Supercharge Your Data Collection: Transform and Enrich Your Logs with Sumo Logic Script Action
 WhatDoesKmean?
WhatDoesKmean?
In this article, we'll explore how to create a Script Action in Sumo Logic by writing a simple bash script that pings an IP found on an event log. We'll then use the Sumo Logic UI to configure a Collector to run the script and send the results to its platform.
This process can be used for a wide range of use cases, allowing you to enrich your log collection and enhance the insights gained from your data.
A Script Action allows the output of a Scheduled Search to be passed on to a script, which can then be executed on a machine with an Installed Collector.
Any output sent to the standard output (STDOUT) will be gathered and made available for searching.

Step-by-step process
Note: If you're using a Collector with version 19.245-4 or later, Script Actions may be disabled by default.
To enable Script Actions, you'll need to set the enableActionSource parameter in the user.properties file to true and restart the Collector.
sudo vi /opt/SumoCollector/config/user.properties
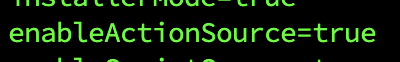
sudo systemctl restart collector
To create and configure Script Actions on the Sumo Logic Collector, please follow these steps:
Step 1 - Creating and Configuring the Script Action:
In our case, we will set up the Script Action using the platform's UI.
Go to Manage Data > Collection > Collection.
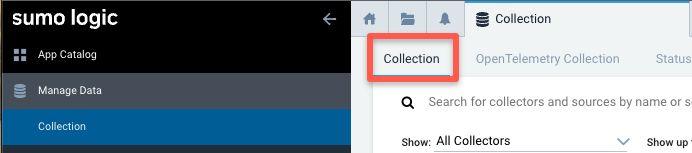
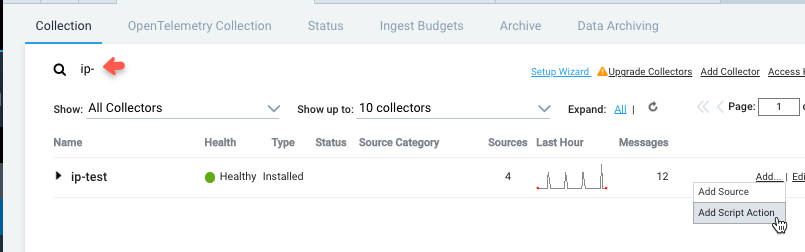
Find the name of the Installed Collector to which you want to add the script action and select Add > Add Script Action.
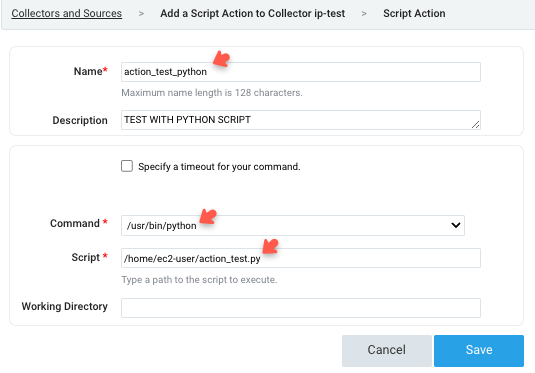
Enter a name to display the Script Action in the Name field.
Optionally provide a Description for the Script Action.
To set a timeout for the script execution, specify a value in the Timeout field. This ensures that the script is killed if it runs for too long and consumes too many resources.
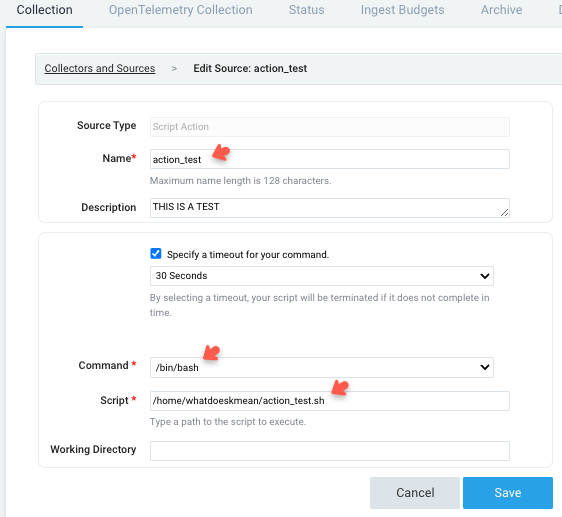
Choose the type of command you're going to use from the Command options.
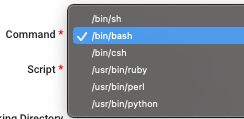
Enter the path to your script in the designated field. When the Collector executes the script, it will automatically pass the full path to a file containing the search results that triggered the Script Action as the first and only parameter.
If you need your Script Action to execute in a different directory than the Collector installation directory, specify the desired working directory.
Click the Save button to apply your changes.
Optional: This is the configuration for a Python script
Step 2 - Configuring the Scheduled Search
Once you have configured the Script Action to your Collector, you can proceed to create a Scheduled Search.
When the Scheduled Search runs, it will start generating new log events (based on the bash script results within the Installed Collector)
To create a Scheduled Search, you need to save the search first and then click on the Schedule this search button.

Choose the Alert Type and then choose the Script Action from the menu, which will be displayed along with the name of the Collector.
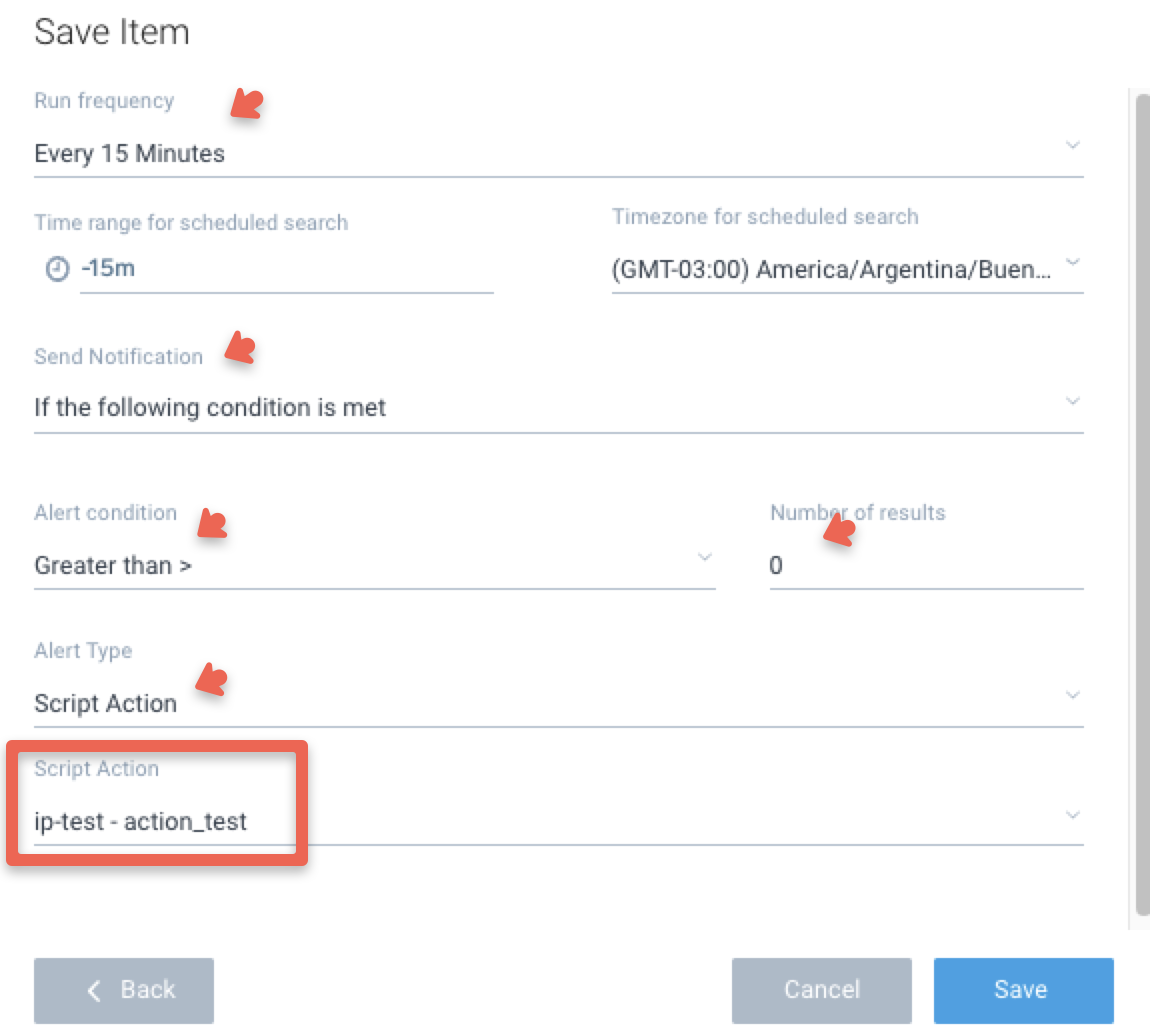
Finally, save your selection by clicking the Save button.
Step 3 - DEMO
This demonstration illustrates the process of preparing a script and configuring a Script Action.
First, create a bash script named action_test.sh.
Its contents should be as follows:
#!/bin/bash
ip=$(grep -Eo '([0-9]{1,3}.){3}[0-9]{1,3}' "$1" | head -1) res=$(ping -c 3 "$ip" | tr '\n' ' | ')
echo "$(date) - The ping result for $ip is: $res"
This Bash script takes an argument, which is the Sumo Logic log containing an IP address. The script uses the IP address to ping the host and report the result.
Script explanation:ip=$(grep -Eo '([0-9]{1,3}\.){3}[0-9]{1,3}' "$1" | head -1)
Using grep to extract the first IP address found from the log line ($1). The RegEx '([0-9]{1,3}\.){3}[0-9]{1,3}' matches IP addresses, and the -Eo option tells grep to use extended regular expressions and to only print the matched text.
The head -1 command then takes the first line of output (i.e., the first IP address) and assigns it to the ip variable.
res=$(ping -c 3 "$ip" | tr '\n' '|')
Ping to send three ICMP echo request packets to the IP address stored in the ip variable. The -c 3 option tells ping to send three packets. Then, we pipe the output of the ping command to the tr command with the option to replace newline characters (\n) with pipes. This removes the newline characters from the output, effectively putting the entire ping output on a single line and assigning it to the res variable.
echo "$(date) - The ping result for $ip is $res"
Lastly, this line prints the current date, time, IP address, and ping result. The output will look something like this:
Tue May 2 18:17:48 UTC 2023 - The ping result for 179.38.0.129 is: PING 179.38.0.129 (179.38.0.129) 56(84) bytes of data. --- 179.38.0.129 ping statistics --- 3 packets transmitted, 0 received, 100% packet loss, time 2033ms
To make the shell script executable, run the following command:
chmod +x action_test.sh
Next, navigate to Manage Data > Collection > Collection. Look for the Installed Collector name where you want to use the script action and select Add > Add Script Action.
Configure the Script Action as instructed in Step 1 and Step 2.
For your convenience here's the same sample script but in Python 2:
#!/usr/bin/env python
import re
import subprocess
import sys
from datetime import datetime
if len(sys.argv) != 2:
print "Usage: " + sys.argv[0] + " <filename>"
sys.exit(1)
raw_log = sys.argv[1]
match = re.search(r"(\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3})", raw_log)
if not match:
sys.exit(1)
ip = match.group(0)
ping_result = subprocess.Popen(["ping", "-c", "3", ip], stdout=subprocess.PIPE).communicate()[0]
ping_output = ping_result.replace("\n", " | ")
print datetime.now().strftime('%Y-%m-%d %H:%M:%S') + " - The ping result for " + ip + " is: " + ping_output
After the Scheduled Search produces a result, the Collector triggers a script to run. The Script Action then gathers the output of the script, which can be queried for its results.
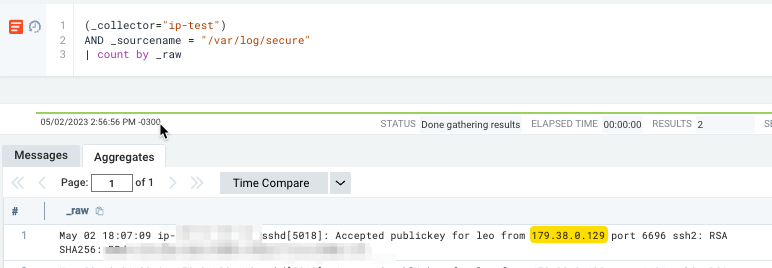
That's it! The script extracts an IP address from an event log, pings it, and ingests the result to the platform.

Now, you know! 😉
Subscribe to my newsletter
Read articles from WhatDoesKmean? directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

WhatDoesKmean?
WhatDoesKmean?
CyberSecurity 👽 | Splunk Ninja 🦸 | DataDog Tamer 🐾 | Sumo Logic Fighter 🧌 | Wazuh Explorer 🧙♂️ | EkoParty 2021 🎉 & SANS DFIR 2022 🔑 Speaker