AWS IAM: Advantages, Common Misconfigurations and Best Practices
 Pradip Bhattarai
Pradip Bhattarai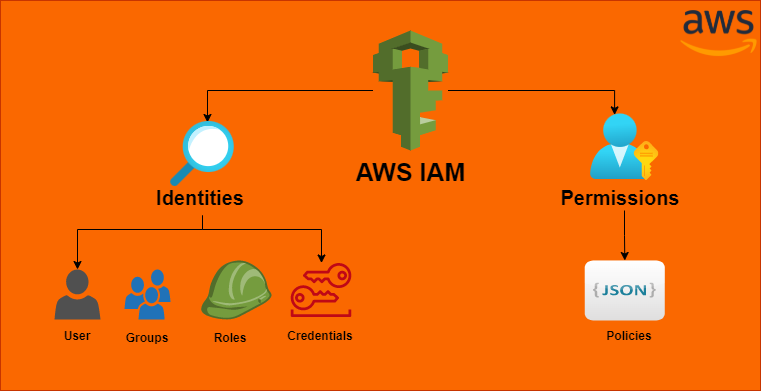
AWS IAM
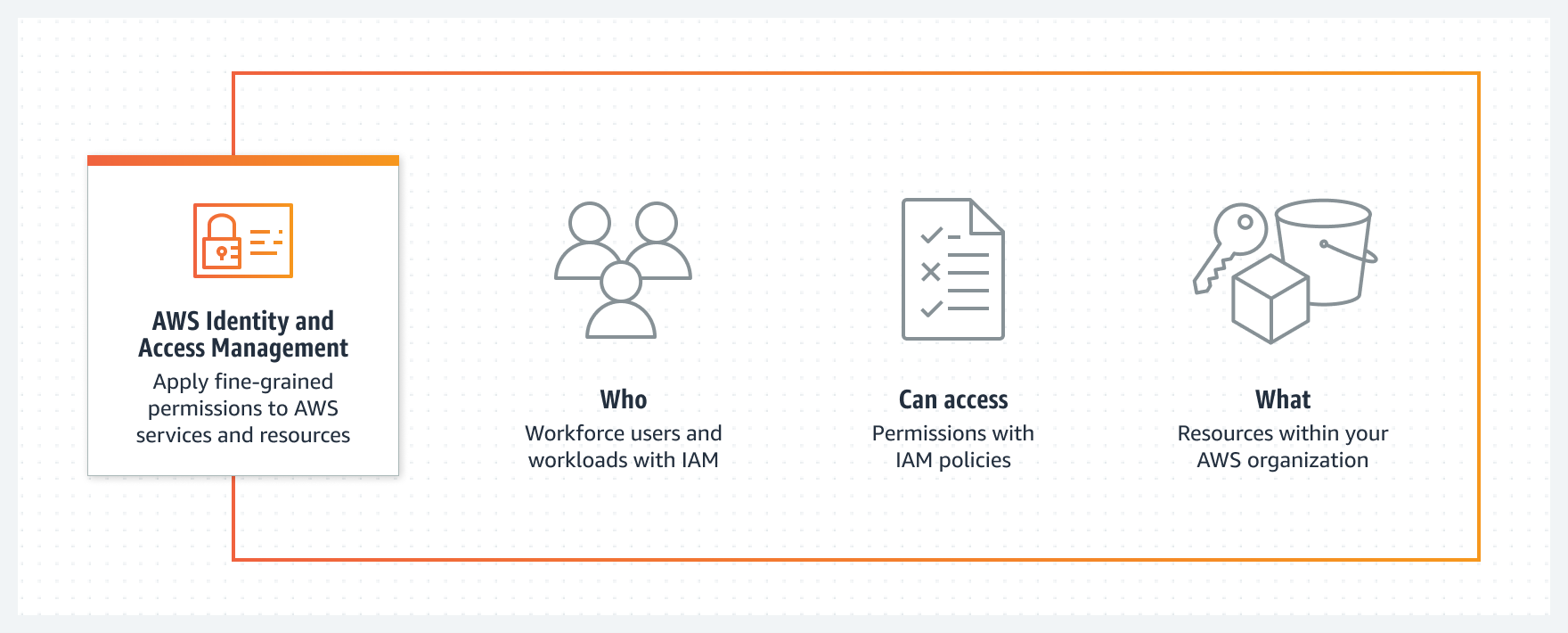
Identity and Access Management (IAM) is an AWS service that helps to provide access control to AWS resources. IAM should and is used to control authentication and authorization. AWS IAM can be used to can specify who and what can access services and resources in AWS. IAM further provides solutions to centrally manage permissions, and analyze access to refine permissions across AWS.
IAM enables creating and managing users, groups, and roles and defines and enforces permissions for those entities. In this way, IAM enables granting or denying access to resources based on the principle of least privilege, which means that users are given only the permissions needed to perform their specific job functions.
IAM enables organizations to create and manage AWS users and groups and use permissions to allow and deny their access to AWS resources. It also enables the creation of IAM roles that can be assumed by AWS services, AWS Identity Federation (Identity Providers), or external user identities. Additionally, IAM enables organizations to set up and manage security credentials, such as access keys and passwords, to access AWS resources.
Read More about IAM: AWS IAM Roles – Everything You Need to Know & Examples
Why use IAM?
Using IAM provides several benefits that help organizations to manage and secure their resources in the cloud. These benefits include:
Improved Security: IAM enables organizations to control access to their resources and data, ensuring that only authorized users can access sensitive information and can only perform actions that are explicitly allowed. This helps to protect sensitive data and resources from unauthorized access and potential breaches.
Cost Savings: IAM allows organizations to control access to resources, reducing the risk of unnecessary usage and unexpected charges. This helps organizations to keep their AWS costs under control.
Compliance: IAM enables organizations to control access to their resources and data, ensuring that only authorized users can access sensitive information and can only perform actions that are explicitly allowed. This helps organizations meet regulatory and compliance requirements.
Improved Collaboration: IAM enables organizations to control access to their resources and data, ensuring that only authorized users can access resources and can only perform actions that are explicitly allowed. This helps to improve collaboration within the organization by enabling users to access the resources they need to perform their job functions.
Advantages of using IAM
Granular Access Control: One of the most significant advantages of IAM is its ability to provide granular access control. With IAM, organizations can create and manage users, groups, and roles and define and enforce permissions for those entities. This enables organizations to grant or deny access to their resources at a very fine level of granularity. For example, an organization can grant a user access to a specific S3 bucket, but not to other buckets in the same account.
Multi-Factor Authentication: IAM also enables organizations to set up multi-factor authentication (MFA) for their users. This means that users are required to provide multiple forms of authentication, such as a password and a security token, to access resources. This helps to improve security by making it more difficult for unauthorized users to access sensitive information.
Auditing and Reporting: IAM enables organizations to audit and report on the actions that users have taken within the AWS environment. This enables organizations to monitor for suspicious or unauthorized activity and take action as needed. This helps organizations to meet regulatory and compliance requirements, as well as improve security.
Integration with Other AWS Services: IAM can be integrated with other AWS services such as S3, EC2, and RDS. This enables organizations to control access to these services using IAM policies. This makes it easier to manage access to resources across multiple services and improve security.
Common IAM Misconfigurations
Lack of Multi-Factor Authentication: One common IAM misconfiguration is the lack of MFA. When MFA is not mandatory, it makes it easier for unauthorized users to access sensitive information.
Over-Permissive Access Policies: Another common IAM misconfiguration is the use of over-permissive access policies. These policies are too broad and allow users to perform actions that they should not be able to perform. This can lead to unauthorized access to sensitive information.
Shared Credentials: Shared credentials are another common IAM misconfiguration. When multiple users share the same credentials, it makes it easier for unauthorized users to access sensitive information.
Lack of Regular Review and Rotation of Credentials: A lack of regular review and rotation of credentials is another common IAM misconfiguration. When credentials are not reviewed or rotated on a regular basis, it makes it easier for unauthorized users to access sensitive information. This can lead to security breaches.
To avoid these common misconfigurations, it's essential to regularly review and update access policies, implement multi-factor authentication, avoid shared credentials, and conduct regular reviews and rotations of credentials to maintain the security of the AWS environment.
Vulnerability Assessment in IAM
Performing a vulnerability assessment of your IAM environment is an essential step in maintaining the security of your AWS resources. There are several tools and techniques that can be used to identify potential vulnerabilities in your IAM environment.
Tools: There are several third-party tools that can be used to perform vulnerability assessments of IAM environments. Some popular tools include AWS Config, AWS Trusted Advisor and AWS Security Hub. These tools can help identify potential vulnerabilities, such as over-permissive access policies, lack of MFA, and outdated access keys.
Techniques: In addition to using tools, there are several techniques that can be used to identify potential vulnerabilities in your IAM environment. One technique is to review your IAM policies and identify any that are overly permissive. Another technique is to review your IAM users and identify any that have not been active for an extended period. Additionally, reviewing the CloudTrail logs for any suspicious activity can also help identify vulnerabilities.
Best Practices for IAM
Regularly review and rotate credentials: It's essential to regularly review and rotate credentials to ensure that they are still needed and that they have not been compromised. This helps to reduce the risk of unauthorized access to sensitive information.
Use Multi-Factor Authentication: Implementing MFA can help to improve security by making it more difficult for unauthorized users to access sensitive information.
Use the Least Privilege Principle: The least privilege principle states that users should be granted only the permissions they need to perform their job functions. This helps to reduce the risk of unauthorized access to sensitive information.
Use IAM Roles for AWS Services: IAM roles can be used to grant permissions to AWS services, making it easier to manage access to resources across multiple services.
Enable CloudTrail to Monitor IAM Logs: Enabling CloudTrail to monitor IAM logs can help to identify suspicious activity and take action as needed.
Conclusion
In conclusion, IAM plays a critical role in maintaining the security of your AWS resources. By using IAM, organizations can control access to their resources and data, ensuring that only authorized users can access sensitive information and can only perform actions that are explicitly allowed. By regularly reviewing and updating access policies, implementing multi-factor authentication, avoiding shared credentials, and conducting regular review and rotation of credentials, organizations can help to reduce the risk of unauthorized access to sensitive information.
Subscribe to my newsletter
Read articles from Pradip Bhattarai directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
