Web Hacking: Cookie Tampering, Directory Traversal, Session Hijacking, Authentication Bypass, Brute Force Attack
 Han
HanWeb hacking is a common technique used by attackers to exploit vulnerabilities in web applications. In this article, we will explore some common types of web attacks, including cookie tampering, directory traversal, session hijacking, authentication bypass, and brute force attacks.
Cookie Tampering
Definition
Cookie tampering refers to the malicious act of modifying cookie values used in web applications.
Purpose
Cookies are stored on the client side and are used to maintain the state between the client and server (such as authentication, session management, user identification, etc.).
Prevention
Authentication and encryption for cookies
Filtering and validation for input values
Filtering for output values
Appropriate cookie settings based on the purpose and duration of use
Example
Using Burp Suite:

Let's confirm a successful login. The response status code is 302.
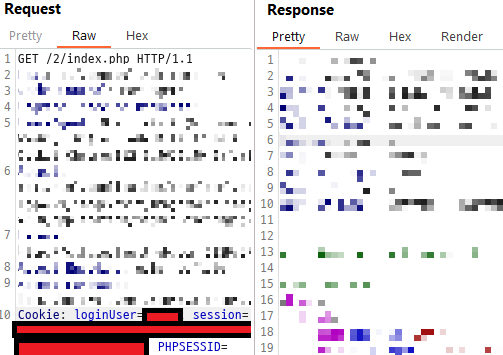
A status code in the 300s indicates redirection. This means that the user has been redirected to another webpage.
Let's check the cookies. We can see that the username is stored in the cookie, rather than using a session to differentiate users.
By changing the value of loginUser to "admin," we can steal authorization through cookie tampering.
Directory Traversal
Another name
- File Path Traversal
Definition
Directory traversal is an attack that involves guessing the paths of files or directories within a website in order to directly access those files or directories.
Prevention
To prevent these vulnerabilities, it is important to:
Limit access to files or directories
Filter and validate input values
Filter output values
Example
Using Burp Suite:
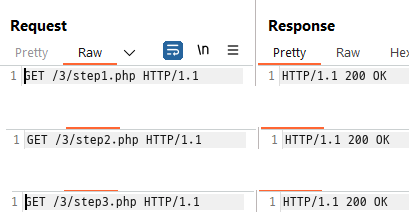
If the homepage is split into step1 and step2, you can try to access step3 directly without logging in.
Session Hijacking
Another name
- Session Fixation
Definition
Session hijacking involves an attacker acquiring a valid session and then using that session to impersonate the user or access other accounts.
Prevention
Proper session management is essential:
Generate session IDs using random and unpredictable values
Set a reasonable session expiration time
Use encrypted protocols such as SSL or TLS to transmit session IDs
Example
The attacker monitors network traffic to capture the user's session ID.
The attacker uses the stolen session ID to log in to the website as an authenticated user.
The attacker can now perform malicious actions with the user's privileges.
Authentication Bypass
Another name
- Login Bypass
Definition
Authentication bypass occurs when login is possible without verifying the ID and password or when login can be done through other means.
Prevention
- Authenticate and verify login credentials
Example
The attacker discovers a vulnerable authentication mechanism (e.g., weak password policy, missing input validation).
The attacker finds a way to bypass the authentication mechanism (e.g., SQL injection, using default passwords, tampering with authentication tokens).
The attacker bypasses the authentication process and gains unauthorized access to the system.
The attacker can now steal information or manipulate the system without being authenticated.
Brute Force Attack
Definition
A brute force attack is an attack that guesses passwords by trying all possible combinations.
Prevention
Encourage users to use safe passwords
Use blacklisting to lock accounts after a certain number of failed logins
Add security features such as CAPTCHA
Example
Using Burp Suite:
Although the Intruder function in Burp Suite can be used, it is much faster to use Python:
import httplib2
# Suppose that the GET request is made to example.php?otpNum=0000.
# URL of target website (in this case, example.php)
url = "<http://example.php>"
# httplib2 instance creation
http_obj = httplib2.Http()
# Range of otp_num (0000 to 9999)
for otp_num in range(10000):
# Format otp_num into a 4-digit number (e.g., 0035)
otp_num_formatted = f"{otp_num:04d}"
# Add otp_num parameter to GET request
request_url = f"{url}?otpNum={otp_num_formatted}"
response, content = http_obj.request(request_url, method="GET")
# Depending on how the results are found, the processing can be modified.
# For example, if the server returns a specific message, it can be checked.
# Use print(content) to check and set success conditions.
if not b"Login Fail" in content:
print(f"Success! OTP number is: {otp_num_formatted}")
break
else:
print(f"Failed for OTP number: {otp_num_formatted}")
Subscribe to my newsletter
Read articles from Han directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
