Container Deep Dive 1: Container Runtime
 Tobias Haindl
Tobias Haindl
Containerization technologies stand upon the shoulders of giants.
Several building blocks are needed to make Docker, Kubernetes and co as powerful as they currently are.
In this series I want to explore each layer of those tools individually.
We will start at the bottom with Container Runtimes and move upwards to higher abstraction layers.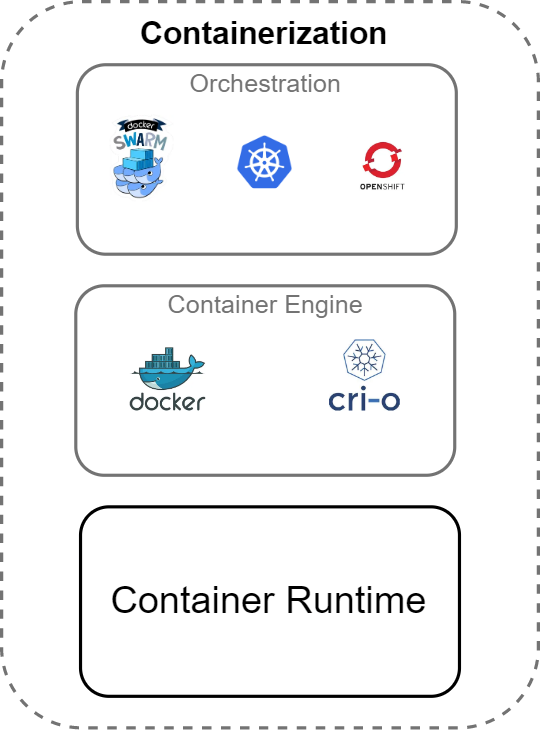
Container Runtime
A Container Runtime provides an execution environment for processes in an isolated manner (a container).
The most common Container Runtimes follow the Open Container Initiative (OCI) Runtime Specification.
- What is the purpose of this specification?
- What does it include?
Open Container Initiative Runtime Specification aims to specify the configuration, execution environment, and lifecycle of a container.
Source
A detailed specification exists for different platforms (Linux, Windows etc.).
The Linux specification for example includes:
- available Namespaces
- available File systems
- available Devices
Let’s have a look at three prominent Container Runtimes:
- runc
- crun
- gVisor (runsc)
runc
Is a low level CLI capable of spawning and managing containers compliant with the OCI Runtime Specification.
It is written in Go and a project of the OCI.
Since it takes care of low level interactions it is not recommended to use runc directly.
…unless there is some specific use case that prevents the use of tools like Docker or Podman, it is not recommended to use runc directly.
Source
So if you want to build the next Docker, feel free to use it directly :)
runc is currently used by Docker as a default Container Runtime and can be used with Podman & Kubernetes as well.
crun
crun basically solves the same problem as runc: creation and management of the actual container instances.
Of course it also fully implements the OCI Runtime Specification.
crun is written in C and promises a lower memory footprint and better performance.
crun is used by default by Podman and can be used with Docker & Kubernetes as well.
gVisor (runsc)
gVisor is all about security. It includes a container runtime matching the OCI Runtime specification called runsc.
For improved security, containers created by gVisor are sandboxed which leads to better isolation between your containers and the host system.
Only a limited surface of the host kernel is available for the container and calls to it are intercepted and monitored for suspicious activities.
gVisor is written in Go and maintained by Google.
runsc can be used with Docker & Kubernetes.
Summary
In this article we had a look at the most basic building block of any modern Containerization tool. We briefly touched the Container Runtime Specification from the Open Container Initiative and compared three different implementations of the specification.
In the next article we will explore Container Engines!
Subscribe to my newsletter
Read articles from Tobias Haindl directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
