Get bearer token using postman & Azure REST API- Grant type as Client Credentials
 Suraj Somani
Suraj Somani
In this post, we will go through steps to get a bearer token which will be used to invoke Azure-provided APIs for various services. We will also learn some basics of using the Postman client app.
Run Postman application- first create a new environment with some name like "Azure config environment" and add variables tenantid, client_id, client_secret, resource, grant_type as below. We will make use of these variables in API requests.
Note- using these variables is optional and you can directly put values in Postman request, but I prefer variables for reusability purposes.

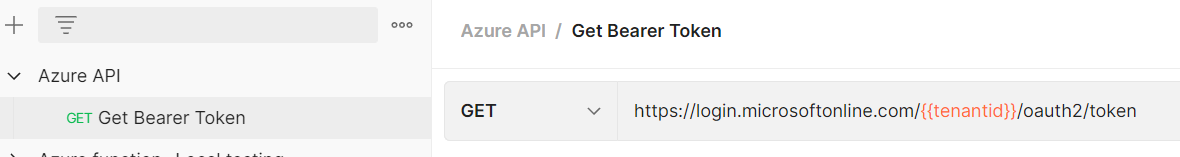
To get the bearer token, we need to send a request (GET/POST both will work) to the below API
https://login.microsoftonline.com/{{tenantid}}/oauth2/token
Create a new collection and add a request- Get Bearer Token with the above URL.
Make sure you have selected the environment as Azure config environment.

Go to the request body tab and select x-www-form-urlencoded. Add key-value pairs as shown below-

To get the Tenant id, go to Azure active directory and on the overview page you can see the tenant id. Copy it and set this value in environment variable.

To get clientId, first, we need to register an app in Azure active directory. Search for and select Azure Active Directory. Under Manage, select App registrations > New registration.

Enter the app name and click register.

Once we registered the app, go to the app and we can get clientId as below. Copy it and update in Postman environment variable.

To add a client secret, go to certificates and secret tab and click on add new secret.
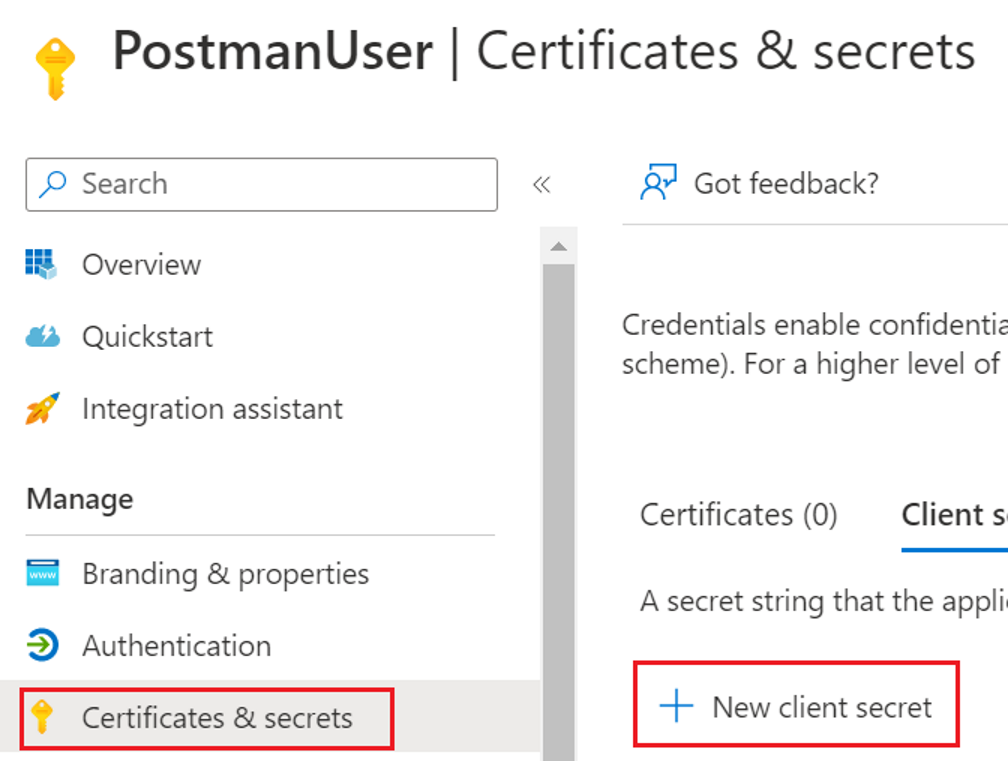
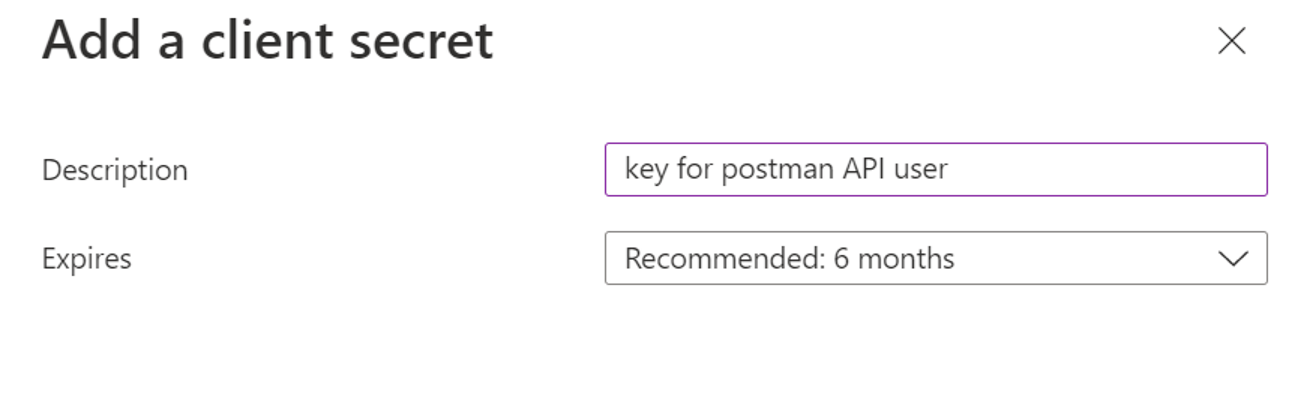
Add description for secret and click on add.
Once added, you will see the client secret value, copy it and update it on client_secret environment variable in Postman. Note that this secret value is visible only at the time of creation, you will not be able to copy it afterwards.

You can add required permissions to this app from API permissions tab.

Now go to postman environment and set variables as resource= "https://graph.microsoft.com", grant_type="client_credentials". Click on Save. Note that resource value can be changed based on the resource type for which you want to use this bearer token. Make sure your app has API permissions for the resource you are using in the request.
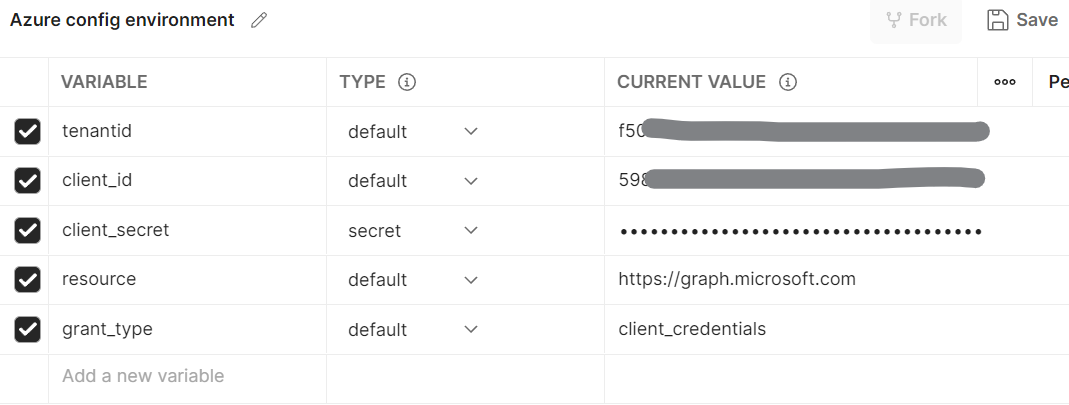
Your environment variables will look like this-
Now go to API request and hit send button, you will get the bearer token in response as below. This token can be used to call graph APIs.

Below are some of the commonly used Azure services and resource parameter value to be used while acquiring to access those services-
Resource Type | Resource parameter value |
Graph APIs | |
Azure storage account | |
Azure databases (all types- SQL database, dedicated pool, serverless) |
Extra Tip-
If you don’t want to copy this token manually every time, then you can automatically save it to the environment variable and use that in other requests (no manual copy-paste required).
Create a new environment variable - "access_token".
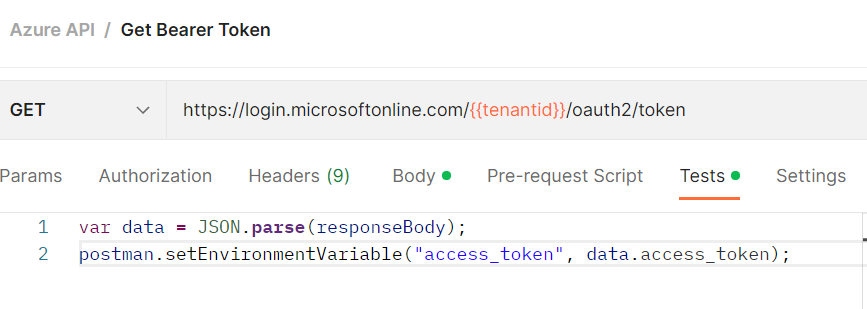
Go to request > Tests and add the below code. It will read access_token from the response and store in an environment variable.
var data = JSON.parse(responseBody);
postman.setEnvironmentVariable("access_token", data.access_token);
In this blog, we saw how to get bearer token from azure AD using postman. Thanks for reading.
Keep Learning !
Subscribe to my newsletter
Read articles from Suraj Somani directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Suraj Somani
Suraj Somani
I am 10+ years experienced IT professional having expertise in various Azure technologies. I am certified Azure Developer & Azure Data Engineer, having vast experience in building cloud solutions.