How does Akamai deliver and secure web apps and APIs?
 Mike Elissen
Mike Elissen
In 2022, I helped Ludum Dare, the largest online game jam community, improve their web application and API microservices architecture to be better performing, more secure and more scalable. I outlined the 'why' in a previous blog post and today, I will highlight the 'how' it works.
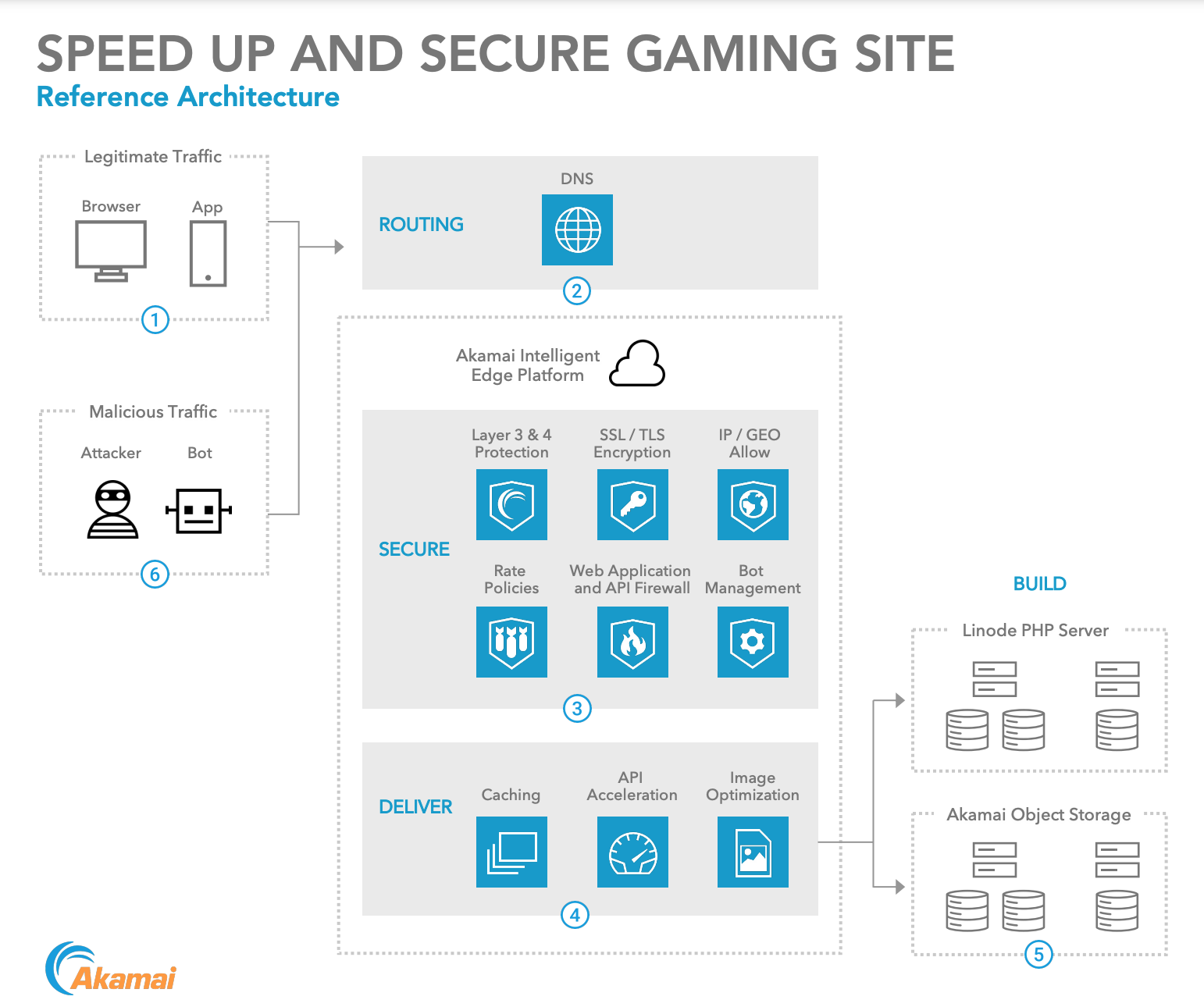
Whenever I consult with a developer to optimize their infrastructure and add new elements, I prefer to create an architecture diagram that showcases all the elements in play, ranging from end-users to server and explain how requests and responses flow across the elements.
When implementing the Akamai solutions on top of leveraging Linode as the origin, Ludum Dare is now also able to offer highly requested capabilities to users — specifically, the ability to directly upload and play games on the site.
I created a video that highlights everything outlined in this blog post as well for those who prefer a visual style.
Ludum Dare is a fantastic reference when it comes to Build, Deliver and Secure with Akamai as Ludum Dare is using key Akamai solutions in each of these areas. We start with the users, the legitimate traffic, that are accessing ldjam.com from their Browsers or Mobile Devices.
Akamai’s Edge DNS handles the DNS query to route the users directly to the Akamai Intelligent Edge Platform. Now, the request is routed to the nearest and best performing Akamai EdgeServer. The Akamai EdgeServer will first go through the ‘Secure’ phase and determine if this is a legitimate request. Akamai’s App & API Protector checks all the mechanisms in play.
The Akamai EdgeServers will determine if the request is a properly formed HTTPS request first. Next it will verify the IP address and country the request originates from. It will also make sure that the IP address is not sending too many requests at once. This is to help protect against large DDoS attacks.
Finally, it will scan the URL, the headers, the cookies and the payload and makes sure that there is nothing harmful, according to our Web Application and API Firewall.
Once the request is determined to be legitimate, the request moves on to the ‘Deliver’ phase. Of course, if the request is not allowed, protections will kick in and users will receive an error message instead.
In the ‘Deliver’ phase, the Akamai EdgeServer inspects the request to see what type of content is needed. If the request is for static assets such as an HTML, JavaScript, CSS files or even a game build, the EdgeServer will check its cache. If it is in cache, it will be directly served to the user which significantly speeds up the performance.
If the content is not yet in cache, it will ask its friendly neighboring EdgeServers for the content and once the EdgeServer gets it, it will place it inside the cache as well. This is what powers the Akamai Content Delivery Network and ensures content can get delivered to millions of users all at once, all around the world.
If the request is not something that can be cached, like a login for instance, this dynamic content request will be routed towards Ludum Dare’s cloud computing infrastructure which is powered by Linode.
The optimized routing towards Linode should help speed up the request. The Linode PHP server will handle the request properly and return a HTTPS response to Akamai which will be forwarded towards the user. Of course, for hackers, requests that fail to pass any of the inspections will simply be blocked by the Akamai Intelligent Edge Platform.
To prevent hackers/threat actors from bypassing Akamai and attacking Linode servers directly, Akamai controls all DNS routing and hides the original hostnames and IP addresses. Linode servers rely on a feature called Akamai Site Shield which only allows Akamai IP addresses to access the servers.
This is how the flow between users, Akamai EdgeServers and the Linode Cloud Computing works.
If you are interested in learning more about this developer use case, consider watching the video series I have created. You can find on the Akamai Developer YouTube.
For more insights from Mike Kasprzak, who manages Ludum Dare, please read or watch the interview where he shares more insights on why he chose for Akamai and Linode.
And finally, the full reference architecture can be found on the Akamai website.
Join me again in 2 weeks, where I will showcase how you can easily replicate the entire Ludum Dare architecture with the help of Terraform and reusing the Infrastructure as Code template that I created for this use-case. It will help spin up a Linode server and add the Akamai CDN and Application Security configurations and get you started!
Subscribe to my newsletter
Read articles from Mike Elissen directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Mike Elissen
Mike Elissen
In today's world, it is difficult to stay secure with your applications, APIs and data. I can help you. Mike Elissen, Developer Advocate @ Akamai Technologies.