Debugging via Decompilation: Reverse Engineering an APK
 Joe Roskopf
Joe Roskopf
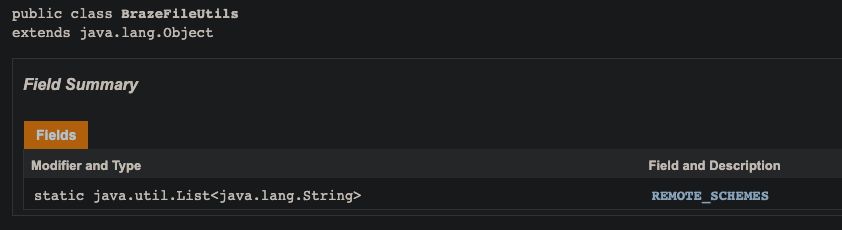
Recently, while looking at integrating Braze into an application, I came across a field in BrazeFileUtils called REMOTE_SCHEMES and I was curious to see what the values were that Braze considered for REMOTE_SCHEMES.
Looking at the docs, there was no reference to what the schemes were, so I thought I'd do a little digging myself to see if I could infer what the value was for this field.
Setup
The first step of the process was to create a new Android application that include the dependency I wanted to look at, namely BrazeFileUtils. This can be accomplished by bringing the Braze SDK into our application via
implementation 'com.appboy:android-sdk-ui:24.3.0'
implementation 'com.appboy:android-sdk-location:24.3.0'
After that, I generated a debuggable apk via ./gradlew :app:assembleDebug. Once I had a debug APK in hand, the next tool I brought in to help was Apktool, a tool for reverse engineering Android apk files.
Decompiling
By following the instructions on the site, and downloading the latest Apktool JAR file, we are ready to decompile the debug APK we generated earlier. I decompiled the apk via
java -jar apktool.jar d app-debug.apkwhereapktool.jaris the jar downloaded from the Apktool website andapp-debug.apkis the debug APK generated from the previous step.After decompilng via Apktool, we are ultimately left with .smali files, the assembly language used by the Android Dalvik Virtual Machine; usually created by decompiling. We are getting close though! If we open up the new
app-debugfolder created from Apktool, we can look inside/smali/com/braze/support/BrazeFileUtils.smaliand see the field we want! Unfortunately, we don't see the values for it yet.
The next step is to use a Dex (Smali) to Java decompiler to get the code in a format a little more digestible by a human. For this, we will use jadx. Following the instructions in the readme, and installing jadx via brew (
brew install jadx), we are ready for the next step.After installing jadx, we can finally get the Java code from the .smali files generated earlier via
jadx -d out app-debug/smali/com/braze/support/BrazeFileUtils.smali.Usage is from the docs on the site as follows:jadx[-gui] [options] <input files> (.apk, .dex, .jar, .class, .smali, .zip, .aar, .arsc, .aab) options: -d, --output-dir - output directory
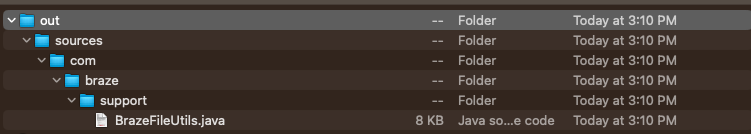
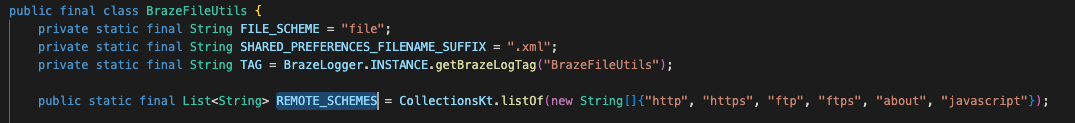
After opening up the Java file, we can finally see what the remote schemes are!
In conclusion, we utilized Apktool and jadx to reverse engineer source from a debug apk. This can be useful when a 3rd party tool that you have to utilize doesn't expose certain things about their SDK.
Subscribe to my newsletter
Read articles from Joe Roskopf directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Joe Roskopf
Joe Roskopf
Hey! I’m Joe! I’m an Android developer who is passionate about the human side of software development.