Understanding KSI: Keyless Signature Infrastructure
 Shreya Srivastava
Shreya SrivastavaTable of contents

Keyless Signature Infrastructure(KSI) was developed by GuardTime LLC in 2007 with the aim of associating a tag with every digital file/media that would help in verifying and determining the authenticity of the same.
To understand KSI we must first understand the following terms:
- Hashes
- Merkle Tree
Hashes
Hashes are values obtained by passing data into a hashing function. We can share the hashes for the purpose of verification instead of original data, thereby preventing the data from getting exposed.
SHA256 is the one of the most widely used hashing algorithms. It's hashes consist of 64 hexadecimal characters, 64 x 4 = 256 bits
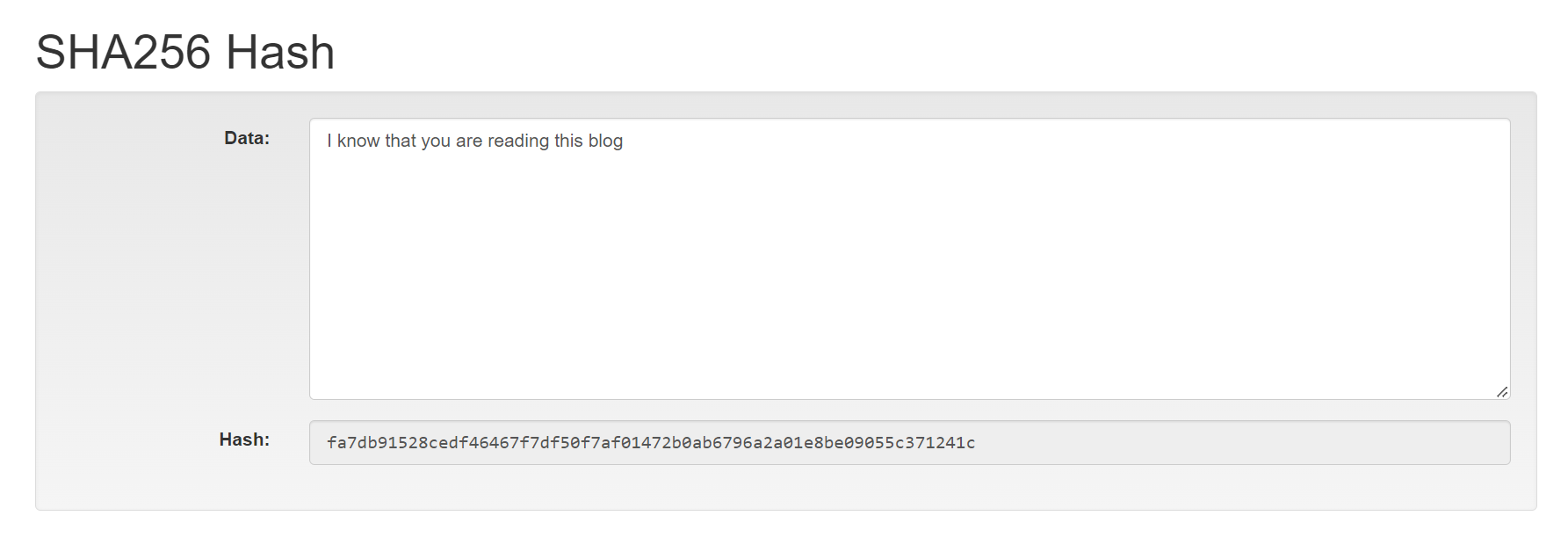
Notice how the hash changes when I simply add an exclamation mark at the end.
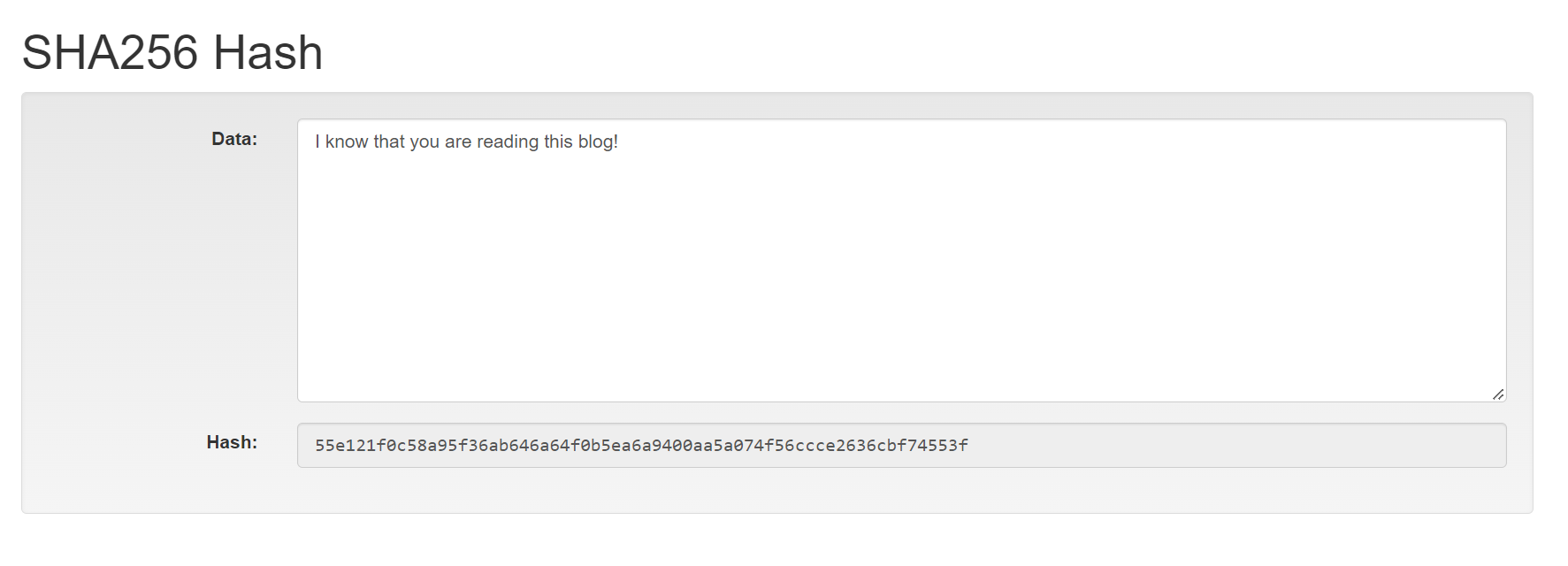
Properties of hash function:
- Deterministic : H(A) = 123 , H(A) = 567
This should not be the case, i.e no matter how many times we pass the same data (here it's A) into the function, we should always get the same hash.
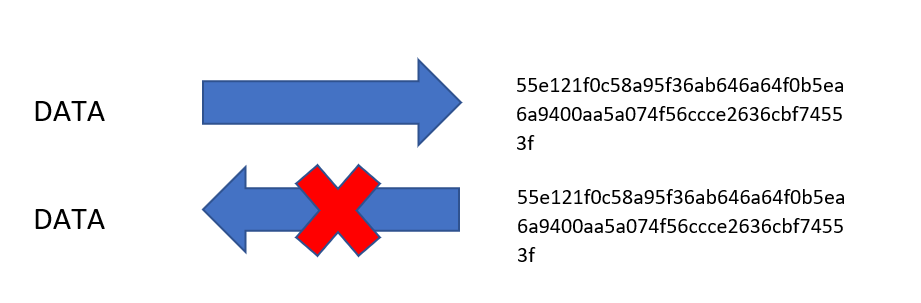
- One-way: Once data is encoded in the form of a hash, it cannot be obtained back via the hash.
Merkle Trees
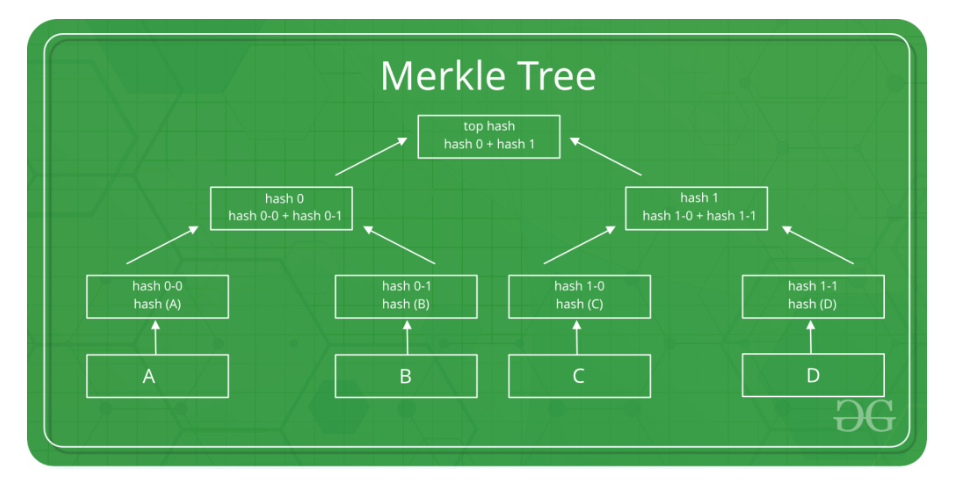
It is a tree data structure where each non-leaf node is a hash of it’s child nodes. All the leaf nodes are at the same depth and are as far left as possible. It maintains data integrity by making use of hash functions.
In this tree, the root hash is considered as the fingerprint of the entire data. So, if we want to know whether the data is compromised, we can check it with the root hash itself instead of having to traverse the entire tree.
Alright! Now that we have covered all the pre-requisites, we can finally jump onto KSI.
Understanding KSI
KSI is a blockchain technology that provides massive scale data authentication without the reliance on centralized authorities. It solely relies on the security of hash functions and the blockchain.
With the help of KSI or Keyless Signature Infrastructure we eliminate the need of symmetric or asymmetric keys for the purpose of verification. KSI only makes use of hashes, so to verify whether the given data is the original data, all we'd need to do is hash the original file and compare it with that of the given data's and if they match, then the data isn't compromised and we're good to go!
Importance of KSI
Let's look at a few features of KSI blockchain that make it so valuable:
- Scalability: Traditional blockchains grow linearly with the number of transactions whereas KSI blockchain grow linearly with time and independent of the number of transactions.
- Speed: The time to record a particular transaction on a traditional blockchain ranges from minutes to hours while on KSI blockchain, it's a matter of seconds as it has a straightforward mathematical process for generating digital signatures.
KSI Vs PKI
PKI stands for public key infrastructure and it involves the use of asymmetric keys(public and private keys). The public key can be shared with everyone and the private key must remain private to the client. If the private key is compromised then the PKI digital signature must be revoked. Such a case would not take place under KSI.
KSI maintains integrity while PKI maintains confidentiality.
Bitcoin Vs KSI
Bitcoin pushes the contents of a transaction onto the ledger to record it. This helps the other nodes on the blockchain to view the transactions and prevent 'double spending'. The transaction contents must necessarily be made public which dramatically increases the size of the ledger, i.e., the ledger size scales linearly with the number of transactions. Also, for the 'proof-of-work', the miners have to solve a mathematical puzzle that consumes a lot of time.
KSI was patented two years before Bitcoin came into picture and is focused more on the integrity of processes, supply chains and the authenticity of digital data. It does not expose client data to a large number of entities.
A KSI client submits the hash of the data (SHA 256 or SHA 3 currently supported) through a Merkle Tree that passes the identity of the requester from known credentialed permissions and from there to the ledger once per second to integrate the hash, time (via a hash calendar) and identity by creating a 2-3Kbyte signature cryptographically linking the underlying data.
Thus, in the future, the original data and its associated signature can verify that the data was part of the published calendar and therefore it existed in the original form at that time identified in the signature. These signatures can be processed at a rate of billions per second, sufficient to cover all the data generated in the world within one second.
To sum up the comparison:
- Bitcoin exposes transaction content to the world whereas KSI only exposes an irreversible hash value to anyone wishing to inspect it or validate authenticity.
- Bitcoin requires minutes to process one transaction while KSI can process billions per second.
- The KSI ledger scales at a constant rate of approximately 2GB per year whereas the Bitcoin ledger grows with the number of transactions and is already on the order of 20-30GB.
Conclusion
The value of KSI digital signatures is in how it is applied to solve a customer’s problem. The KSI signing and verification process currently in use today, is scalable and controlled and easily integrated in systems for interoperability and thus, can be used to mitigate insider threats, frauds and unwanted data loss.
Subscribe to my newsletter
Read articles from Shreya Srivastava directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Shreya Srivastava
Shreya Srivastava
I'm passionate about back-end development, web development and love solving real-world problems using my coding skills. I keep exploring new technologies as I don't want to limit myself to one domain.