API Security Top 10 and Web Application Security Top 10: The Similarities, Differences & Threat models
 Precious Ishiguzor
Precious Ishiguzor
Introduction
API Security Top 10 and Web Application Security Top 10 are two lists of top vulnerabilities published by the Open Web Application Security Project (OWASP). These lists aim to provide guidance to software developers, security professionals, and decision-makers on the most critical security risks for web applications and APIs. Although both lists cover security vulnerabilities related to web applications, they differ in their focus and scope.
Importance of Web Application and API Security
Web Application Security Top 10 focuses on the security risks related to web applications. Web applications are software programs that are accessed through web browsers or mobile devices and can be used for various purposes, such as online banking, e-commerce, and social networking.
API Security Top 10, on the other hand, focuses on the security risks related to APIs (Application Programming Interfaces), which are sets of protocols, routines, and tools that enable different software applications to communicate with each other. APIs are used extensively in modern web applications to connect with different services and applications, such as payment gateways, social media platforms, and third-party software.
Overview of API Security Top 10 vulnerabilities (2019)
Definition of APIs
API stands for Application Programming Interface. It is a set of protocols, routines, and tools that enable different software applications to communicate with each other. They are often used to connect with third-party services to distribute or share data. APIs can be accessed by both authorized and unauthorized users, making them a potential target for attackers who can use them to steal sensitive data, launch denial-of-service attacks, or execute malicious code.
Differences in API Threat Models compared to Web Applications
The attack surfaces of APIs compared to web apps, include:
1. Smaller attack surface due to how APIs are designed to provide programmatic access to specific functions or data.
2. Simpler Input validation requirements, as APIs handle specific types of data or requests.
3. Complexity in transport security, API authentication and access control requirements and methods for different levels of access and protection of sensitive data transmitted over longer periods of time to specific users and resources.
4. API error handling requirements can expose sensitive information meant for developers to unauthorized users which can be used to launch attacks.
API-specific vulnerabilities and Mitigations
API 1. Broken Object Level Authorization
Where API functionalities do not properly check authorization for objects, this vulnerability allows an attacker gain unauthorized access to sensitive data.

Fig 1: Broken Object Level Authorization vulnerability (API-1)
Mitigation:
a) Implement strong authentication at both the user and session levels and the implementation of authorization controls at the object or function level.
b) Use Role-Based Access Control (RBAC) to individual objects or functions based on user roles.
c) Implement access controls based the principle of Least Privilege.
d) Use Secure Coding Practices when developing APIs.
e) Perform regular security testing to identify and address any vulnerabilities in the API.
API 2. Broken User Authentication and Authorization
The vulnerability occurs when APIs do not properly authenticate and authorize users, allowing unauthorized access to resources.

Fig 2: Broken User Authentication and Authorization vulnerability (API-2)
Mitigation:
a) Use strong authentication mechanisms, such as multi-factor authentication (MFA) and OAuth 2.0.
b) Use access control mechanisms to limit access to sensitive data and functionality.
c) Implement proper session management techniques, such as session timeouts and revocation on logout.
API 3. Excessive Data Exposure
When APIs expose too much data or sensitive information, this vulnerability can be exploited by attackers.
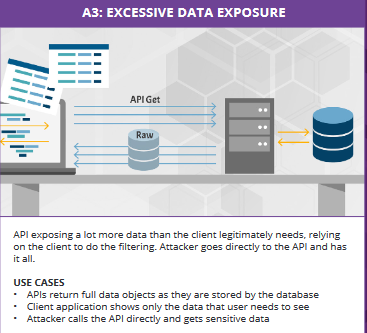
Fig 3: Excessive Data Exposure vulnerability (API-3)
Mitigation:
a) Only return the data that is necessary for the API request to limit exposure of sensitive information.
b) Use data masking, encryption or hashing techniques to obfuscate sensitive data.
c) Use tokens or session management techniques to restrict access to sensitive data.
d) Use secure communication channels (TLS) to prevent data from being intercepted or tampered.
e) Monitor API requests and responses using monitoring tools to detect potential security issues
Other API vulnerabilities include:
API 4 - Lack of Resources and Rate Limiting (url: https://bit.ly/3XGPLBv)
API 5 - Broken Function Level Authorization (url: https://bit.ly/3xzQbim)
API 6 - Mass Assignment (url: https://bit.ly/3EJnbsP))
API 7 - Security Misconfiguration (url: https://bit.ly/3YR7jwo)
API 8 - Injection attacks (url: https://bit.ly/3IEvYP5)
API 9 - Improper Assets Management (url: https://bit.ly/3XL1KOo)
API 10 - Insufficient Logging and Monitoring (url: https://bit.ly/3IgdPpb)
Overview of Web Application Top 10 Security vulnerabilities (2021)
Definition of Web Applications
Web applications run on a server and are accessed through a web browser or a web-based interface by clients over an internet network. They can be accessed from any device with a web browser and include interactive features such as forms, search bars, and menus that allow users to interact with the application and access its functionalities (eg. Information websites, e-commerce platforms or social networks).
Differences in Web application Threat Models compared to APIs
i. Larger attack surface than APIs.
ii. Complex input validation requirements, unlike APIs.
iii. Simpler transport security, authentication and access control requirements compared to APIs.
iv. Provides meaningful error messages to software developers to mitigate security risks.
Web Application-specific vulnerabilities and Mitigations
A01. Broken Access Control
When a web application fails to properly enforce restrictions on what actions a user can perform or what resources they can access, this vulnerability allows an attacker to perform unauthorized actions within the application.
Mitigation:
a. Define and enforce access control policies based on the principle of least privilege.
b. Use strong authentication and authorization mechanisms, such as multi-factor authentication, role-based access control, and attribute-based access controls for users and applications to access specific resources.
c. Use encrypted session tokens and rate limiting of concurrent sessions to prevent session hijacking.
d. Regularly test and audit access controls to identify potential vulnerabilities.
e. Monitor, log and track user behaviour to detect, alert and respond to any suspicious/unauthorized activity.
f. Keep software and systems up to date to prevent known vulnerabilities from being exploited.
g. Educate users about the associated risks and train to implement security best practices.
A02. Cryptographic Failures
This refers to vulnerabilities that arise from the incorrect or inadequate use of cryptography to protect sensitive data such as passwords, credit card numbers, and other personal identifiable information.
Mitigation:
a. Use strong encryption algorithms, such as AES-256, RSA-2048, and SHA-256 to protect sensitive data against cryptographic attacks.
b. Encryption keys should be generated using a secure and random algorithm and stored in a secure location.
c. Use secure transport protocols such as HTTPS to transmit sensitive data over the internet.
d. Update cryptographic libraries and software regularly using the latest and most secure algorithms.
e. Store sensitive data in encrypted databases or encrypted file systems and use access control mechanisms to restrict access to sensitive data.
f. Conduct regular security audits and test web applications for cryptographic vulnerabilities to identify and remediate potential weaknesses.
A03. Injection attacks
This is type of security vulnerability occurs when an attacker injects/sends malicious data, commands or code as a user input to a software/web application with the intent of manipulating the application to exfiltrate or expose sensitive data and to corrupt the database when it executes the malicious script.
Mitigation:
a. Validate and sanitize user input including data entered into web forms, to prevent malicious code from being injected into the application.
b. Use prepared statements and parameterized queries in your application code to prevent the execution of malicious scripts.
c. Use input validation libraries and frameworks to simplify input validation tasks and reduce the risk of coding errors.
d. Limit database permissions of the user account to prevent an attacker who has gained access to the application from being able to manipulate or view sensitive data in the database.
e. Use secure coding practices such as using parameterized SQL statements, input validation, and error handling to prevent injection attacks.
f. Keep software and systems up to date to prevent known vulnerabilities from being exploited.
g. Use intrusion detection and prevention systems to detect and block malicious traffic.
h. Train and Educate users on security best practices and to report insider/suspicious activity to security teams.
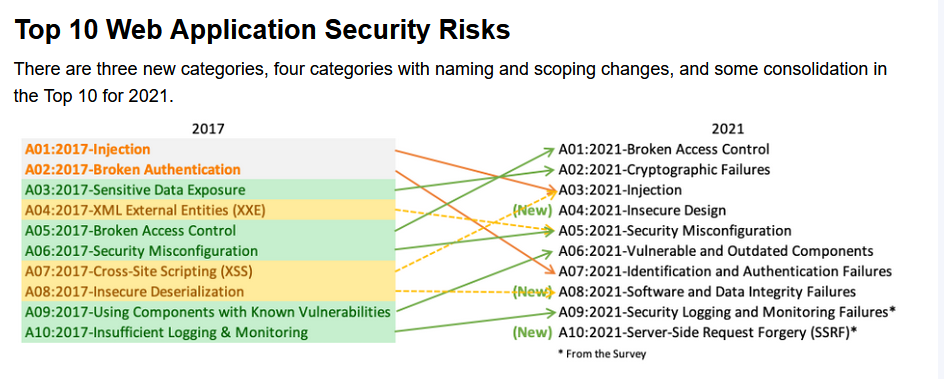
Fig 4: Web Application Top 10 Security risks
Others Web App vulnerabilities include:
A04 - Insecure Design (url: https://bit.ly/3k9zkA5)
A05 - Security Misconfiguration (url: https://bit.ly/41bAnQM)
A06 - Vulnerable and outdated Components (url: https://bit.ly/3Km7g71)
A07 - Identification and Authentication Failures (url: https://bit.ly/3kcMyMs)
A08 - Software and Data Integrity Failures (url: https://bit.ly/3lRyIzH)
A09 - Security Logging and Monitoring Failures (url: https://bit.ly/3lUqg2g)
A10 - Server-side Request Forgery (url: https://bit.ly/3IAnZlY)
Conclusion
Overall, while there are similarities in the attack surfaces of web applications and APIs, there are also some key differences in terms of input validation, authentication and access control, transport security, and error handling. By understanding the differences in threat models between APIs and Web applications, software developers and security professionals can implement appropriate measures to mitigate the risks to both types of applications.
However, it is important to note that mitigation measures alone may not be enough to fully protect against all potential security threats. A comprehensive security strategy should be implemented to ensure the highest level of protection.
Subscribe to my newsletter
Read articles from Precious Ishiguzor directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Precious Ishiguzor
Precious Ishiguzor
Enterprise Cloud Security Architect with exceptional business and digital transformation skills in Multi-Cloud Security architectures, Cloud Infrastructure designs, threat assessment, hybrid and multi-cloud technologies. Demonstrated strong business acumen of enterprise solutions, solid understanding of high-performance computing environments, zero trust security, network vulnerability analysis, risk frameworks, architecting high level and robust end-to-end security solutions.