What is MITRE ATT&CK Framework?
 Suraj Tripathi
Suraj Tripathi

The MITRE ATT&CK framework is a comprehensive matrix of Adversarial Tactics, Techniques, and Common Knowledge used by threat hunters, red teamers, and defenders to better classify attacks and assess an organization's risk.
Tactics Vs Technique vs Procedure.
• Tactics are the adversary’s technical goals.
• Techniques are how those goals are achieved.
• Procedures are specific implementations of techniques.
Think of these in terms of your day:
You have several sorts of major things you do every day that can be split into broad categories or goals. These could be things like getting to work safely or staying healthy. These are your tactics. You have different ways to meet these goals. For something like getting to work safely, you may drive to work. You might walk to work. You may even have a mixed commute of driving, walking, and public transit. In terms of staying healthy, you may employ techniques like washing your hands, taking a walk, or lifting weights.
Note:- That the same technique of taking a walk was used in both tactics of staying healthy and getting to work safely. Techniques may span multiple tactics.
We will continue with “taking a walk” as our technique since it spans both tactics. The map you would use with the turn-by-turn directions for your walk could be a procedure for the technique of taking a walk. This is the basic organizational principle of the MITRE ATT&CK Framework, so it’s important to commit these to memory.
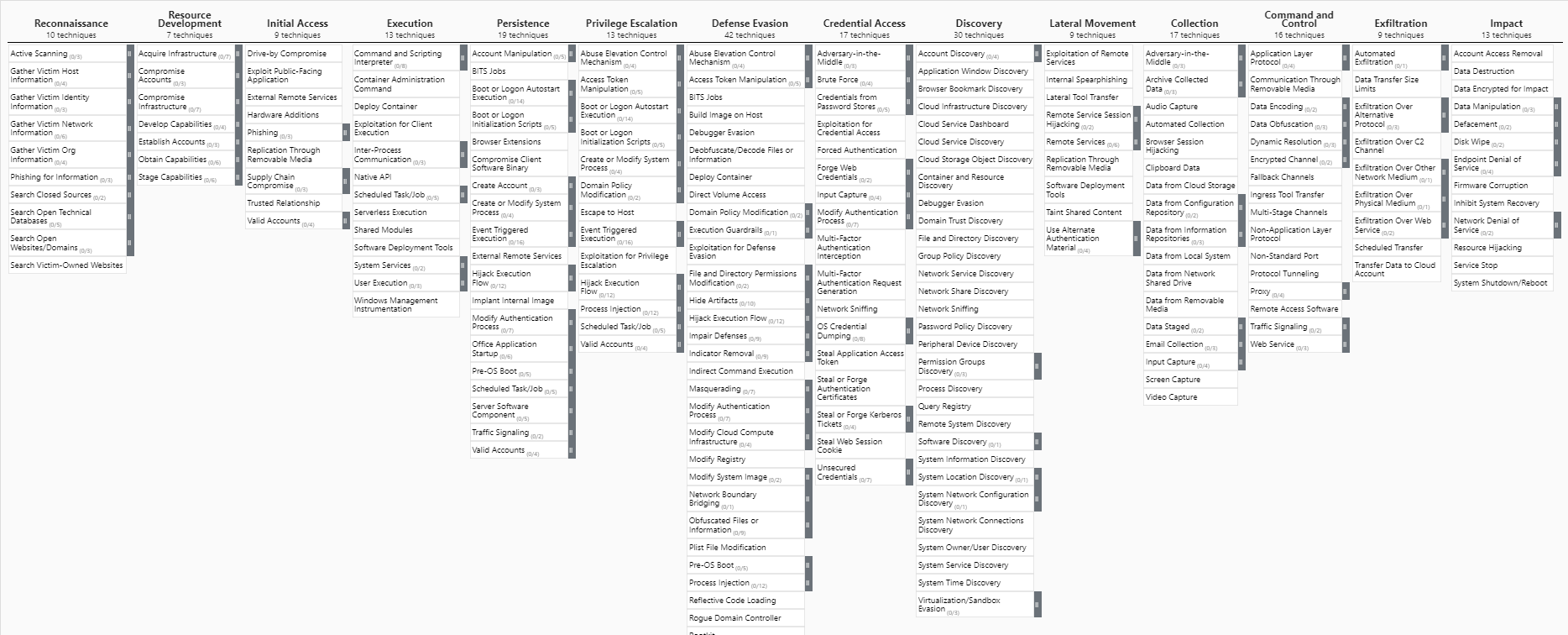
The MITRE ATT&CK Framework is a collection of techniques used by attackers during a breach. The ATT&CK Matrix breaks the techniques down into the following tactics:
• Reconnaissance
• Resource Development
• Initial Access
• Execution
• Persistence
• Privilege Escalation
• Defence Evasion
• Credential Access
• Discovery
• Lateral Movement
• Collection
• Command and Control
• Exfiltration
• Impact
MITRE ATT&CK helps in Operationalizing Threat Intelligence, Detection & Analytics and Adversary Emulation & Red Teaming.
Subscribe to my newsletter
Read articles from Suraj Tripathi directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Suraj Tripathi
Suraj Tripathi
I am a Information security expert with experience in Data Security, Application Security, Penetration testing, Risk Management.