Unlocking the magic of SSH
 Vishweshwaran M J
Vishweshwaran M J
In this article, I will try my best to easily make you understand how SSH works and how to make an SSH connection. Without much hesitation take a deep breath and let's go!!
Boooooommmm!!
Quick Intro on SSH
SSH stands for Secure Shell or Secure Socket Shell. It is a protocol in which the traffic is encrypted over the network thus called a Cryptographic Network Protocol.
This is used to establish a secure network connection between two computers over the internet.
SSH is mainly used for the following:
Secure Remote Login:
- Users can securely login to remote computers and access its command line interface and execute remote commands.
Secure File Transfers:
- Users can securely transfer files between computers using SCP (Secure Copy) or SFTP (Secure File Transfer) protocols.
Tunneling:
- SSH Tunneling creates an encrypted connection between computers thus making the transit of data secure and safer.
The Two Keys - Public & Private
We need to understand the two keys that are involved in the connection process. So what are the two keys, let's go further reading
When we wanted to access another computer we generally use passwords which are not secure and can be hacked by anyone. So the much better, secure alternative to using passwords is the SSH Keys.
With these Keys, we can make a secure connection and this is also called passwordless authentication.
So in SSH, we have a key pair named Public key and Private key.
Public Key
Can be distributed to anyone
Stored on the server that you want to connect to
Used for encrypting messages
Key ends with
.pubextension
Private Key
Should be kept safe and should not be shared with anyone
This is used to decrypt messages that are encrypted with the help of Public Key
Steps to Generate the Key Pair
Firstly, let's understand how these two keys are generated on the client machine (am working on an Ubuntu machine, so it should be similar for other machines as well)
Launch your terminal
Type the below command to create the Public & Private key pair
ssh-keygen
- The below key pair was generated with a couple of prompts and uses RSA encryption by default
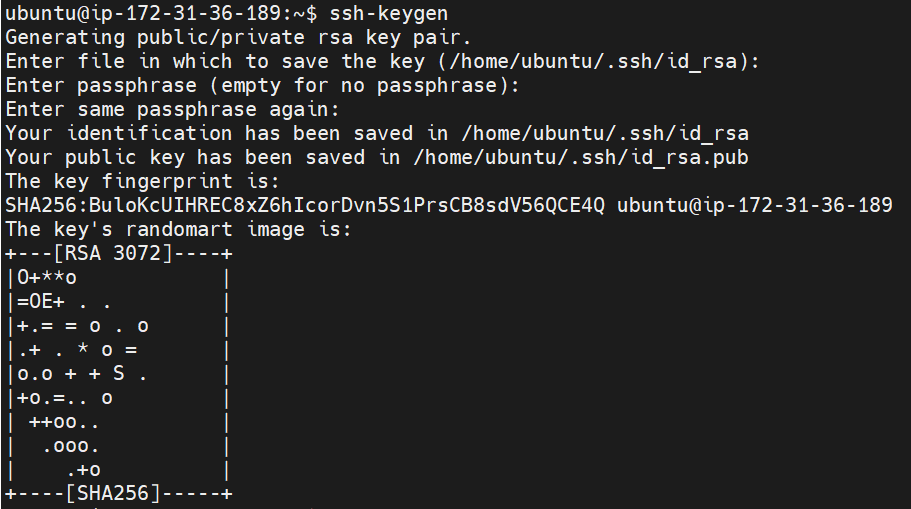
- I have left the prompts to have default values by hitting ENTER and those prompts are
Enter file in which to save the key (/home/ubuntu/.ssh/id_rsa):
- This is the default folder location
(/home/ubuntu/.ssh/)where the keys are stored. You can also change its location if required.
Enter passphrase (empty for no passphrase):
- If you want to make the key more secure you can input a password. I have left blank in my case.
Enter the same passphrase again:
- You need to input the same password that was entered above to confirm the match.
That's it, your key pair is generated and stored in the defined location.
Here are the keys now available in
(/home/ubuntu/.ssh/)locationid_rsa- Private Keyid_rsa.pub- Public Key (.pubstands for public)
ubuntu@ip-172-31-36-189:~$ cd .ssh/
ubuntu@ip-172-31-36-189:~/.ssh$ ls -l
total 12
-rw------- 1 ubuntu ubuntu 393 Apr 22 15:45 authorized_keys
-rw------- 1 ubuntu ubuntu 2610 Apr 22 16:19 id_rsa
-rw-r--r-- 1 ubuntu ubuntu 577 Apr 22 16:19 id_rsa.pub
We are now halfway through and pending with one thing which is copying the Public key to the target server.
Copy Public Key to Target Server
In order to make a connection to the target Server (the server which we wanted to login) we have to copy the Public key to the target server's .ssh folder.
This can be achieved via two ways
manually copying the Public key to the target server
using the
ssh-copy-idcommand
Thus by copying the Public key to the target server we can make passwordless authentication and take control of the remote host.
Using Manual Copy
To manually copy the Public key we have to perform the below actions on the target server
Navigate to the
.sshfolder of the target serverIf the
authorized_keysfile is not available, create it and add the Public key contents into the file and save itTo get the Public key contents, execute the
catcommand on the client server (the machine from which you wanted to connect to the target server)cat id_rsa.pub
If the
authorized_keysfile is already having a Public key, "DO NOT" modify the existing key and append our Public key contents to the end of the file and save it
Note: "Excercise Caution" when working manually with keys.
Using "ssh-copy-id" Command
This is another way of copying the Public key to the target server. Using this method the .ssh folder and authorized_keys file are automatically created and Public key is appended.
But this method requires a password authentication of the target server initially so that the Public key is appended to the authorized_keys file
ssh-copy-id <target-host-ip-address>
So now we have the Key pair created and placed the Public key on to the target server we are now all set to automatically establish a connection using the SSH keys.
The Core Concept - Connection Establishment
Let's now deep dive into the actual working/connection being established between two machines while using SSH Keys
I know it's more now, relax and do not panic we have almost there to closure, it is easy to understand, continue reading!!
Let's try to connect to the target server from the client (our Ubuntu machine)
When a client attempts to login to the target server, the server asks to prove its identity by sending back a random encrypted message to the client
This message encryption is done with the help of the Public key that we copied to the target server
Yes, you got it right, this is the reason we placed the Public key on to the target server. Let's move on further
The client then decrypts the message using its Private key and sends it back to the target server
The target server verifies and confirms yes this is the random message I sent to you. I trust and confirm you have the associated Private key with you and thus the connection is established.
Yes again, you got it right, the connection was established as the key pair was associated with each other during ssh-keygen creation
If the decrypted random message was wrong the target server would have denied the connection request
That's it. Easy isn't it??
Finally, the SSH Command
ssh -i <path-to-the-private-key> <userName>@<target-ip-address>
ssh- instructs the client to make a secure shell connection to the target server-i- identity file (i.e) your Private keyuserName- user which you wanted to login to the target servertarget-ip-address- the target server you wanted to get connected to
Understanding with AWS EC2 Instance Launch
When launching the new AWS EC2 instance you would have seen a section for "Key pair (login)" where we are asked to type the name of the Key pair for creating a new key pair. So when we do this behind the scenes these two keys Public and Private are created.
The Public key goes to the authorized_keys file of the AWS EC2 instance that you are trying to create and the Private key is downloaded into your local machine.
Once the instance is launched you use this Private key to connect to the instance using ssh command and the connection is established as said above.
Please let me know in the comment section about any corrections/mistakes, am open to improvements and suggestions.
Please do follow me for more such content related to DevOps world
Cheers, Vish. Happy Learning!!!
Subscribe to my newsletter
Read articles from Vishweshwaran M J directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Vishweshwaran M J
Vishweshwaran M J
Hello reader, this is Vish currently working as a DevOps Engineer for the past 3+ years and a total of 9+ years of experience in the IT industry. Am passionate about learning DevOps and in the mission of enhancing my learning into container orchestration tools, monitoring and security.