IPsec VPN: NAT Traversal (NAT-T)
 Jitin Tyagi
Jitin Tyagi
Overview of NAT-T feature
NAT-T (Network Address Translation Traversal) is a feature of IPSec VPN that allows two endpoints to communicate with each other even if they are behind a NAT device.
It works by encapsulating the IPSec packets in UDP packets and using ISAKMP to negotiate the security parameters.
The two modes of IPSec VPN, Main mode and Quick mode, use NAT-T to establish secure communication between two endpoints.
In addition, ESP (Encapsulating Security Payload) and PAT (Port Address Translation) are used for data encryption and port forwarding respectively.
What is NAT-T?
NAT-T performs 2 tasks :
NAT-T Negotiation - whether or not the peer support the NAT-T feature.
NAT Discovery (NAT-D) - detects NAT device(s) along the transmission path between the peers.
How does NAT-T work with IPSec?
Main mode messages 1 & 2 | NAT-T Negotiation
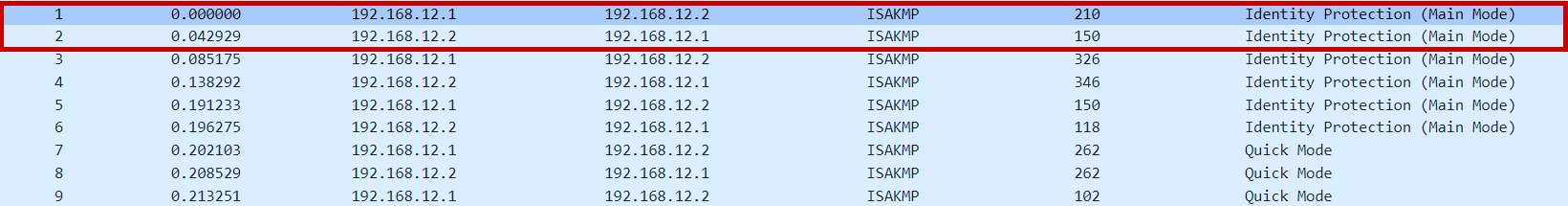
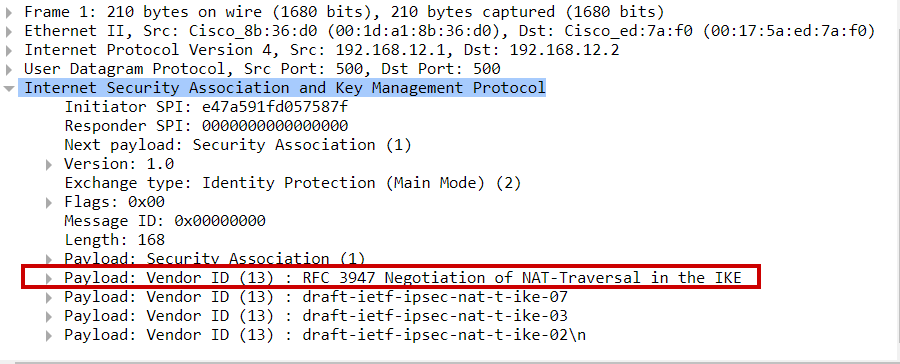
In the main mode messages 1 & 2, negotiation of NAT-T is done i.e. peers notify each other that they support the NAT-T feature by sending a hash of RFC 3947 as one of the payloads in the messages.
Main mode messages 3 & 4 | NAT Discovery (NAT-D)
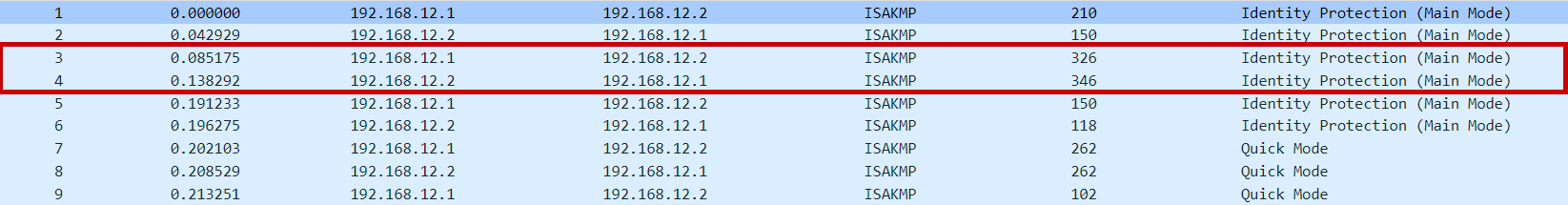
In the main mode messages 3 & 4, NAT-DIscovery (NAT-D) is performed. NAT-D payload is sent by each VPN peer which is a hash of original IPs and port numbers.
Devices exchange 2 NAT-D payloads, one with source IP and port number and another with destination IP and port number
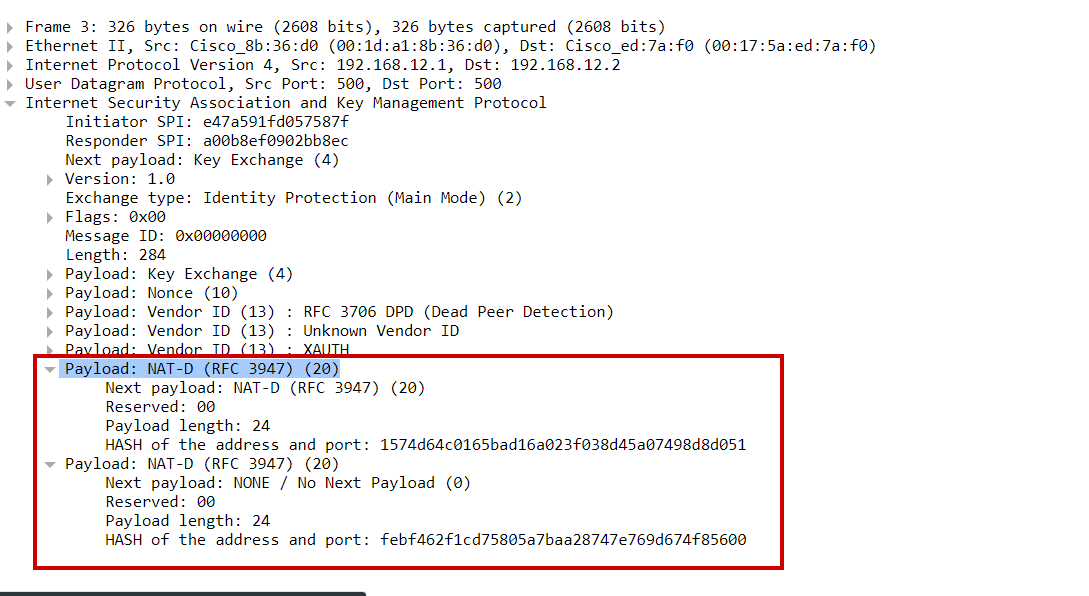
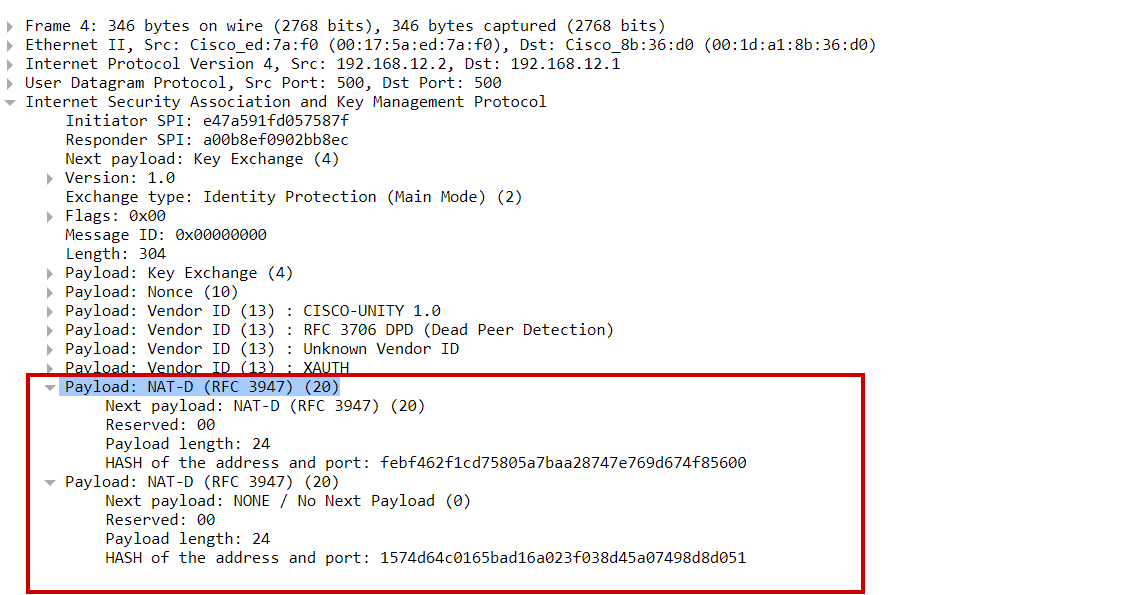
The receiving device recalculates the hash and compares it with the received hash and if they are not the same, then it means NAT/PAT-enabled device(Firewall/router) exists along the transmission path between the peers. (But in our packet capture hash are same and hence no NAT/PAT-enabled device exists between VPN peers)
Main mode message 5 & 6 | The start of encapsulation of packets

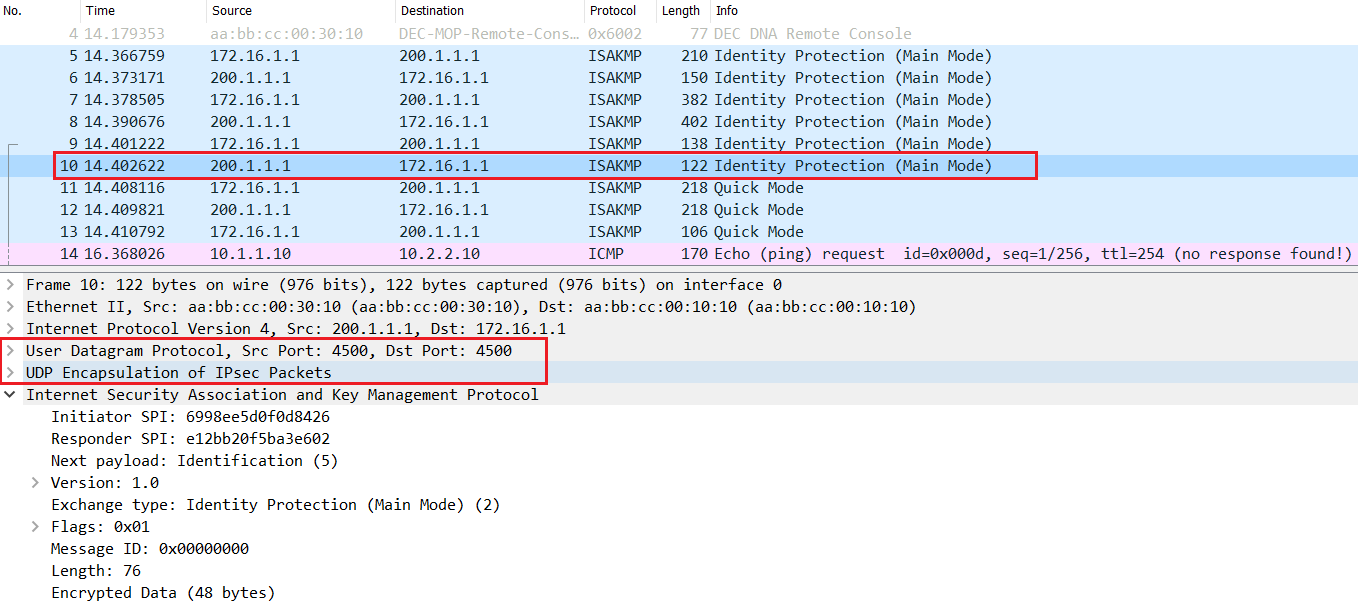
As NAT/PAT device has been detected, NAT-T will start its magic i.e. by changing the ISAKMP transport with UDP port 4500 instead of UDP port 500 starting from main mode messages 5 & 6.
NAT-T & IKE Phase 2 (Quick mode)
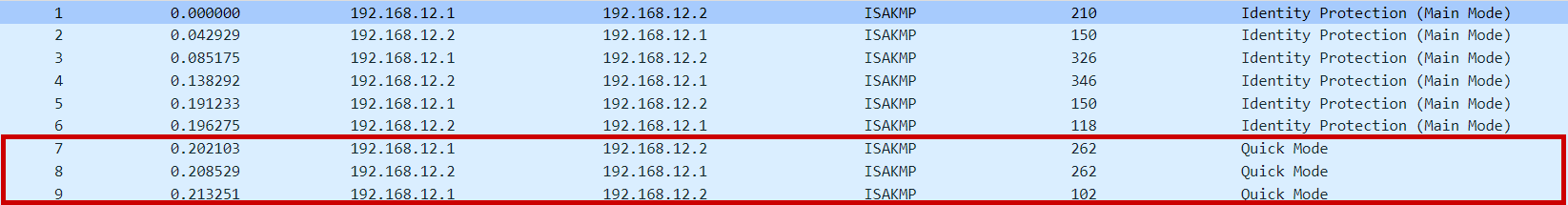
After the successful completion of the main mode messages, NAT-T encapsulates the Quick mode messages (IKE phase 1) with UDP port 4500 as well.
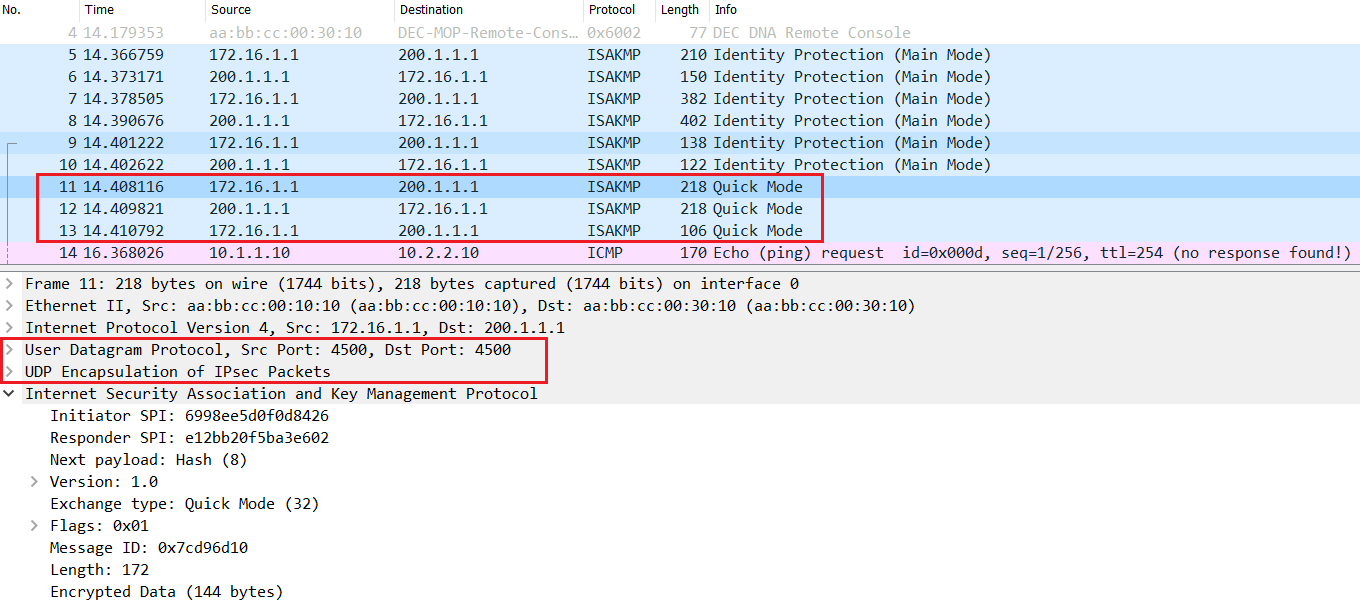
NAT-T & ESP protocol | Data traffic
After the successful completion of IKE phase 2, data is ready to get encrypted as per the user's specified security associations (SA) & transmitted across the transmission path using the ESP (Encapsulating Security Payload) protocol.
NAT-T encapsulates data traffic sent over with UDP port 4500 as well instead of just ESP protocol as ESP packet can't pass via a PAT-enabled device.
Why can't the ESP packet pass via a PAT-enabled device?
ESP is a protocol of the IPSec suite without ports that prevents it from passing via a PAT-enabled device. As there is no port number to translate in the ESP packet, the translation to a unique port can't happen and hence the packet can't be forwarded.
NOTE: NAT-T always uses the standard port, UDP port 4500 and it is not configurable.
References:
Subscribe to my newsletter
Read articles from Jitin Tyagi directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
Jitin Tyagi
Jitin Tyagi
CCNP SCOR | CCNP ENCOR | CCNA 200-301 | FORTINET NSE-1,2