How to Implement FSLogix Profile Containers in AVD
 Ash Roberts
Ash Roberts
Background
In the first article we built an Azure Virtual Desktop lab that consisted of cloud only infrastructure. We deployed Storage accounts ready for FSLogix profile containers and we created an instance of Azure Active Directory Services (AADDS) so we can use domain join/NTFS and other benefits we would get if we had synced an on premise domain via AD Connect.
We then deployed a host pool with a session host via the "create a host pool" wizard
If you missed that article or need a reference of what's been deployed or a refresher you can check the link out below!
https://switchitup.tech/setting-up-an-azure-virtual-desktop-lab
Other articles:
How to connect to Azure Virtual Desktop:
https://switchitup.tech/how-to-connect-to-azure-virtual-desktop-session
Lockdown AVD with Conditional Access
https://switchitup.tech/lockdown-avd-with-conditional-access
Introduction
This post is going to look at how to implement FSLogix Profile Containers within our AVD lab. We have actually covered some of the pre-requisite setup when we setup the AVD lab in my first post. I will quickly review what we already have in place:
A storage account with a "fslogix-profiles" file share.
The file shares in our storage account are joined to Azure Active Directory Domain Services
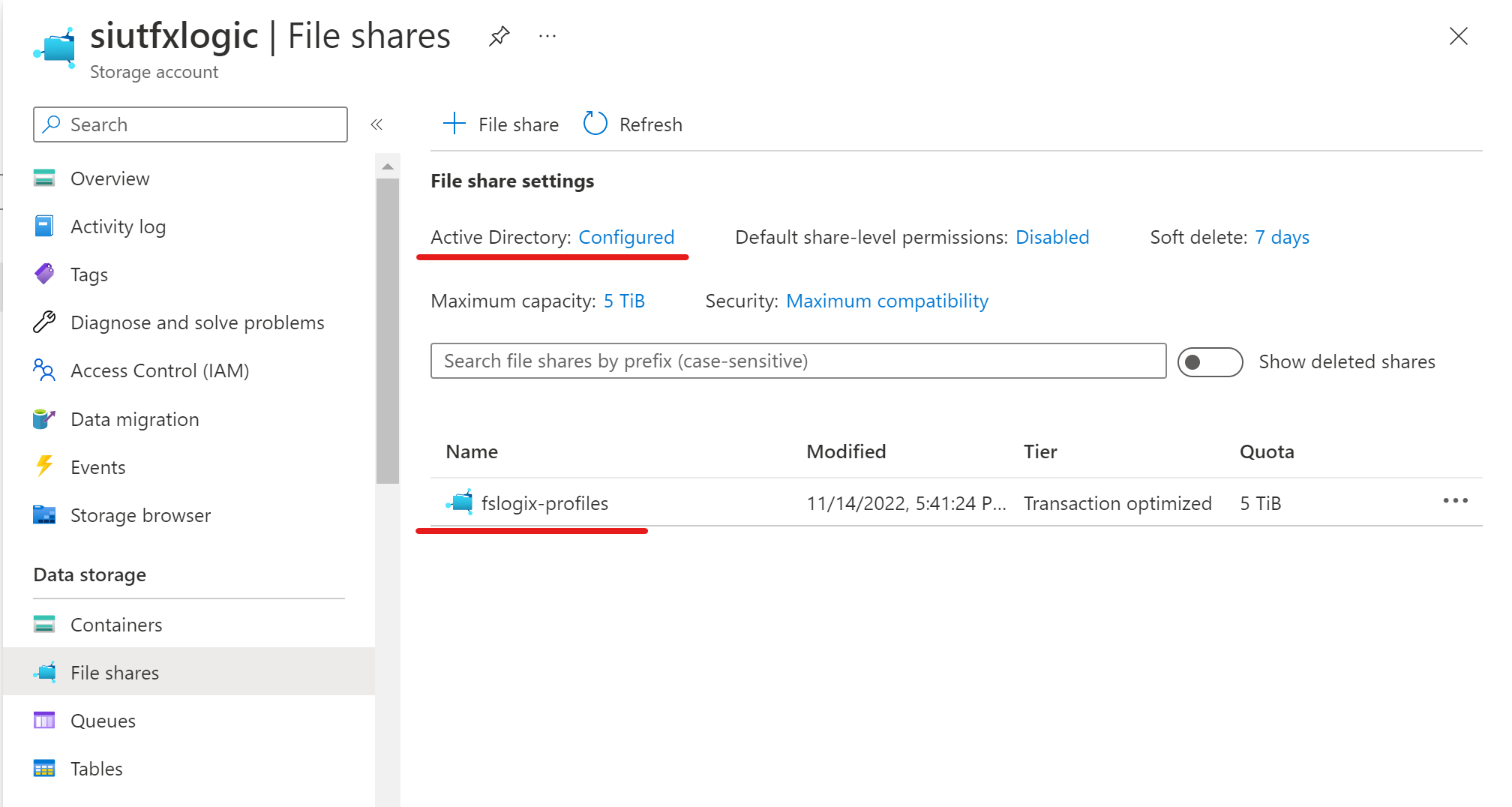
- We have a security group in Azure Active Directory called "FSLOGIX-Profiles" and this is applied to a user account called "Testuser1"
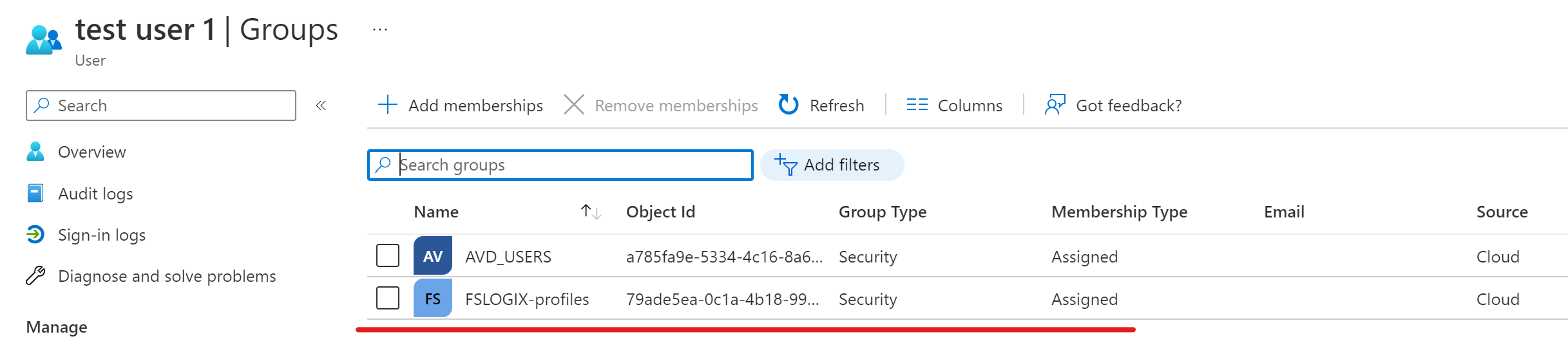
As another reminder we are using windows 10 multi session that comes with FSlogix pre-installed, if you are using a custom image you will need to install the FSLogix Agent, more information on that here:
https://learn.microsoft.com/en-us/azure/virtual-desktop/fslogix-profile-container-configure-azure-files-active-directory?tabs=aadds
For more detail on the steps previously completed above view my first post:
https://switchitup.tech/setting-up-an-azure-virtual-desktop-lab
What is FSLogix?
FSLogix enhances and enables user profiles in Windows remote computing environments. FSLogix may also be used to create more portable computing sessions when using physical devices. User profiles are stored in VHD files that get attached to the users AVD session.
FSLogix includes:
- Profile Container
- Office Container
- Application Masking
- Java Version Control
FSLogix allows you to:
- Roam user data between remote computing session hosts
- Minimize sign in times for virtual desktop environments
- Optimize file IO between host/client and remote profile store
- Provide a local profile experience, eliminating the need for roaming profiles.
- Simplify the management of applications and 'Gold Images'
- Specify the version of Java to be utilized by specific URL and applications
You are eligible to use FSLogix if you have one of the following licenses:
- Microsoft 365 E3/E5
- Microsoft 365 A3/A5/ Student Use Benefits
- Microsoft 365 F1/F3
- Microsoft 365 Business
- Windows 10 Enterprise E3/E5
- Windows 10 Education A3/A5
- Windows 10 VDA per user
- Remote Desktop Services (RDS) Client Access License (CAL)
- Remote Desktop Services (RDS) Subscriber Access License (SAL)
- Azure Virtual Desktop per-user access license
Information courtesy of Microsoft:
https://learn.microsoft.com/en-us/fslogix/overview
In this post we will focus on the profile container element.
FSLogix Implementation Steps
Setup a Storage account with a fileshare for storage of FSLogix profile containers
Join the storage account to Active Directory or Azure Active Directory Domain Services
Assign RBAC role to users that require FSLogix profile containers
Set NTFS Permissions
Configure session hosts to use profile containers
Validate
we have completed steps 1 and 2 already in our lab setup so we will start with step 3
Assign RBAC role to users that require FSLogix
Users that require the use of FSLogix profile containers need to have the following permissions to be able to acces the fileshare in our storage account:
- Storage File Data SMB Share Contributor
to achieve this we will navigate to our fslogix-profiles fileshare in our storage account:
Storage Accounts > sasiufslogix > File Shares > fslogix-profiles > Access Control (IAM) > Add > Add Role Assignment
Select "Storage File Data SMB Share Contributor" from the roles list:
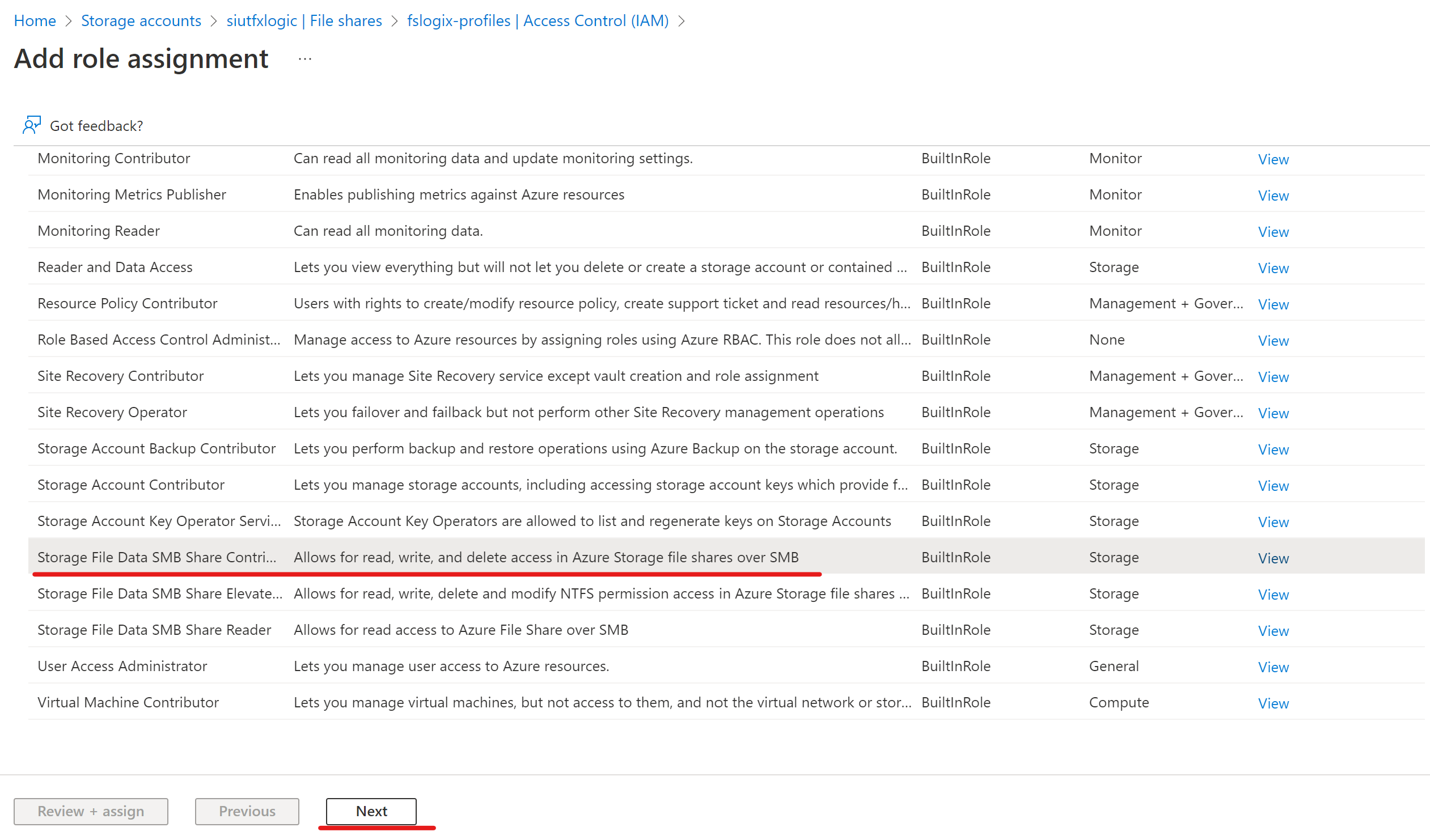
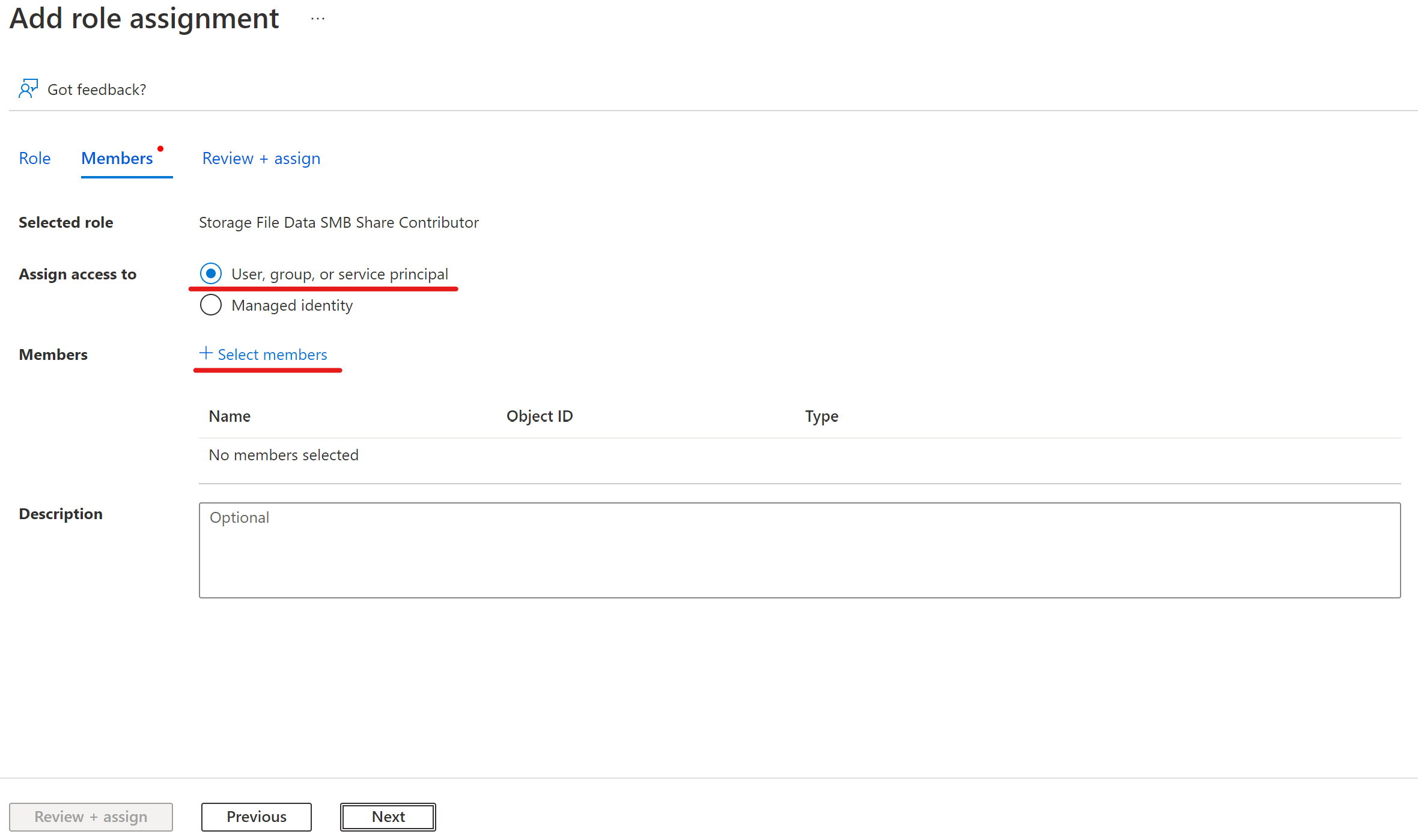
Add the "FSLOGIX-Profiles" security group we created in post 1 to the Storage File Data SMB Share Contributor role. This is alot simpler then adding individual users as new users who need access can just be assigned the security group and you wont need to touch the role assignment settings again.
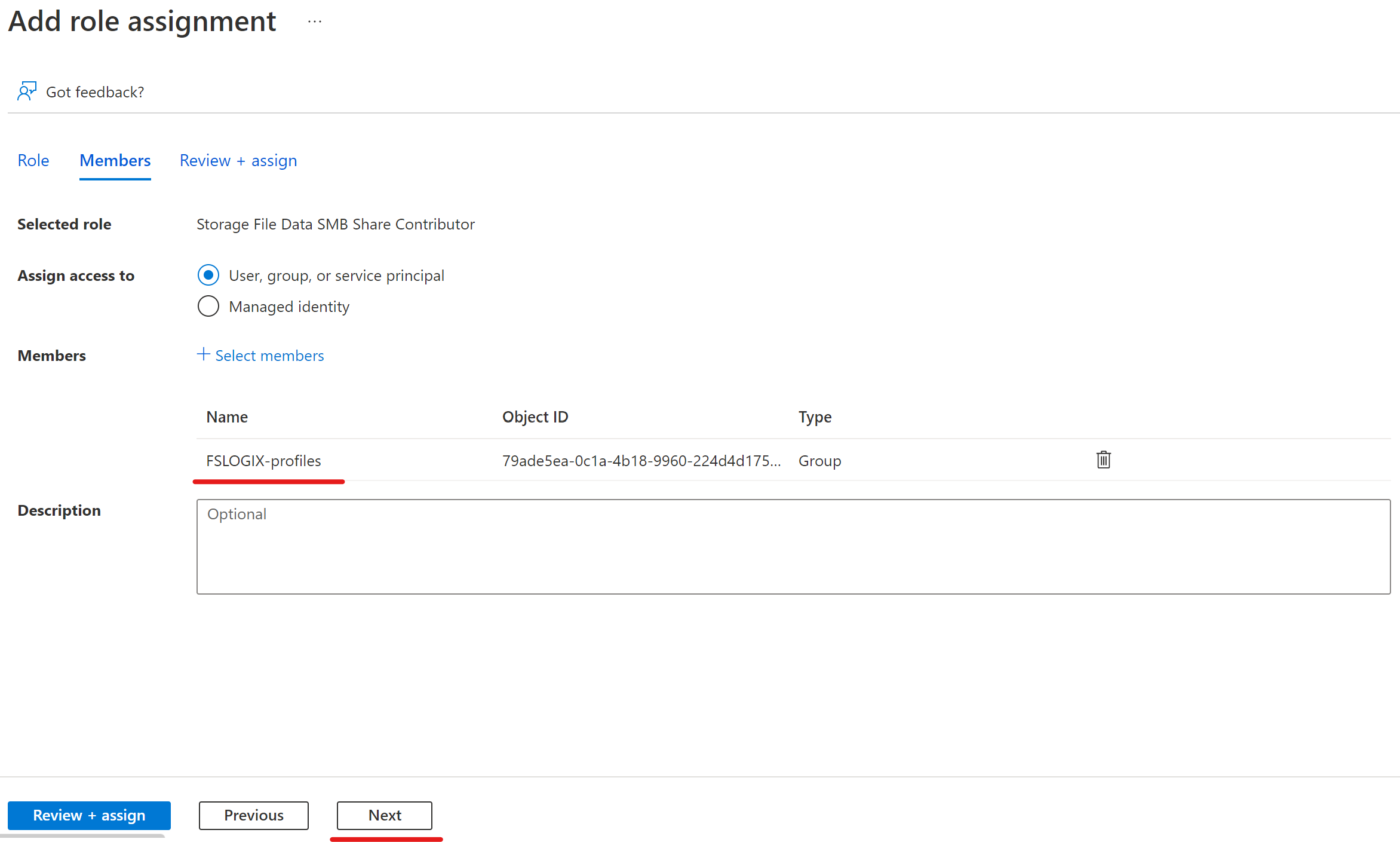
You should end up with the following:
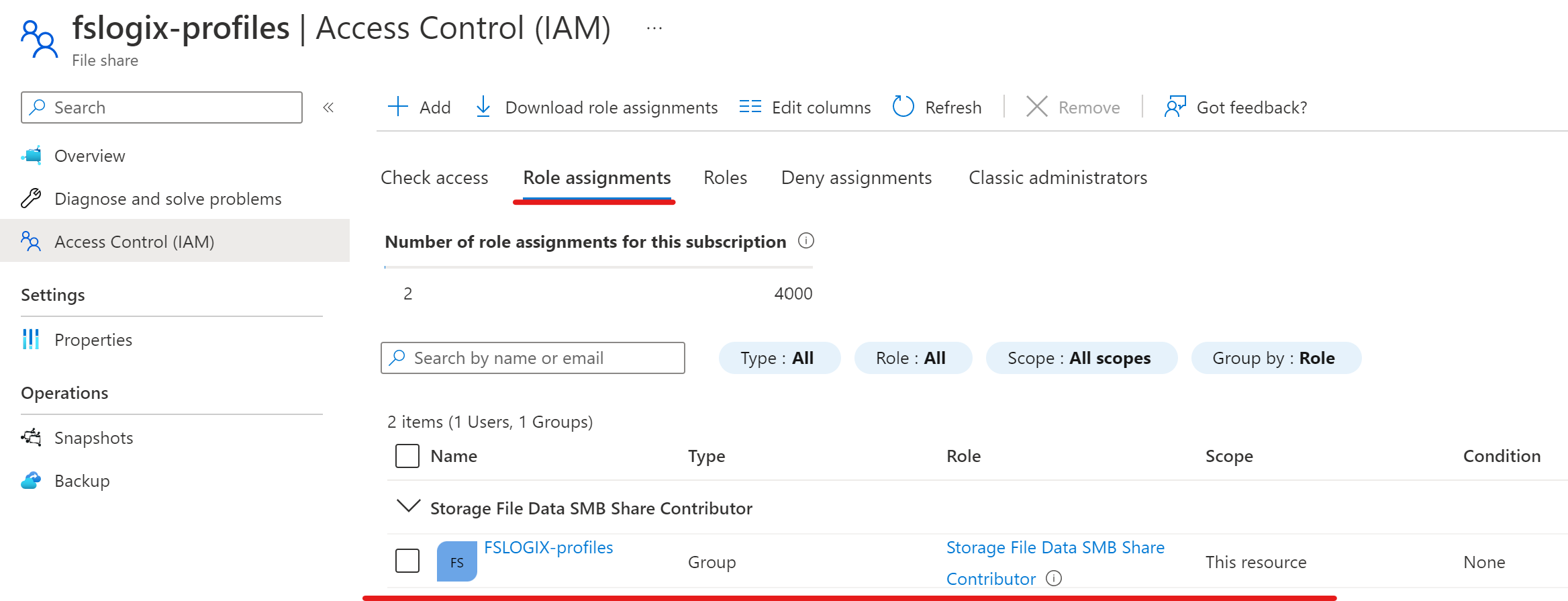
Set NTFS Permissions
We now need to set the NTFS permissions on the share, we do this via CMD/PowerShell in the session host(s).
first, we need to identify the storage account and the file share in Azure and assign it to a drive letter. This is so your session host knows where the profile information will be held. The format of the command for this is below:
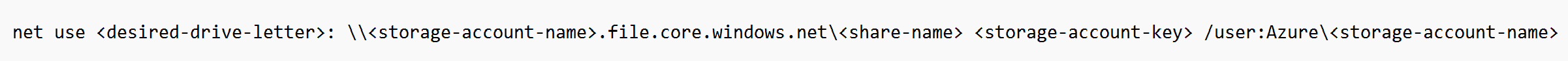
To locate your storage account key navigate to the following in the Azure Portal:
Storage Accounts > Storage account name > Access Keys
On key 1, click show, then copy the key to input in the script.
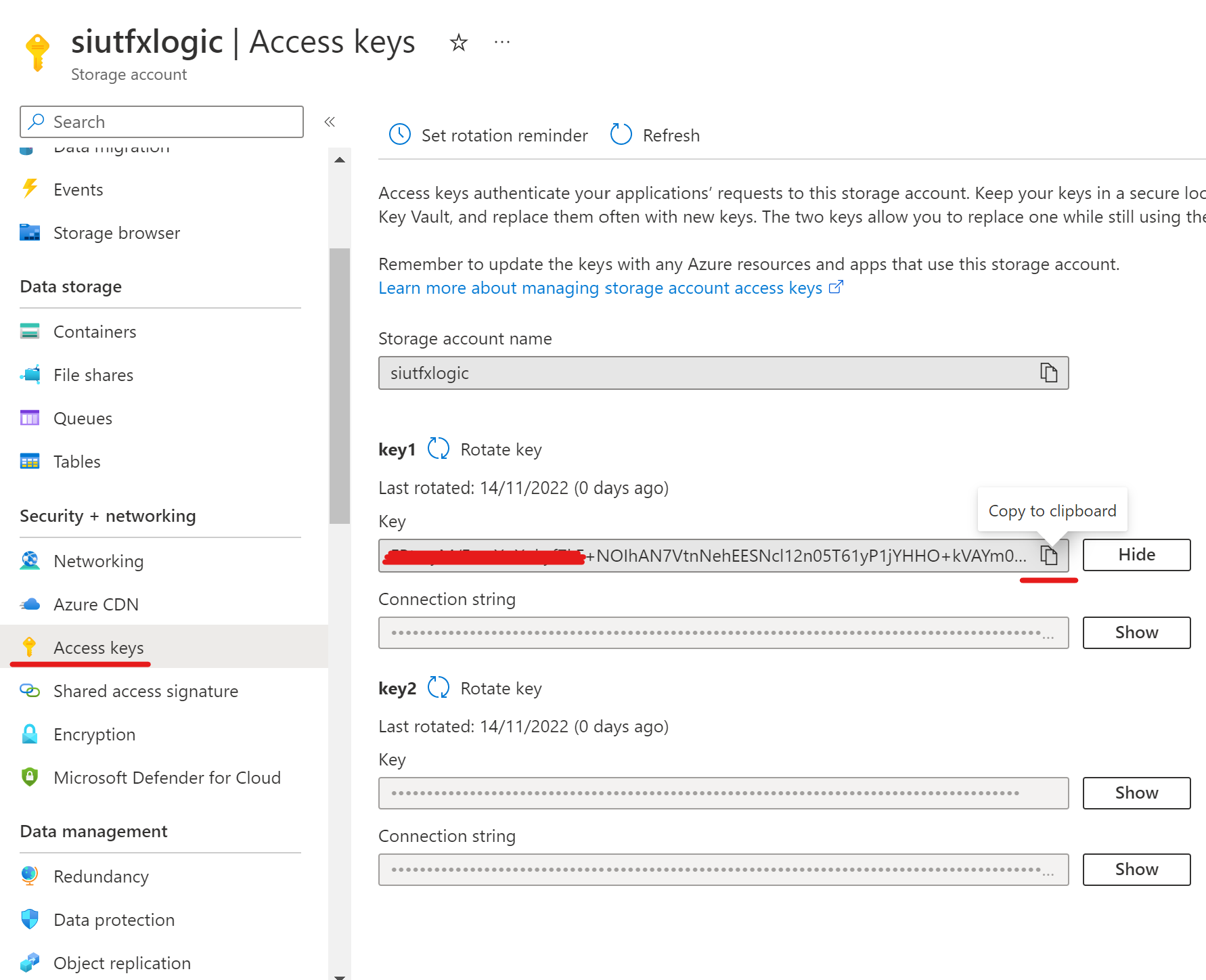
net use p: \\siutfxlogic.file.core.windows.net\fslogix-profiles FBtmyM/FmvXoXukyf7kF+(omitted for security) w== /user:Azure\siutfxlogic
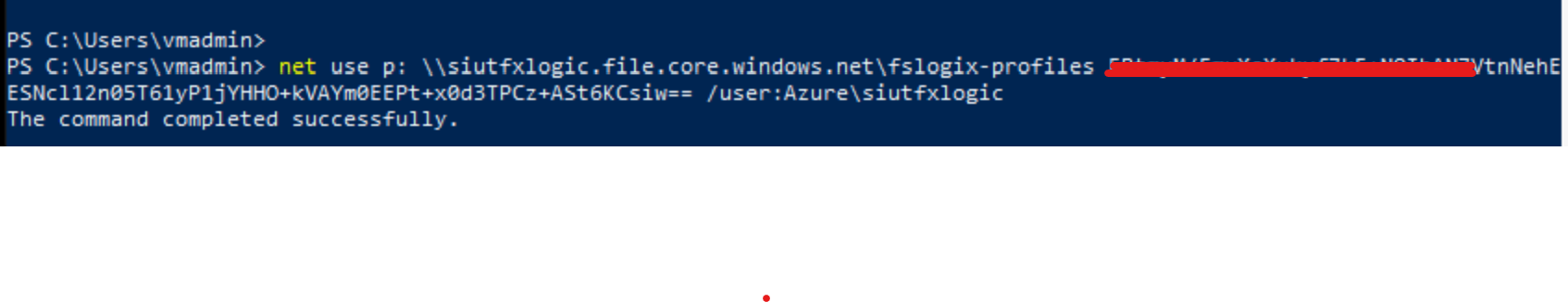
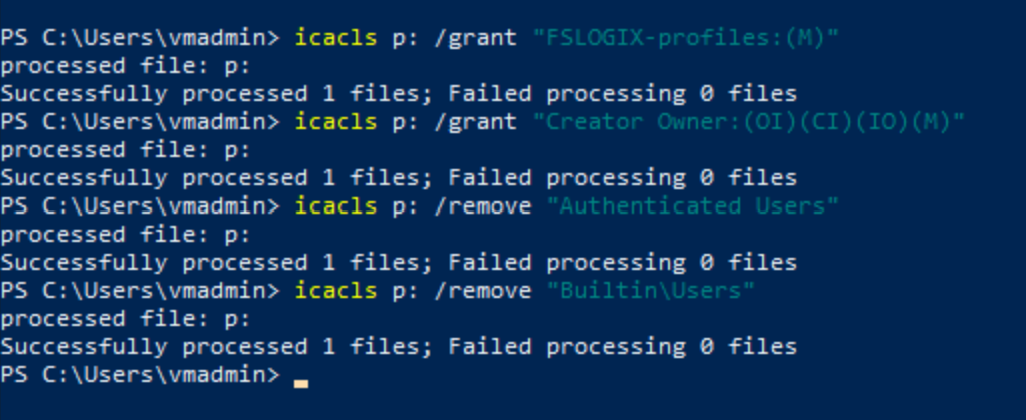
We can now set the NTFS ACLS on the "fslogix-profiles" file share, notice the top line is our security group "FSLOGIX-profiles" we applied to the RBAC role:
icacls p: /grant "FSLOGIX-profiles:(M)"
icacls p: /grant "Creator Owner:(OI)(CI)(IO)(M)"
icacls p: /remove "Authenticated Users"
icacls p: /remove "Builtin\Users"
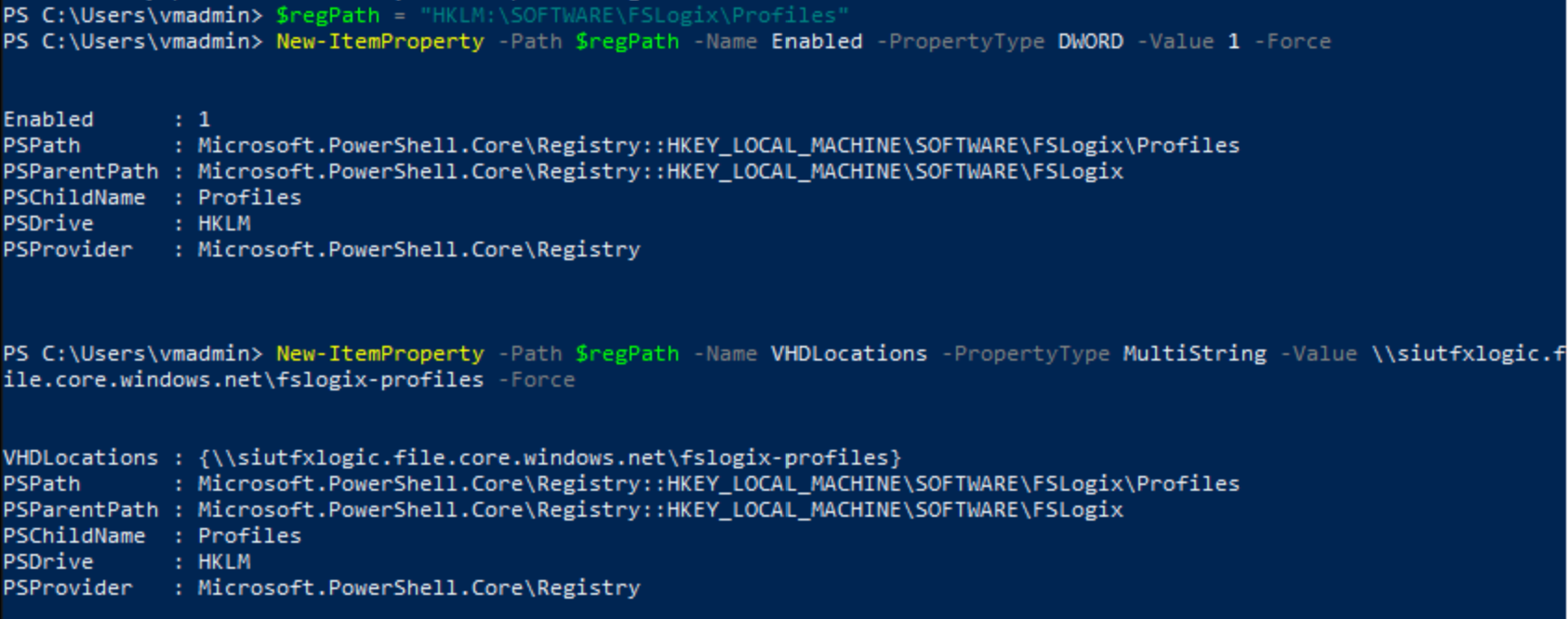
Configure Session Hosts to use Profile Containers
This stage involves editing two registry settings, firstly turning ON profile containers. Secondly, pointing the session host to the profile container share.
VHDLocations = \storage account.file.core.windows.net\File Share
$regPath = "HKLM:\SOFTWARE\FSLogix\Profiles"
New-ItemProperty -Path $regPath -Name Enabled -PropertyType DWORD -Value 1 -Force
New-ItemProperty -Path $regPath -Name VHDLocations -PropertyType MultiString -Value \\siutfxlogic.file.core.windows.net\fslogix-profiles -Force
Once completed and hopefully error free you can restart the session host(s) to apply settings.
Validate
Finally we can test profile containers are now working. Log into your AVD with testuser1 via your remote desktop client or web access. You should see on login when it is applying policies and settings "Applying FSLogix Profile Containers". Once the desktop has loaded, change your desktop background to something of your choosing. In File Explorer create a text file called "Test.txt" in "Documents". Disconnect form the session.
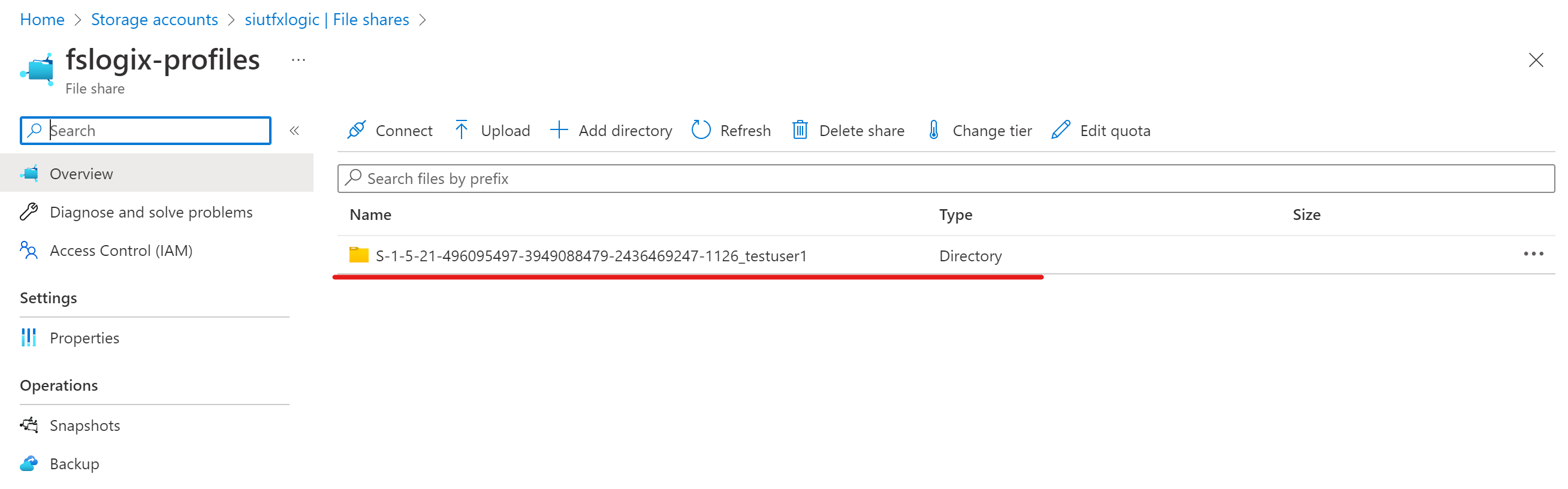
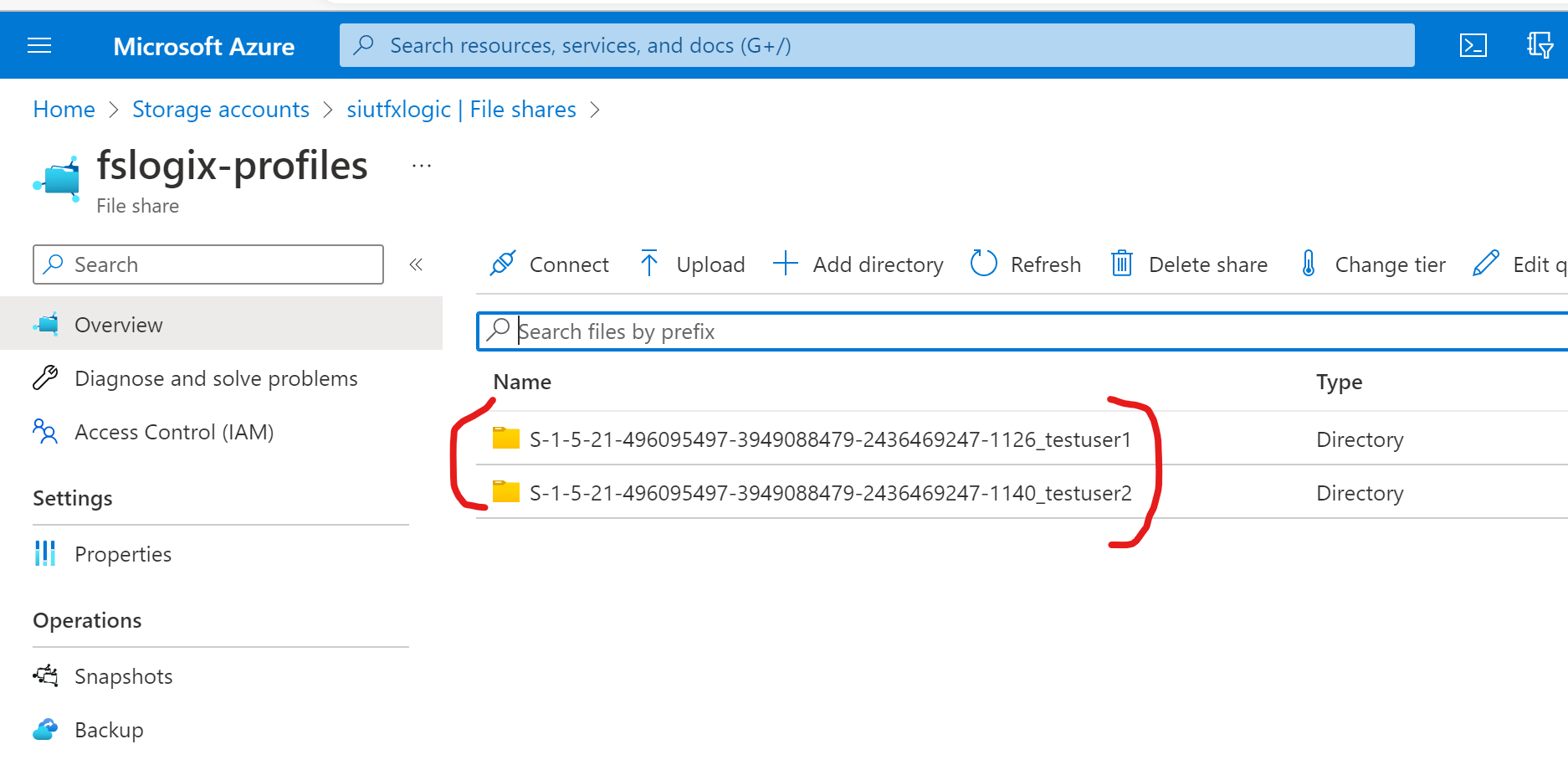
All being correct if we navigate to our "fslogix-profiles" file share we should see the users profile directory created in the format of SID-Username, drill into this and you will see a vhd file:
Now lets create a second user in Azure Active Directory "Testuser2" give them the AVD_Users security group so they can access AVD and FSLOGIX-profiles security group. You may need to set up MFA if you have Conditional Access in place before logging into AVD. Then connect to the AVD environment via Remote Desktop Client.
On login change the desktop and create some files in "Documents" . Disconnect from AVD.
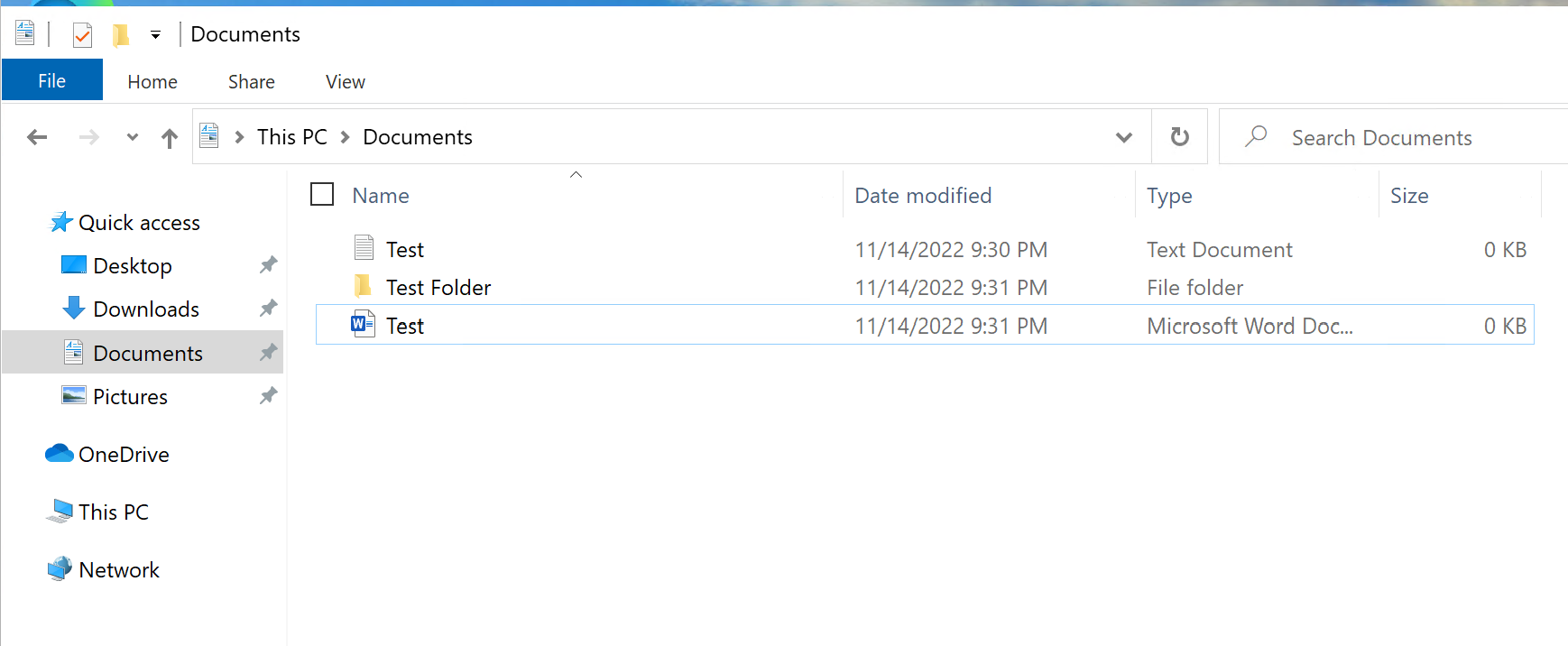
Now log back in as TestUser1 and notice your desktop settings and the test file you created are accessible from "Documents".
Now login as TestUser2, notice again your desktop settings and user documents are available in "Documents".
Verify that TestUser2 profile now exist with TestUser1 in you fslogix-profiles file share.
Summary
Congratulations you we have just configured FSLogix Profile Containers in your AVD environment to store your users profiles centrally via an Azure File Share.
My next article will review "RDP properties" and how you can control what users can do within your VDI environments such as limiting copy and past functionality or passing through users local devices to the VDI environment.
Thanks for reading!
Subscribe to my newsletter
Read articles from Ash Roberts directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ash Roberts
Ash Roberts
I am a technical consultant for a fast growing MSP. Due to the nature of my job I have quite a range of real world experience focusing around server/cloud(Azure) infrastructures, network design, installation and configuration all across multiple vendors such as Microsoft/Cisco/HP Aruba/FortiNet to name a few. All which, I am trying to share with yourselves. Whether you are new to the IT landscape or a veteran I hope there is something for you as my content grows. Currently hold certifications in following: Aruba switching CCNA route and switch CCNA cyber ops CCNA security MCSA windows 10 MCSA server 2016 MCSE core infrastructure Azure Administrator (az104) O365 administrator expert (ms100/101) Modern desktop administrator (md100/101) Hybrid server administrator (az800/801) Azure virtual Desktop specialty (AZ140) So, join me on my learning journey as well as work experience!