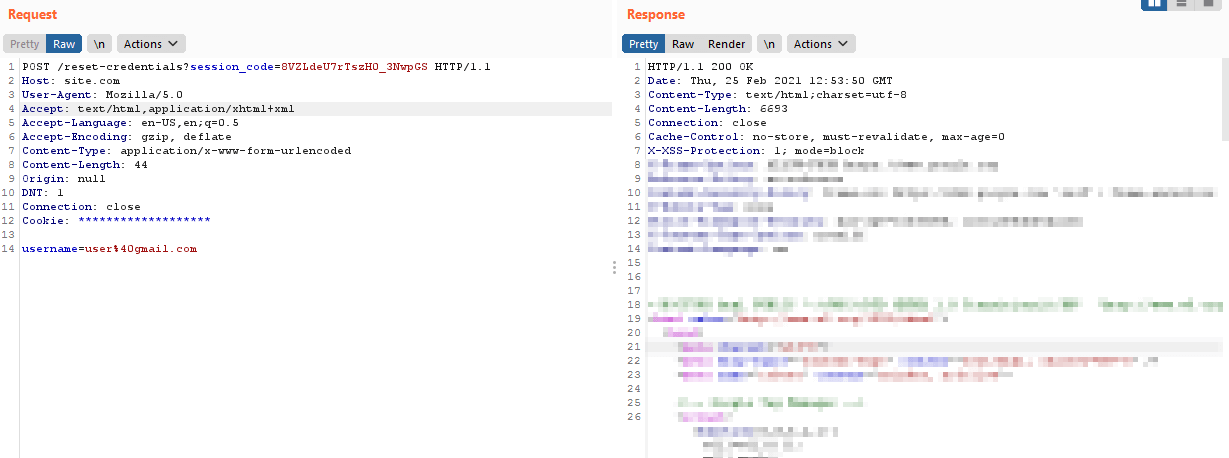
Then I added another header “X-Forwarded-Host” with my ngrok server domain in the original request. So now the modified request is something that looks like this:
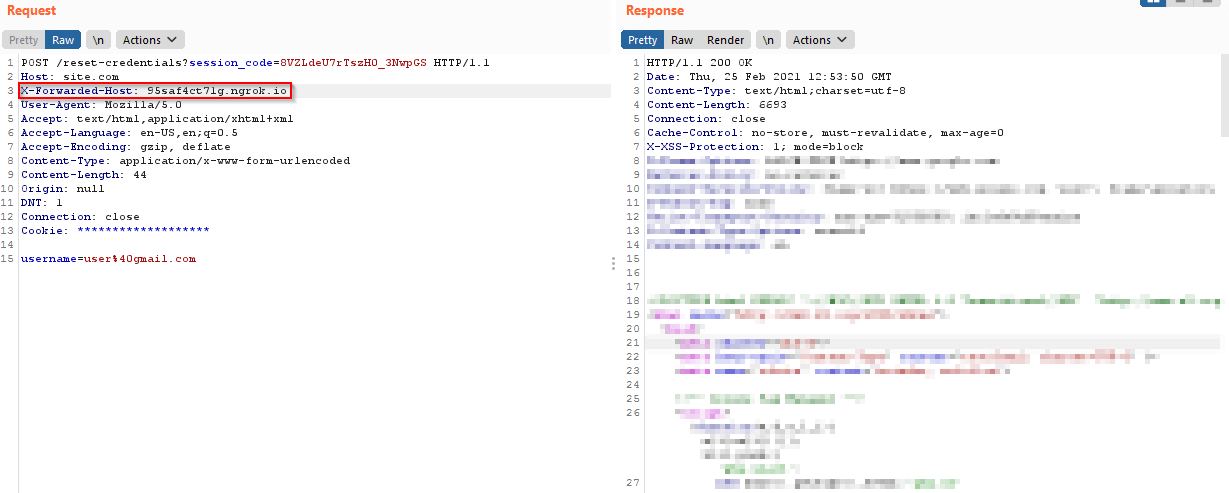
Now this time I got an email for changing the password but with my ngrok server domain. And the password reset token link looks like this:
https://95saf4ct71g.ngrok.io/action-token?key=wia2lkIiA6ICciOiJIUzI1NiIsInR5cCIgODU2ZeyJhbGiA
You also can see, I am successfully able to change the Host by simply adding the header “X-Forwarded-Host” in the password reset request.
Then I noticed that If I enter the victim’s email in the password reset page and also intercept that request and if I add another header “X-Forwarded-Host” with my malicious domain. Then victim will get an email of the password reset token link with my malicious domain. And when the victim clicks on that link he will redirect to my website and his all token will leak to me. Then I can change the victim’s password by using his leaked token. Yeah, the Impact of this vulnerability is a full account takeover.
So now I can fully take over anyone’s account who has an account on site.com by resetting their password.

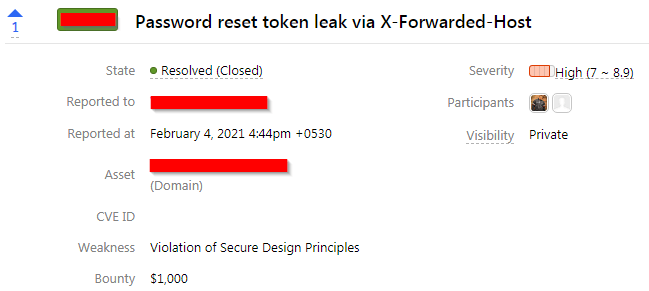
So without wasting any time, I successfully submitted this vulnerability with full proof of concept and then, Hackerone’s private program rewarded me with $1000.
Thank you for reading this blog, and I hope you learn something.
Enjoy your day!….

Subscribe to my newsletter
Read articles from Saajan Bhujel directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Saajan Bhujel
Saajan Bhujel
Hi👋, I’m Saajan Bhujel. I'm a bug bounty hunter👨💻 and I like to secure the web and apps. I’m interested in bug bounty hunting and cybersecurity💻.