OSWE - Advanced Web Attacks and Exploitation - Review (2023)
 Nee
Nee
Introduction
It's been a while since I wrote one of these and I'm thrilled to share with you my journey to becoming an Ofsec Web Expert (OSWE). As someone who's always been interested in web application security, earning the OSWE certification has been a major accomplishment for me both personally and professionally.
In this blog post, I'll give you a glimpse into my background in web application security, and share my experience studying for the certification exam. I hope that by sharing my own story, I can inspire and guide others who are on a similar path.
So, whether you're a fellow security enthusiast, a student just starting out, or my future employer, I invite you to join me as I reflect on my journey and share some tips and insights along the way. Let's dive in!
Background
Professional
I am a cybersecurity enthusiast with limited experience in web application security. My passion lies more in finding vulnerabilities and exploiting them rather than in coding. I have a solid foundation in cybersecurity and penetration testing, but not the same for web exploitation. I have worked on various security projects in the past, including vulnerability assessments, penetration testing, and incident response.
Education & Certifications
I have a background in Information Technology and hold a couple of red certs like the OSCP and CRTO, networking certs and server-sided certs like the RHCSA. Although coding is not my strong suit, I do have some experience in PHP web application development which has given me a basic understanding of web application architecture. I also consider myself a scripter and not a coder 😂. Hope that changes soon tho...
Motivation to Pursue OSWE
Despite my background in offensive cybersecurity, I had a strong interest in web application security and wanted to learn more about it. I decided to pursue the Advanced Web Attacks and Exploitation (AWAE) course to deepen my knowledge and skills in this area and more specifically a white box approach. Although I knew that digesting the various coding languages would be a challenge for me, I was motivated to push myself and expand my skill set to become a more well-rounded cybersecurity professional.
Preparation
Out-of-Lab Preparation
Before stepping into the offsec labs, I preped for the course by completing a couple of the BurpSuite labs and building Python scripts to automate the exploitation of the challenges. I found that this helped me build up my scripting ability, specifically in using the requests & sockets library to interact with web applications. By automating the exploitation process, I was able to gain a deeper understanding of how different web application vulnerabilities could be exploited and how to craft custom payloads and incorporate them into the exploitation chain. I also practiced using various BurpSuite extensions to assist with manual testing and vulnerability identification.
Offsec Labs
Guided Labs
The Offensive Security labs for the OSWE were definitely challenging and rigorous given my background. But they provided an excellent learning experience. The labs covered a wide range of web application vulnerabilities, including injection attacks, broken authentication and session management, cross-site scripting (XSS), and more.
The lab materials were well-written and provided clear guidance on how to identify and exploit the vulnerabilities. However, the labs also required a lot of independent research and experimentation to fully understand and exploit the vulnerabilities, which I found to be both frustrating and rewarding.
I also appreciated the ability to use the lab environment to test out new techniques and hone my skills. The lab environment was realistic and walked the students through real-world (outdated) applications and their exploitation techniques. Additionally, the lab environment was well-designed and easy to use, which allowed me to focus on learning and exploiting vulnerabilities instead of struggling with technical issues (I'll get to this in the next few sections lol). Overall, the lab experience was challenging and time-consuming, but it was also one of the most valuable parts of my preparation for the OSWE exam.
Extra-Mile Exercises
The OSWE labs also feature a set of "extra mile" challenges, which are designed to push candidates even further beyond the guided exercises. These challenges require a deeper understanding of the underlying web technologies and an ability to think outside the box to identify and exploit vulnerabilities. The extra mile challenges are not guided and there is no walk-through available, which means that the candidate must use all the knowledge and skills they have acquired to complete these challenges. These extra-mile challenges were particularly satisfying to complete, as they required me to apply what I had learned in a more creative and unguided manner.
Unguided Labs
One of the unique features of the OSWE course is the unguided labs, which test the techniques taught in the course without any walkthrough or guidance. (Similar to how we'd use Proving Grounds or HTB for the PWK) These labs are designed to simulate real-world scenarios where the attacker has to identify and exploit vulnerabilities on their own. I found these labs to be particularly challenging(ish), as they required a lot of independent research and experimentation to complete successfully. However, they were also very rewarding, as they helped me develop my problem-solving and critical-thinking skills.
The unguided labs forced me to think creatively and come up with unique solutions to exploit the vulnerabilities, which helped me gain a deeper understanding of web application security.
Community
Community support was a critical component of my preparation for the OSWE exam. I found the OSWE Discord channel and the internal forums to be excellent resources for asking questions, getting feedback on my approaches, and learning from other student's experiences. If you run into an "unsolvable" issue, there's probably someone who has been there and gotten over the hurdle.
The student admins were also fairly active on the discord channel and provided valuable insights and guidance throughout the course to students who were facing issues.
Additionally, I found the various online blogs written by individuals (like this one) to be helpful resources for some initial guidance.
Note-taking
(Notion is the only right answer)
Note-taking was a critical component of my preparation for the exam. During the course, I made sure to take detailed notes on every technique and attack vector covered in the lectures and labs. I found that by taking notes, I was better able to internalize the material and retain the information. Additionally, note-taking allowed me to keep track of the various tools and commands used in each attack vector, which made it easier to reference them later.
During the exam, having detailed notes allowed me to quickly look up anything I needed, saving me precious time and allowing me to focus on the task at hand.
The Exam
Background
The OSWE exam is a 48-hour practical exam focused on web application security. It is conducted remotely, and candidates are given access to a virtual network containing multiple vulnerable web applications. The goal of the exam is to identify and exploit vulnerabilities in these applications to gain access to sensitive information or perform unauthorized actions.
The exam is hands-on, meaning that candidates must demonstrate their ability to identify, exploit, and document vulnerabilities in a practical setting. The exam is graded based on the number and severity of vulnerabilities found, as well as the quality of the documentation provided. To pass the exam, a candidate must score at least 85 points out of 100.
Remote Proctoring
Candidates are closely monitored by a proctor to ensure the integrity of the exam. The proctoring process is conducted via webcam and screen-sharing software, which allows the proctor to observe the candidate's actions and ensure that they are not using any unauthorized resources or receiving outside assistance. Although the idea of being closely monitored can be intimidating, I found the proctoring process to be quite professional and unobtrusive. Candidates are allowed to plug headphones in as long as its only connected to the host device that's involved in the exam. (Didn't know this previously lol)
As always you're allowed to take short breaks & logoff for naps. However, you're given 2 options if you decide to log off. You could leave your computer on and untouched or disconnect from the VPN. But this will cause you to lose connection to the infra and the VPN connection would be paused. Thus, I decided to leave my computer on and run some of my scripts for testing.
I'm sorry to the proctor that had to sit through me bopping my head and "rapping".
The Actual Exam
During the exam, I was able to fully exploit both the given machines and complete all the required objectives. It was a very humbling experience to see how far I had come from my initial dabbling in web exploitation. I was especially grateful for the unguided lab machines and the extra-mile exercises.
Debugging
debugging is an important aspect of the OSWE exam. During the exam, you will encounter various challenges that require you to write your own exploits. It's essential to have a solid understanding of how the exploit works and what it does. If something isn't working correctly, debugging is the process of finding out what's wrong and fixing it.
This can involve looking at the source code of the exploit, understanding how the target application works, and using various debugging tools to pinpoint the issue. In some cases, you may need to use trial and error to identify the problem. The ability to debug effectively can make all the difference in the success or failure of an exploit. It's crucial to practice this skill during your preparation so that you are comfortable with it on exam day(utilize the lab!!).
Methodology
During the exam, I followed a methodology that prioritized understanding the web application and its functionalities over just looking for individual vulnerabilities. This approach helped me to chain together multiple attack vectors and achieve full exploitation of the given machines. I first performed a thorough reconnaissance to identify all possible entry points and attack surfaces. Then, I used manual testing techniques to identify potential vulnerabilities and attack vectors.
Once I identified potential attack vectors, I focused on understanding the application logic and how I could chain together different vulnerabilities to achieve my objectives. I found that by taking this approach, I was able to maximize my exploitation potential and fully demonstrate my understanding of the web application. Starting my analysis from unauthenticated portions of the web application always seems to reward me the most (as expected).
This methodology was extremely effective during the exam (at least for me!).
Deliverables
The OSWE exam requires the candidate to submit two deliverables (in one document) within 24 hours of completing the exam. The first deliverable is a detailed report of the exploitation process, including steps taken, tools used, and vulnerabilities exploited (with vulnerable code snippets and explanations). The report must also include a description of the custom scripts or tools developed during the process. The second deliverable is the 0-click exploit script which is able to automate the exploitation of all discovered vulnerabilities.
The report and script are both reviewed by the OffSec team, and the candidate must demonstrate a clear understanding of the exploitation process and the vulnerabilities exploited. The deliverables are an important part of the OSWE exam, as they allow the candidate to showcase their skills and provide evidence of their abilities.
Templated snippets
While you go through the course, you'll have created and improved your custom exploit scripts. Please template these and safe keep them. It's gonna be extremely helpful in the exam when you need to not only find and exploit the vulnerabilities but create a script to automate them. Read up and practice using requests, WebSockets (made me contemplate life decisions in the lab) and other web-related libraries.
Support
The exam support team was always available to answer any questions or concerns I had. Whenever I encountered any technical issues or needed clarification on the exam instructions, they were quick to respond and provide assistance. Their prompt and professional responses helped me to focus on the exam itself without any added stress or anxiety. ASK IF UNSURE!!
Issues I faced
(more like issues that faced me but ok)
As always, not everything was rainbows and sunshine. While going through the AWAE course, I faced a few challenges that tested my perseverance. From grappling with complex web application vulnerabilities to struggling with the NEW Offsec Learning Portal, I encountered various hurdles along the way.

The New Portal (LMS)
Offsec recently released a new portal to replace its old portal which could only be accessed via their VPN. The platform itself is pretty flash, clean and pleasing to the eye. The issues I faced during my lab time were all reliability related.
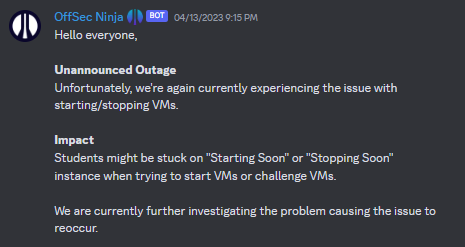
The portal was extremely unstable. It kept going down without prior notice which affected a ton of fellow students. There were multiple instances where I would set aside precious time away from work and uni just to get hit with the "Unannounced Outage".
Offsec did give out lab extensions to students on a case-by-case basis. However, the extension was pretty invaluable to me as I was already on the learn one package. I was only left with frustration and disappointment ☹️.
But I don't entirely blame them as their support team was pretty responsive and transparent. They were facing such instability due to the new PEN200 labs and having students migrated to the new infrastructure. Hope future students wouldn't have to go through what I did!
Deliverables
I found it odd that candidates are expected to attach the exploit script in the report document that is due for submission. I was extremely paranoid and kept pasting my exploit script multiple times into the report document before converting it to the preferred .pdf format.
I'm sure they have a valid reason for this. (Don't want students possibly submitting malicious files. Do let me know if you know of other reasons). But I do believe something else can be done about this situation to prevent paranoia amongst students.
Conclusion
Undoubtedly, the OSWE certification journey was a demanding one, but the knowledge gained and the skills developed throughout the process made it all worthwhile. The course and lab materials provided by Offensive Security were extensive and well-structured, allowing me to develop a deeper understanding of web application security and hone my skills in exploiting web vulnerabilities.
The exam itself was a true test of my abilities and required me to think outside of the box to fully exploit the given machines. I am proud to have earned the OSWE certification and look forward to applying my knowledge and skills in future engagements. Thank you to everyone who's helped me through this journey😁! Hope this help's someone out there who's looking to embark on this journey. Do not hesitate to reach out to me Nee#0110!

Subscribe to my newsletter
Read articles from Nee directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Nee
Nee
All things Information Security!