Device and infrastructure security made easy
 Kunal Kushwaha
Kunal Kushwaha
A world of complexities
As more and more organizations adopt a microservice architecture, the number of complexities keeps on increasing. Applications talk to multiple different services in order to complete their functions, some of these could be third-party services that are not maintained by the organization. A single application could have multiple dashboards for managing various functionalities such as monitoring, configuring pipelines, creating access tokens, etc.
With so many different services interacting with each other, it is possible for some aspects of the workflow to have a security risk. One of the most common risks, and most exploited is user error and misconfigurations. Having just one line of code or configuration wrong can lead to a critical security vulnerability popping up. These complexities get even more difficult to manage when the applications are scaled.
One way to mitigate user error is by ensuring that only a few trusted individuals have access to specific resources. This is where access control and identity management come into play. Commonly, you could use a traditional username and password or shared secrets to manage control of specific resources. However, these are things that are prone to get leaked intentionally or not.

If these credentials got leaked, it's possible for a malicious actor to access your infrastructure or applications and steal sensitive information such as payment details, introduce threats such as backdoors, delete essential security modules and services, or do a number of other risky activities. Shared secrets such as passwords and keys are the norm, and also the number one source of data breaches.
Teleport - A secure way to access resources
Teleport is an open-source tool for providing zero-trust access to servers and cloud applications using SSH, Kubernetes, and HTTPS. It is completely transparent to client-side tools and designed to work with everything in today's DevOps ecosystem. It can eliminate the need for VPNs by providing a single gateway to access computing infrastructure via SSH, Kubernetes clusters, and cloud applications via a built-in proxy.
Controlling access to infrastructure has always meant a trade-off between security operations and engineering experience. Teleport removes the number one source of breaches, passwords, and shared secrets, and replaces them with easier-to-use and more secure methods. In addition to removing shared secrets, it also enables zero trust, while creating a single source of truth for all your infrastructure.
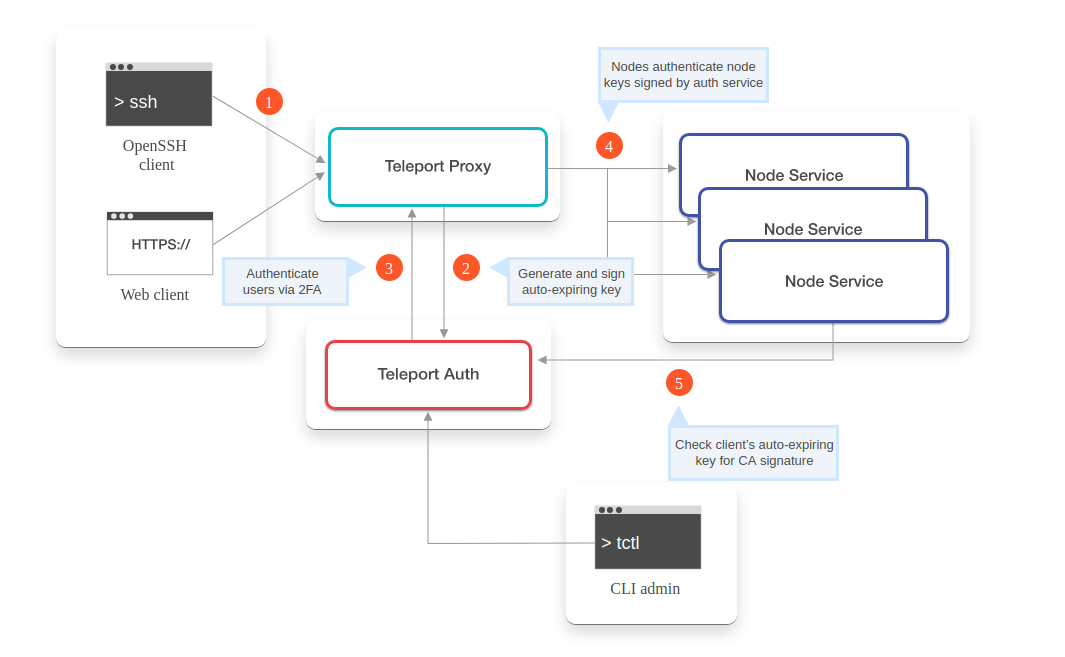
The key concept of Teleport's architecture is the cluster. A Teleport cluster consists of the Teleport Auth Service, Teleport Proxy Service, Teleport agents, and resources that you want to connect to such as Linux or Windows servers, databases, Kubernetes clusters, Windows desktops, and internal web apps. You can learn more about how teleport works here.
Advantages of using Teleport
Let's say you want to access a Kubernetes cluster using kubectl or access an ssh server. Normally to use either of these, you would first need to use a password to access them. However, we already discussed the risks having passwords can carry. Using teleport, you can use the simple teleport CLI utility called tsh to authenticate to your resource via Teleport. It generates a short-lived certificate which will expire after a while, and the certificate would need to be regenerated to regain access.
You can also use the teleport proxy to access a web dashboard from where you can access and manage all your connected services. This dashboard asks you for a username and password, but also requires a 2nd-factor authentication, meaning that even if the password got leaked, attackers would still need access to the 2FA device.

Teleport also recently introduced Machine ID, which essentially stores your device ID and allows you to access services only from that specific device. You can also pair Machine ID with a physical key such as a yubikey or a fingerprint scanner and you will have an additional layer of security, completely eliminating the need for passwords.
Teleport is being used by many companies, some of whom have shared their experiences which you can read here.
Conclusion
Teleport is truly Secretless, replacing insecure shared secrets with phishing-proof access for every engineer and service connected to your global infrastructure. It completely eliminates passwords, and instead uses short-lived certificates in order to make sure your infrastructure is secure.
Get involved
Subscribe to my newsletter
Read articles from Kunal Kushwaha directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
