AWS Parameters and Secrets Lambda Extension Demo Using AWS CDK
 Vu Dao
Vu Dao
Abstract
The story: AWS launched the AWS Parameters and Secrets Lambda Extension, a convenient method for AWS Lambda users to retrieve parameters from AWS Systems Manager Parameter Store and secrets from AWS Secrets Manager. AWS Lambda customers can leverage this extension to improve their application performance as it decreases the latency and the cost of retrieving parameters and secrets.
What makes you happy? Until now, parameters and secrets were obtained in the Lambda function process using the AWS SDK or other means. With this extension, these values can be cached and reused during the lifecycle of a Lambda function. This reduces the latency and cost of retrieving parameters and secrets.
This post uses AWS CDK Typescript to create a lambda function URL where its handler gets
SecureStringvalue of the parameter store.
Table Of Contents
🚀 Pre-requisite
You need slack workspace (free) to create slack incoming-webhooks
Getting started with AWS CDK
🚀 How lambda handler gets Parameter/Secret value through the extension layer
To authorize and authenticate Parameter Store requests, the extension uses the same credentials as those used to run the Lambda function itself, so the lambda role need to have permission
ssm:GetParameterandkms:DecryptTo use the AWS Parameters and Secrets Lambda Extension, we add the extension to the Lambda function as a layer. The layer ARN differs from the region which we can get in retrieving-secrets_lambda_ARNs
With the above setup, the lambda hander just calls to the GetParameter API to retrieve the value with the following input
Host:
localhostPort: 2773
Header:
X-Aws-Parameters-Secrets-TokenwithAWS_SESSION_TOKENenvironment variableEncode the
queryStringParameters
Source code: Here we get the
secureStringparameter store of slack incoming webhookSSM_SLACK_WEBHOOK_PRAMETER_NAME='/slack/webhook/url/devops'def get_ssm_parameter_store(): SSM_SLACK_WEBHOOK_PRAMETER_NAME = os.getenv( 'SSM_SLACK_WEBHOOK_PRAMETER_NAME') url = 'http://localhost:2773' header = {'X-Aws-Parameters-Secrets-Token': os.getenv('AWS_SESSION_TOKEN')} parameter_encode = requests.utils.quote(SSM_SLACK_WEBHOOK_PRAMETER_NAME) path = f'systemsmanager/parameters/get?name={parameter_encode}&withDecryption=true' res = requests.get(f'{url}/{path}', headers=header) if res.status_code == 200: data = res.json() return data['Parameter']['Value'] else: print( f"Failed to get SSM parameter store {SSM_SLACK_WEBHOOK_PRAMETER_NAME}") return None
🚀 Dive deep into CDK code
The cdk is not much, just includes the following stacks:
CMK (custom managed key): This key is to encrypt the parameter store value
Lambda role: Provides the function lambda basic execution,
ssm:GetParameterandkms:Decryptrestrict to the above CMK onlyLambda function with enable function URL (AuthType:
AWS_IAM)
Source code:
main.ts
🚀 Deploy and Demo
Run
cdk deploywe will have our resources. Note the output of the lambda function URL✨ hotswapping resources: ✨ Lambda Function 'sin-d1-parameters-secrets-extension-test' ✨ Lambda Function 'sin-d1-parameters-secrets-extension-test' hotswapped! ✅ aws-parameters-secrets-lambda-extension-cdk-dev ✨ Deployment time: 10.76s Outputs: aws-parameters-secrets-lambda-extension-cdk-dev.sind1parameterssecretsextensiontesturl = https://5vz5x3mo2aifykigcgnljuwqzy0izsyy.lambda-url.ap-southeast-1.on.aws/ Stack ARN: arn:aws:cloudformation:ap-southeast-1:123456789012:stack/aws-parameters-secrets-lambda-extension-cdk-dev/cdd50120-52f4-11ed-ad52-06a9bacec754 ✨ Total time: 15.56s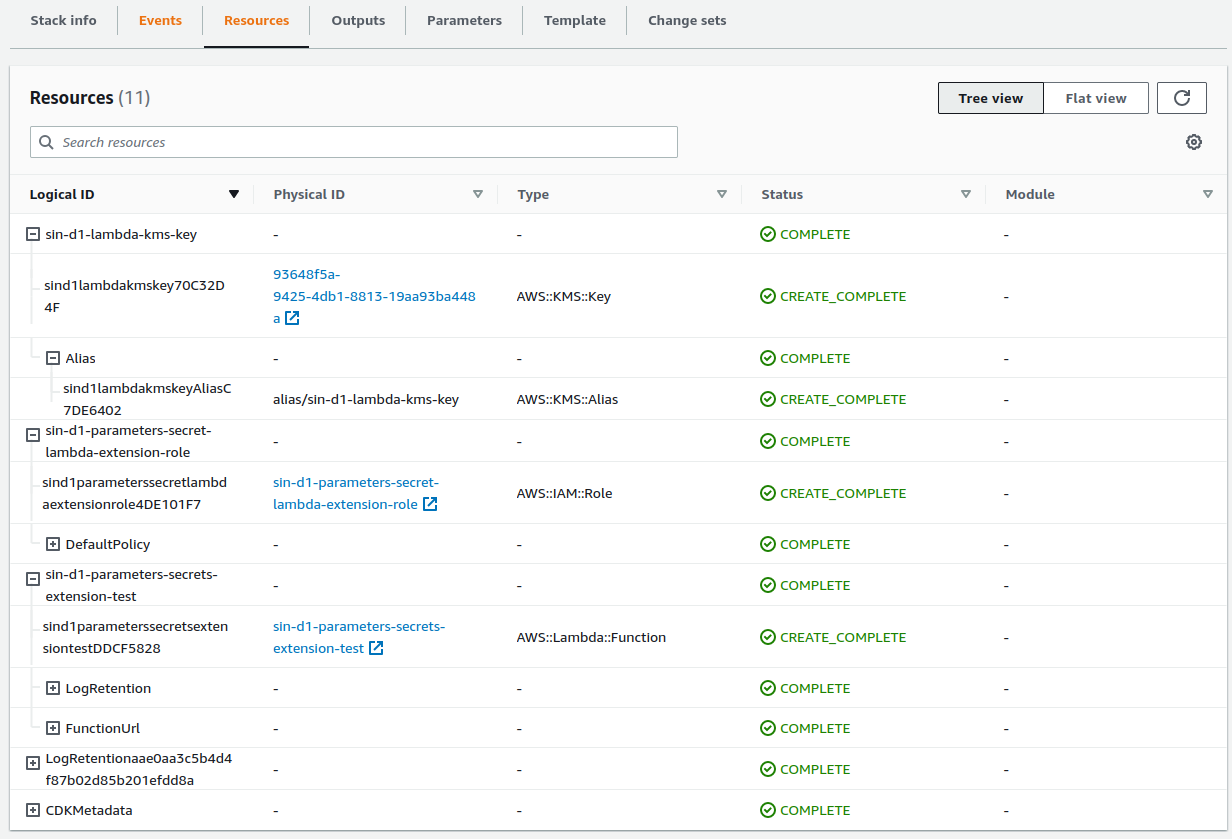
The function URL uses
AWS_IAMauth type so we must sign each HTTP request using AWS Signature Version 4 (SigV4). Here we use the tool awsculr to sign the requestCall request to send
HelloCdkServerlessslack message~ $ awscurl https://5vz5x3mo2aifykigcgnljuwqzy0izsyy.lambda-url.ap-southeast-1.on.aws/?message=HelloCdkServerless --profile mfa --region ap-southeast-1 --service lambda null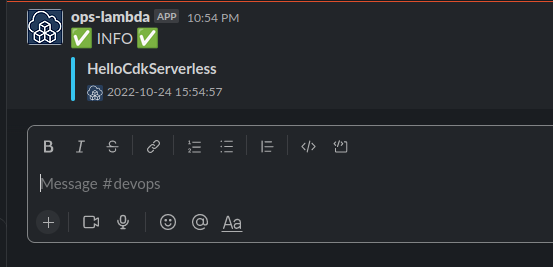
🚀 Conclusion
We now have another option to get secret values from parameter store or secret by using AWS Parameters and Secrets Lambda Extension.
Hope this will be of help to someone else and remember to destroy the stacks after testing
cdk destroy
Subscribe to my newsletter
Read articles from Vu Dao directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Vu Dao
Vu Dao
🚀 AWSome Devops | AWS Community Builder | AWS SA || ☁️ CloudOpz ☁️