Multi-Factor Authentication (MFA) in the Cloud
 James Ajayi
James AjayiTable of contents
- Introduction
- What is Multi-Factor Authentication?
- Different Multi-Factor Authentication Methods Used in Cloud Environments
- How to Implement Multi-Factor Authentication Work in the Cloud?
- Importance of Multi-Factor Authentication(MFA) for Securing Cloud Environment
- Considerations for Selecting the Right MFA Solution for your organization
- Conclusion

Introduction
Cloud technology is an integral part of modern business operations, offering a range of benefits such as cost-effectiveness, scalability, and cost-effectiveness. However, using cloud services also introduces new security risks, and organizations need to take appropriate measures to protect their cloud environments.
According to a recent report by Flexera on the state of the Cloud, security is the second biggest challenge cloud-based organisations worldwide face. Fortunately, Multi-Factor Authentication provides solutions to help organizations combat the ever-rising threats in the Cloud. This article will explore Multi-Factor Authentication, how it works, and why it is essential for securing cloud environments.
What is Multi-Factor Authentication?
Multi-Factor Authentication(MFA) is a security measure that mandates users to provide at least two authentication routes to access a system, application, or service. These authentication factors can be something that the user knows (e.g., password, PIN), something that the user has (e.g., smart card, token), or something that the user is (e.g., biometric data like fingerprint, voice recognition).
Multi-Factor Authentication is becoming increasingly important in today's digital landscape, especially as more and more applications and services move to the Cloud. It is often used with other security measures, such as encryption and access control, to provide a multi-layered approach to security.

According to a report by Microsoft, 99.9% of identity attacks can be prevented by using Multi-Factor Authentication. This statistic shows the effectiveness of Multi-Factor Authentication in preventing identity attacks. By implementing Multi-Factor Authentication, organizations can significantly reduce the risk of data breaches, protect their sensitive information, and maintain the trust of their customers.
Multi-Factor Authentication is a more secure form of authentication than traditional username and password authentication because it requires the user to provide at least one additional piece of information, making it more difficult for attackers to gain unauthorized access.
Different Multi-Factor Authentication Methods Used in Cloud Environments
There are several Multi-Factor Authentication (MFA) methods used in cloud environments. Here are some of the most common MFA methods:
One-Time Password(OTP) Authentication:
This method sends a unique code through SMS or email to a user. Next, the user inputs a code to verify their identity. The passcode is only valid for a short time.
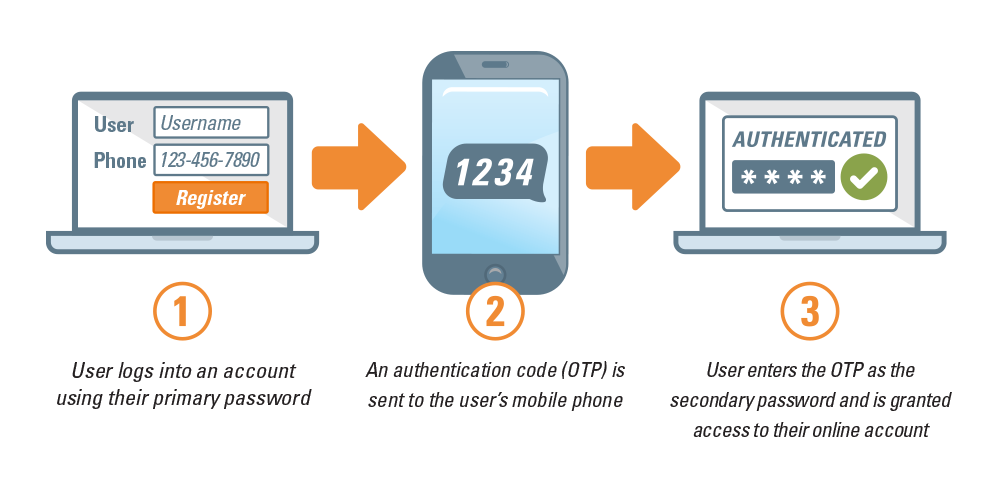
Benefits:
It cannot be reused.
No need for specialized hardware or software.
It can be implemented quickly and easily.
Drawbacks:
Vulnerable to SIM-swapping attacks.
It can be affected by mobile network coverage issues.
SMS messages and emails can be intercepted or redirected by attackers.
Software tokens:
This method involves installing a software token on a user's device, such as a mobile phone or tablet. The user must then enter a unique code generated by the token to authenticate their identity. Examples are Google and Microsoft Mobile Authenticators.

Benefits:
Convenient and easy to use.
It can be used on multiple devices.
No need for specialized hardware.
Drawbacks:
Vulnerable to malware attacks.
It can be lost or stolen.
It can be affected by device compatibility issues.
Hardware tokens:
This method involves using a physical token, such as a USB key or smart card, to authenticate a user's identity. The user must insert the token into a device and enter a unique code to gain access to the cloud environment.

Benefits:
Highly secure.
It cannot be easily duplicated or forged.
No need for network connectivity.
Drawbacks:
It can be expensive to purchase and maintain.
It can be cumbersome to use.
It can be lost or stolen.
Biometric authentication:
This method uses unique biological features, such as fingerprints, facial recognition, or iris scans, to authenticate a user's identity.

Benefits:
Highly secure.
Convenient and easy to use.
No need for additional hardware or software.
Drawbacks:
Requires specialized hardware and software.
It can be affected by environmental factors, such as lighting conditions.
Biometric data can be stolen or compromised.
How to Implement Multi-Factor Authentication Work in the Cloud?
Implementing Multi-Factor Authentication (MFA) in the Cloud depends on your cloud environment. Here's a general overview of how to implement Multi-Factor Authentication in different cloud environments:
Amazon Web Services (AWS): AWS provides several Multi-Factor Authentication(MFA) options, including virtual MFA devices, hardware MFA devices, and SMS MFA. To implement MFA in Amazon Web Services(AWS), you'll need to enable MFA for each Identity and Access Management(IAM) user or root user who requires it. You can then choose the MFA type that you want to use and configure the MFA device for each user.
Microsoft Azure: Azure offers various Multi-Factor Authentication(MFA) options, such as Azure MFA, conditional access policies, and third-party MFA providers. To implement MFA in Microsoft Azure, you can create an MFA provider, configure MFA for individual users or groups, and specify the authentication methods you want.
Google Cloud Platform (GCP): Google Cloud provides several Multi-Factor Authentication(MFA) options, such as Google Authenticator, FIDO U2F security keys, and SMS-based MFA. To implement MFA in Google Cloud, you'll need to enable MFA for your account and then configure MFA for individual users or groups using one of the available MFA methods.
Salesforce: Salesforce offers several Multi-Factor Authentication(MFA) options, including Salesforce Authenticator, SMS-based MFA, and security tokens. To implement MFA in Salesforce, you'll need to enable MFA for your org and then configure MFA settings for individual users or groups.
Oracle Cloud Infrastructure (OCI): Oracle Cloud Infrastructure provides several MFA options, including software tokens, hardware tokens, and SMS-based MFA. To implement MFA in Oracle Cloud Infrastructure, you'll need to enable MFA for your OCI account and then configure MFA settings for individual users or groups.
Importance of Multi-Factor Authentication(MFA) for Securing Cloud Environment
Multi-Factor Authentication (MFA) is essential for securing cloud environments, and here are some reasons why:
Prevents unauthorized access: MFA adds an extra layer of security to the cloud environment by requiring users to provide multiple authentication factors before gaining access. This implementation effectively increases security measures to prevent unauthorized access to crucial information or resources.
Protects against credential theft: Passwords can be easily stolen or guessed, so MFA is crucial for protecting against credential theft. Although an attacker may obtain a user's password, they will still require an extra authentication factor to gain entry into the cloud environment.
Complies with regulations: Many industry regulations, such as the Payment Card Industry Data Security Standard(PCI-DSS) and the Health Insurance Portability and Accountability Act (HIPAA), require using MFA to protect sensitive data. By implementing MFA, organizations can ensure compliance with these regulations.
Enhances user experience: MFA can improve the user experience by providing additional options for authentication. For example, users may prefer a biometric authentication method, such as a fingerprint scan or facial recognition, over a traditional password.
Provides audit trail: MFA can help provide an audit trail of user activity within the cloud environment. By requiring users to provide multiple authentication factors, organizations can better track who is accessing what resources and when.
Considerations for Selecting the Right MFA Solution for your organization
When selecting an MFA solution for your organization, there are several considerations to remember. Here are a few things to consider:
Compatibility with Your Cloud Environment: Not all MFA solutions are compatible with all cloud environments. Ensure the solution you choose can be integrated into your current cloud infrastructure, whether AWS, Azure, Google Cloud, or another provider.
Types of Authentication Factors Supported: As earlier explained, different MFA solutions support various authentication factors. Consider your organization's specific needs and preferences when selecting an MFA solution.
Ease of Use: MFA solutions should be user-friendly and easy for employees. If an MFA solution is too complicated to use, it may be more of a hindrance than a benefit.
Integration with Existing Identity and Access Management (IAM) Tools: MFA solutions should be integrated with your existing IAM tools to streamline authentication processes and ensure access is granted only to verified users.
Cost: MFA solutions can vary widely, depending on the features offered. Consider your organization's budget and the MFA solution's value in terms of improved security and compliance.
Scalability: Your MFA solution should be able to scale as your organization grows and expands. Consider the number of users and devices needing support, and ensure the solution can accommodate future growth.
Security Features: Look for MFA solutions that offer additional security features, such as threat detection and adaptive authentication. These features can help protect your organization against advanced threats and attacks.
Conclusion
It's crucial for organizations to adopt Multi-Factor Authentication (MFA) as a vital security measure to safeguard their cloud environments. With the increasing adoption of cloud services, it is essential to take appropriate steps to protect sensitive data and systems from unauthorized access.
MFA is a critical security measure that can help organizations mitigate risks associated with cloud computing and enhance the overall security posture of their organization.
Thanks for reading!
Subscribe to my newsletter
Read articles from James Ajayi directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

James Ajayi
James Ajayi
Hello there! I'm a Software Developer and technical writer. I help SaaS brands and startups in creating technical content that increase search engine ranking, traffic generation, lead conversion, user retention and brand awareness. I do this by creating educative and engaging content that simplifies complex concepts for easy understanding and application.