Create Custom Wordlists for Password Cracking Using the Mentalist
 LoneD3VIL
LoneD3VILTable of contents
- Brute-Forcing WPA, SSH, FTP & Other Passwords
- Starting Point Options: Default Lists
- Details Approach — OSINT Research
- Custom Wordlist Generators
- Word Manglers & Generating Chains
- Download the Software
- Create the Seed List
- Create a Chain with the Mentalist
- Defending Against Tailored Brute-Force Attacks

The restrictions of default wordlists like RockYou based on stolen passwords frequently let down beginners learning brute-forcing attacks against WPA handshakes. By creating personalized wordlists, we can increase our efficiency beyond simply using these pre-made lists. Based on information about the target, we can generate millions of likely passwords using the Mentalist.
It takes a mix of brute-force processing power and the capability to narrow down your list to likely alternatives based on what you know about a target to successfully crack a password. Numerous security methods are susceptible to brute-forcing attacks, which are fundamentally based on a few fundamental ideas.
To begin with, you must be permitted to quickly and repeatedly attempt a variety of passwords. Second, you must be able to tell whether a password is successful or unsuccessful. Third, you require a list of passwords to rapidly and automatically try. Finally, for the attack to be successful, the password needs to be in the list. As password attempts are made more quickly as password lists grow, CPU and GPU speed become more crucial.
Brute-Forcing WPA, SSH, FTP & Other Passwords
The majority of wireless networks use WPA or WPA2 encryption, which may be broken by intercepting a network handshake and brute-forcing the password using the CPU of your machine. In addition to WPA, protocols like SSH and FTP are also susceptible to brute-forcing, albeit there are differences between online and offline types of assaults in the brute-forcing techniques.
When conducting an online assault, we establish a direct connection with the target service and send documented password attempts. Reaver or SSHtrix are two examples of this, both of which require network connectivity to submit password guesses to the host. The number of incoming connections the FTP or SSH server may accept and the amount of time you have to be connected to the host while cracking is frequently the limiting factors in these attacks.
The main constraint on an offline attack is how rapidly your CPU or GPU can try various passwords. Examples of this include breaking password hashes from a stolen database or brute-forcing a WPA handshake after gathering the relevant data. Generally speaking, this is the only instance where you need to be concerned about the performance of your GPU or CPU during brute force.
Starting Point Options: Default Lists
An intelligent attacker would frequently initially search for lists that contain real passwords rather than simply starting with a dictionary-style attack. These lists are typically regarded as the starting point for these kinds of tactics because they may be used to attack anyone who uses a password that is either really bad or widely used. For these kinds of password audits, you can anticipate success rates of about 15% in the real world. Naturally, this is a relatively slim probability of success if you are aiming for a particular account or network.
Despite this, you can still use these lists as a starting point for a more targeted attack based on knowledge of the target. These lists are useful since they provide a statistical analysis of the most popular passwords that people use. Since most users reuse these passwords across numerous accounts, we may utilize the most popular passwords as a starting point for tiny changes in a program called a word mangler, like adding or removing numerals.
Details Approach — OSINT Research
Luckily for hackers, there is a wealth of knowledge available online when attempting to break a specific target. An organization that mandates the use of strong passwords may not be seriously threatened by a brute-force attack by the typical script child. However, a well-planned brute-force assault can limit the number of guesses and provide only somewhat solid suggestions depending on the target's information and any password constraints. Because of this, a brute-force attack may be successful against some well-studied portions of a target's architecture.
We can provide the information for wordlist creator programs that employ information learned about a target to construct a unique wordlist based on details the user may have drawn from while creating their password with a little bit of study.
Custom Wordlist Generators
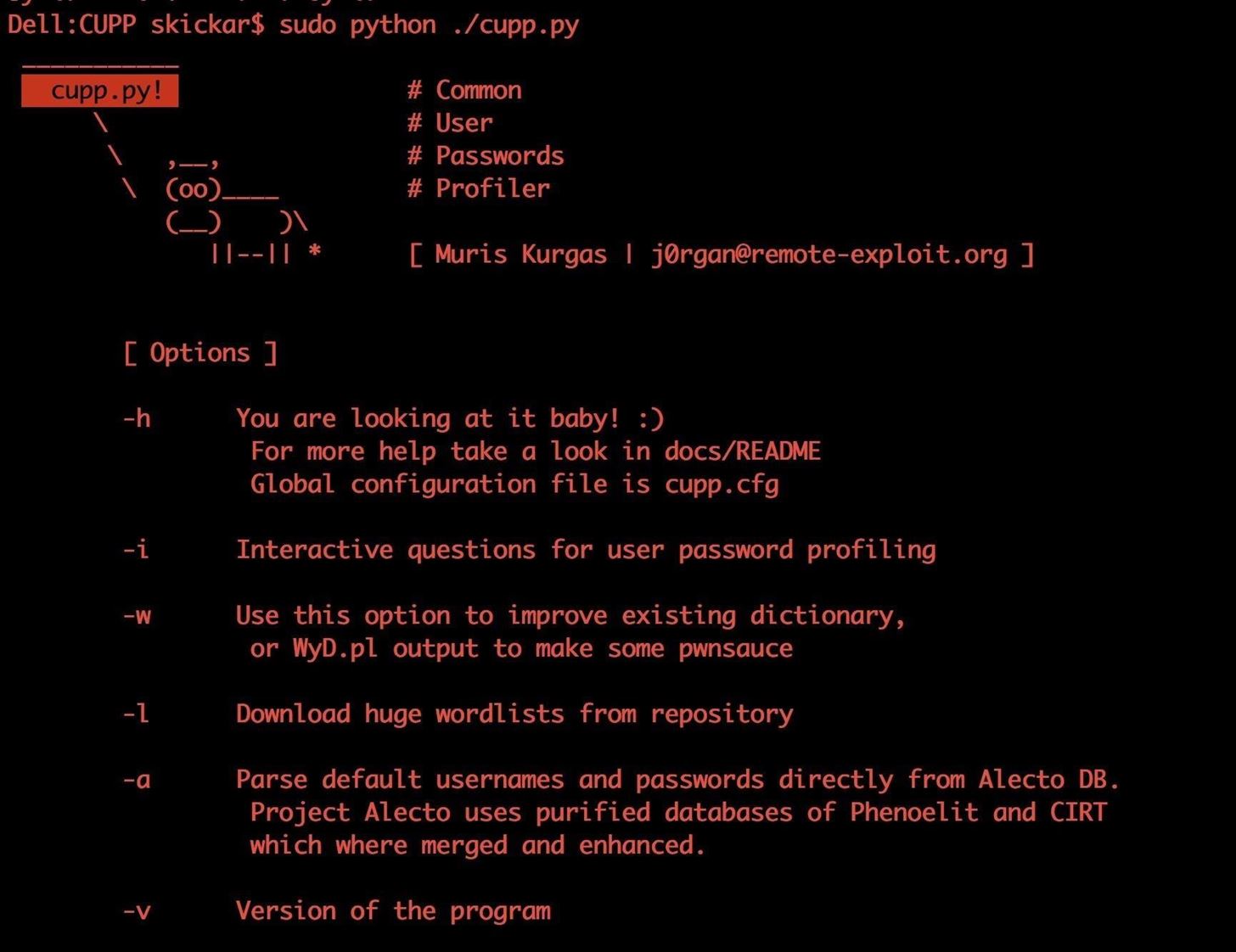
In addition to using a simple dictionary, there are other ways to create wordlists. Today, we'll look at Common User Passwords Profiler (or CUPP). CUPP is a lightweight, straightforward Python program that can provide an astounding seed of unique password guesses. Other tools, such as CeWL, enable target websites to be scraped for distinctive terms so that words that are widespread inside the organization can be used.
Running CUPP in the user interactive mode enables an interview-style approach to create a bespoke password list with a little bit of information obtained from social media and other public sources.
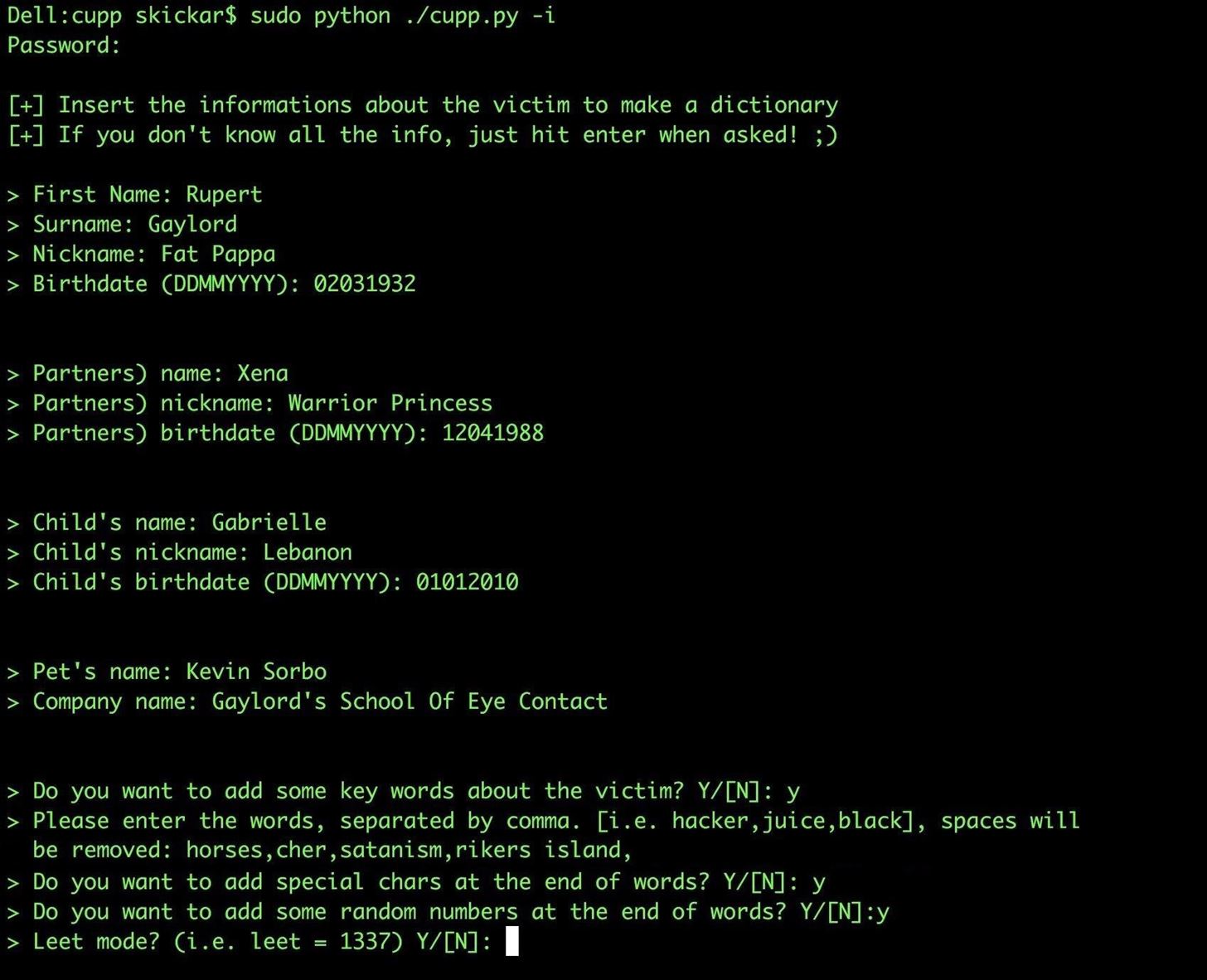
The aforementioned example generated 14,301 words in our test file, which is a wonderful start but insufficient to launch a successful brute-force attack. However, we can use this output to create a much larger password list by applying certain rules to these initial seeds using a word mangler, a more advanced wordlist generator.
Word Manglers & Generating Chains
According to predetermined rules, a word mangler generates fresh password guesses from a list of "seed" passwords. This modification might be as straightforward as adding a single change to the end of each seed password or as complex as appending the numbers 0 through 9 to the end of each seed password. For every password entered into the latter, 10 new password guesses would be generated, so these lists might grow quite quickly.
We'll use the Mentalist, a graphical program that enables us to establish a "chain" of these rules to apply to our seed password list, to manage these rules conveniently. In addition to our password list, we can also scatter other seeds, like words from the English lexicon. The main "nodes" that can be used to modify the basic word list often add, prepend, change the case of, or substitute letters from the words that are sent through them.
Applying just a few criteria to the chain can result in a significant expansion of the size of your password list, as you can see in the example below. This isn't always a good thing because we'll need a processor that can truly chew through these password guesses. Probably overkill, but this password collection has over a billion guesses. The length of the list will vary depending on how many and what kind of nodes you apply, but we'll go over each one.
Download the Software
The Mentalist is easy to run even for absolute beginners, so we can download it for Windows, macOS, or Linux. To do so, you can head to the download link on GitHub and select the version that matches your operating system. After downloading it, install the application following the on-screen prompts, then open the Mentalist.
To create our seed list, we'll use CUPP. Aside from making sure you have Python installed and updated on your computer, it shouldn't require additional dependencies to run. You can download CUPP by running the following in a terminal window.
git clone github.com/Mebus/cupp.git
Create the Seed List
Once you've downloaded CUPP, you'll be ready to use the data you've gathered on a target to generate a custom list. Navigate to the directory CUPP was cloned into by typing cd CUPP into your terminal window. Next, type python ./cupp.py -i to run CUPP in the interactive-user mode.
You'll see a series of prompts asking for information about the target. If you don't know, you can skip the particular question, but it's best to answer as many questions as you can find the information for.
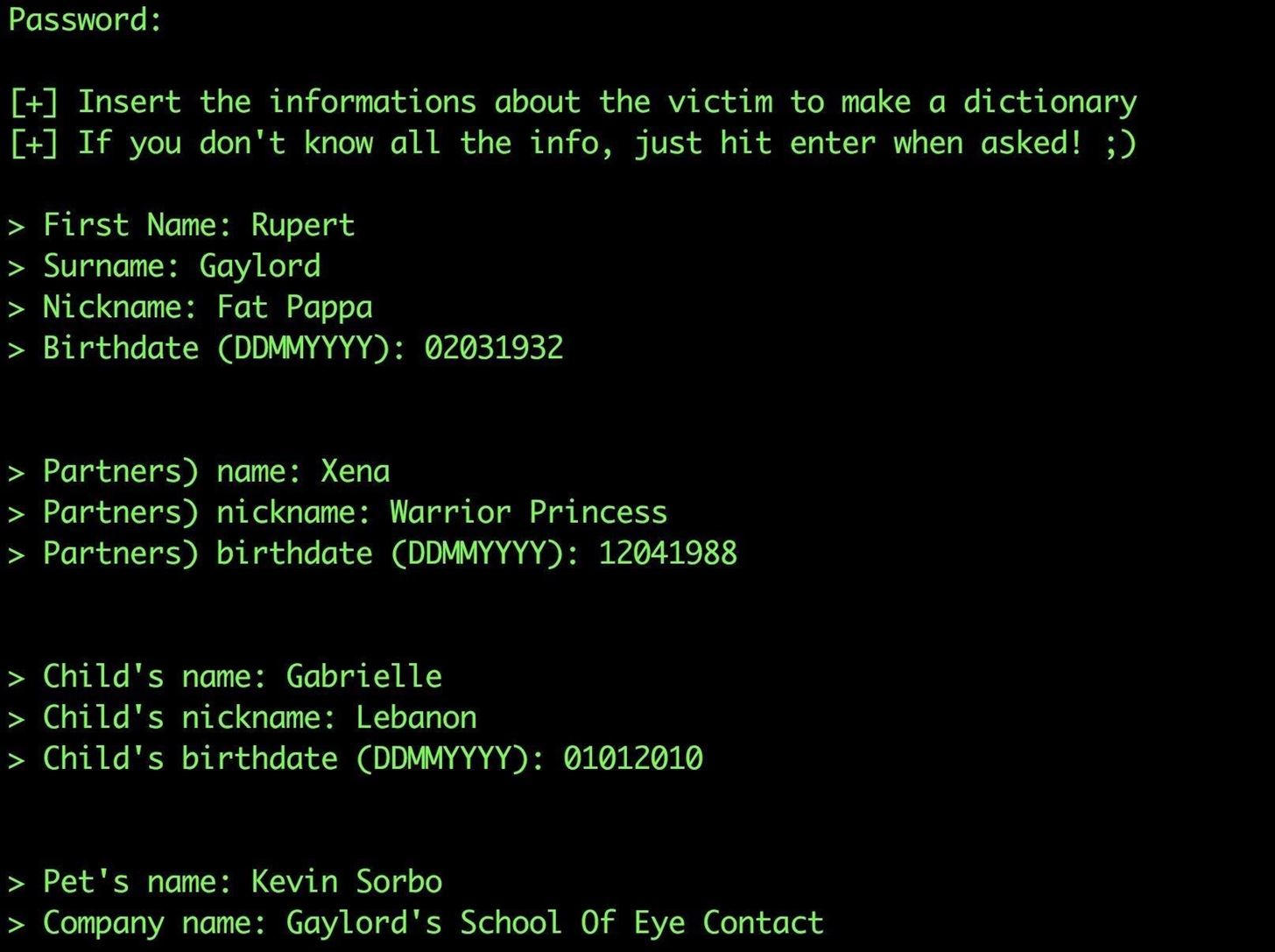
Once you enter the information you know, you'll be given the opportunity to add additional keywords you know about the target that can be thrown into the mix. At this point, you can also select the option to add special characters at the end of a password guess or add random numbers at the end. Finally, if your target thinks using leetspeak is clever, you can select a substitution rule that will convert password guesses to 1337 formatting.
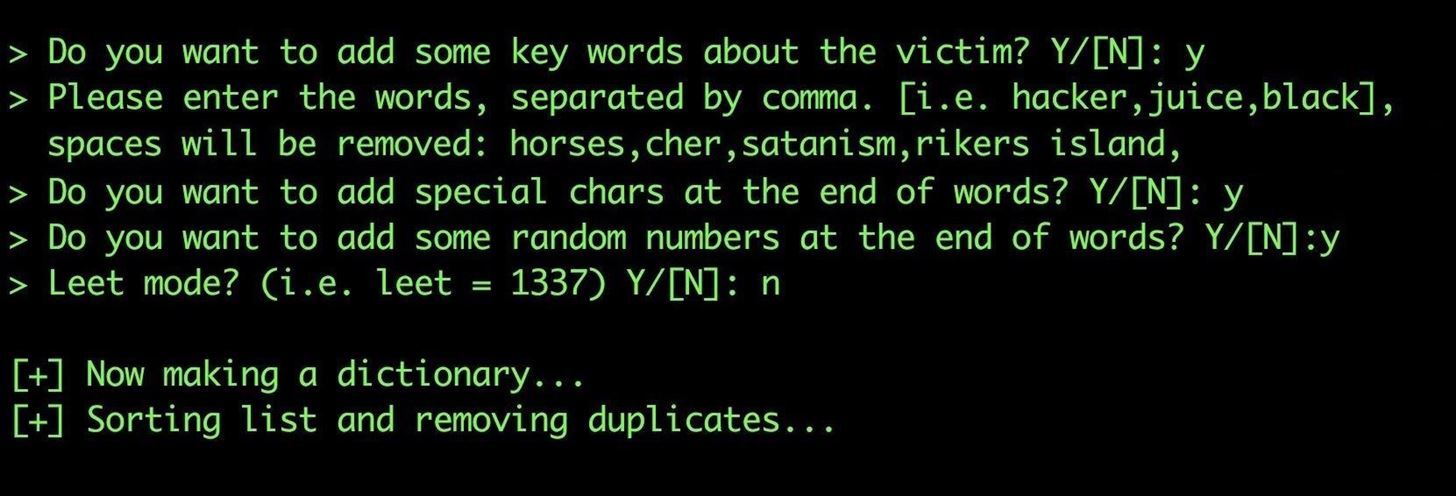
Once this is complete, the output should be a text file with thousands of password guesses. While this is a great start, it's time to expand our guesses with the Mentalist.
Create a Chain with the Mentalist
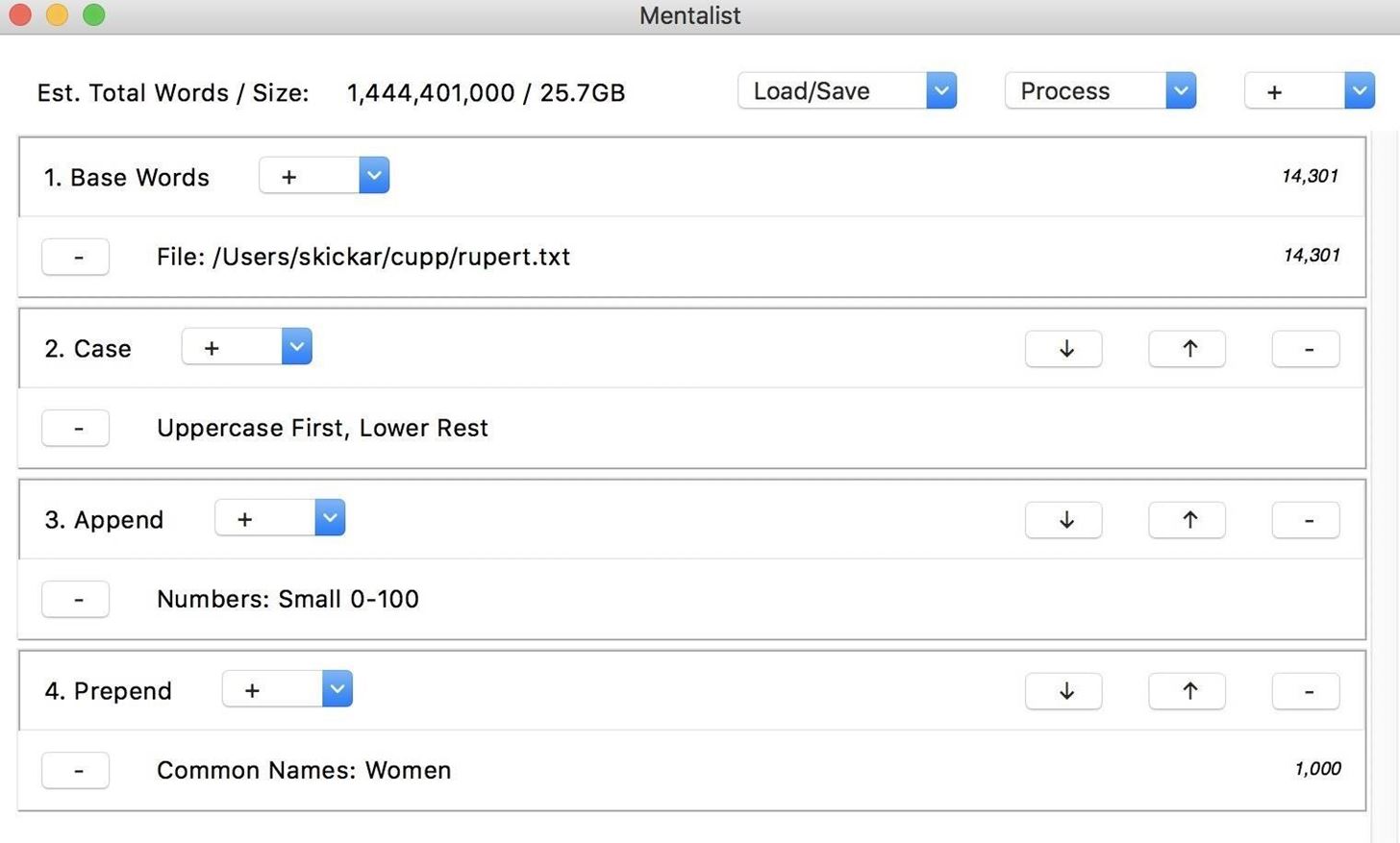
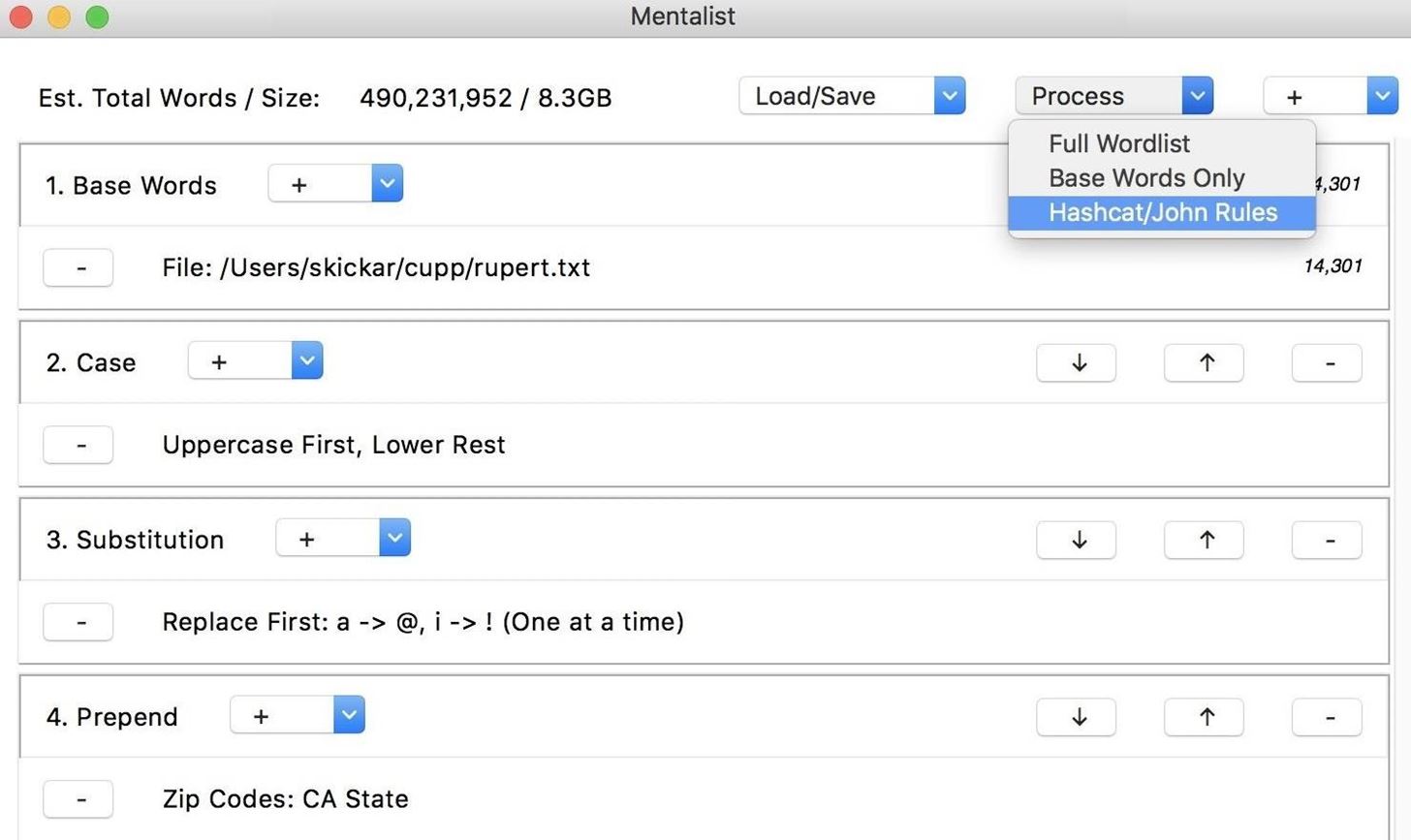
To get started, open the Mentalist application you downloaded and installed previously. Once you see the GUI window, click on the plus in the "Base Words" node, and you'll see the option to add a custom file. Select "Custom File," and then open the TXT file we created with CUPP. We can also delete the English dictionary default node by clicking the minus button to the right of it.
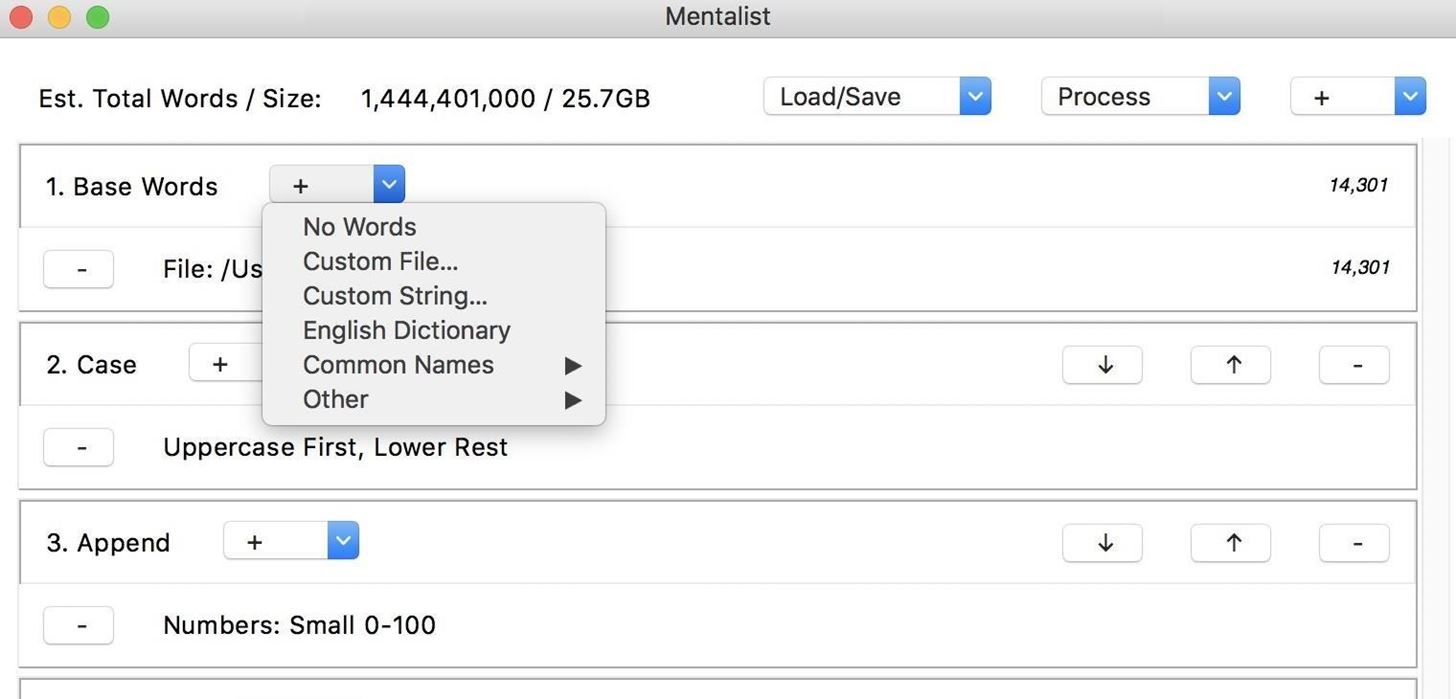
Once we have the base words added from CUPP, we can start adding our word mangling nodes. To create a chain, we will need to apply all of the rules we'd like to apply to our password guesses in sequence. We can explore the four main types of nodes we can add by clicking on the plus button in the top-right corner. This will give us a list of case modifications, substitutions, prepend, or append.
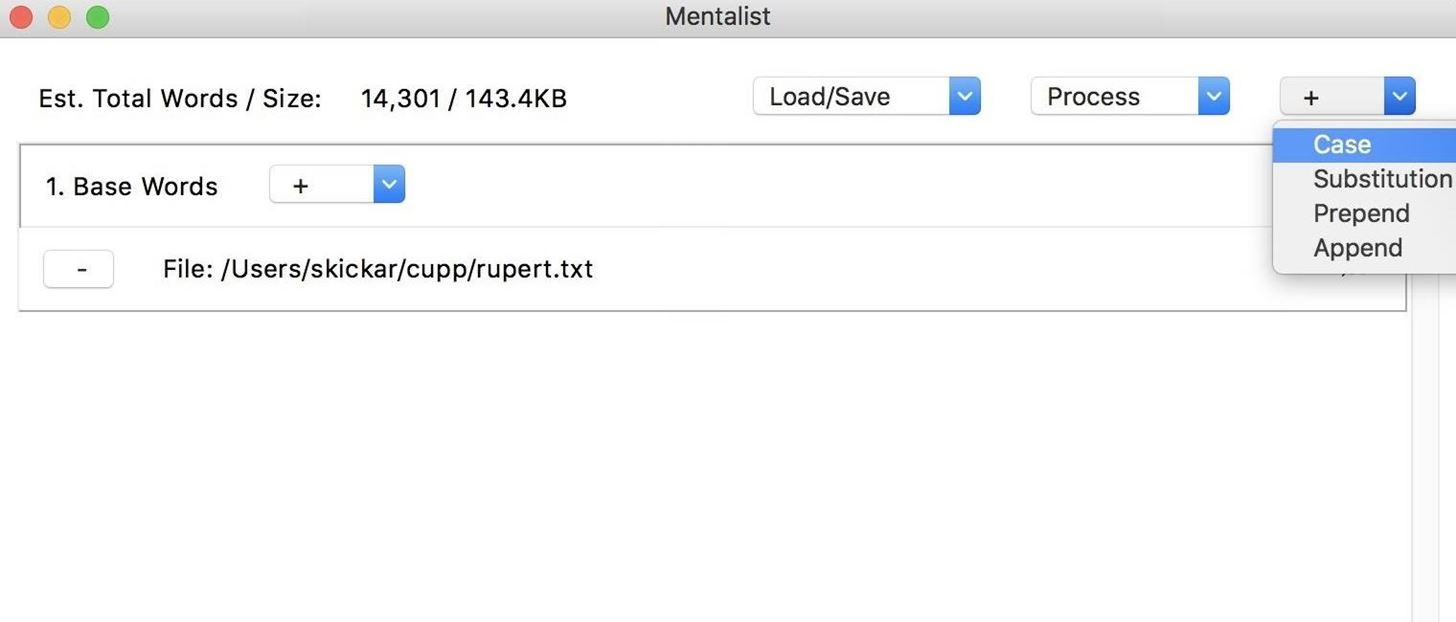
For our first node, we can apply a "Case" node to modify the case of our generated password guesses. Once we select the node, we can click the plus button next to the node we created to see a list of options. We can modify uppercase or lowercase in different ways. Here, we'll set the first letter to uppercase, and all following lowercase letters. Since this operation only creates one output per word from our base list, you won't see the size of the wordlist file change yet.
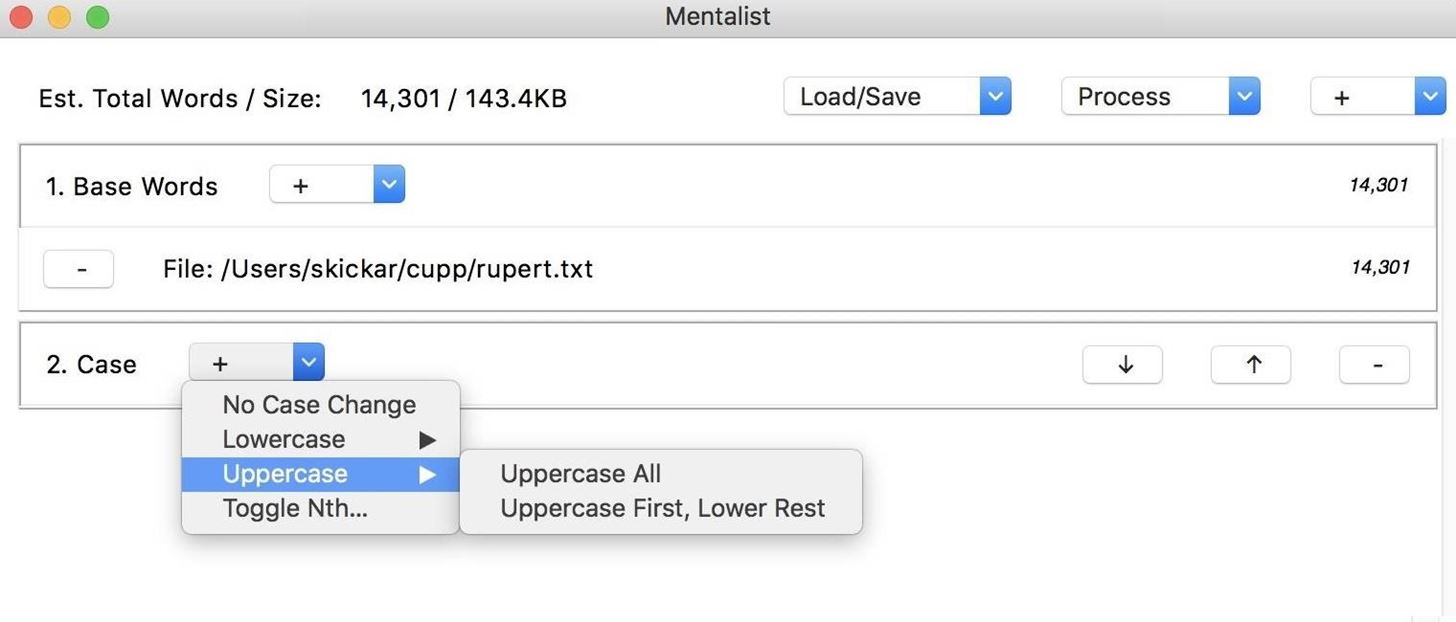
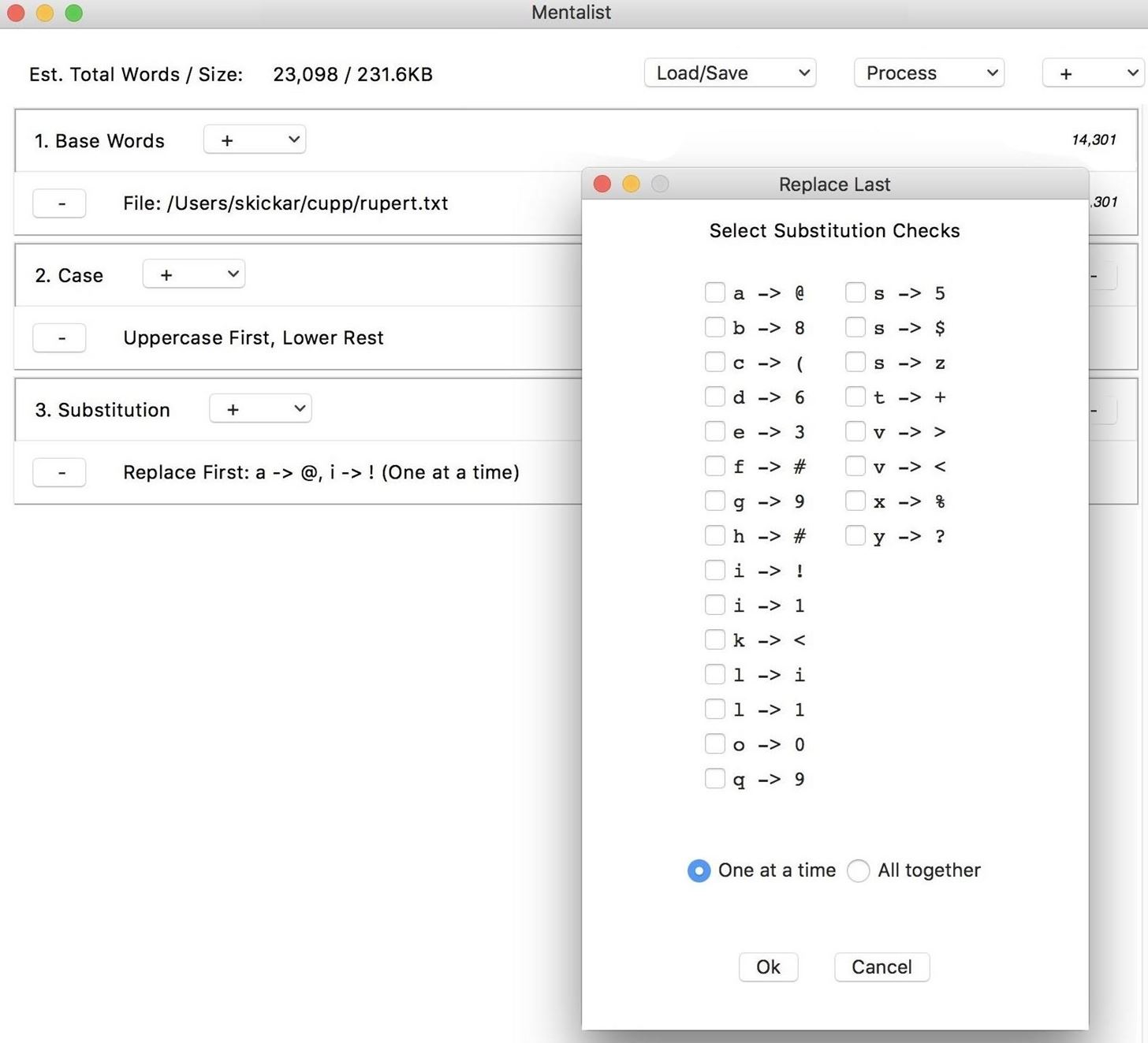
Next, we can add a "Substitution" node by clicking the plus icon in the top-right corner again. This will give us the option to substitute letters, and in this case, we'll choose to substitute the letters "i" and "a" for their leetspeak counterpart.
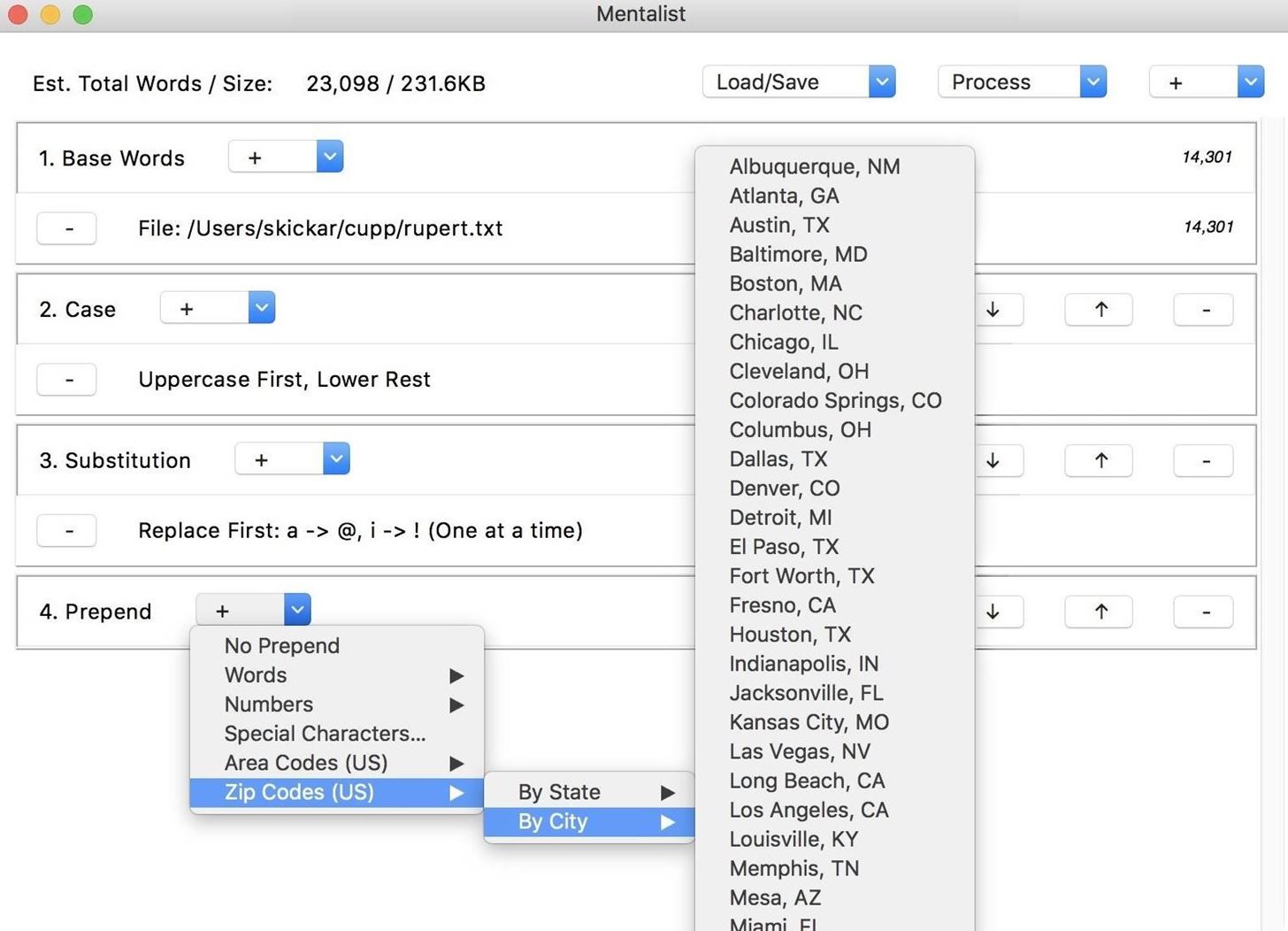
Next, we can add a "Prepend" node, which will add something to the beginning of each password guess. By clicking the plus icon next to the node we created, we can do things like incorporate zip codes by city or state. This will increase the size of our file by creating many outputs for each base word that goes into the node.
Finally, we can add an "Append" node, which will put something at the end of our word guesses. By again clicking on the plus icon next to the node we created, we can see there are many options preinstalled for what we can add to our chain. In this case, I chose to add telephone area codes from the city of Los Angeles. This will increase our output even more, as for each guess passing into this node, there will be many outputs.
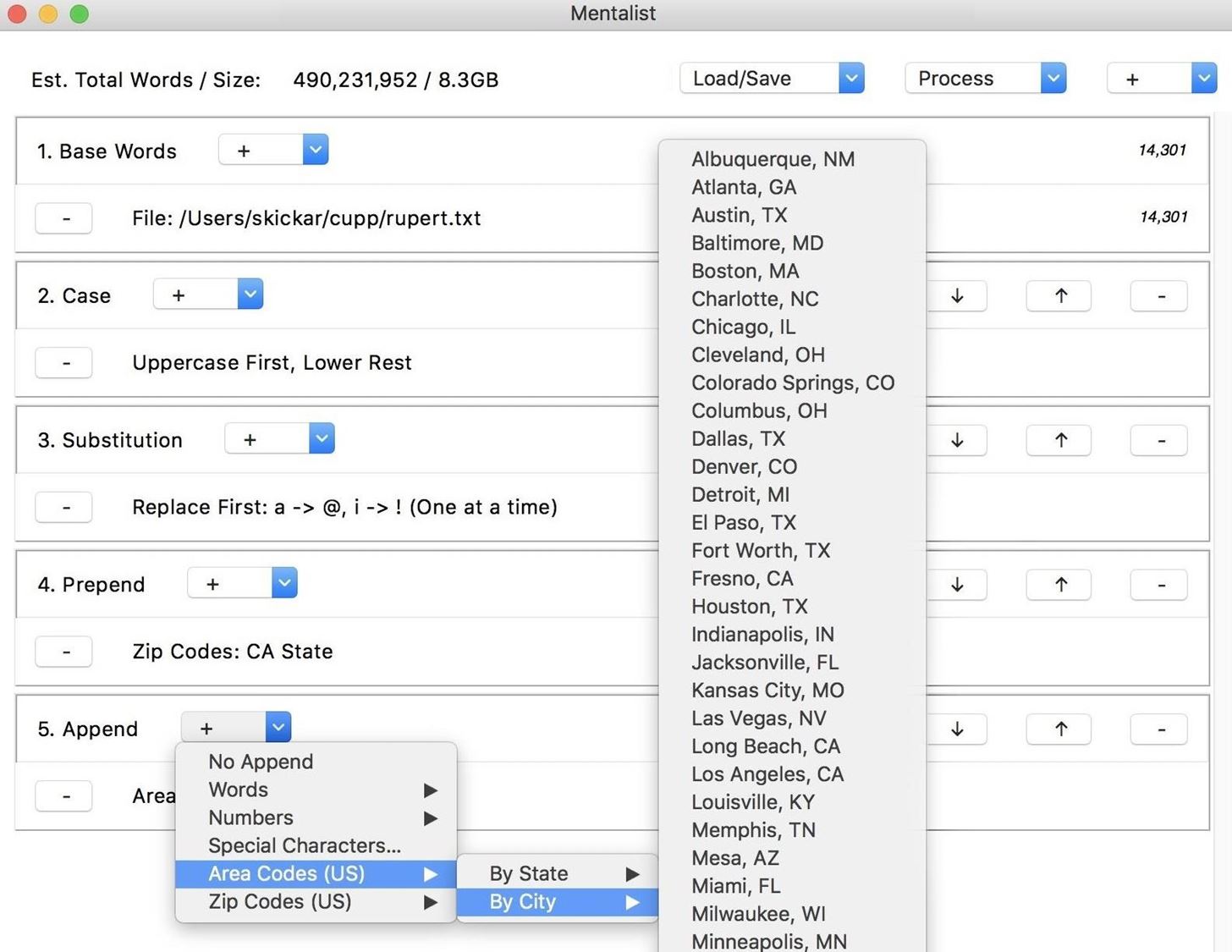
We've produced a wordlist with a lot of outputs! This file would be 8.3 GB of password guesses to save. While this may be fine for some scenarios, we can also compress this with the option to save these options instead as a set of rules to dynamically generate the same list with tools like Hashcat or John the Ripper. To save your wordlist as either a wordlist file or as a set of rules, click the "Process" icon in the top-right corner, and select if you'd like to output the wordlist or rules.
Once you save your final list, you've created a large, customized set of password guesses tailored to the individual user. This wordlist should be much more effective at brute-forcing a target you know more information about and can benefit even more if you have examples of the password policy for the account you're trying to hack or a previously breached password.
Defending Against Tailored Brute-Force Attacks
These attacks target users who attempt to create stronger passwords using details around them that can be easily memorized. By using details like names of pets or family, significant dates, or another password "seeds" that can be researched, a word mangler can create many different variations using the same seed, increasing the likelihood of brute-forcing the password.
To defend against this, users should never pick a password derived from easily researched details, especially if adding a number or modifying the case is the only thing modifying it. Instead, pick an acronym for a long phrase you can remember, or use a password manager to generate a completely random and secure password. By using a password manager, you can sidestep needing to always remember your password in the first place.
Creating a custom password list of several million potential guesses based on details about the target is easy and requires only a small amount of research. I hope this guide has given you a window into the science of password cracking, and encourages you to explore how much further you can go with increasing the performance of brute-force attacks.
Subscribe to my newsletter
Read articles from LoneD3VIL directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

LoneD3VIL
LoneD3VIL
nobody cares.