PenTest Introduction
 Abdul Hakim
Abdul Hakim
What is PenTest?
PenTest is the acronym for "Penetration Testing" or a kind of activity that conducts to identify any security weakness and vulnerabilities that may exist in our network or system. There are many ways to perform Penetration Testing in a real-world scenario, based on the best practice, some security researchers create a community to build an objective and standard for Penetration Testing (such as OWASP for the Standard Penetration Testing in Web Applications).
Some situations when we need to conduct Penetration Testing :
System security evaluation: If you want to evaluate the security of a system or network, using a pentest framework can help identify weaknesses and security vulnerabilities in the system.
Security audit: If you want to conduct a security audit on a system or network, using a pentest framework can help determine how the system or network protects data and ensure that things like configuration, access, and authentication are properly implemented.
Security planning: If you want to plan and prepare for the security of a system or network, using a pentest framework can help determine what needs to be done to strengthen and improve the security of the system or network.
Attack simulation: If you want to simulate an attack on a system or network, using a pentest framework can help determine how the system or network responds to the attack and ensure that the system or network has effective defense mechanisms in place.
How to Perform PenTest?
The Methodology
PenTest can be conducted by several methods, those are including the Blackbox, Greybox, and Whitebox.
BlackBox Testing is a type of penetration testing where the pentester has zero knowledge about the target. The pentester must conduct the testing based on the basic information that they know such as the organization name / the domain name of the target.
GreyBox Testing is a type of penetration testing where the pentester has some knowledge about the target. The pentester must conduct the testing based on some information/access that can be used to interact with the target.
WhiteBox Testing is a type of penetration testing where the penetration tester has all knowledge about the target. The pentester will conduct the testing with all the information / full access to the target, such as the source code, technical documentation, and system configuration.
The Approach
Generally, PenTest can be defined in three main phases, those are Pre-Exploitation, Exploitation, and Post-Exploitation.
Pre-Exploitation is the phase conducted by penetration testers before attempting to exploit vulnerabilities in the target system or network. The aim is to prepare the penetration tester before executing an attack, to increase the effectiveness and efficiency of the attack.
Exploitation is the process of exploiting vulnerabilities or weaknesses in the target system or network to gain unauthorized access or take control of the system or network.
Post-Exploitation is the stage after an attacker successfully gains access to the target and exploits it to obtain access and control. The goal of this stage is to maintain access to the system and obtain more detailed information, such as sensitive data or passwords, and manipulate the system according to the attacker's wishes.
The PenTest phases can be described in the diagram below :
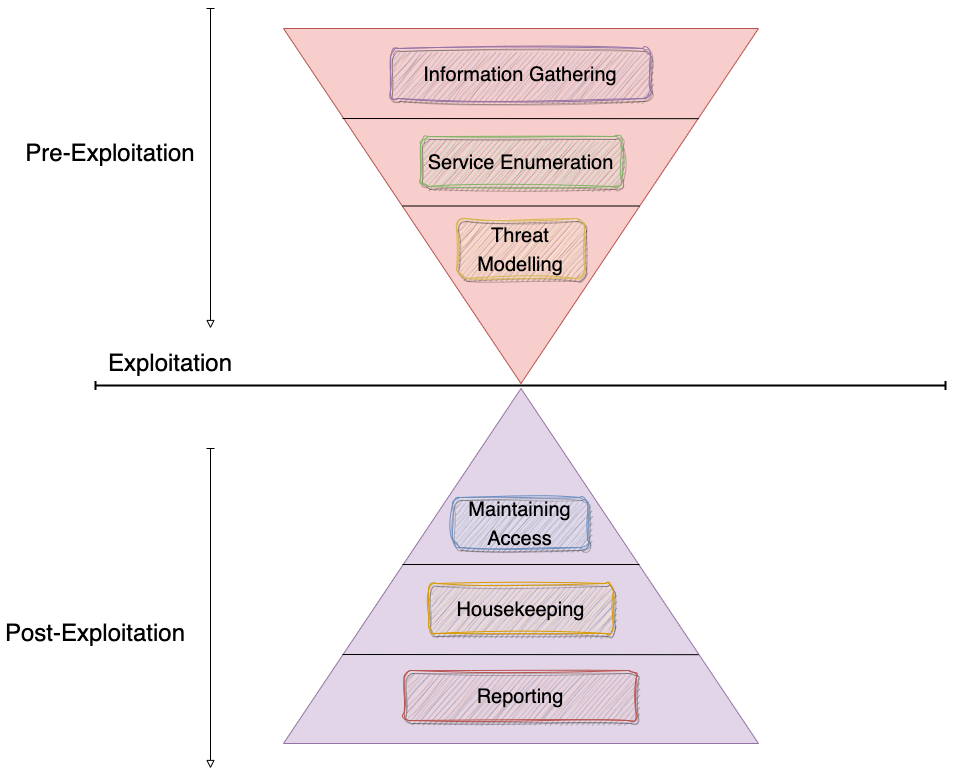
Pre-Exploitation
Information Gathering
Collect information about the target through various methods, such as footprinting and enumeration, to gain a better understanding of the target and help determine the appropriate attack strategy.
Technical, is the information gathering that is performed by any technical thing. Based on the tools that are used to conduct the information gathering, there are two kinds of technical information gathering.
Active (performed with direct interaction with the target), tools: OSINT such as Google Dork, ShodanHQ, Maltego, Recon-NG, etc.
Passive (performed with no interaction with the target), tools: scanner such as netdiscover, nmap, etc.
Non-Technical, is the information gathering that is performed by any social experience. The tools that can be used in this kind of information gathering such as social engineering toolkit.
Service Enumeration
The process of identifying the services and applications running on the target system or network during penetration testing. This information is crucial for penetration testers as these services and applications often have security vulnerabilities that can be exploited to gain entry to the target system or network.
Some tools that can be used to perform the service enumeration such as nmap, dirsearch, whatweb, wpscan, etc.
Threat Modelling
Conduct the threat model to identify potential attack scenarios and determine which parts of the target system or network are most vulnerable to those attacks. A sample framework that can be used in the threat modeling phase is STRIDE. Developed by Praerit Garg and Loren Kohnfelder at Microsoft, it provides a mnemonic for security threats in six categories. Those are :
Threat | Desired property |
Spoofing | Authenticity |
Tampering | Integrity |
Repudiation | Non-repudiability |
Information disclosure | Confidentiality |
Denial of service | Availability |
Elevation of privilege | Authorization |
Some tools that can be used to define the threat model for the target such as BurpSuite, Nessus, Nexpose, etc.
Exploitation
Perform the attack scenario that may lead to a security compromise. The step can be described below :
Choosing a vulnerability to exploit: this is based on the information gathered during the reconnaissance or vulnerability assessment and threat modeling phase.
Choosing the appropriate tool or method to exploit the vulnerability that has been identified.
Executing the exploitation using the selected tool or method.
Some tools that can be used in the exploitation process such as Metasploit, exploit-db, sqlmap, etc.
Post-Exploitation
Maintaining Access
In the phase after successfully gaining access to the system, the attacker must maintain access to the target system. The steps that can be taken to maintain access include creating a backdoor or installing malware that allows the attacker to continue accessing the system.
Some tools that can be used in the maintaining access process such as Meterpreter, LinPEAS, etc.
Housekeeping
Housekeeping in post-exploitation is the steps taken by an attacker after successfully infiltrating the target system and maintaining access to it. The goal is to minimize the digital footprint left by the attacker and ensure that the access gained remains secret.
Some tools that can be used in housekeeping such as Linux commands:
$ dd if=/var/log/app.log of=/dev/null
$ dd if=/var/log/app.log of=/dev/zero
Reporting
Reporting is a stage where the attacker reports the results of the exploitation performed to the party that employs penetration testers or security teams. The purpose of this stage is to provide detailed and accurate information regarding vulnerabilities and security gaps that exist in the target system or network and provide recommendations to fix them.
Some tools that can be used for reporting such as app-office, app ticketing, etc.
Where can we start our PenTest Journey?
We can begin our journey with some platforms such as HackTheBox, Tryhackme, etc.
Subscribe to my newsletter
Read articles from Abdul Hakim directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Abdul Hakim
Abdul Hakim
I'm Cloud DevOps Enthusiast | AWS Community Builders.