Dirty Pipe: A Critical Linux Kernel Vulnerability
 Pradip Bhattarai
Pradip Bhattarai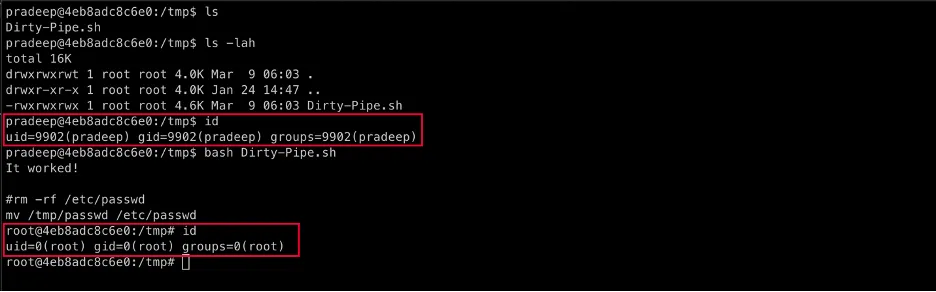
Recently, security researcher Max Kellermann discovered a critical vulnerability in the Linux kernel that has been affecting all versions since 5.8, including Android devices. This vulnerability, dubbed "Dirty Pipe," has the potential to lead to privilege escalation, allowing an attacker to inject code into root processes.
What is Dirty Pipe?
Dirty Pipe is a local privilege escalation vulnerability that is similar but easier to take advantage of compared to the previously released "Dirty Cow" (CVE-2016-5195). It occurs when there is a flaw in the "flags" member of the new pipe buffer structure that lacks proper initialization in copy_page_to_iter_pipe and push_pipe functions within the Linux kernel. This can result in the contamination of data in arbitrary read-only files, allowing an attacker to write to pages within the page cache backed by these read-only files and thus escalate their privileges on the system.
Technical Details
The vulnerability stems from the fact that the "flags" member of the new pipe buffer structure was lacking proper initialization in copy_page_to_iter_pipe and push_pipe functions within the Linux kernel. This can lead to stale values and thus allow an unprivileged local user to write to pages within the page cache backed by read-only files. This flaw affects all Linux kernel versions before 5.17-rc6.

Implications of Dirty Pipe
The Dirty Pipe vulnerability has significant implications for Linux users, as it allows attackers to escalate their privileges on the system. This means that attackers can gain root access to a vulnerable system, which can result in the theft of sensitive information, the compromise of critical systems, or the execution of malicious code.
Mitigating Dirty Pipe
To mitigate the risk of Dirty Pipe, it is recommended that Linux users update their systems to the latest version of the Linux kernel, which includes the patch for this vulnerability. The patch was included in the Linux 5.17-rc6 release, so all users running a version of the Linux kernel that is equal to or later than 5.17-rc6 should be protected against this vulnerability.
Conclusion
Dirty Pipe is a critical vulnerability in the Linux kernel that has been affecting all versions since 5.8, including Android devices. This vulnerability has the potential to lead to privilege escalation, allowing attackers to inject code into root processes. It is important that all Linux users update their systems to the latest version of the Linux kernel to mitigate the risk of this vulnerability. The patch for Dirty Pipe was included in the Linux 5.17-rc6 release, so all users running a version of the Linux kernel that is equal to or later than 5.17-rc6 should be protected against this vulnerability.
Subscribe to my newsletter
Read articles from Pradip Bhattarai directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
