Effortlessly Manage Your Resource Demands: How Terraform Autoscaling Can Help You.
 Sushrut Netkar
Sushrut Netkar
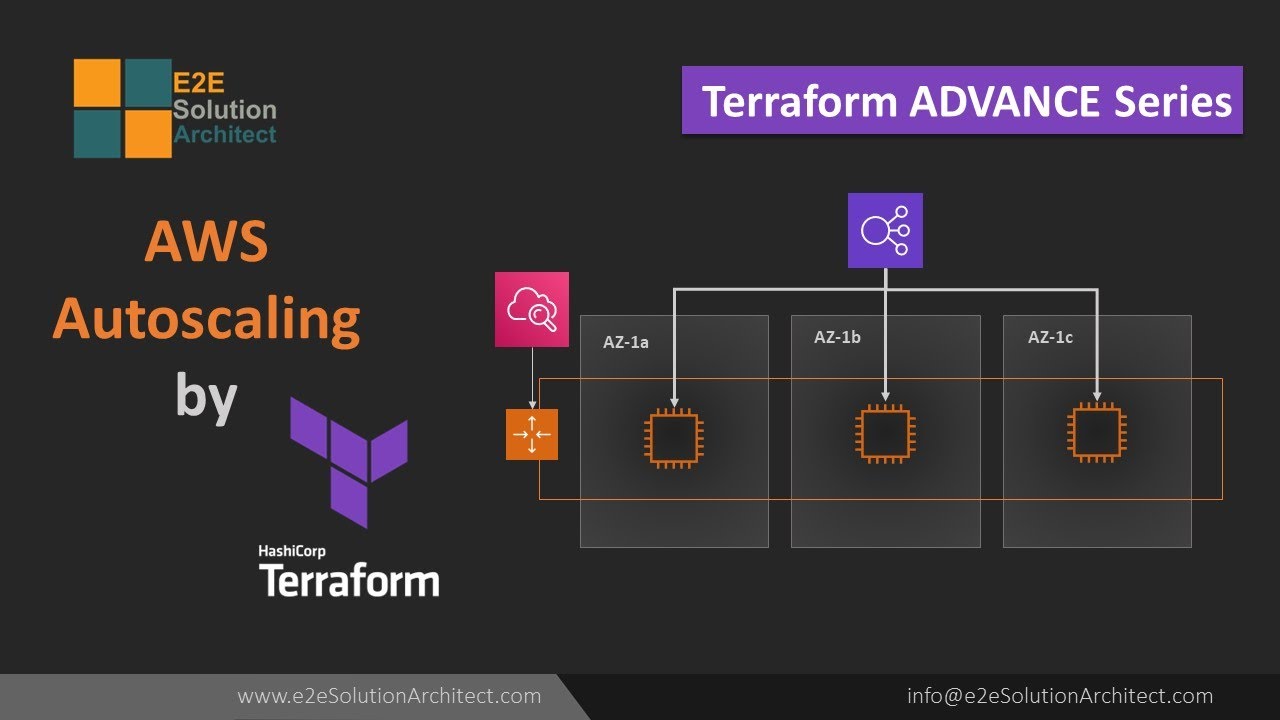
As your business grows, so does the demand for your services. To keep up with the increased traffic, you need to scale your infrastructure. This means adding more servers or resources to handle the load. However, manually scaling your infrastructure can be time-consuming and error-prone. This is where Terraform autoscaling comes in.
Terraform autoscaling is a feature that allows you to automatically add or remove resources based on the demand of your application. For example, if your website is experiencing a sudden spike in traffic, Terraform autoscaling can automatically add more servers to handle the load. Conversely, if the traffic decreases, Terraform autoscaling can remove the servers to reduce costs.
Prerequisites
Before we get started, you'll need to make sure that you have the following:
An AWS account
Terraform installed on your local machine
AWS access keys (access key ID and secret access key)
Implementing Terraform Autoscaling

First, we need to specify the provider we want to use, in this case, AWS. We set the region to us-east-2.
provider "aws" {
region = "us-east-2"
}
Next, we define the AWS VPC. The aws_vpc resource creates a VPC with a specified CIDR block.
resource "aws_vpc" "example" {
cidr_block = "10.0.0.0/16"
}
We also create a subnet, which is associated with the VPC we created above. The aws_subnet resource creates a subnet with a specified CIDR block and availability zone.
resource "aws_subnet" "example" {
vpc_id = aws_vpc.example.id
cidr_block = "10.0.1.0/24"
availability_zone = "us-east-2a"
}
We create a security group associated with the VPC we created above. The security group allows inbound traffic from anywhere on any port.
resource "aws_security_group" "example" {
name_prefix = "example-"
vpc_id = aws_vpc.example.id
ingress {
from_port = 0
to_port = 65535
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
}
We create an IAM instance profile that can be associated with an EC2 instance to provide it with an IAM role.
resource "aws_iam_instance_profile" "example" {
name = "example-profile"
role = aws_iam_role.example.name
}
We create an IAM role that specifies what actions EC2 instances associated with the role are allowed to perform.
resource "aws_iam_role" "example" {
name = "example-role"
assume_role_policy = jsonencode({
Version = "2012-10-17"
Statement = [
{
Effect = "Allow"
Principal = { Service = "ec2.amazonaws.com" }
Action = "sts:AssumeRole"
}
]
})
}
We create a launch configuration that specifies how to launch EC2 instances in the autoscaling group. The launch configuration uses the Amazon Machine Image (AMI) with ID ami-0c55b159cbfafe1f0 and an instance type of t2.micro. We also associate the security group and IAM instance profile created above with the launch configuration. Finally, we specify the user data that will be run when the instance launches.
resource "aws_launch_configuration" "example" {
name_prefix = "example-"
image_id = "ami-0c55b159cbfafe1f0"
instance_type = "t2.micro"
security_groups = [aws_security_group.example.id]
iam_instance_profile = aws_iam_instance_profile.example.name
user_data = <<EOF
#!/bin/bash
echo "You're doing really Great" > index.html
nohup python -m SimpleHTTPServer 80 &
EOF
}
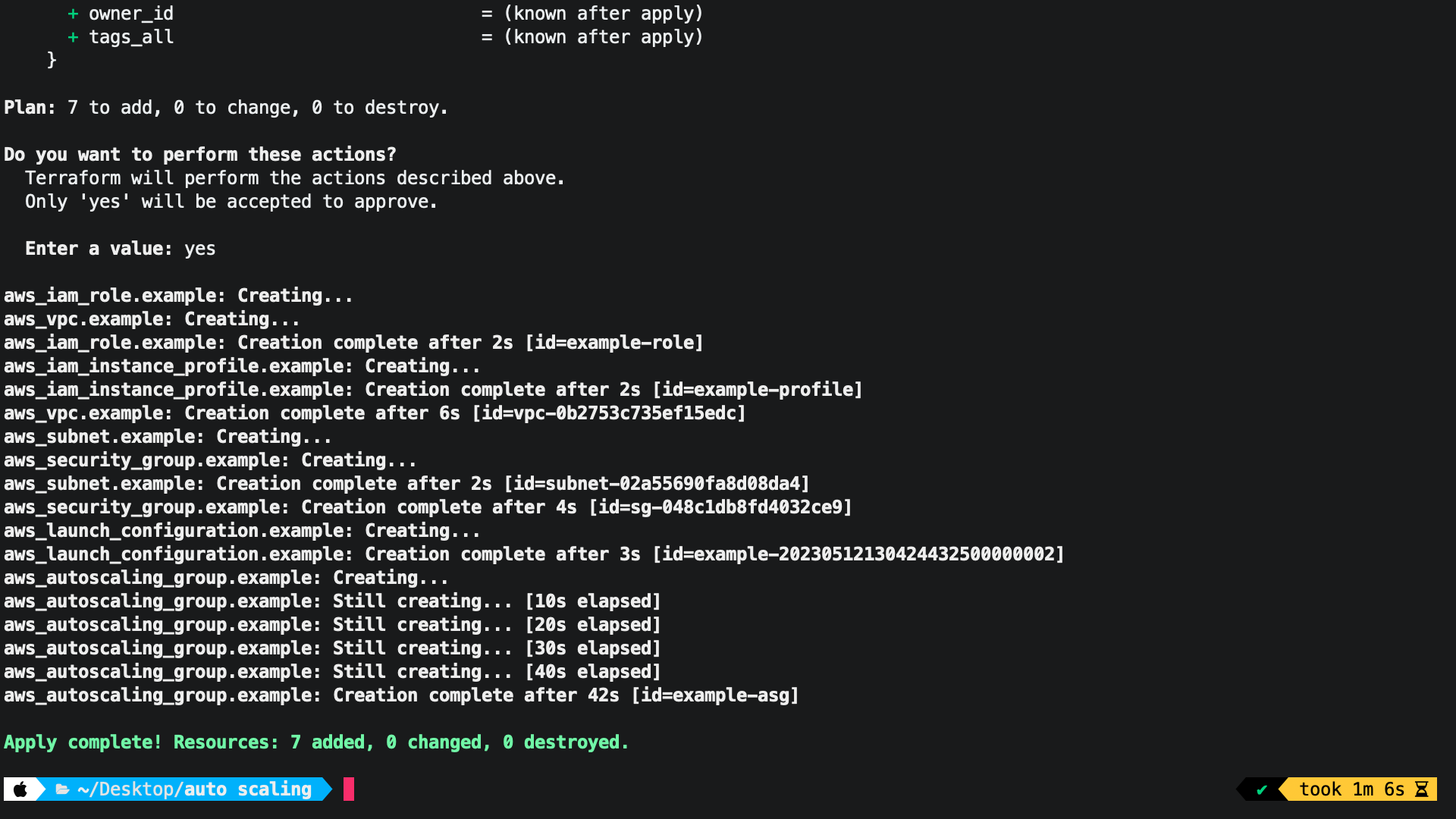
This code block creates an AWS Auto Scaling Group resource named "example-asg". An Auto Scaling group is a collection of EC2 instances that are launched from a common template (a launch configuration).
resource "aws_autoscaling_group" "example" {
name = "example-asg"
launch_configuration = aws_launch_configuration.example.id
min_size = 1
max_size = 3
desired_capacity = 2
health_check_type = "EC2"
vpc_zone_identifier = [aws_subnet.example.id]
}
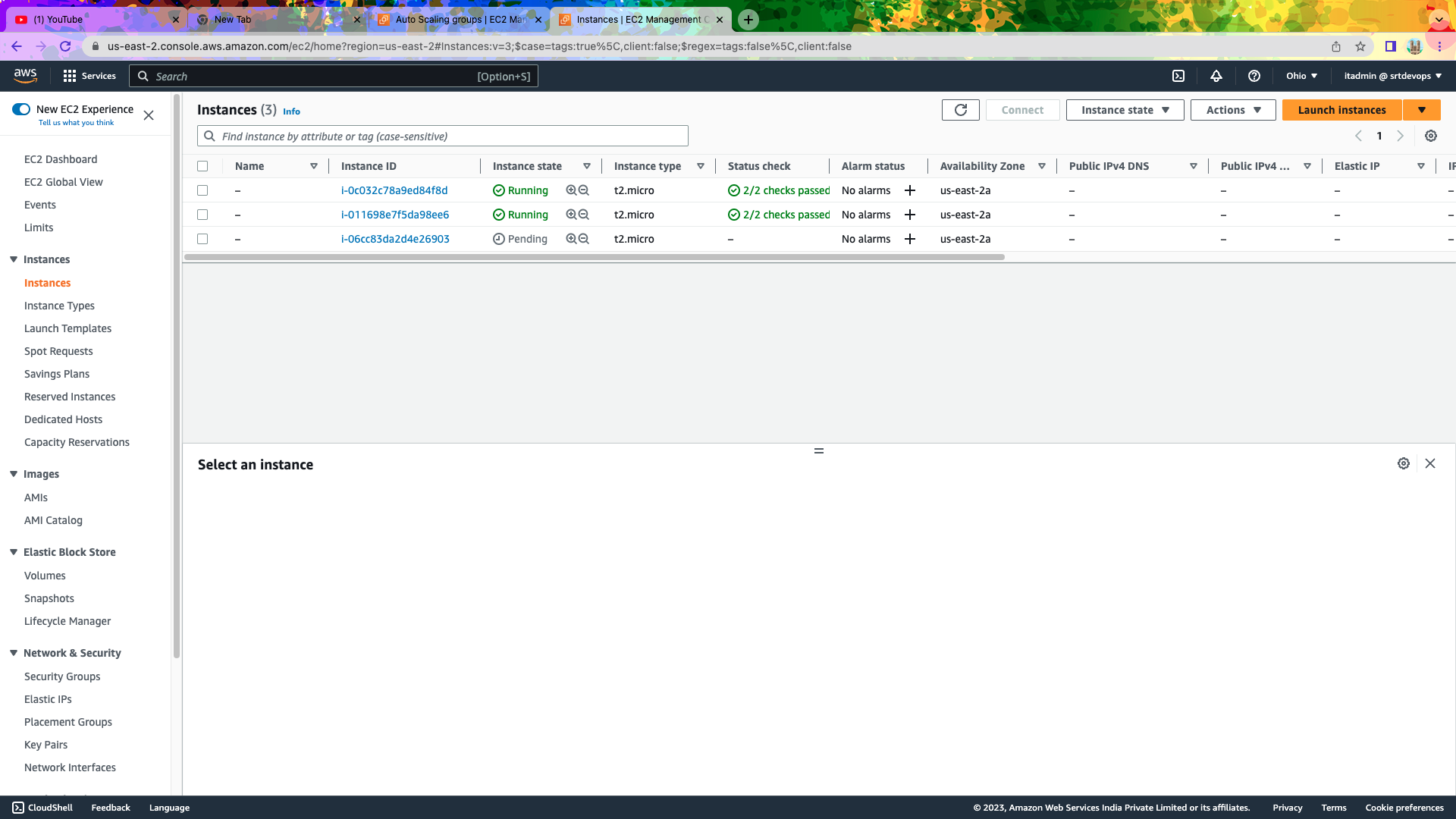
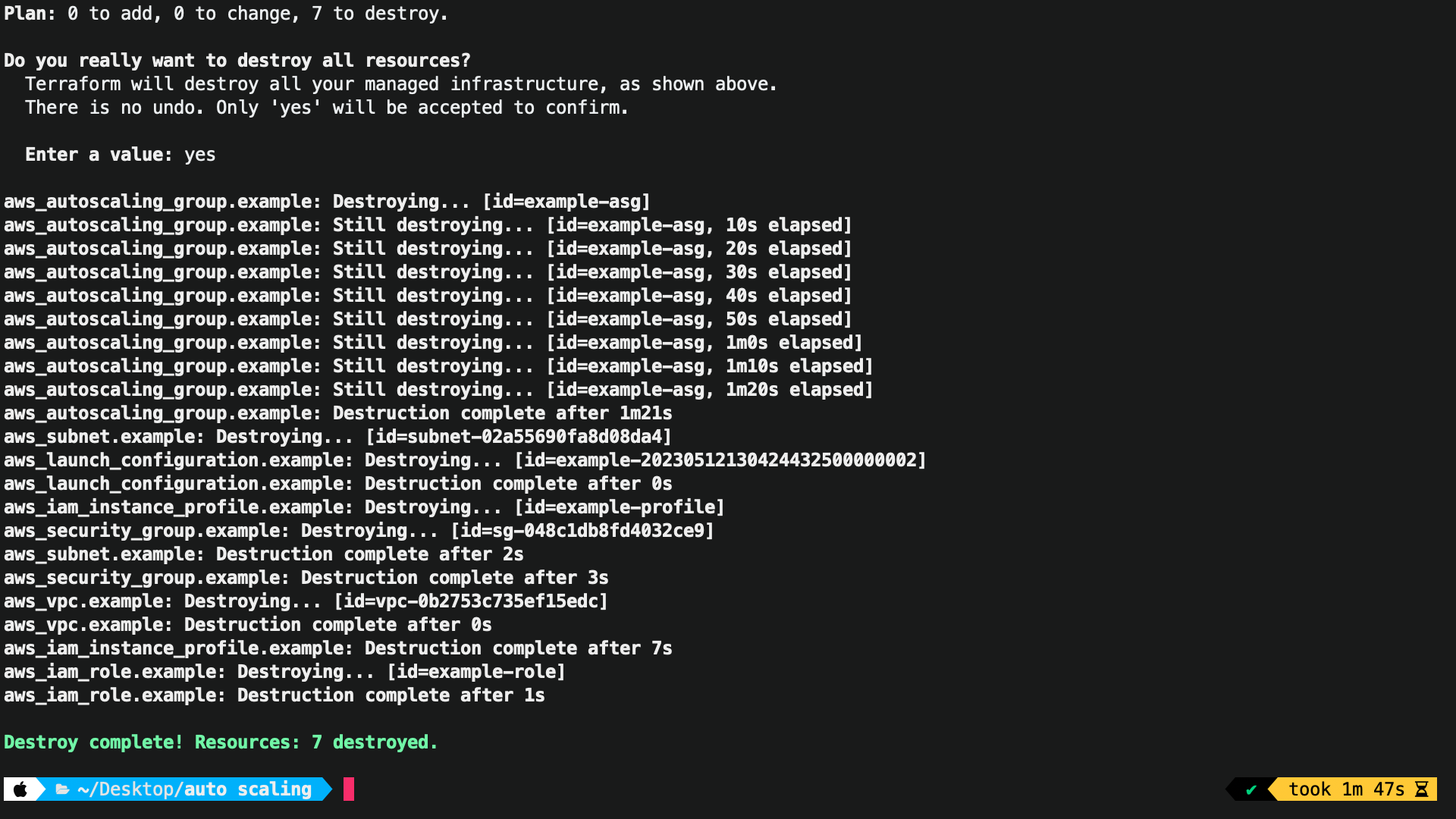
After Apply
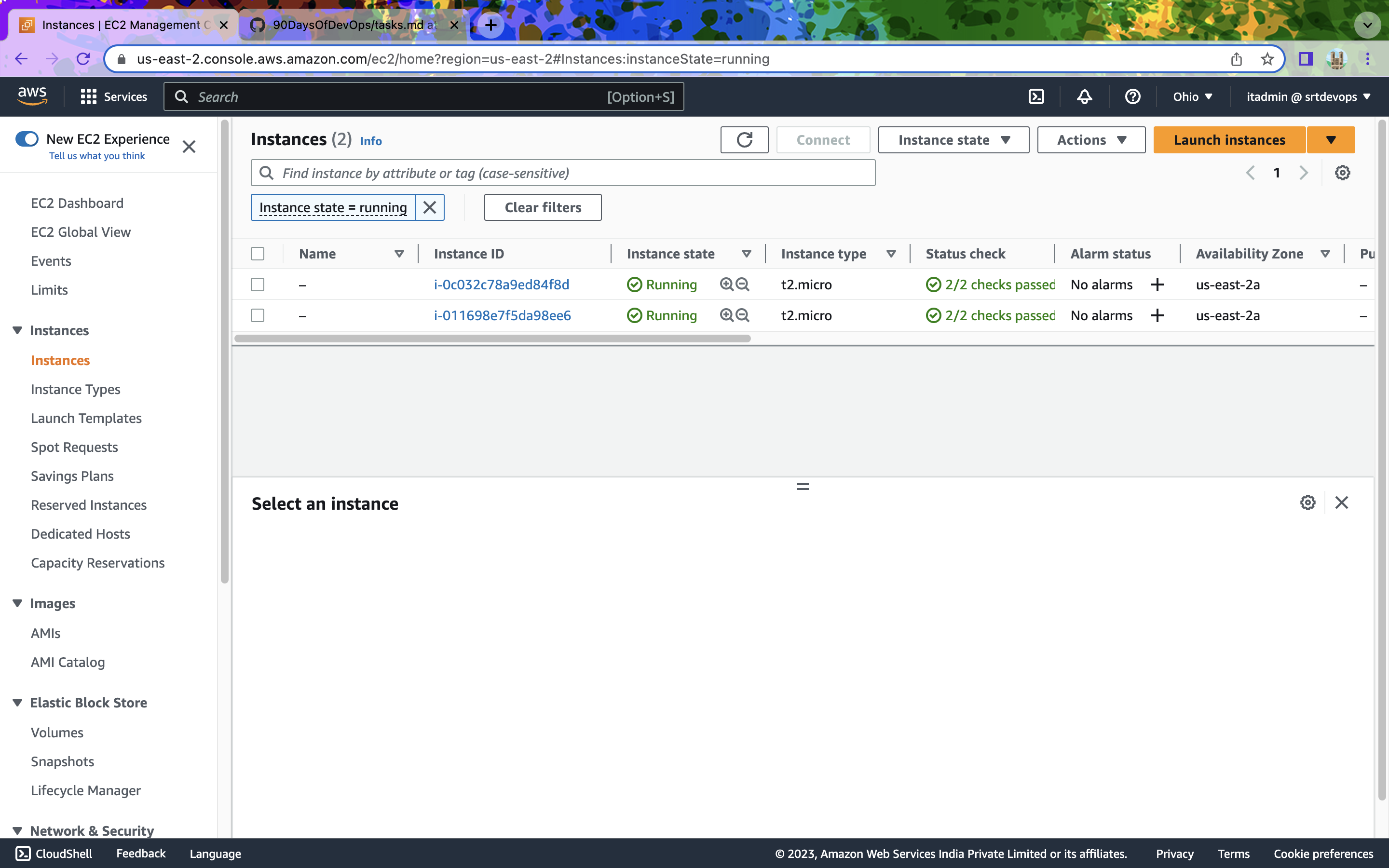
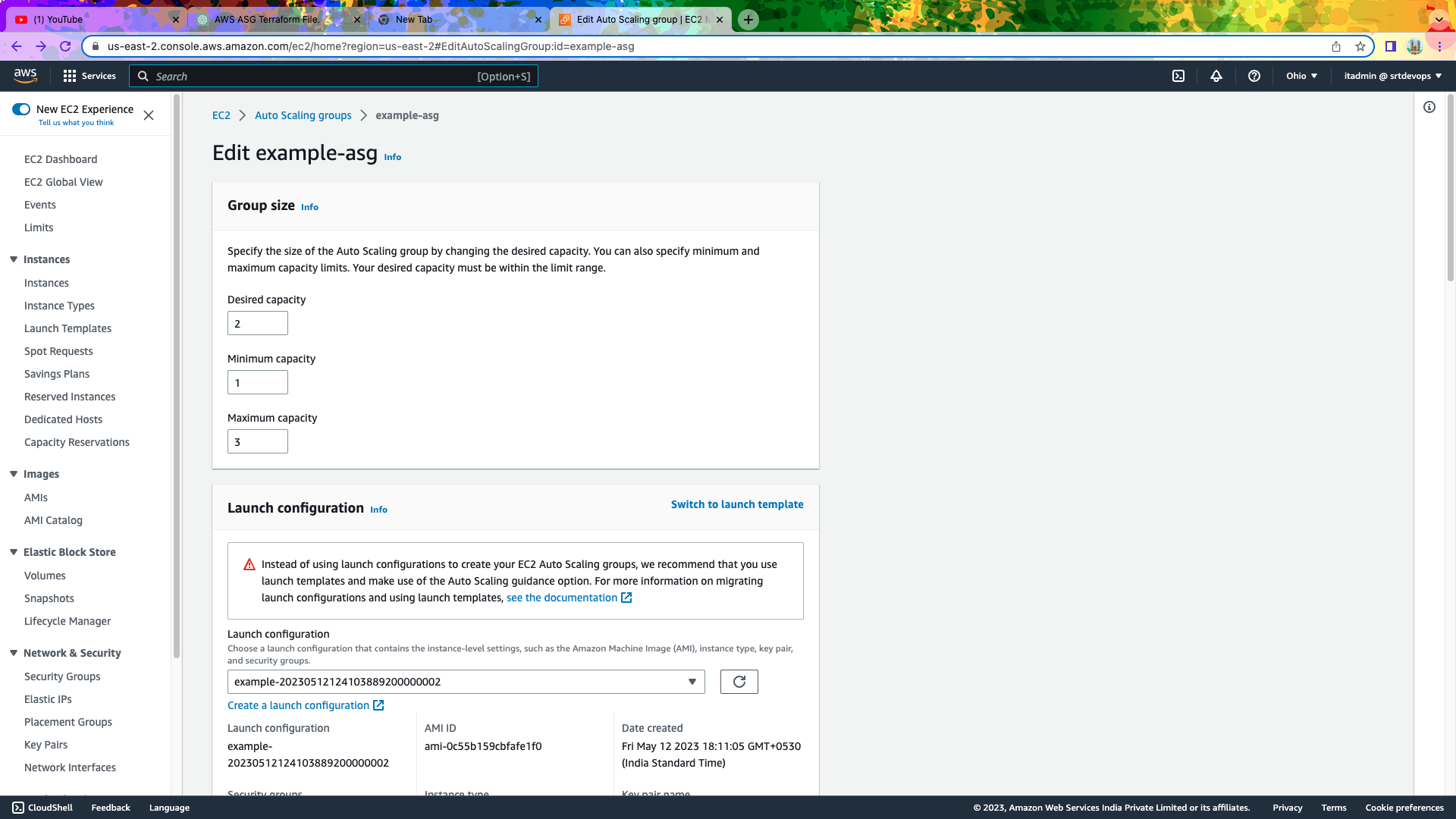
Frome Desired Capacity You Can Increase Or Decrease.


Subscribe to my newsletter
Read articles from Sushrut Netkar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
