Understanding Managed Identities in Azure - Part I
 Amit Khanna
Amit Khanna
In this article, we'll discuss what are Managed Identities in Microsoft Azure and how we can use them to secure and host truly credential-less .NET applications in the cloud.
What are Managed Identities in Azure?
Managed Identies is a feature in Azure AD that allow applications to be credentials-less, meaning it can remove the need to keep credentials in the application code and configuration files like username, passwords, secrets, API keys, etc. There is a common challenge for an application developer to manage secrets, keys, certificates, and credentials used to communicate with other services securely. Managed Identities are only supported for the Azure resources that support Azure Active Directory (AAD)
Managed identities for Azure resources is the new name for the service formerly known as Managed Service Identity (MSI).
Though developers can use Azure Key Vault to store the secrets and credentials in the Key Vault, again your application still needs to know the credentials to connect to the Key Vault to grab the secrets. Managed Identities eliminate that and automatically provide manage identity in Azure Active Directory for applications while connecting to resources protected by Azure AD which is a more secure way to host applications in the cloud. We'll look into how this can be achieved in the upcoming posts.
Note:
Managed Identities only work with services that support Azure AD authentication.
It only provides authentication and NOT authorization.
Types of Managed Identities
System-assigned - This type of identity is enabled directly on the Azure Service instances such as App Services, Function Apps, Virtual Machines, etc.
One identity is created per Azure Service instance.
Identity is deleted when the service instance is deleted.
User-assigned - This type of identity is created as a standalone for the Azure resource.
It can be assigned to more than one Azure service instance.
Its lifecycle is separate from the Azure service instance, meaning if the service instance is deleted the user-assigned identity remains.
How can I use Manage Identities in Azure?
Configuring Managed Identities in Azure is a two-step process.
Create Identity
Assign Permissions.
To create an Identity for App Service, open the app service and click on 'Identity' under settings.
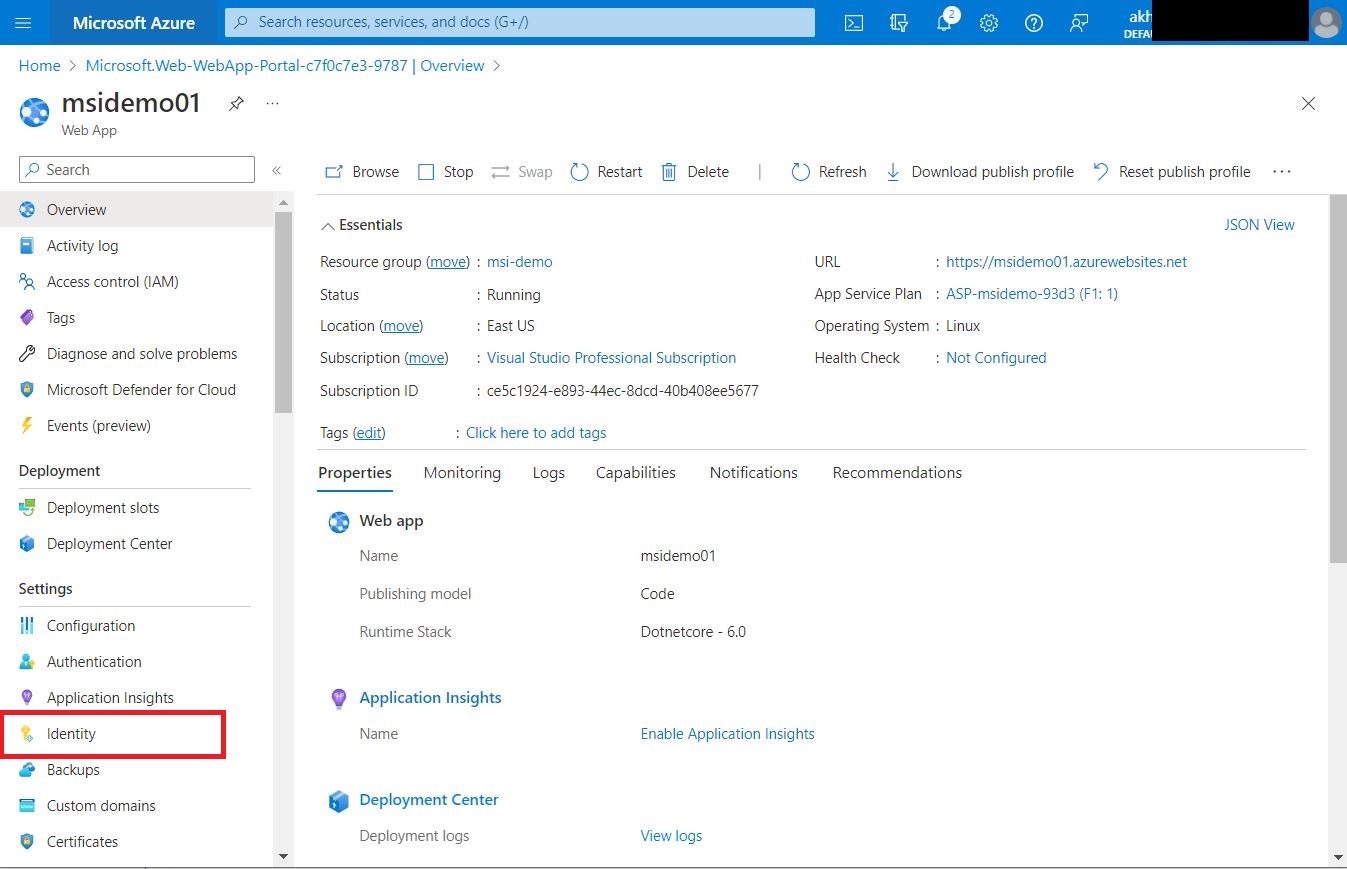
Under the System assigned, enable the Status setting to 'ON' and click 'Save'
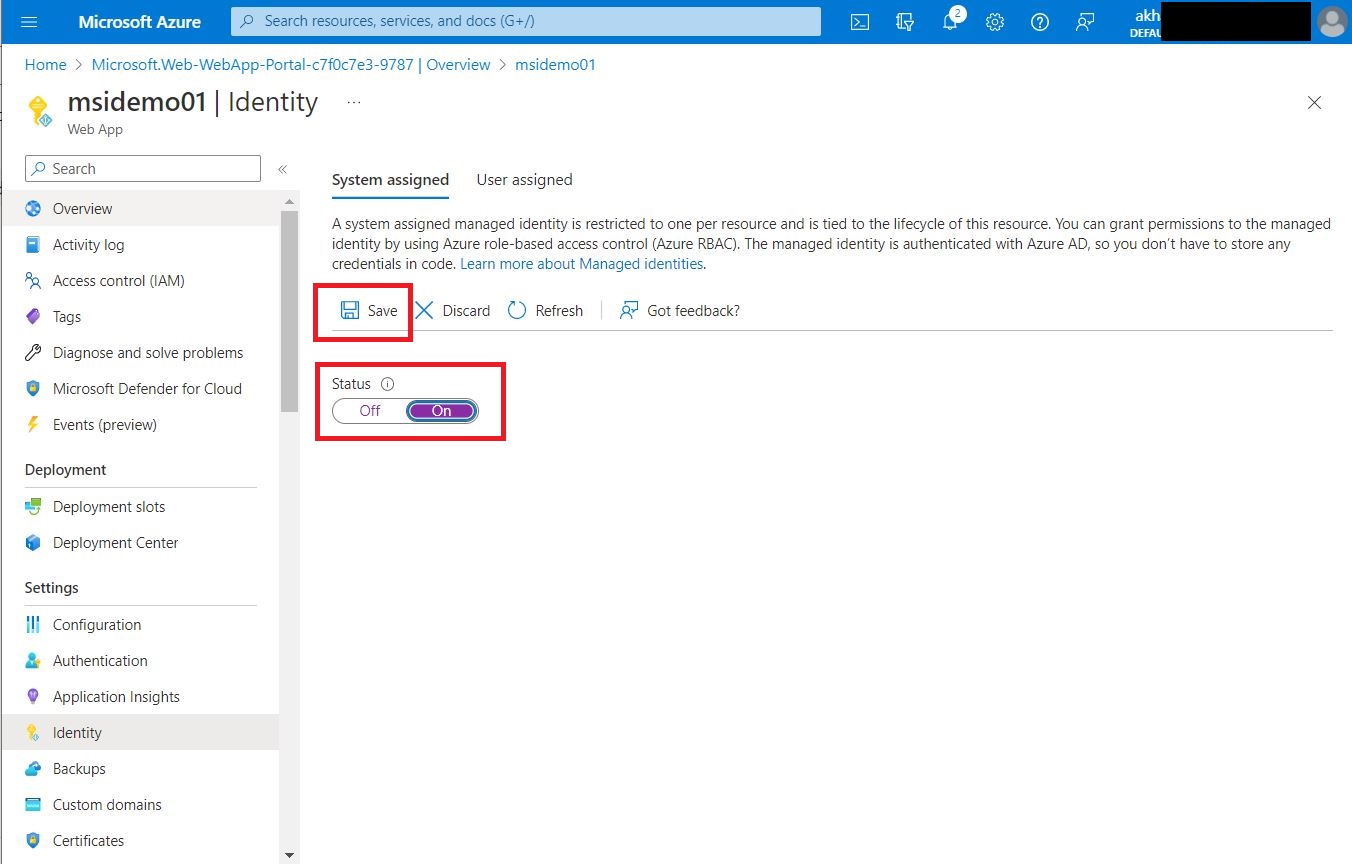
Now, the managed identity is registered with Azure AD and ready to be used to assign permissions.
Conclusion
We just read about what Managed Identities are and their types. In Part II of this series, we'll see how we can use the Managed Identities, Access Policies and Key Vault References to store credentials for a .NET application.
Subscribe to my newsletter
Read articles from Amit Khanna directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
Amit Khanna
Amit Khanna
Passionate technology professional, solution architect, and senior engineer currently focused on cloud and cloud-native technologies.