Ansible vault Tutorial
 Piyush T Shah
Piyush T ShahInfrastructure as code (IaC) is the process of automating the infrastructure management and deployment process using code. One of the key challenges with IaC is the need to manage sensitive data (aka secrets) such as passwords, API keys, and other credentials. Ansible Vault is an open-source, free tool that helps with this problem.
So what exactly is Ansible Vault?
Ansible Vault is a command-line tool that allows you to encrypt sensitive data such as passwords, API keys, and other credentials. Ansible Vault uses symmetric encryption, which means that the same password is used for both encryption and decryption. The encrypted data is stored in a YAML file and can be used by Ansible in the same way as unencrypted data. Ansible Vault can be used to encrypt individual variables or entire files.
Ansible Vault vs Leading Industry Solutions
Amazon AWS offers a service called AWS Key Management Service (KMS) that allows you to encrypt data using keys that are managed by AWS. KMS can be used to encrypt data at rest and in transit. Microsoft Azure offers a similar service called Azure Key Vault. Both KMS and Key Vault are cloud-based services that are designed for use with cloud infrastructure. They are well suited for organizations that are using cloud services and need to store sensitive data in the cloud.
Ansible Vault, on the other hand, is a command-line tool that is designed for use with on-premises or cloud infrastructure. It is well suited when you are managing your own infrastructure and need to store sensitive data locally. It is not recommended for enterprise-grade or production environments. Ansible Vault is also open source, which means that it is free to use and can be customized to meet specific needs.
When to use which vault?
If you are using cloud services and need to store sensitive data like passwords, tokens and keys in the cloud, then Amazon AWS KMS or Microsoft Azure Key Vault may be the best option. These services are cloud-native solutions designed for use with cloud infrastructure and provide a high level of security and scalability.
If you need to manage and store sensitive data locally, then Ansible Vault may be the best option. Ansible Vault is a simple and effective way to encrypt sensitive data and can be customized to meet specific needs. It is also open-source, which means that it is free to use and can be integrated with other tools.
Using Ansible Vault
Using Ansible Vault is a straightforward process. First, you need to create an encrypted file using the "ansible-vault create" command. This will create a new encrypted file and prompt you for a password.
ansible-vault create secrets.yml
Once you have created the encrypted file, you can edit it using the "ansible-vault edit" command.
ansible-vault edit secrets.yml
This will open the encrypted file in your default editor. You can add your sensitive data to the file and save it. When you save the file, Ansible Vault will automatically encrypt the data.
You can also use the "ansible-vault encrypt" command to encrypt an existing file.
ansible-vault encrypt secrets.yml
This will encrypt the file and prompt you for a password. You can then use the encrypted file in your Ansible playbooks by specifying the "vault_password_file" option.
ansible-playbook site.yml --vault-password-file=vault_pass.txt
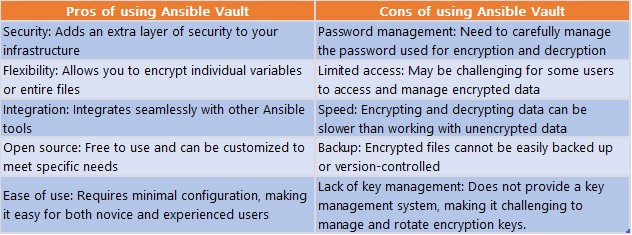
Pros and Cons of using Ansible Vault
Let us now look at some advantages/disadvantages of using Ansible Vault
Some extended options with Ansible vault
- Rekey: The "rekey" command in Ansible Vault allows you to re-encrypt an encrypted file with a new password. This can be useful if you need to change the password used for an encrypted file. To use the "rekey" command, you can run the following code:
ansible-vault rekey secrets.yml
This will prompt you for the old password and then the new password for the encrypted file "secrets.yml". Once you enter the new password, Ansible Vault will re-encrypt the file with the new password.
- Edit: The "edit" command in Ansible Vault allows you to edit an encrypted file directly without decrypting it first. This can be useful if you need to make a quick change to an encrypted file. To use the "edit" command, you can run the following code:
ansible-vault edit secrets.yml
This will open the encrypted file "secrets.yml" in your default editor. You can then make changes to the file and save it. Ansible Vault will automatically encrypt the file again with the same password.
- View: The "view" command in Ansible Vault allows you to view the contents of an encrypted file without decrypting it. This can be useful if you need to quickly check the contents of an encrypted file. To use the "view" command, you can run the following code:
ansible-vault view secrets.yml
This will display the contents of the encrypted file "secrets.yml" in your terminal. Since the file is encrypted, the contents will be unreadable.
- Decrypt: The "decrypt" command in Ansible Vault allows you to decrypt an encrypted file. This can be useful if you need to extract unencrypted data from an encrypted file. To use the "decrypt" command, you can run the following code:
ansible-vault decrypt secrets.yml
This will prompt you for the password for the encrypted file "secrets.yml". Once you enter the password, Ansible Vault will decrypt the file and display the contents in your terminal.
- Vault IDs: Ansible Vault allows you to use multiple vault IDs to manage different sets of encrypted data. This can be useful if you need to manage encrypted data for different environments or projects. To use vault IDs, you can specify a vault ID when encrypting or decrypting a file. For example, to encrypt a file using a vault ID, you can run the following code:
ansible-vault encrypt secrets.yml --vault-id my-vault-id
This will encrypt the file "secrets.yml" using the vault ID "my-vault-id". You can then use the same vault ID when decrypting the file.
- Prompt for the password: Ansible Vault provides an option to prompt for the password at runtime using the "--ask-vault-password" flag. This can be useful if you want to avoid storing the password in a file. To use the "--ask-vault-password" flag, you can run the following code:
ansible-playbook site.yml --ask-vault-password
This will prompt you for the password for any encrypted files used in the Ansible playbook "site.yml".
Conclusion
Ansible Vault is a simple and cost-effective way to encrypt sensitive data and manage it. However, do also keep in mind other solutions specific to the cloud or automation tool.
Subscribe to my newsletter
Read articles from Piyush T Shah directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
