E1: Intro to Offensive Security
 saurabh sharma.
saurabh sharma.
introduction and a foreword.
This room provides an opportunity for you to get hands-on experience of breaking a hypothetical banking system, by gaining access to a critical page that was public by design, but not indexed anywhere on the website. Additionally, you will become familiar with a useful tool called gobuster.
task 1: hacking your first machine.
When you click on the "Start Machine" button, it will load a split view in your browser with a working Linux machine. This machine can be used to access a website http://fakebank.com, which we will be fiddling around with henceforth. The website is already open on the Firefox browser, but as you can see, our bank balance is quite thin – we will be changing that.
To accomplish this, we will use a tool called GoBuster. If you have followed the link to their GitHub repository, you may already know that GoBuster is a useful tool for brute forcing website URIs among other things.
It is common for websites to have special admin portals for website maintainers and employees, and brute forcing web directories can often lead us to interesting pages.
Let's open a terminal and enter the following command:
gobuster -u http://fakebank.com -w wordlist.txt dir
This command calls gobuster, the -u is called a flag, and it tells gobuster the target URL, i.e. the URL of the webpage you want to brute force. The -w flag gives gobuster the path to a wordlist file. dir is the mode in which you want to run gobuster, it makes gobuster use the directory/file enumeration mode.
Press Enter ↵ and let it run.
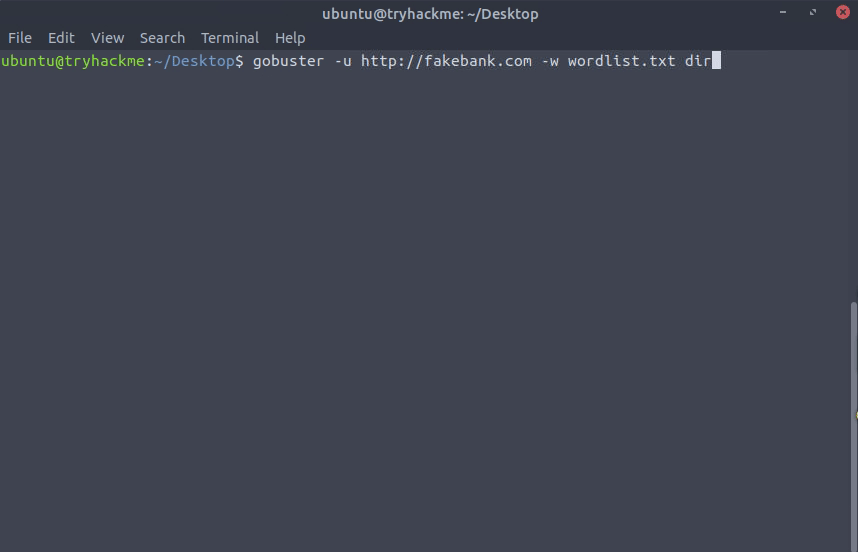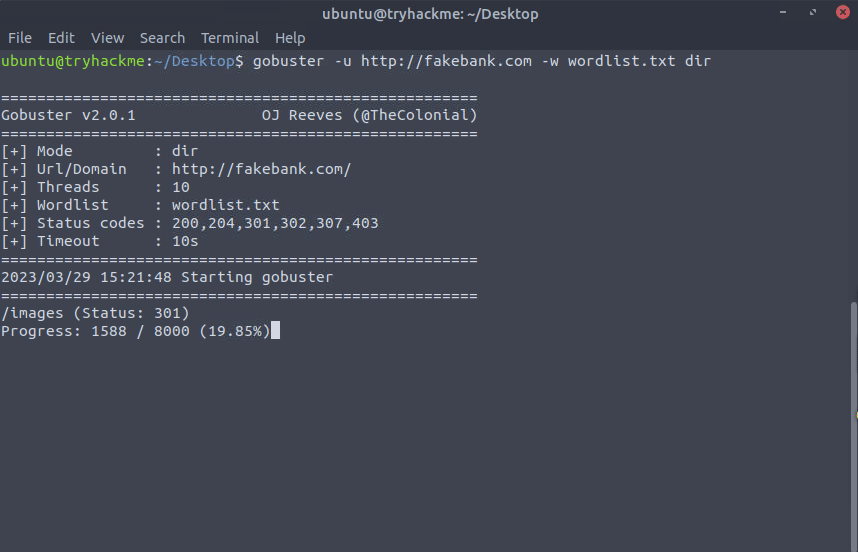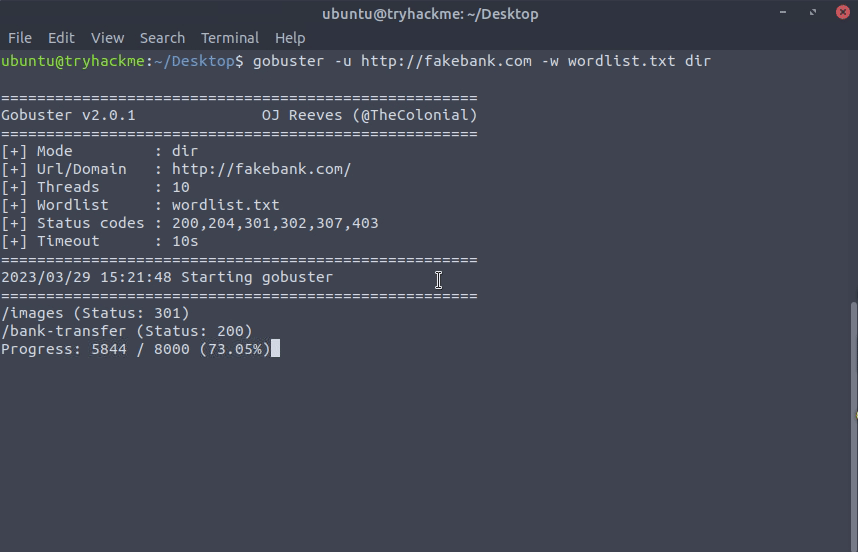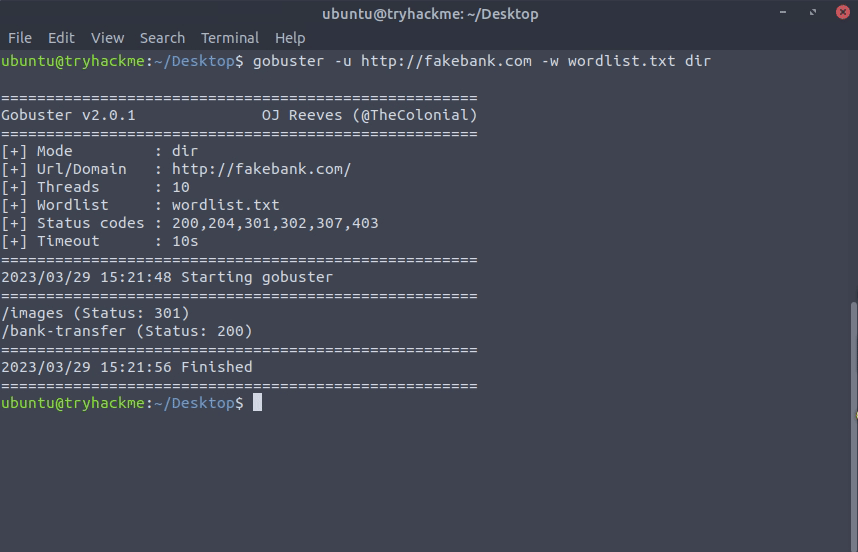
Once the execution is complete, you will notice that gobuster has discovered two directories under the URL http://fakebank.com. These are:
imageswithstatus code: 301forMoved Permanently.bank-transferwith astatus code: 200forSuccess.
I don't know about you, but bank-transfer sounds more promising to me and I will visit it before I check out images, especially given the status code 301.
Here's how http://fakebank.com/bank-transfer looks.
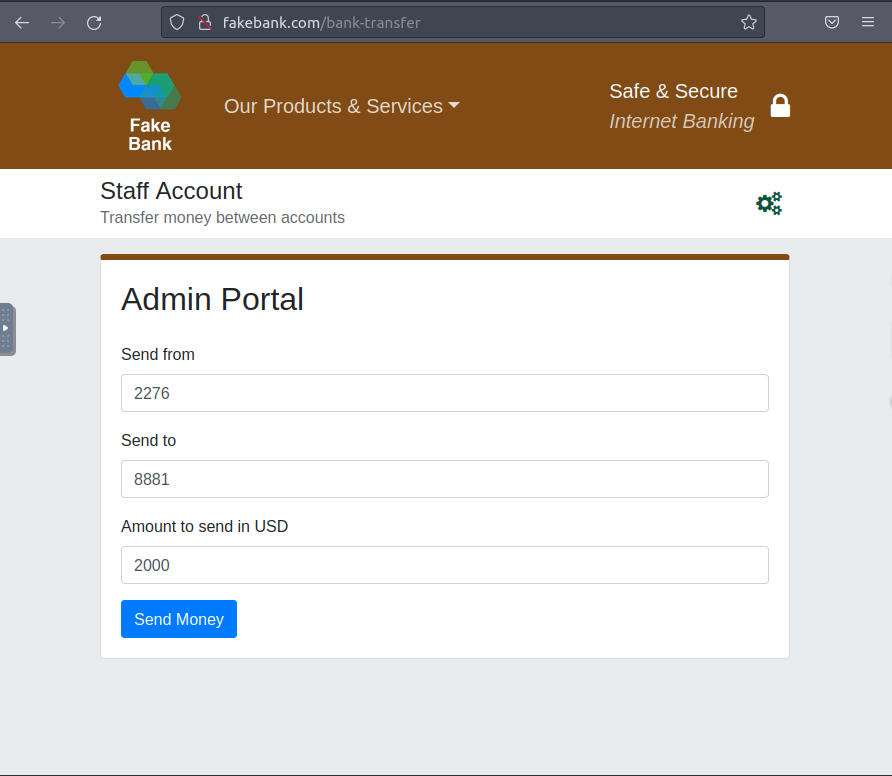
It has a form, titled Admin Portal, which apparently would allow a staff member to transfer money between accounts!
Finding such an unashamedly glaring loophole in something as critical as a bank's infrastructure would typically require a time machine. However, even though this is unrealistically simple, I hope it makes you appreciate how a tool like Gobuster simplifies the process and helps you discover something that would otherwise be difficult to stumble upon.
Now, let's complete the task to clear the room.
Transfer $2000 from the bank account 2276, to your account (account number 8881).
To do this, populate the form as shown above, set the following-send from: 2276, send to: 8881, and amount to send in USD: 2000. Finally, click on Send Money.
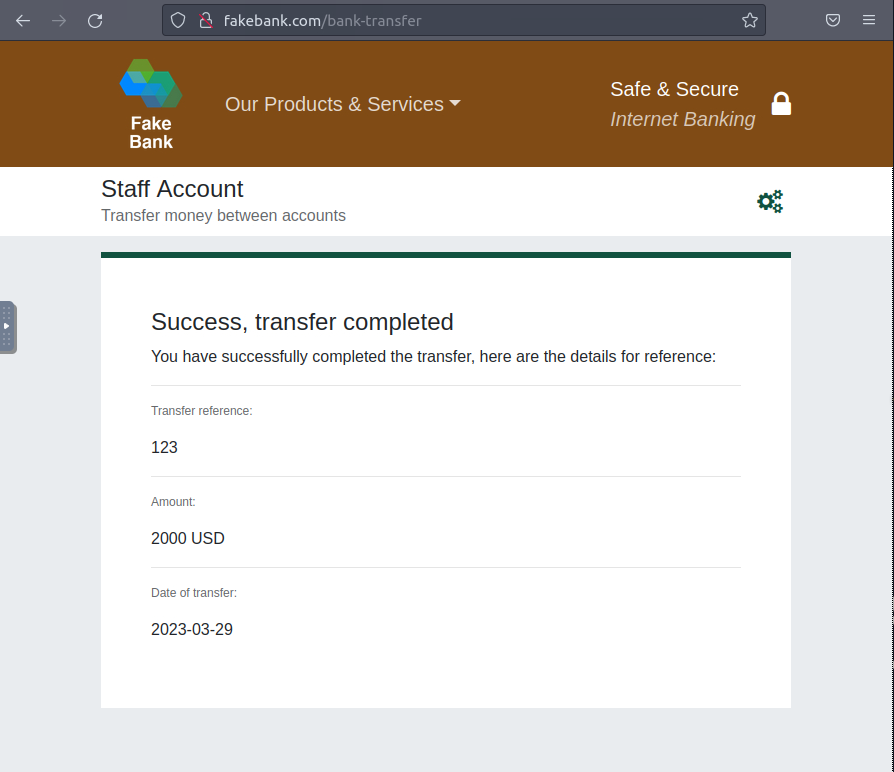
You will be greeted by a transfer completion message as shown in this screengrab below:
After navigating back to the bank's homepage at http://fakebank.com to check our account balance, we can see that we now have that flex money. Additionally, a new active div congratulates us for clearing the room and provides the answer flag. The transaction we made through the "admin portal" can be seen in the list of transactions.
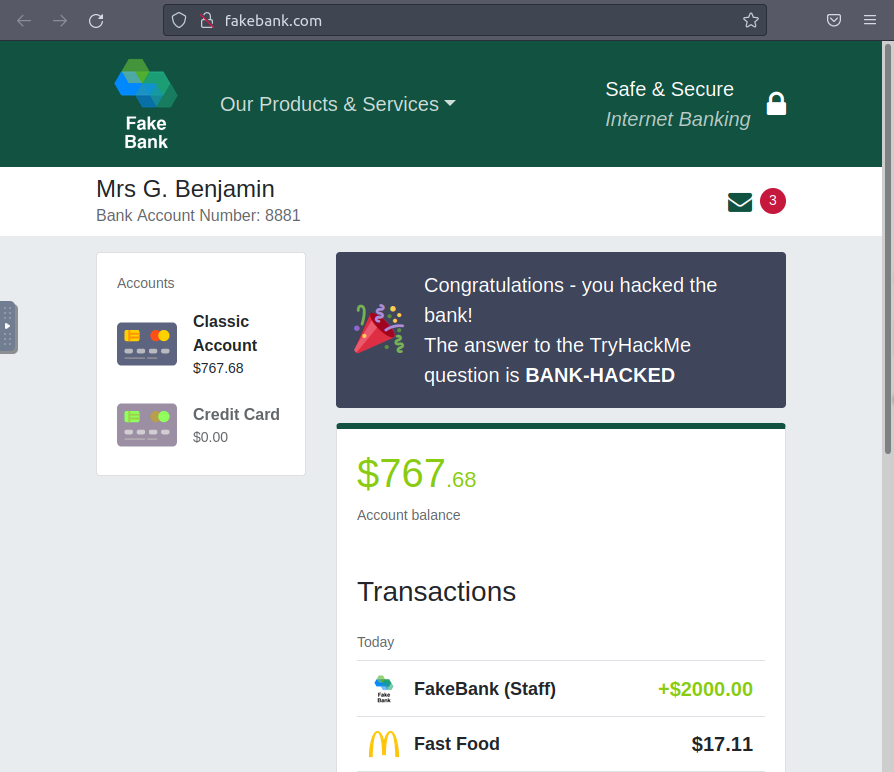
Congratulations, you have hacked into the first piece of (hypothetical) infrastructure! To recapitulate, you used gobuster to find a directory in the website which wasn't necessarily meant for public view. You gained access to it, impersonated FakeBank (Staff) and transferred the money into your account.
task 2: what is offensive security (reading)
This section talks more about offensive security and compares it against defensive security.
More formally speaking, offensive security is a term that describes a proactive and aggressive approach to securing networks and systems from cyber threats by actively seeking out vulnerabilities and weaknesses. Offensive security involves simulating real-world attacks and attempting to penetrate systems, networks, and applications to identify and exploit security flaws. The ultimate goal of offensive security is to seek out threat actors and attempt to take down their operations.
Red-teaming is an intriguing area of offensive security where you adopt the role of an attacker and adopt an aggressive approach to testing and breaking your system. This provides you with valuable insight into the attacker's thought process, enabling you to identify and fix vulnerabilities, as well as strengthen your overall infrastructure security.
Offensive security can be contrasted with defensive security, which is a reactive and passive approach that focuses on protecting systems and networks from attacks by implementing security measures such as firewalls, antivirus software, encryption, etc. Defensive security aims to prevent or minimize the impact of attacks, while offensive security aims to disrupt or eliminate the source of attacks.
task 3: careers in cybersecurity (reading)
This section lists some testimonials which are really inspiring if you ask me. I encourage to read more about these people's journeys to motivate and inspire yourselves. This section also highlights the various careers that exist i this domain.
tldr;
In this exercise, you'll be using a tool called Gobuster, along with a wordlist provided by the TryHackMe team, to perform a brute force attack on a hypothetical bank's website. Upon running the Gobuster report, you'll come across a URI called bank-transfer, which happens to be a critical page that should have been kept private. Surprisingly, this page allows you to transfer money from a random account into your own. Simply fill the form, transfer $2000 into your account, and switch back to the homepage to check your balance. Upon a successful transfer, your balance will reflect the new funds, and TryHackMe will congratulate you and provide the answer, which is BANK-HACKED.
Subscribe to my newsletter
Read articles from saurabh sharma. directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

saurabh sharma.
saurabh sharma.
472783B373EF3BCFAAE1C7029A447B9E9D18DF48