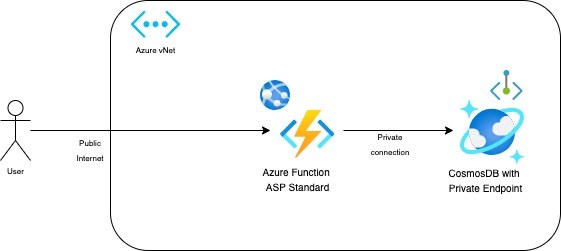
Secure Connection from Azure Function to Azure CosmosDB
 Amresh Krishnamurthy
Amresh KrishnamurthyTable of contents

About
This article is about having a secure network connection to Azure CosmosDB from an Azure Function. Though this article uses Azure CosmosDB, the same concept applies to the other Azure PaaS Services that support Private Link.
Prerequisites
Microsoft Azure Account, Basic understanding of Subscription and Resource Group
Azure Resources Used
vNet - Azure Virtual Network to isolate PaaS Resources
AzureCosmosDB - Microsoft offers the first 1000RU free which is good enough for this setup
Azure Functions - Azure Function App is hosted in Azure App Service B1
Setup
Azure Virtual Network and Subnets
Create a virtual network and two subnets - one for each Azure CosmosDB & Azure Function
Create a new vNet in the same Resource Group as we have the PaaS resources. Azure vNet by default adds a "default" subnet on creation
Add two subnets under the vNet. Subnets can be either be added when the virtual network is created or later using the "subnets" tab under "settings" section.
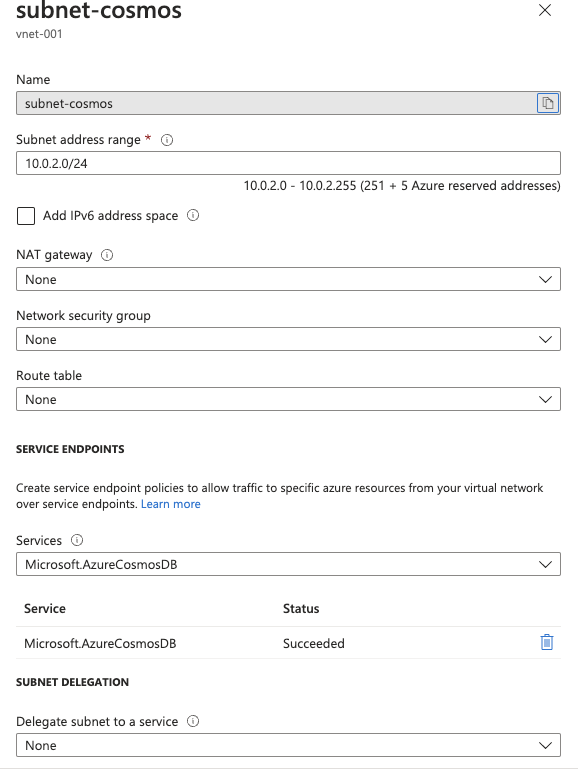
Subnet - 1
Added subnet-cosmos by choosing an address range. Optionally subnet provides service endpoint targets. This restricts the subnet communication to specific resource types. Here it is restricted to Cosmos DB
Subnet-2
Added subnet-function with a different address space. These are the current subnets that are created in the Virtual network.
Azure CosmosDB
Create a sample Azure CosmosDB with a sample document to test. Add a private end-point connection
Assuming there is an active Azure Subscription and a Resource Group has been created
Azure CosmosDB with SQL is used for this exercise and one of the steps in the DB creation is Networking as seen below,
- Note, the Portal and Local IP access is also denied
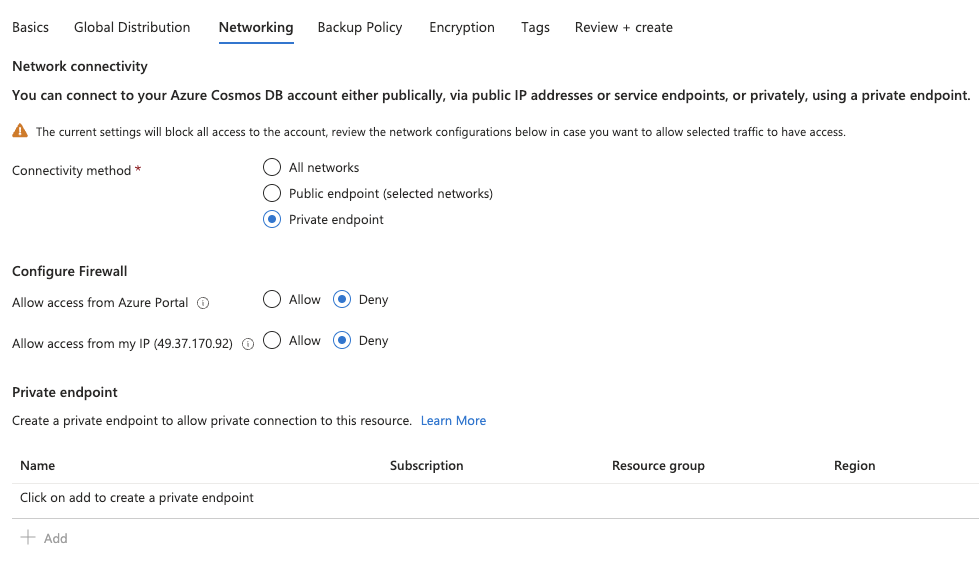
Add a private endpoint by using the +Add button above, and provide
A name for the private endpoint
Choose the Virtual Network and subnet created in the previous step
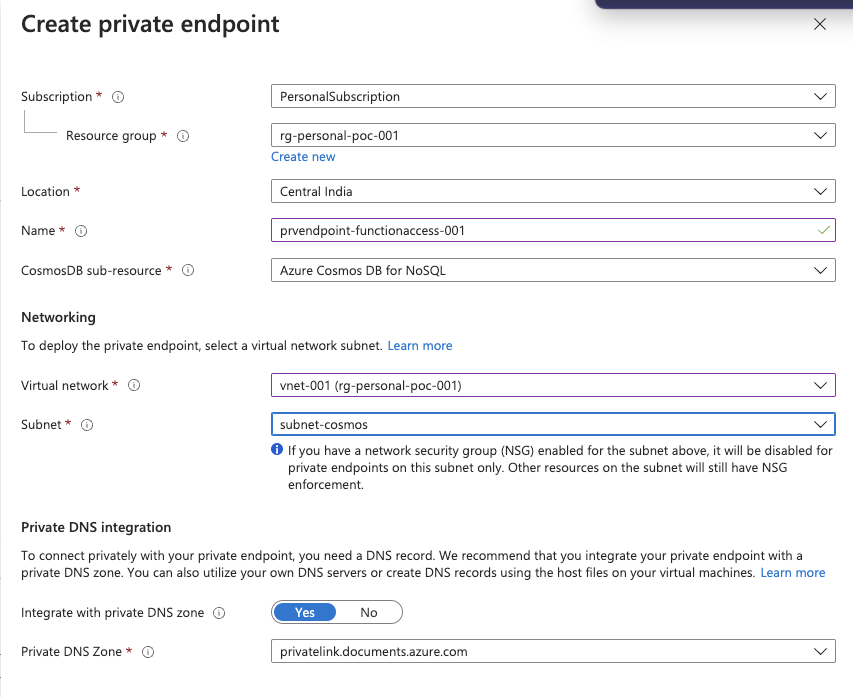
This configuration blocks Public & Azure portal access and the connectivity can now happen only using the private endpoint configured. You can (add) and view the private endpoints created in the Networking Tab -> Private Access in the cosmos db
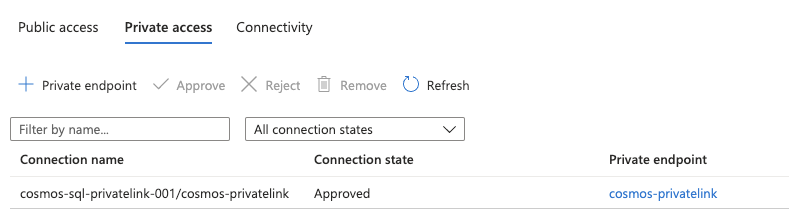
Added a Database called "ProductCatalog" and a collection "Product" with a sample document. This document will be accessed by Azure Function.
Azure Function
Create an Azure Function that has a private inbound connection over a Virtual Network to an Azure CosmosDB
Created a sample Azure function, and used Azure Function VS Code plugin to deploy this as a function app into Azure. Ensure to add a local settings file with the appropriate CosmosDB connection string.
This plugin by default deploys to a free tier App Service Plan. We may have to create an Azure App Service with a minimum B1 tier (which supports networking options) and use the same when prompted while using the plugin.
Once the function app is deployed into Azure, use the networking tab in the portal to set inbound and outbound connections,
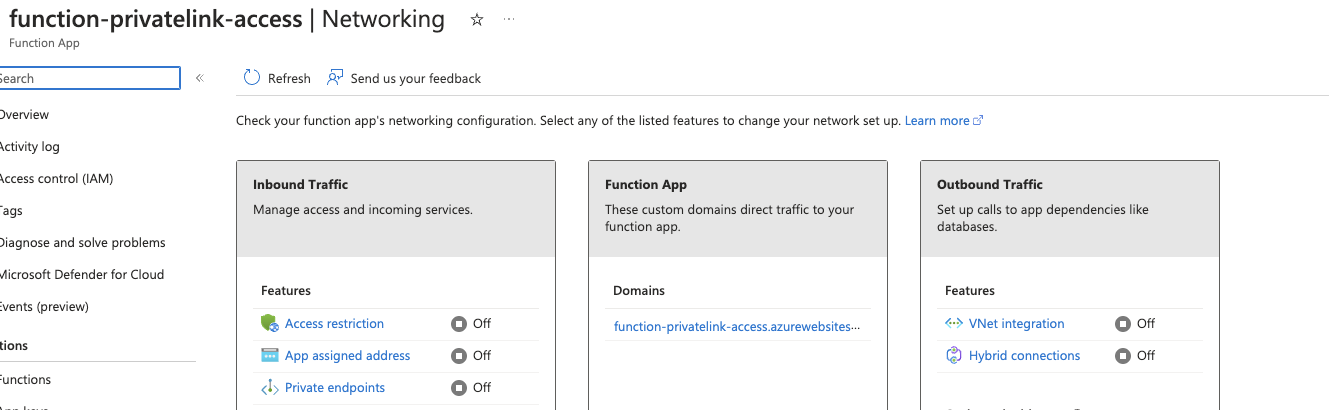
Inbound traffic is open to the internet. Click on Vnet Integration under Outbound traffic to choose a subnet "subnet-function" created under vNet.
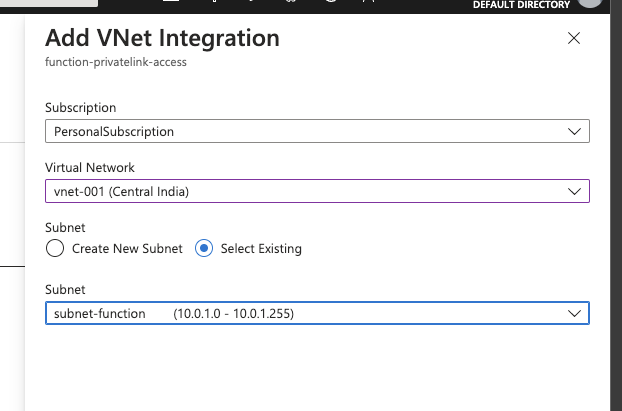
Click on VNet Integration and continue the workflow to choose a subnet that was created earlier and save and refresh the connection to check the status.
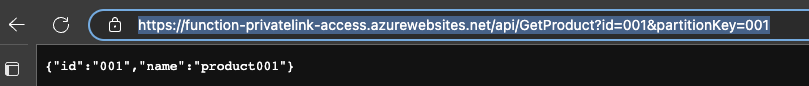
Voila !! This creates a private n/w connection between the Azure function and Azure CosmosDB to fetch the sample data
Subscribe to my newsletter
Read articles from Amresh Krishnamurthy directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Amresh Krishnamurthy
Amresh Krishnamurthy
👋 Hi, I’m Amresh Krishnamurthy 👀 I’m interested in learning, building distributed systems, serverless architecture, sharing knowledge 🌱 I’m currently learning distirbuted cache, graph database Pronouns - He/Him 📫 reach me at https://twitter.com/amreshkris
