Kubernetes Storage Kubernetes Security
 Ritul Gupta
Ritul Gupta
☸ Volumes
Containers are short-lived in Nature.
All data stored inside a container is deleted if the container crashes. However, the kubelet will restart with a clean state, which means that it will not have any of the old data.
To overcome this problem, Kubernetes uses volumes. A volume is essentially a directory backed by a storage medium. The storage medium and its content are determined by the volume type.
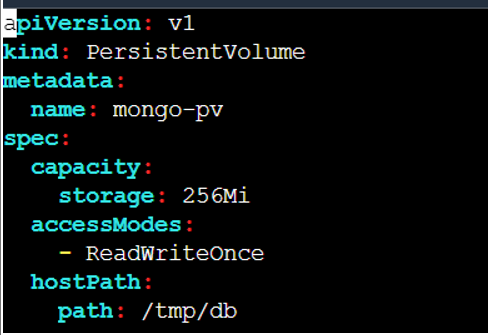
☸ Persistent Volumes
In Kubernetes, a volume is attached to a Pod and shared among the containers of that pod.
The volume has the same life span as the pod, and it outlives the containers of the pod preserved across container Restarts.
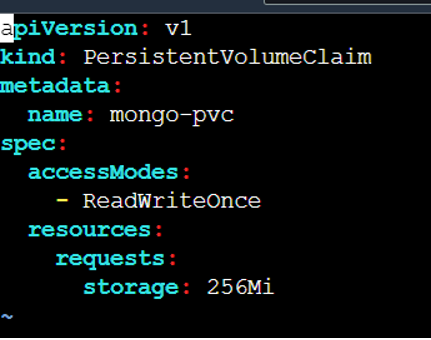
☸ Persistent Volumes Claims
Persistent Volume Claims (PVCs) act as a request for storage resources from a Persistent Volume. They allow pods to consume the storage provided by a Persistent Volume.
☸ Storage Classes
By using StorageClasses, applications can be deployed on different Kubernetes clusters and cloud platforms without requiring changes to the application code.
apiVersion: storage.k8s.io/v1
kind: StorageClass
metadata:
name: fast
provisioner: kubernetes.io/aws-ebs
parameters:
type: gp2
zone: us-west-2a
☸ Statefulsets
In Kubernetes, a StatefulSet is a controller that manages a set of stateful pods. Unlike a Deployment, which manages a set of stateless replicas, a StatefulSet manages a set of pods that have a unique identity and state.
When a StatefulSet is created, it creates a set of Pods that have a unique identity and are created in a predictable, ordered fashion. Each pod in the StatefulSet has a stable network identity in the form of a DNS hostname, which includes the name of the StatefulSet and a unique ordinal index. This allows other applications in the cluster to discover and communicate with the pods in a consistent and reliable way.
apiVersion: apps/v1
kind: StatefulSet
metadata:
name: webapp
spec:
serviceName: webapp
replicas: 3
selector:
matchLabels:
app: webapp
template:
metadata:
labels:
app: webapp
spec:
containers:
- name: web
image: nginx:latest
ports:
- containerPort: 80
volumeMounts:
- name: config
mountPath: /etc/nginx/nginx.conf
subPath: nginx.conf
volumes:
- name: config
configMap:
name: nginx-config
volumeClaimTemplates:
- metadata:
name: data
spec:
accessModes: [ "ReadWriteOnce" ]
resources:
requests:
storage: 1Gi
☸ Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is a method of controlling access to resources in the cluster. RBAC allows the cluster administrator to define roles and permissions that can be assigned to users, groups, or service accounts, based on their responsibilities and permissions.
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: my-role
rules:
- apiGroups: [""]
resources: ["pods"]
verbs: ["get", "list", "watch"]
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: my-role-binding
subjects:
- kind: User
name: alice
api Version: rbac.authorization.k8s.io/v1
roleRef: kind: Role name: my-role
apiGroup: rbac.authorization.k8s.io
subjects:
- kind: User
name: alice
apiGroup: rbac.authorization.k8s.io
☸ Pod Security Policies
PSPs are used to enforce security policies for pods in Kubernetes. They define a set of security conditions that a pod must meet in order to be created or updated. These conditions include things like the use of privileged containers, the use of host namespaces, and the use of host networking.
apiVersion: policy/v1beta1
kind: PodSecurityPolicy
metadata:
name: my-psp
spec:
privileged: false
allowPrivilegeEscalation: false
seLinux:
rule: RunAsAny
runAsUser:
rule: RunAsAny
fsGroup:
rule: RunAsAny
volumes:
- '*'
☸ Secrets
Secrets in Kubernetes provide a way to store and manage sensitive information, such as API keys, passwords, and certificates. They are encrypted and can be mounted as volumes or used as environment variables in pods.
apiVersion: v1
kind: Secret
metadata:
name: my-secret
type: Opaque
data:
username: dXNlcm5hbWU=
password: cGFzc3dvcmQ=
☸ Network Policies
In Kubernetes, Network Policies are used to define rules for traffic within the cluster. Network Policies provide a way to control the flow of network traffic to and from pods based on a set of rules that are defined in the policy.
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: allow-ingress-from-nginx
spec:
podSelector:
matchLabels:
app: my-app
policyTypes:
- Ingress
ingress:
- from:
- podSelector:
matchLabels:
app: nginx
☸ Transport Layer Security (TLS)
TLS (Transport Layer Security) provides secure communication between clients and servers. In Kubernetes, TLS can be configured for various components, such as ingress controllers, API servers, and service-to-service communication.
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: tls-ingress
annotations:
nginx.ingress.kubernetes.io/ssl-redirect: "true"
nginx.ingress.kubernetes.io/ssl-ciphers: "ECDHE-RSA-AES128-GCM-SHA256"
spec:
tls:
- secretName: tls-secret
rules:
- host: my-domain.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: my-service
port:
number: 80
Thanks for Reading!! 🙏
Subscribe to my newsletter
Read articles from Ritul Gupta directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ritul Gupta
Ritul Gupta
Packaged App Development Associate @ Accenture | Infrastructure Engineering | Exploring Cloud & Security