Shifting Left: Improving Software Security by Integrating it Early in the Development Process
 Shivashish Yadav
Shivashish Yadav
Enterprise security teams have been extremely concerned about ransomware over the past few years, but now software vulnerabilities are becoming an increasingly significant threat. With the surge in cloud-based applications and services and the increasing digitization of work, hackers are capitalizing on the efforts of developers and DevOps teams to work more efficiently and quickly to keep up with demand. According to cybersecurity researchers like the Zero-Day Tracking Project, 620 zero-day exploits were recorded within 2 months of 2023 passed.
Various factors contribute to this increase in vulnerability. Developers are under pressure and reusing code, which can result in misconfigurations and vulnerabilities appearing unexpectedly in different programs. Additionally, numerous cloud services divide security measures and reduce visibility into the code that runs many enterprise functions. As a result, developers and security professionals emphasize security throughout the software development life cycle (SDLC), especially in the preliminary stages.
Defining "Shift Left" in Software Development
Before delving into the specifics of shifting security left, it's essential to understand the concept of shifting left in general. Although shifting left has gained popularity recently, the idea is not new. It involves moving tasks typically performed later in the software development workflow to earlier stages. To illustrate, consider the traditional waterfall software development model, which involves project initiation, requirement analysis, design, development, testing, and deployment. In this model, teams typically design, build, test, and deploy the software.
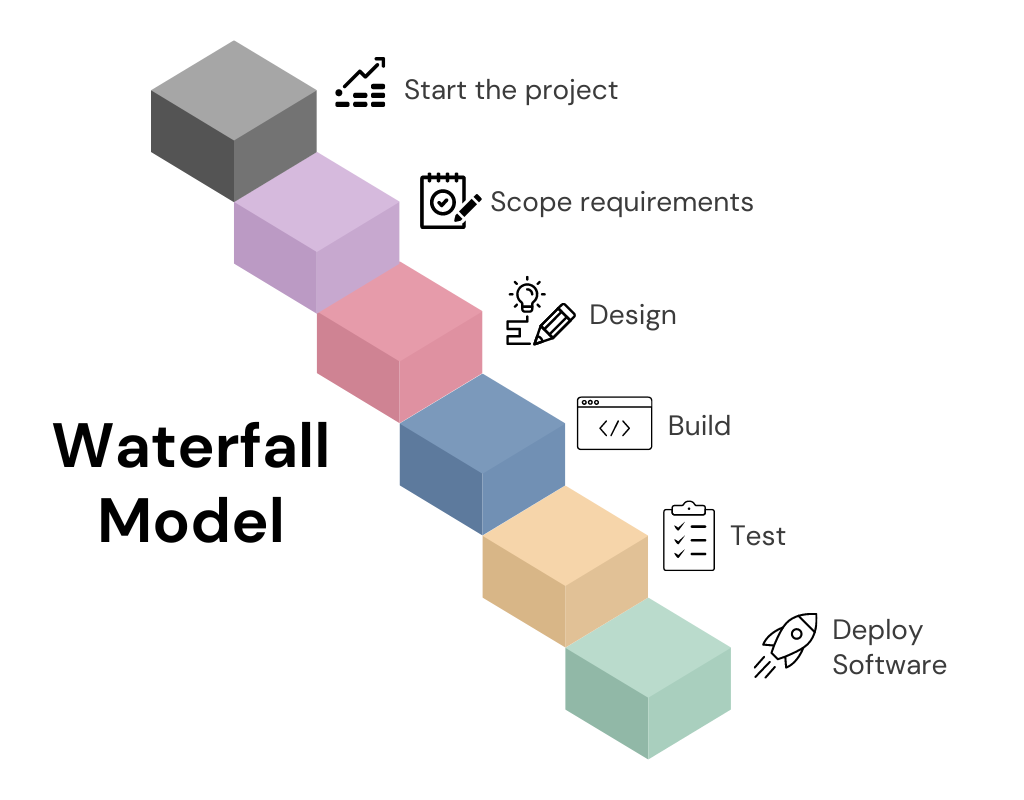
Under the traditional waterfall software development model, bugs often remained undetected until the testing phase, requiring significant resources. As a result, this approach led to higher costs associated with resolving flaws.
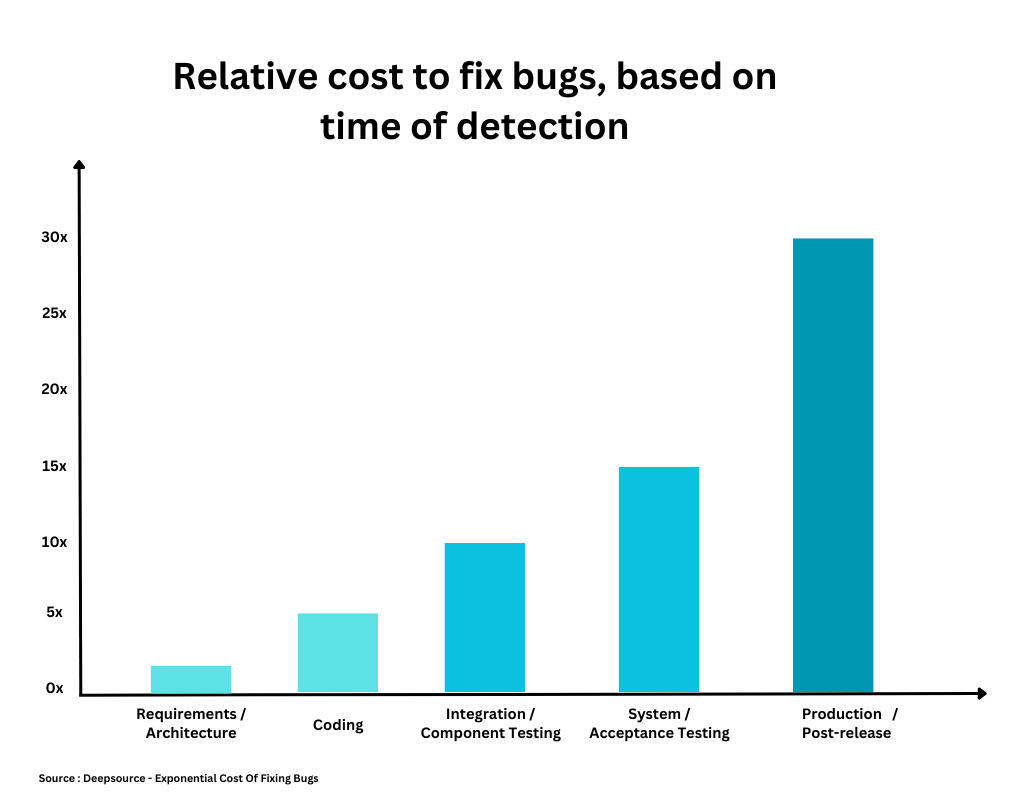
Over time, the development process has transformed with the emergence of agile methodologies, DevOps practices, and the advent of continuous integration and continuous delivery (CI/CD) tools. As a result of these changes, bug fixing has shifted to earlier stages in the release cycle.
Organizations have reaped significant benefits by incorporating testing at every process stage, from building to integrating code. Developers are notified of problematic code as soon as it appears, enabling them to fix issues quickly. Teams can deploy code to production more rapidly, as they no longer must wait for manual reviews, and testing policies are consistently applied. As a result, developers can concentrate on writing code while automated testing handles everything else.
What shift-left means?
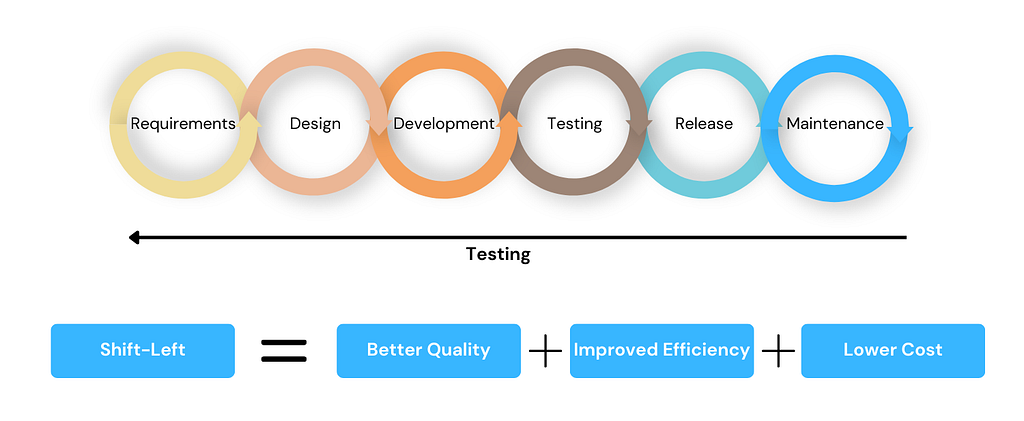
Security testing is distinct from other types of testing as it frequently only takes place once the code has already gone live in production. Organizations are shifting their approach to security to address this issue by adopting the same principles used to modernize quality testing and applying them to security testing.
By embracing a "shift left" approach to security testing, teams can identify and resolve security issues earlier in development. This involves integrating automated security testing into every step of the development cycle, from code check-ins to the final deployment.
Shifting security left allows for frequent, automated, consistent testing, significantly benefiting developers and security teams. Developers can identify and fix security vulnerabilities as soon as they appear, and security teams can ensure that security policies are consistently enforced throughout the development cycle.
Problems faced by organizations without shifting security to the left?
Security issues arise in production systems: Without proper security measures, the system is at substantial risk of exploitation. Developers may write hasty and vulnerable code patches or manually apply changes to production machines.
Less productivity: When a vulnerability is exploited, engineering teams are thrown into disarray, causing damage control and incident response, leading to heavy-handed reactions from the security team and restriction of developer access to cloud resources. This results in decreased productivity.
Cost of Data Breaches: Without proper security mechanisms, the risk of data breaches is high, and the organization may need help to detect the breach. This can lead to a high data breach cost of $3.61 million in hybrid cloud environments.
Regulatory Non-Compliance: A weak security posture towards open-source libraries can lead to violating licensing terms. Mishandling of personally identifiable information or protected health information can result in heavy financial penalties or legal consequences.
Cost of System Downtime: Vulnerable applications, when attacked, can result in system downtime, which hurts the business. Any downtime leads to revenue loss as customers cannot use or access the applications.
Risk to Business Reputation and Loss of Customer Trust: If the applications are not secure, it is only a matter of time before security threats are realized, leading to loss of customer trust, brand damage, and loss of customers.
The Significance of Shift Left Security
One of the advantages of implementing shift-left security and DevOps is that it enables early intervention in the software development process, leading to both faster development speed and improved security capabilities throughout the organization. The ultimate objective of this approach is to prevent critical bugs and security defects from occurring during the deployment phase while still maintaining the quality of the software being produced.
Early Detection of Security Vulnerabilities: By integrating security practices earlier in the software development process, shift left security allows businesses to detect and address security vulnerabilities much earlier before they become bigger problems that are more difficult and expensive to fix. This can lead to more secure software and reduced costs for addressing security vulnerabilities.
Improved Collaboration: Shift left security encourages collaboration between security and development teams, which can lead to improved communication, more effective risk management, and faster identification and resolution of security issues.
Reduced Time to Market: By incorporating security practices earlier in the software development process, shift-left security can reduce delays and accelerate time-to-market for new products and features while ensuring security risks are identified and addressed early on.
Cost Savings: Implementing security practices early in the software development process can help businesses reduce costs associated with fixing security vulnerabilities and addressing security breaches that occur after release. By catching vulnerabilities early, shift left security can save businesses money in the long run.
Increased Customer Trust: As cyber-attacks become more prevalent, customers are becoming increasingly concerned about the security of their products and services. Implementing shift-left security practices can help businesses demonstrate their commitment to security and build customer trust.
Strong Compliance: Shift left security can help businesses comply with regulatory requirements, such as GDPR and HIPAA, by incorporating security into software development processes.
Adopting shift-left security can help businesses improve the security of their products, reduce costs, accelerate time-to-market, build customer trust, and ensure compliance with regulatory requirements.
How to start with shifting security left?
The following are the three primary areas of focus when implementing a shift-left approach to security.
Are security policies implemented across your software engineering teams?
Is early testing of security vulnerabilities implemented?
Have you engaged in automating your security control processes?
Additionally, to get started with shifting left, consider the following questions:
Is a security and vulnerability gate in place for each PR (Pull Request)?
Can measures be implemented before the PR to aid in control?
What is being done to prevent vulnerable code from being added to the main branch?
Are there additional measures that can be implemented?
How and when are engineering and security teams collaborating to evaluate tools and process improvements?
Are software engineering teams authorized to make security fixes during the coding process?
Best practice for implementing shift-left security
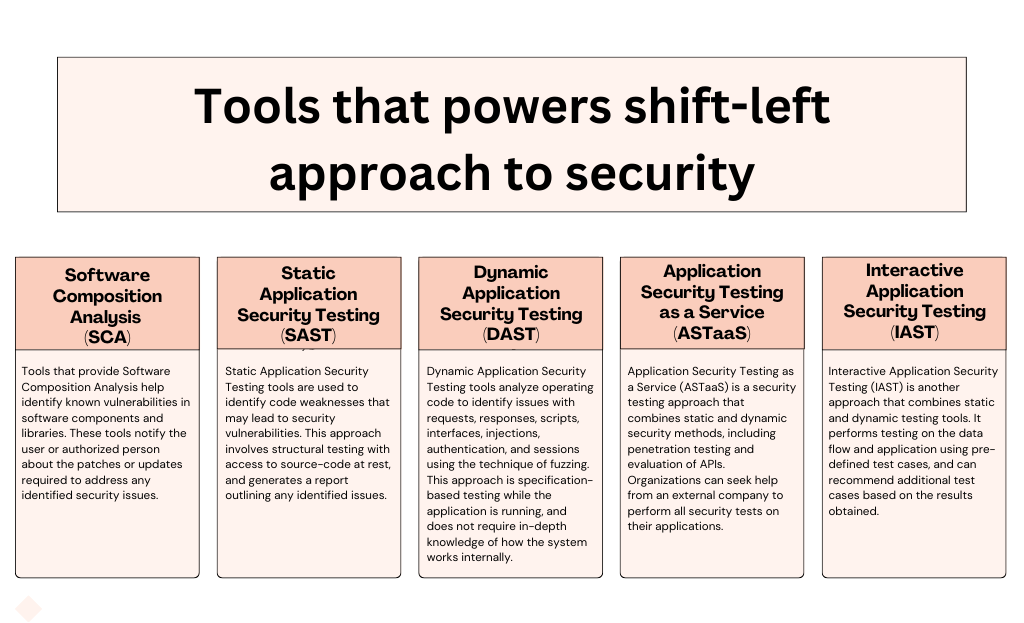
Establishing Security Policies - The first step in implementing shift-left security is establishing security policies and protocols. These should include all critical information for efficient development processes, including security measures.
Integrating Security into Development - Shift-left security involves integrating security fixes into the code as it is being developed. This requires collaboration between developers and testers to ensure that security issues are addressed as soon as possible.
Creating a Security-Conscious Culture - To achieve a satisfactory level of security, teams need to embed visibility into the culture. This means that all team members must be aware of and actively engaged in ensuring the application's security. This will enable them to remedy issues quickly when required through software updates.
Leveraging Security Automation - Embracing security automation is crucial for successful shift-left security. Automating security processes, such as code analysis, can enhance security efforts by identifying security bugs after every commit and notifying developers to address them immediately.
Subscribe to my newsletter
Read articles from Shivashish Yadav directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Shivashish Yadav
Shivashish Yadav
Information Developer | Cyber Security | Web3 & Blockchain | Web Dev | Penning the Cosmos of Information 🌌🖋️