Active Directory: Misconfigurations, Lab and Best Practices
 Pradip Bhattarai
Pradip Bhattarai
Active Directory
Active Directory is a directory service used by organizations to store information about their users, computers, and other network resources. It's used primarily to provide a secure way to manage users, applications, and network resources. Active Directory can be used to simplify the administration of a network and provide single sign-on capabilities to users.
Active Directory plays a significant role in enabling the administrators to manage the privilege, permissions and access over the network resources. Each resource in a domain can be regarded as an object and the objects within an Active Directory consist of different attributes associated with them. Taking an example of a User object, its attributes include the first name, last name, group, email, etc.
Active Directory Domain Services (AD DS) is a core component of Active Directory providing the mechanism for authenticating users by determining what can they access over the network resources. Active Directory Domain Services (AD DS) also provides additional features like SSO, LDAP, etc.
Common Active Directory Misconfigurations
Common Active Directory misconfigurations refer to a set of security risks that can occur due to improper management or configuration of an organization’s Active Directory, such as granting incorrect access rights, exposing audit trails, using weak or default credentials, setting incorrect group policies, etc.
1) Failing to apply security patches and updates
Failing to apply security patches and updates in Active Directory refers to the lack of regular patching/updating of Active Directory components, such as domain controllers and application servers, which can leave systems vulnerable to malicious attacks.
2) Incorrect access rights granted
Incorrect access rights granted in Active Directory refer to the granting of inappropriate user and group permissions, which can lead to unauthorised access, data manipulation, data leakage, and other security risks.
3) Weak or default credential policies
Weak or default credential policies in Active Directory refer to the lack of strict password policies, such as minimum length, complexity and expiration, which can make it easy for attackers to gain access to systems.
4) Weak or missing audit trails
Missing audit trails in Active Directory is the lack of adequate auditing and logging of administrative activities, such as user access, permissions changes and system configuration changes, which makes it difficult to detect and investigate security and compliance incidents.
5) Improperly secured group policies
Improperly secured group policies in Active Directory refer to the setting of the incorrect user or group permissions, for example granting too much access to a user or granting administrative privileges to a normal user account which can lead to data leakage and data manipulation.
6) Unsecured replication between domain controllers
Unsecured replication between domain controllers in Active Directory refers to the lack of encryption when replicating data between domain controllers, which is a major security risk as it can lead to data leakage, data manipulation and other security risks.
7) Unsecured authentication protocols such as Kerberos or NTLMv2
Unsecured authentication protocols such as Kerberos or NTLMv2 in Active Directory refer to the lack of secure protocols being used for authentication, which can make it vulnerable to Man-in-the-Middle and other types of attacks. It is important to ensure that secure protocols are used for authentication.
9) Missing user accounts and related objects
Missing user accounts and related objects in Active Directory refer to user accounts or objects that are not properly managed or even forgotten altogether, which can lead to security vulnerabilities. Such users/objects could be maliciously created and used to gain access to data or applications, resulting in data leakage, data manipulation and other security risks.
Installing Active Directory
Install-WindowsFeature AD-Domain-Services -IncludeManagementTools
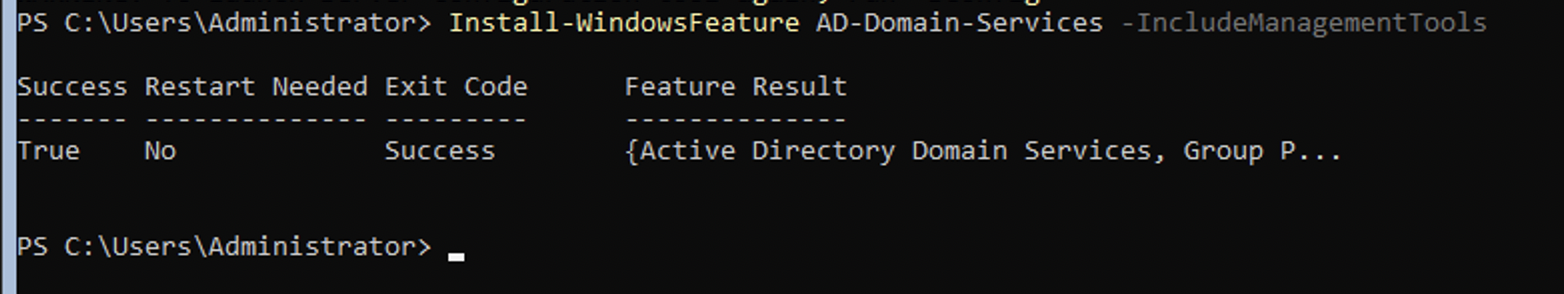
Issue the below-listed command to create the Active Directory Domain under vulnlab.local and enter the credentials as required in the prompt. The Active Directory domain will be created, the workstation will be promoted to a Domain Controller, and the PC will restart. After restarting, the message "Please wait for the Group Policy Client" is shown.
Install-ADDSForest -DomainName "vulnlab.local" -InstallDns:$true
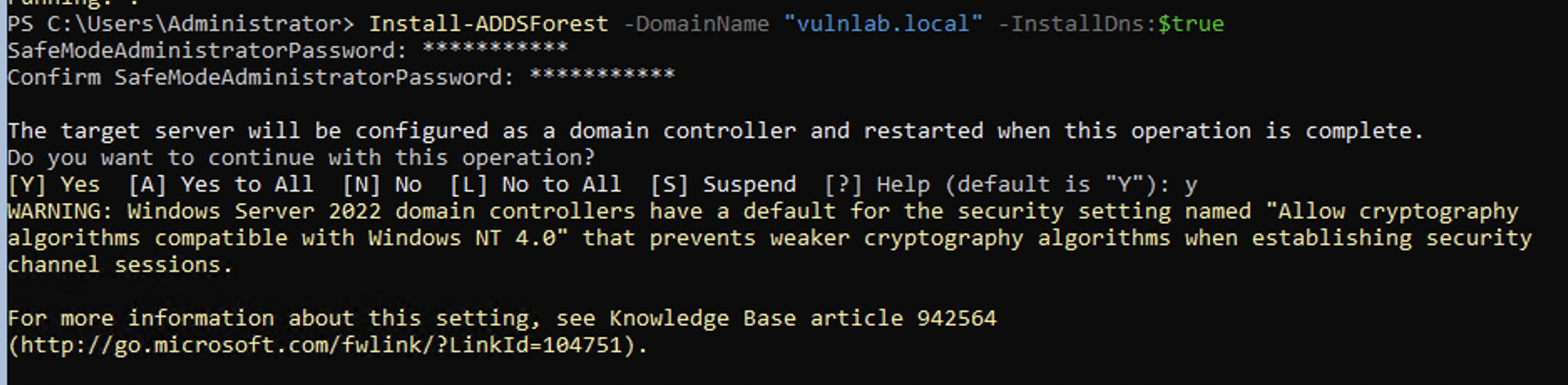
After a few minutes, the message disappears, and will now be greeted to Server Manager if you're using Windows Server with Desktop Experience, or the screen shown in the below image if the minimal version of Windows Server is installed.
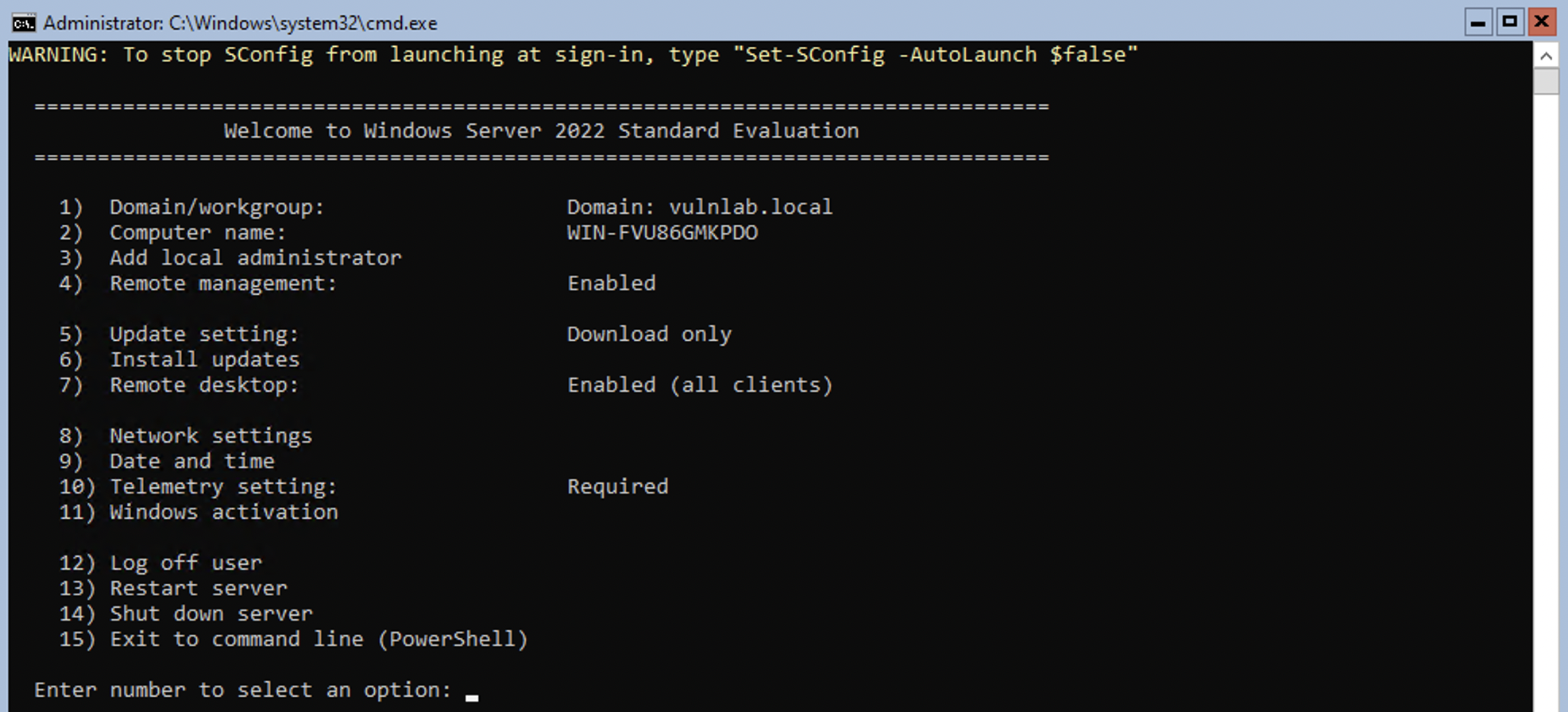
Since this blog is about creating a vulnerable Active Directory, let's directly jump into how different vulnerabilities/ misconfigurations can be set up.
Loading System.Web
Since we are using an automated password generator, let's import the Web assembly as it is not a part of PowerShell Core.
Add-Type -AssemblyName System.Web
Creating a Normal User
$generated_password = ([System.Web.Security.Membership]::GeneratePassword(12,2))
[New-ADUser -Name "John Doe" -GivenName John -Surname Doe -SamAccountName john.doe -UserPrincipalName john.doe@vulnlab.local -AccountPassword (ConvertTo-SecureString $generated_password -AsPlainText -Force) -PassThru | Enable-ADAccount](Link)
Write-Host "User is created with a password of $generated_password"
Creating multiple users
So, to simplify the above script, and add multiple users at a time, I have created a simple PowerShell script. To create a vulnerable domain with Nepalese names, I have collected some common first and last names.
$Global:Domain = "vulnlab.local"
$Global:firstNames = @('Kumar', 'Yukti', 'Himal', 'Sarala', 'Iswari', 'Hom', 'Sudir', 'Samana', 'Manoj', 'Sinij', 'Salim', 'Amira', 'Anisha', 'Bishnu', 'Manushi', 'Tilasmi', 'Binod', 'Nisa', 'Durga', 'Rupesh', 'Bimala', 'Bishwas', 'Ranjit', 'Raj', 'Deej', 'Riyanka', 'Utkrist', 'Loosun', 'Trimik', 'Afreen', 'Soyal', 'Sworup', 'Parajuli', 'Romit', 'Rijan', 'Shreejan', 'Renu', 'Krishal', 'Selina', 'Alish', 'Urusha', 'Chitra', 'Sumi', 'Kanti', 'Shuvekshya', 'Rupa', 'Mahananda', 'Ashish', 'Aarati', 'Nirmala', 'Manbahadur', 'Megh', 'Prakash', 'Gurubhakta', 'NIraj', 'Kaveri', 'Aadarsh', 'Raju', 'Khushbu', 'Sneha', 'Sakib', 'Ruchi', 'Rajeet', 'Hemkala', 'Sachit', 'Ramesh', 'Basant', 'Kapil', 'Achut', 'Sujil', 'Rabina', 'Anushiya', 'Sudeep', 'Bipin', 'Alisha', 'Yuvraj', 'Utsav', 'Bidyanand', 'Durgendra', 'Mallika', 'Niru', 'Awantika', 'Abha', 'Shivnath', 'Aakriti', 'Diwakar', 'Sujindra', 'Bidhan', 'Pallavi', 'Hemlal', 'Arbin', 'Rajesh', 'Pramod');
$Global:lastNames = @('Adhikari', 'Aryal', 'Amgai', 'Basyal', 'Bajgai', 'Baral', 'Bhandari', 'Bhurtel', 'Chapagai', 'Dahal', 'Dangal', 'Devkota', 'Dhakal', 'Dhungana', 'Deoja', 'Dangol', 'Dulal', 'Chaulagain', 'Khanal', 'Khatiwada', 'Kuikel', 'Koirala', 'Lamsal', 'Mahat', 'Mishra', 'Neupane', 'Osti', 'Paneru', 'Parajuli', 'Poudel', 'Pokhrel', 'Pathak', 'Regmi', 'Rijal', 'Rimal', 'Risal', 'Rupakheti', 'Sapkota', 'Sigdel', 'Simkhara', 'Singyal', 'Karki', 'Timalsina', 'Malla', 'Shrestha', 'Magar', 'Mahara', 'Lamichhane', 'Ghimire', 'Khulal', 'Parajuli', 'Sahani', 'Shahi', 'Singh', 'Sen', 'Chouhan', 'Chand', 'Hamal', 'Dhami', 'Budhathoki', 'Prasai', 'Rai', 'Bhusal', 'Thapa', 'Rana', 'Pun', 'Ale', 'Gyangmi', 'Palami', 'Gurung', 'Subba', 'Phuyal');
function CreateADUser {
Param(
[int]$limit = 1
)
Add-Type -AssemblyName System.Web
for ($i=1; $i -le $limit; $i=$i+1 ) {
$fName = (Get-Random -InputObject $Global:firstNames);
$lName = (Get-Random -InputObject $Global:lastNames);
$fullName = "{0} {1}" -f ($fName , $lName);
$principalName = "{0}.{1}" -f ($fName, $lName);
$SamAccountName = ("{0}" -f ($principalName)).ToLower();
$generated_password = ([System.Web.Security.Membership]::GeneratePassword(12,2))
Write-Host "Creating $SamAccountName User with a password of $generated_password."
Try { New-ADUser -Name "$fullName" -GivenName $fName -Surname $lName -SamAccountName $SamAccountName -UserPrincipalName $principalName@$Global:Domain -AccountPassword (ConvertTo-SecureString $generated_password -AsPlainText -Force) -PassThru | Enable-ADAccount } Catch {}
}
}
CreateADUser -limit 50
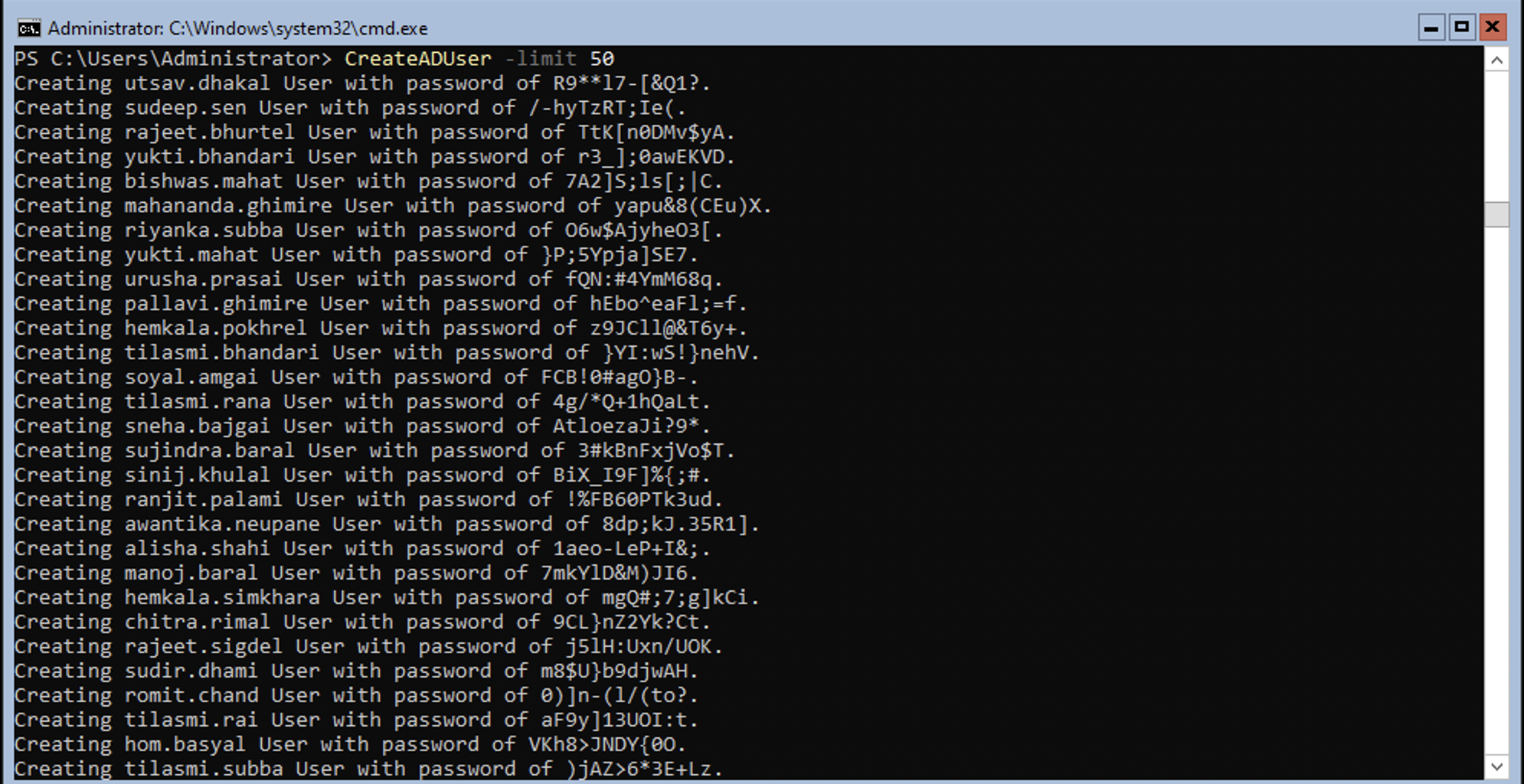
Listing AD Users
To list all the users in an Active Directory, using a PowerShell, the below-listed command can be issued.
Get-ADUser -Filter *
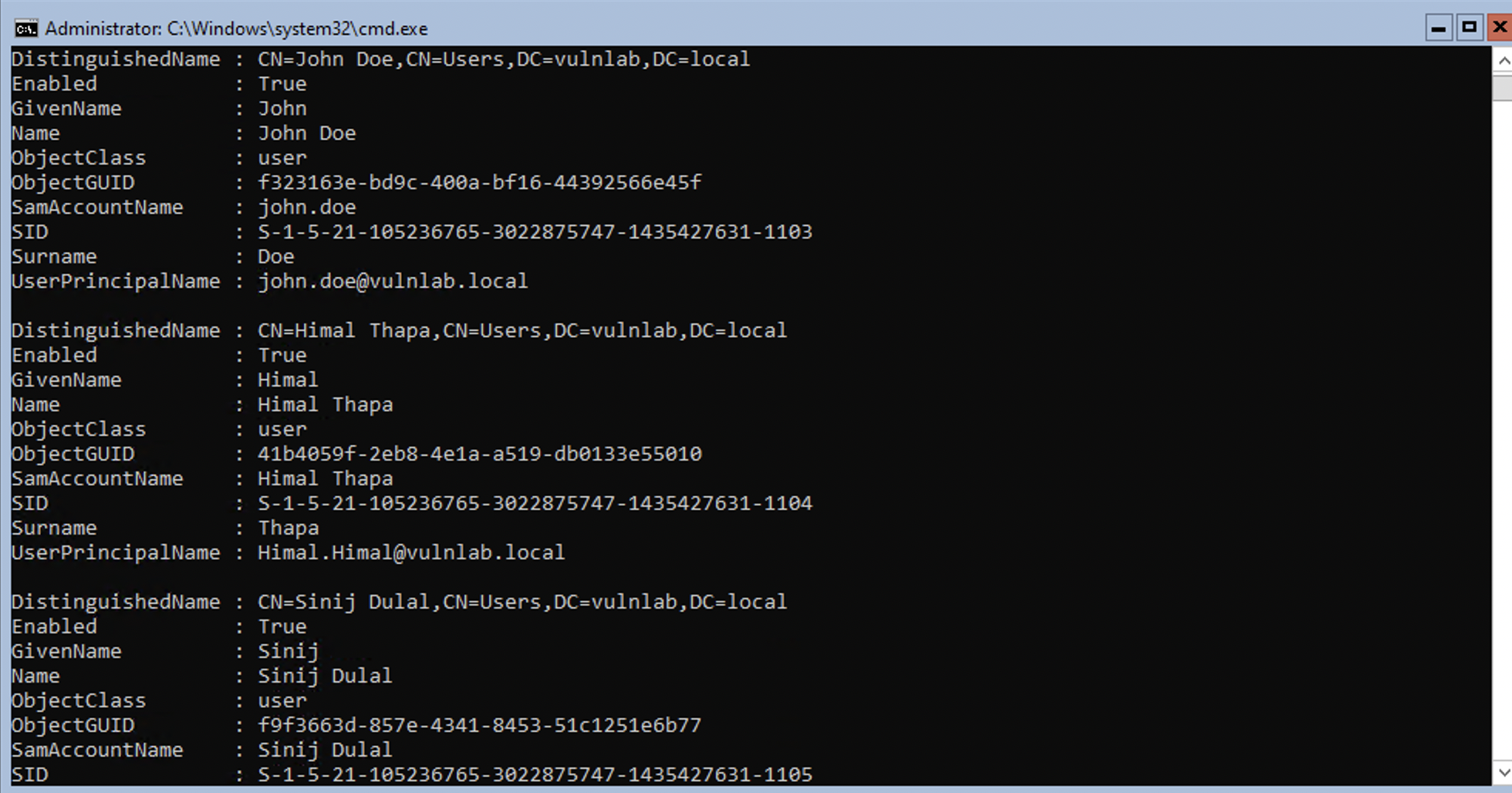
Common Misconfigurations
Password in AD User Description
Storing passwords in the description field exposes them to potential unauthorized access or exploitation by attackers who have access to the AD database. It is not a secure practice for sys admins to store AD user passwords in the description field. This field is not designed to store sensitive information and is not protected in the same way as the password field.
$Password = "P@ssw0rd"
New-ADUser -Name 'Firstname Lastname' -AccountPassword (ConvertTo-SecureString $Password -AsPlainText -Force) -Description $Password -Enabled $true
Kerberoasting
Kerberoasting is a technique used to attack a Microsoft Active Directory (AD) network by exploiting a weakness in the Kerberos authentication protocol. The goal of a Kerberoasting attack is to obtain the password hashes of service accounts, which can then be used to attempt to crack the passwords and gain unauthorized access to the network.
In a Kerberoasting attack, the attacker requests service tickets for a large number of service accounts on the network. The service tickets contain the password hashes of the service accounts, which are encrypted using the RC4 or AES encryption algorithm. The attacker can then attempt to crack the password hashes offline using a password-cracking tool. If the attacker is successful in cracking the password, they can use the service account's credentials to gain unauthorized access to the network.
Creating kerberoasting vulnerability
New-ADServiceAccount -Name "KerberoastableSvc" -ServicePrincipalNames http/KerberoastableSvc.vulnlab -AccountPassword (ConvertTo-SecureString "P@ssw0rd" -AsPlainText -Force) -Enabled $true
Set-ADAccountControl -Identity $serviceAccountName -PasswordNeverExpires $true
AS-REP Roasting
AS-REP Roasting is a type of attack that exploits a weakness in the Kerberos authentication protocol used by Microsoft Active Directory (AD) networks. The goal of an AS-REP Roasting attack is to obtain the password hashes of user accounts, which can then be used to attempt to crack the passwords and gain unauthorized access to the network.
In an AS-REP Roasting attack, the attacker sends a request for a user's password hash to the domain controller. The domain controller responds with an encrypted version of the password hash, encrypted using the RC4 encryption algorithm. The attacker can then attempt to crack the password hash offline using a password-cracking tool like hashcat. If the attacker is successful in cracking the password, they can use the user's credentials to gain unauthorized access to the network.
Creating AS-REP Roasting vulnerability
New-ADUser -Name 'ASREPRoastableUser' -AccountPassword (ConvertTo-SecureString 'P@ssw0rd' -AsPlainText -Force) -Enabled $true -PassThru | Set-ADAccountControl -PasswordNeverExpires $true -PassThru | Set-ADUser -DoesNotRequirePreAuth $true
SMB Relay Attack
SMB (Server Message Block) signing is a security feature that allows clients and servers to authenticate and verify the integrity of SMB traffic between them. When SMB signing is enabled, the client and server sign and verify each SMB packet using a digital signature, ensuring that the packets have not been tampered with during transmission.
When SMB signing is disabled, it can create a vulnerability in the network as it allows attackers to intercept and modify SMB traffic without being detected. This can potentially allow an attacker to perform an SMB relay attack. The attacker uses responder, and ntlmrelayx to listen for SMB traffic and forward it to a target server, pretending to be the victim.
Creating SMB Signing disabled
Set-SmbClientConfiguration -RequireSecuritySignature 0 -EnableSecuritySignature 0 -Confirm -Force
For creating additional vulnerabilities, refer to the code: https://github.com/Orange-Cyberdefense/GOAD
Best Practices for Securing Active Directory
Best practices for secure Active Directory management include:
1) Applying security patches and updates regularly
Applying security patches and updates regularly in Active Directory ensures that all components of the system, such as domain controllers, application servers and workstations, are kept up-to-date in order to prevent malicious attacks. It is important to ensure that security patches and updates are applied in a timely manner.
2) Configuring and enforcing strong passwords and expirations
Configuring and enforcing strong passwords and expirations in Active Directory prevents attackers from easily gaining access to the system by exploiting weak or default credentials. It is important to enforce secure password policies, such as long length, complexity and expiration, in order to ensure secure access.
3) Enabling audit trails
Enabling audit trails in Active Directory is an important security measure as it allows you to track user access, permission changes and system configuration changes, which can help to detect and investigate security and compliance incidents. It is important to ensure that audit trails are configured and regularly monitored.
4) Setting correct access rights (permissions)
Setting correct access rights in Active Directory refers to granting appropriate user and group permissions to ensure that users only have the necessary access to perform their job functions. It is important to ensure that users are granted the appropriate level of access and that permissions are regularly reviewed and adjusted if needed.
5) Securing group policies
Securing group policies in Active Directory is important as it helps to ensure that users and groups are granted only the minimum access rights that they need to do their job. It is important to regularly review group policies and ensure that only the necessary permissions are granted.
6) Enabling secure replication between domain controllers
Enabling secure replication between domain controllers in Active Directory is important as it helps to ensure that data is securely transferred between domain controllers without any unauthorized access. It is recommended to use secure protocols and encryption when replicating data between domain controllers.
7) Enforcing secure authentication protocols such as Kerberos or NTLMv2
Enforcing secure authentication protocols such as Kerberos or NTLMv2 in Active Directory is important as these protocols protect data transmitted over the network. It is important to ensure that secure authentication protocols are implemented and enforced.
8) Enabling SMB Signing
Enabling SMB (Server Message Block) signing in an Active Directory (AD) network helps protect against SMB relay attacks by allowing clients and servers to authenticate and verify the integrity of SMB traffic between them. When SMB signing is enabled, the client and server sign and verify each SMB packet using a digital signature, ensuring that the packets have not been tampered with during transmission.
9) Encrypting data transfers
Encrypting data transfers in Active Directory is important as it prevents unauthorized access and manipulation of data. It is important to ensure that all data transfers between domain controllers and other systems are encrypted.
9) Properly managing user accounts and objects
Properly managing user accounts and objects in Active Directory is important for security and compliance. It is important to ensure that all user accounts and related objects are properly created and managed and that any expired or unused accounts are deleted or disabled.
10) Restricting inbound and outbound traffic
Restricting inbound and outbound traffic in Active Directory is important as it helps to prevent malicious attacks and data theft. It is important to use firewalls and other security measures to ensure that only authorized traffic is allowed.
Subscribe to my newsletter
Read articles from Pradip Bhattarai directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
