What is OSI Model | 7 Layers Explained
 Darshan Patil
Darshan Patil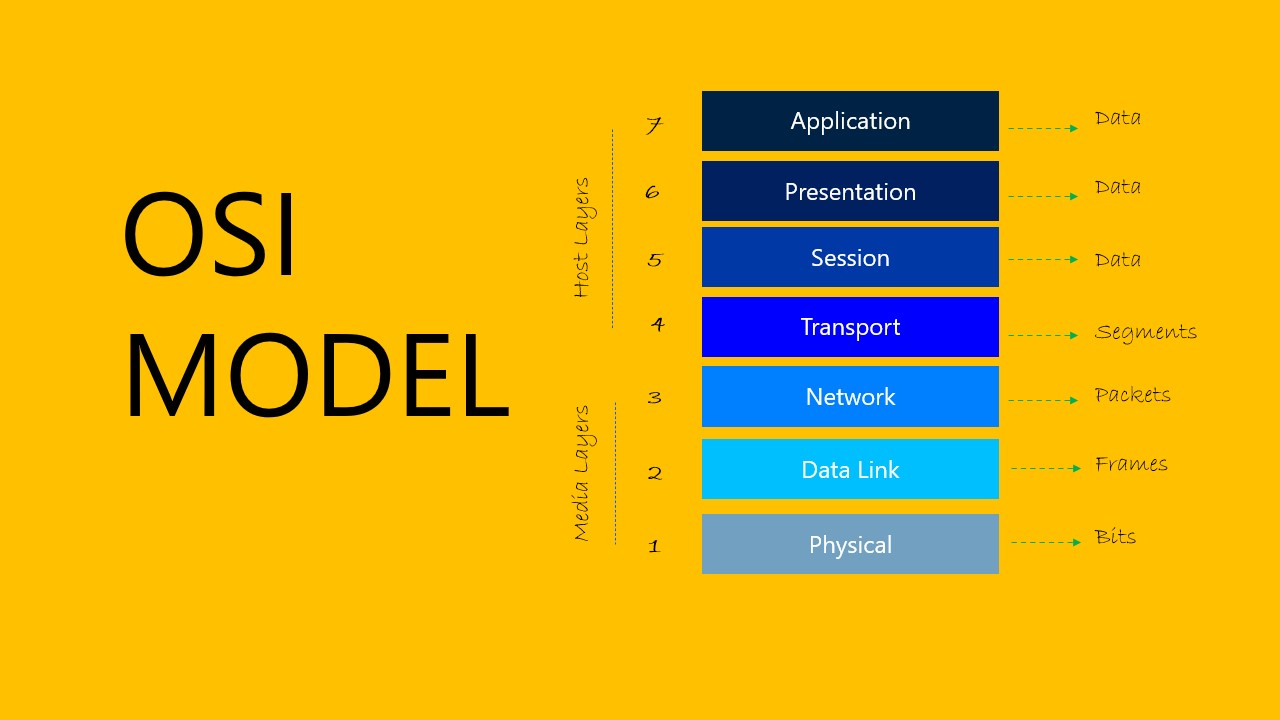
The Open Systems Interconnection model (OSI model) is a conceptual framework that describes how data is exchanged across a network or telecommunications system. This model's goal is to provide a standardised method for devices to communicate with one another.
Why was the OSI model created?
The International Organization for Standardization (ISO) developed the OSI (Open Systems Interconnection) model in the late 1970s and early 1980s to standardise and facilitate communication between various computer systems and networks.
There was no standardisation in the way different computer systems communicate with one another before the development of the OSI model. This made communication between different types of computer systems and networks difficult, limiting the potential for collaboration and interoperability between different organisations and countries.
The ISO began developing the OSI model in 1977 to address this issue. The model's goal was to develop a standardised framework for communication between various computer systems and networks, regardless of their underlying hardware or software.
The OSI model was built on a layered architecture, with each layer in charge of a different aspect of communication. The model was made up of seven layers, each with their own set of protocols and functions. These layers were designed to be modular and self-contained, allowing for system flexibility and interoperability.
The creation of the OSI model was a watershed moment in the history of computer networking because it provided a standardised framework for communication between various systems and networks. Although the OSI model is no longer widely used in practice, it has had a long-lasting influence on the development of networking technologies and standards.
7 Layers of OSI Model

Application Layer (Layer 7)
The Application layer is the closest to the user and the application they are using. it is responsible for the interaction between the user and the network. It deals with application-specific communication between devices, such as sending emails, browsing the web and file transfers.
Presentation Layer (Layer 6)
The Presentation Layer (layer 6) also known as the syntax layer it is in charge of transforming the data into a format which can be transported across the network. Encryption and decryption of data for secure communication such as SSL and TLS take place within this layer.
Session Layer (Layer 5)
The Session Layer (Layer 5 ) coordinates the communication between two networked devices. This involves establishing, managing and terminating connections. It deals with the coordination of communication between devices and the management of data exchange between them.
Transport Layer (Layer 4)
The Transport Layer (layer 4) is in charge of ensuring that data is delivered reliably and efficiently. It is in charge of data segmentation and flow control, ensuring that data is sent in the correct order and that no data is lost.
Network Layer (Layer 3)
The Network Layer (layer 3) is in charge of routing data packets between devices and networks. It is responsible for the logical addressing of devices as well as the routing of data packets through the network. It involves in selecting the best path the data should take to reach its intended destination.
Data Link Layer (Layer 2)
The Data Link Layer (layer 2) is in charge of establishing a dependable link between devices by detecting and correcting errors. It is in charge of sending data packets across the network and establishing logical connections between devices.
Physical Layer (Layer 1)
The Physical Layer (layer 1) is in charge of sending raw data bits over a physical medium, such as a cable or wireless connection. It is concerned with the physical aspects of the network, such as the cables, connectors, and devices used to transmit data.
| Layer No | Layer | Protocol | Devices |
| 7 | Application | HTTP, FTP, SMTP, SSH | Web servers, Mail servers, File servers, DNS servers, and Proxies. |
| 6 | Presentation | SSL, TLS, ASCII | Data Encryption devices, Compression devices, and Codecs. |
| 5 | Session | NFS, SMB, NetBIOS | SBCs and Firewalls |
| 4 | Transport | TCP, UDP | Load balancers, NAT Devices and Firewalls |
| 3 | Network | IP, ICMP | Routers, Layer 3 Switches and Gateways |
| 2 | Data Link | Ethernet, Token Ring, FDDI, PPP, and Frame Relay, MAC | Switches, Bridges and NICs |
| 1 | Physical | Ethernet, Token Ring, FDDI, SONET | Hubs, Repeaters, Transceivers, Cables, Connectors, Fiber Optic Cables, and Network Interface Cards (NICs) |
How does the data flow in the OSI Model?
Human-readable data must travel down the seven layers of the OSI Model on the sending device and then up the seven layers on the receiving end in order to be transferred over a network from one device to another.
For example, Mr Smith wishes to send an email to Ms Potts. Mr Smith composes his message in an email application on his laptop before pressing the 'send' button. His email client will send his email message to the application layer, which will select a protocol (SMTP) and forward the data to the presentation layer. The presentation layer will then compress the data before passing it on to the session layer, which will begin the communication session.
The data will then be segmented at the sender's transportation layer before being broken down into packets at the network layer, which will be broken down even further into frames at the data link layer. The data link layer then sends those frames to the physical layer, which converts the data into a bitstream of 1s and 0s and sends it over a physical medium, such as a cable.
When Ms Potts' computer receives the bit stream via a physical medium (such as her wifi), the data flows through the same series of layers, but in the opposite order. The physical layer will first convert the bitstream from 1s and 0s to frames, which will then be passed to the data link layer. The frames will then be reassembled by the data link layer into packets for the network layer. The network layer will then separate the packets into segments for the transport layer, which will reassemble the segments into a single piece of data.
The data will then flow into the receiver's session layer, which will pass it on to the presentation layer before terminating the communication session. The presentation layer will then decompress the data and pass it up to the application layer. Ms Potts' email software will then receive the human-readable data from the application layer, allowing her to read Mr Smith's email on her laptop screen.
Subscribe to my newsletter
Read articles from Darshan Patil directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Darshan Patil
Darshan Patil
Application Security Engineer | DevSecOps | Cloud Security | Penetration Testing | MLSecOps