Intune: Setting up a Device Enrollment Status Page
 Ash Roberts
Ash RobertsTable of contents
Introduction
So, you have configured Windows Autopilot and have tested your deployment profile works as intended on your enrolled machine. But you can't see any indication of your deployment in progress during testing or if anything has failed. Then an Enrollment Status page (ESP) is for you!
This can be found in your endpoint portal under:
Windows enrollment > Device Enrollment page
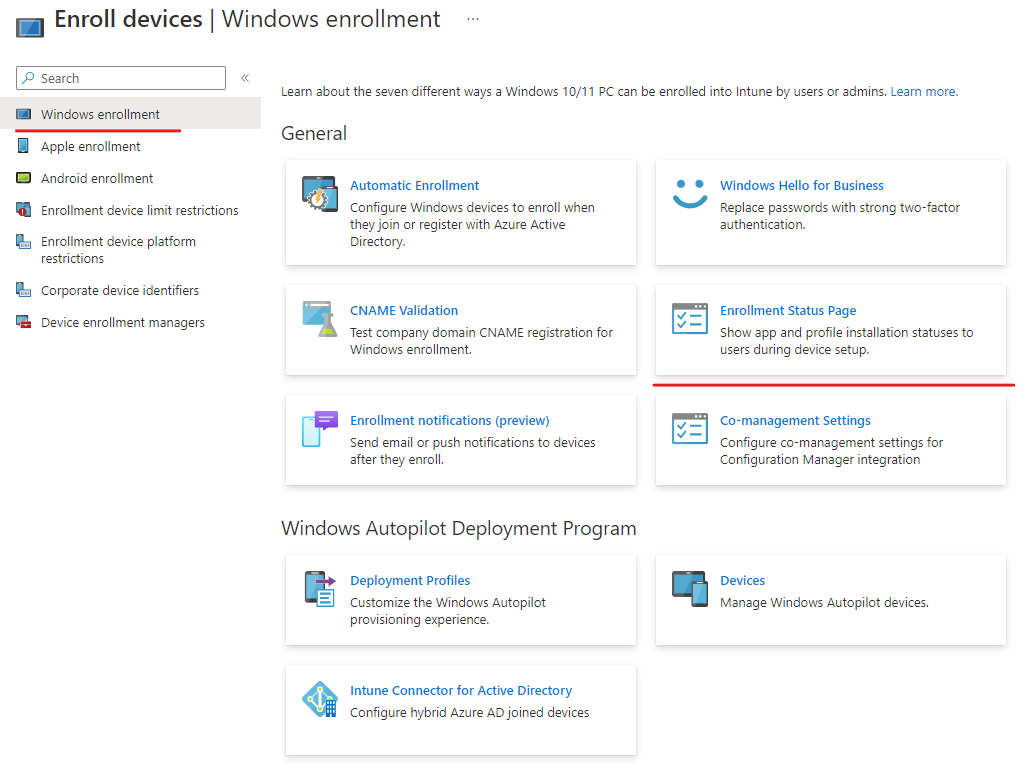
From this page you can create an ESP profile that is applied to the autopilot process to give some indication to the user that something is going on in the background. You can use this to control what information they can see on the ESP.
While this seems quite simple, and it is, there is actually some logic behind the scenes. ESP tracks certain stages of the Autopilot process.
Device Preparation Stages
(Securing hardware/Joining your organizations Network/register your device for MDM)Device Setup
(Device Targeted - Security Policies/Certificates/Network Connection/Apps)Account Setup
(User Targeted - Security Policies/Certificates/Network Connection/Apps)
ESP uses the EnrollmentStatusTracking configuration service provider (CSP) and FirstSyncStatus CSP to track app installation.
You can actually set this process to block a user using their device until certain apps and policies have applied as we will see in our working example.
Creating an ESP Profile
There is actually a default policy applied for ESP but not a lot is configured. You can create a new policy or edit this default policy. I will be creating a new policy. Navigate to the following to begin policy creation:
Windows Enrollment > Enrollment Status Page > +Create
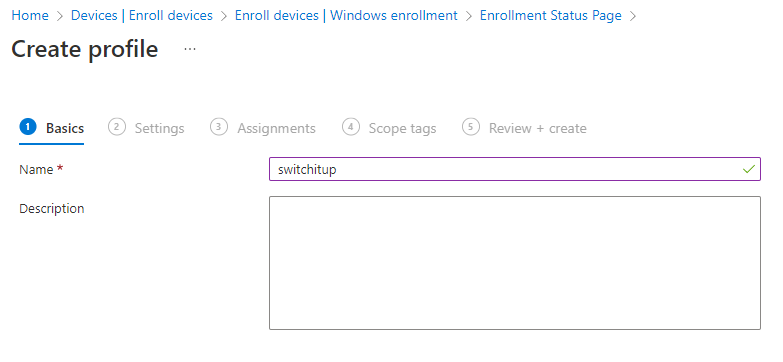
First, we must name the policy:
Second, turn on "show app and profile configuration progress", we can then add more granular controls:
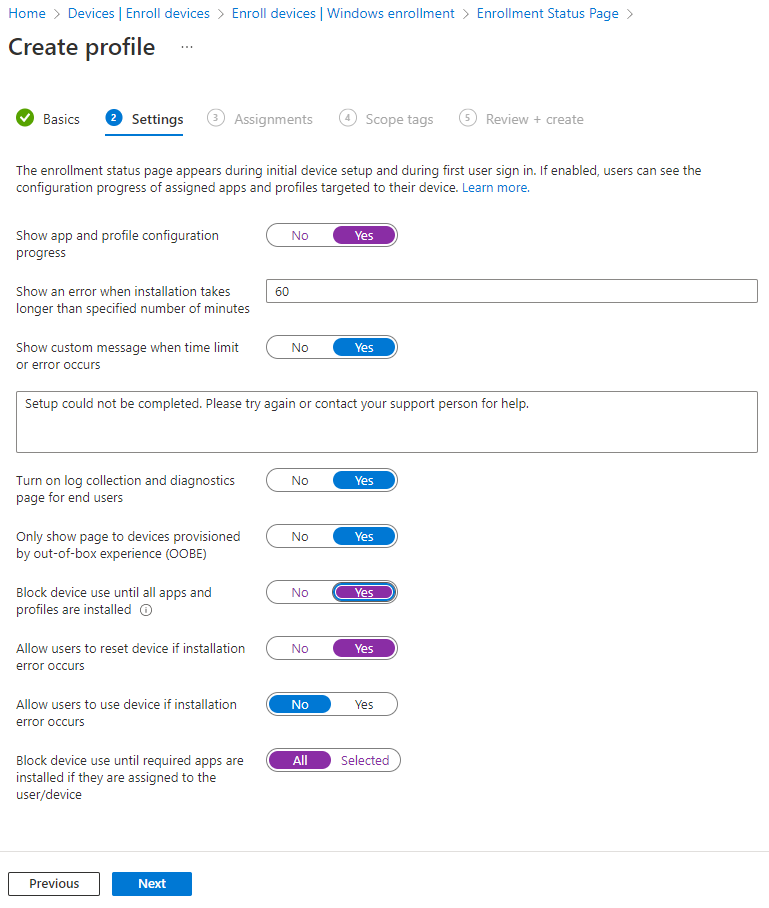
a number of things to consider here:
Is 60 minutes enough to deploy? Some enterprises may have many configuration profiles/policies and apps to deploy. If you can't deploy them within the 60mins your autopilot deployment will error out.
Do you want users to be able to reset devices if autopilot fails? personally this could rule out network issues/timeouts
If you select block until required apps are installed, you can select the apps from your applications that have been pre-staged into Intune.
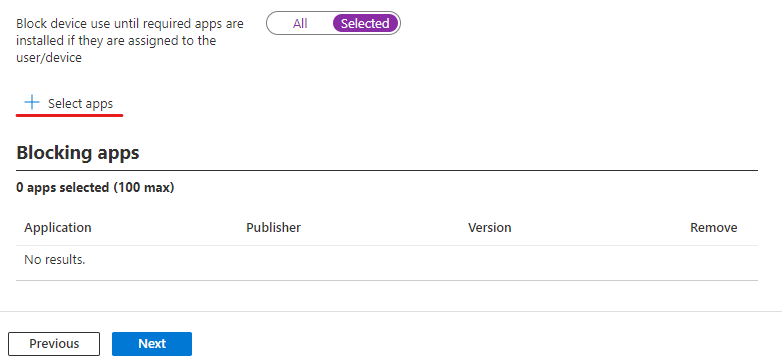
Finally, we will assign this profile to "Autopilot_Deployment" security group I created for my autopilot devices. I have no scope assignments, so I review and create
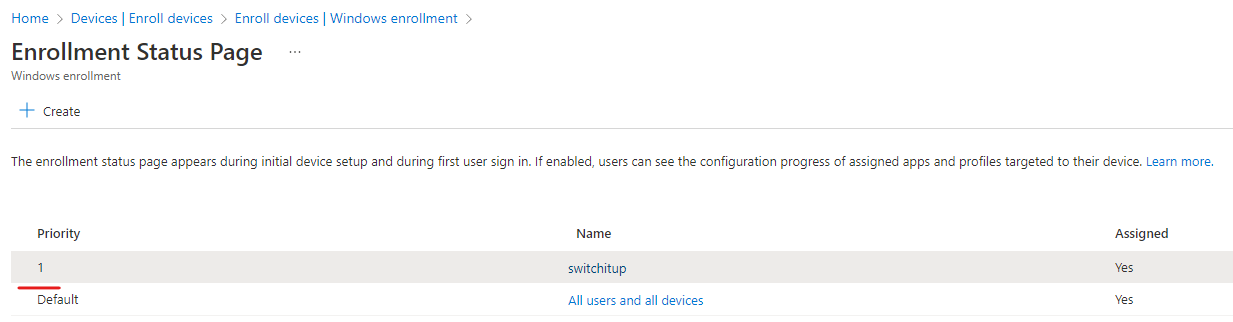
You will be taken back to the ESP screen, notice your new profile has been created with priority 1 meaning it will take precedent over the default profile.
Testing
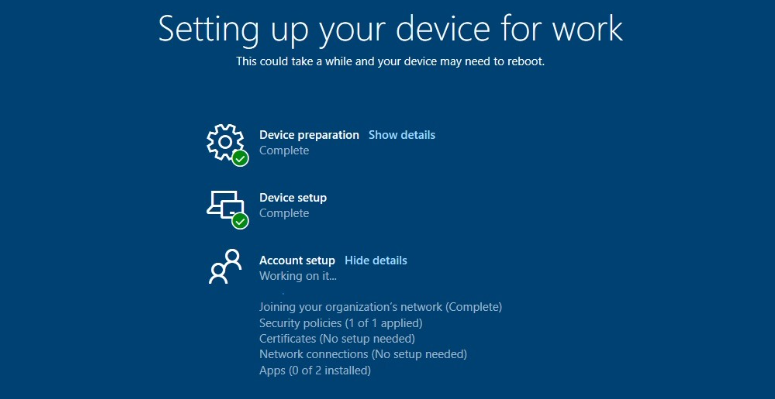
Now we have an ESP profile in place we will test by putting a machine through Autopilot. All being well you should be greeted with an ESP status page when your deployment is running (see below):
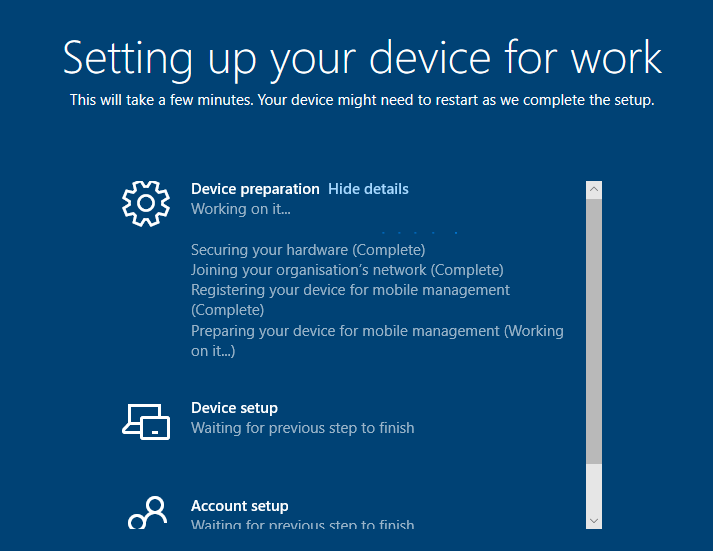
Users or admins can now see what stage the Autopilot build process is at and should it fail a reason code why. If you allowed users to reset if a failure occurs in the ESP profile, they will be able to restart the process and try again.
Summary
We have learned how to create an ESP profile and apply it to an autopilot build. For more information on how to setup autopilot deployments please see my previous post here:
https://switchitup.tech/windows-autopilot-deployment
Subscribe to my newsletter
Read articles from Ash Roberts directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ash Roberts
Ash Roberts
I am a technical consultant for a fast growing MSP. Due to the nature of my job I have quite a range of real world experience focusing around server/cloud(Azure) infrastructures, network design, installation and configuration all across multiple vendors such as Microsoft/Cisco/HP Aruba/FortiNet to name a few. All which, I am trying to share with yourselves. Whether you are new to the IT landscape or a veteran I hope there is something for you as my content grows. Currently hold certifications in following: Aruba switching CCNA route and switch CCNA cyber ops CCNA security MCSA windows 10 MCSA server 2016 MCSE core infrastructure Azure Administrator (az104) O365 administrator expert (ms100/101) Modern desktop administrator (md100/101) Hybrid server administrator (az800/801) Azure virtual Desktop specialty (AZ140) So, join me on my learning journey as well as work experience!