Segmentation Faults in C
 Manish Kumar
Manish Kumar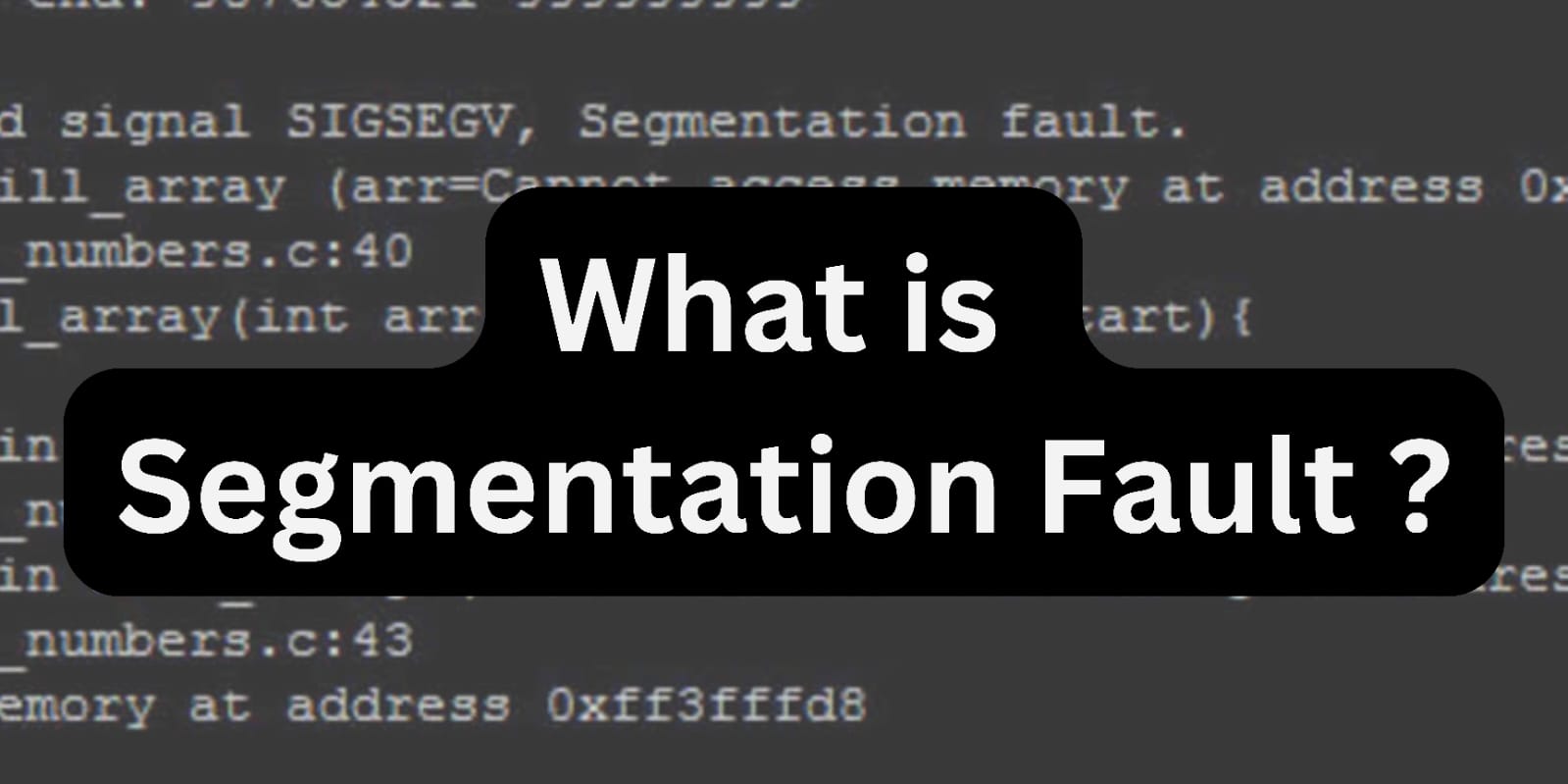
Are you tired of hearing about segmentation faults and feeling like your C programs are constantly crashing? Don't worry, you're not alone. Segfaults can be a headache for even the most experienced programmers, but understanding their causes and how to prevent them can help you avoid future headaches.
What is a Segmentation Fault?
First off, what is a segmentation fault? It's a fancy way of saying your program is trying to access memory that it shouldn't be accessing. You can think of it like a kid trying to sneak a cookie from the cookie jar when they're not supposed to. The parent, in this case, the operating system, catches them and sends them to time out, also known as terminating the program with a segmentation fault error.
How Do Segmentation Faults Happen?
So, how do segmentation faults happen in the first place? Well, they can occur for various reasons, such as trying to dereference a null pointer, writing to a memory location outside the bounds of an array, or using an invalid pointer value. Let's look at an example for each cause.
- Writing to a read-only portion of the memory
int main(){
char *str = "a"; //String literal is read-only
*str = "b"; //Cannot write to a string literal
}
In C or C++, it is possible to accidentally write to a read-only portion of memory by modifying a string literal. When the compiler marks a variable of a string literal as read-only, attempting to write to it will cause a segmentation fault.
- Accessing an array out of bounds
int main(){
int A[10]:
for (int i = 0; i <= 10; i++) {
A[i] = i; //cannot access A[10]
}
}
Arrays indices range from zero to nine, so accessing the tenth index of array a will also result in a segmentation fault as it is considered a memory access violation.
- Using a variable's value as an address
int main(){
int n = 0;
scanf("%d",n); //should be &n
}
To avoid any errors when using the scanf function, it is important to pass in the address of the variable end. If a variable's value is accidentally passed in as an address, it could result in a segmentation fault. Therefore, it is crucial to carefully check the input arguments of the scanf function to prevent any such mistakes.
- Dereferencing a null pointer
int main (){
int *ptr = NULL; //Null Pointer
*ptr = 1;
}
A null pointer typically points to an address that is not a valid part of the process's address space. Hence, attempting to dereference a null pointer can result in a segmentation fault. To prevent such errors, it is crucial to properly initialize pointers and check for null values before dereferencing them in the code.
- Dereferencing or assigning to an uninitialized pointer
int main (){
int *ptr; //Wild Pointer -> uninitialized pointer
*ptr = 1;
}
A wild pointer refers to an uninitialized pointer that can point to a random memory address, leading to undefined behaviour in the code. Attempting to dereference or assign a value to an uninitialized pointer can cause a segmentation fault. Therefore, it is essential to properly initialize pointers before using them in the code to avoid any errors that could potentially cause a segmentation fault.
- Dereferencing or assigning to a freed/dangling pointer
int main (){
int *ptr = malloc(sizeof(int) * 10);
free(ptr); //Dangling pointer - freed pointer
*ptr = 1;
}
A dangling pointer is a pointer that points to a memory that has been freed, making it invalid to dereference or assign a value to it. Attempting to do so can lead to a segmentation fault. To prevent such errors, it is important to carefully manage memory allocation and deallocation in the code and avoid accessing memory that has already been freed, which could result in dangling pointers and potential segmentation faults.
- Buffer Overflow
int main (){
char s[3];
strcpy(s, "hello");
}
A buffer overflow occurs when a program writes data to a buffer and exceeds the buffer's capacity, overwriting adjacent memory locations. For instance, if a variable 's' is defined to hold only three characters and the program attempts to copy a string like "hello" to the buffer of 's', it can cause a buffer overflow, resulting in a segmentation fault. To avoid such errors, it is essential to ensure that the buffer size is sufficient to hold the data being written to it and implement proper bounds checking to prevent buffer overflow vulnerabilities in the code.
- Stack Overflow
int foo() {
return foo();
}
A stack overflow occurs when a program runs out of the allocated space in the call stack. This is often caused by excessive recursion or deeply nested function calls. In simpler terms, it's like a stack of plates that keeps piling up until it reaches the ceiling and spills over. When the stack pointer exceeds the allocated stack space, it can cause a stack overflow resulting in a segmentation fault. For example, if the function "foo" continuously calls itself without an exit condition, it keeps allocating more space on the stack until it overflows and crashes the program, ultimately resulting in a segmentation fault.
How to Prevent Segmentation Faults
One way to prevent segmentation faults is to follow best practices for memory management, such as initializing all pointers, checking for null pointers before dereferencing them, and using bounds-checking functions when working with arrays. It's like putting on your seatbelt before going for a drive - it may take a little extra effort, but it can save you from a lot of pain later on.
Dealing with Segmentation Faults
But let's be real, sometimes segmentation faults just happen. It's like walking on a tightrope - even if you've done everything right, one misstep can lead to a fall. When that happens, the operating system generates a core dump file, which can be used to identify the cause of the error. It's like leaving a trail of breadcrumbs to help you find your way back to where you went wrong.
Conclusion
In conclusion, segmentation faults may be a pain, but they're not the end of the world. By understanding their causes and following best practices for memory management, you can reduce the likelihood of encountering them. And if all else fails, there's always Valgrind (It is a powerful open-source software tool that is used for debugging and profiling applications on Linux and other Unix-like operating systems.) to help you identify and debug your errors. So keep calm, code on, and may your programs run smoothly (with no segfaults in sight!).
Subscribe to my newsletter
Read articles from Manish Kumar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Manish Kumar
Manish Kumar
I am a Software Engineer. Currently, I am doing my Master's in Computer Application. Right now, I am exploring DevOps and AI. Also, I am an active contributor to Open Source.