Azure APIM authorizations- configure Azure Active Directory as identity provider and fetch token dynamically in APIM policy
 Suraj Somani
Suraj Somani
Recently, Microsoft made API Management Authorizations feature generally available. This feature provides the capability to configure OAuth 2.0 authorization with various identity providers and fetch access token in your APIM policy without writing any explicit code. This feature allows us to delegate the authentication step to API management service greatly simplifying the process of authenticating and authorizing users across one or more backend or SaaS services.
Key Advantages-
Using authorizations in API Management, enterprises can easily connect to SaaS providers or backend services that are using OAuth 2.0. Below are some benefits of using Authorizations:
Developers can automatically acquire token from any OAuth provider which reduces the burden of managing authentication and authorization.
Reduces development cost associated with implementing and maintaining connections with one or more SaaS services.
We can design APIM to validate developer access at APIM level and then stuff the request with valid token for the required backend service. In this way, developer has simple authentication process which does not change based on backend SaaS provider.
Durable Functions gets a step closer to Logic Apps with SaaS connectivity.
With Authorizations every API in API Management can act as a Logic Apps custom connector.
Azure APIM authorizations demo- Configure new API to get Azure AD group for specific user
For this blog, we will use Azure active directory as the identity provider and graph API to get user groups as sample API which will use token provided by APIM Authorizations.
Pre-requisite-
Register one application in Azure AD with permission – Application/Directory.Read.All.
Get the client Id and client secret for the same.
API management service should be available.
Lets get started-
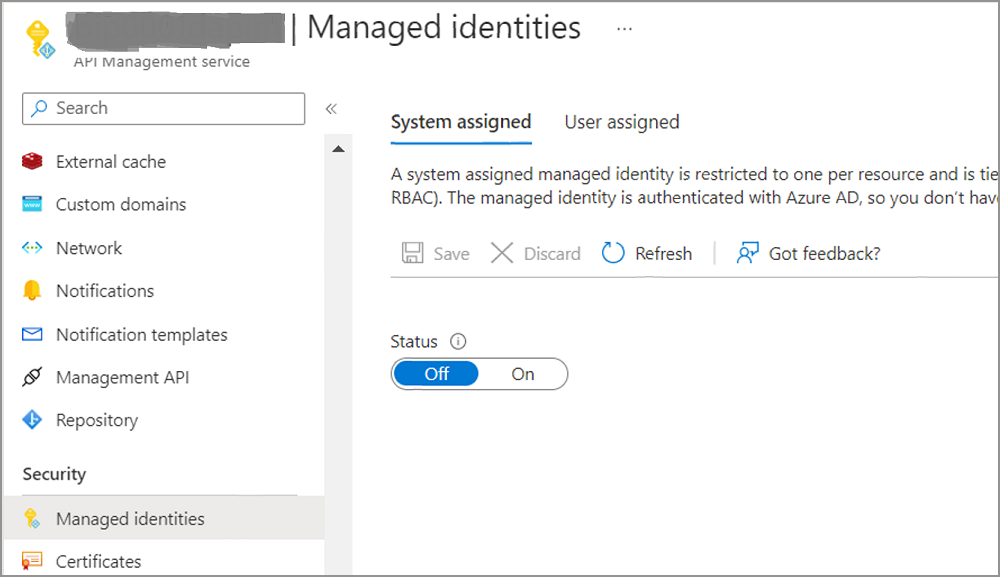
If APIM does not have managed identity enabled, then enable it. Go to APIM service > Managed identities. Under the system assigned tab, change the status to On.
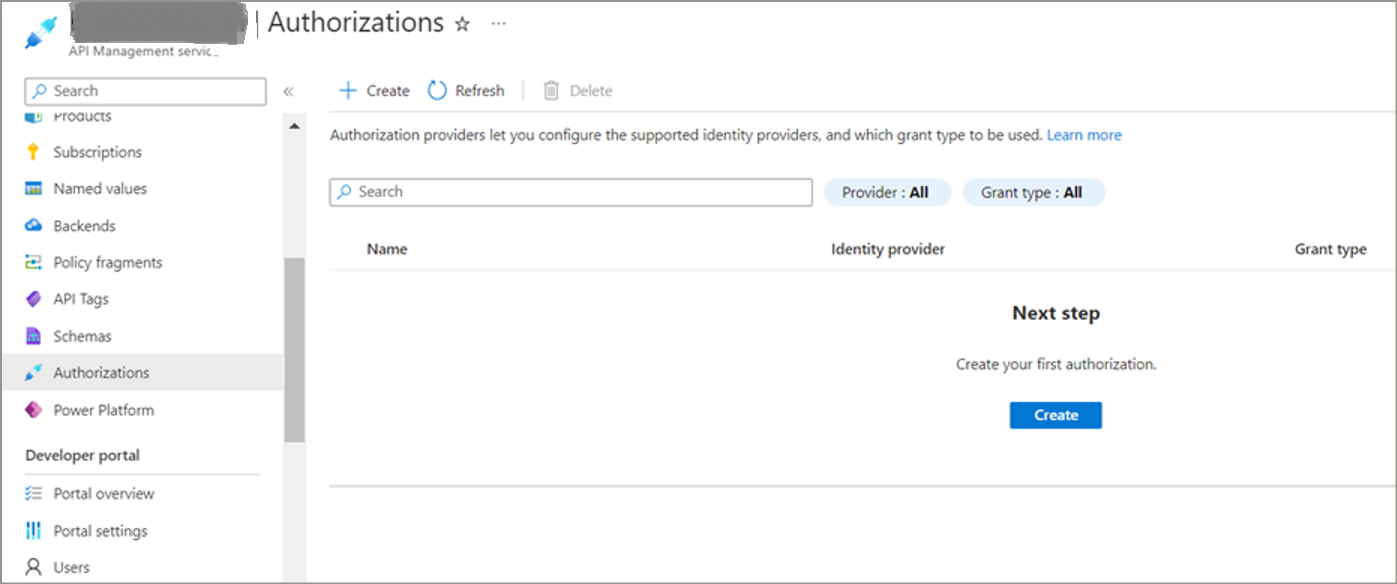
Under APIM, go to Authorizations tab. Click on Create button.
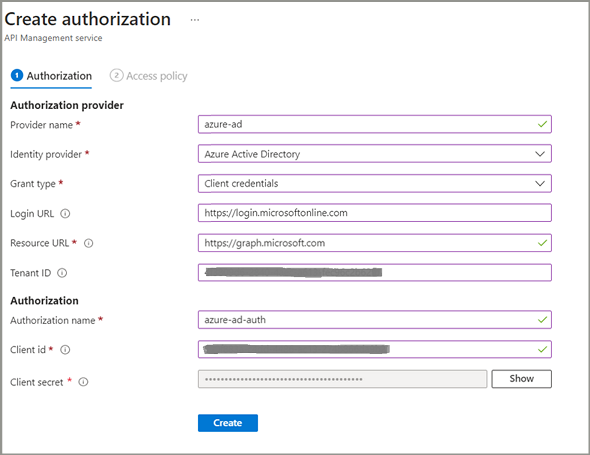
Create new authorization with below details. As we are going to call Microsoft graph API, we need to obtain bearer token from Azure AD using this authorization.
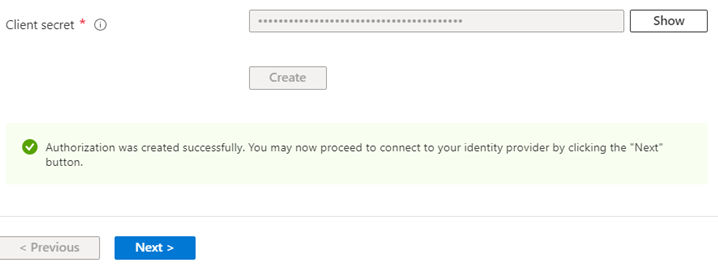
Once you click on Create, you will see below message. Click on Next.
We need to provide our APIM service access on this newly created Authorization. Click on Managed Identity, then click on + Add members. It will open a pop-up like below. Search for APIM service and click on Select.
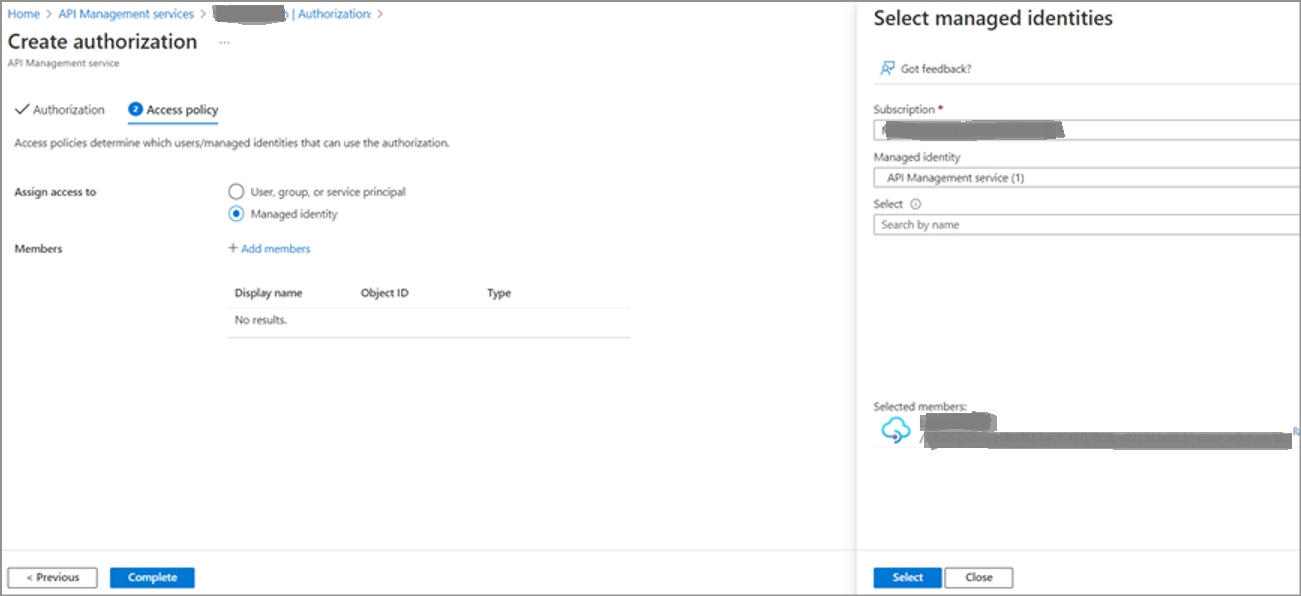
Click on Complete.
Now, go to APIM> API window. Click on create new API. Create a new API as per the below screenshot.
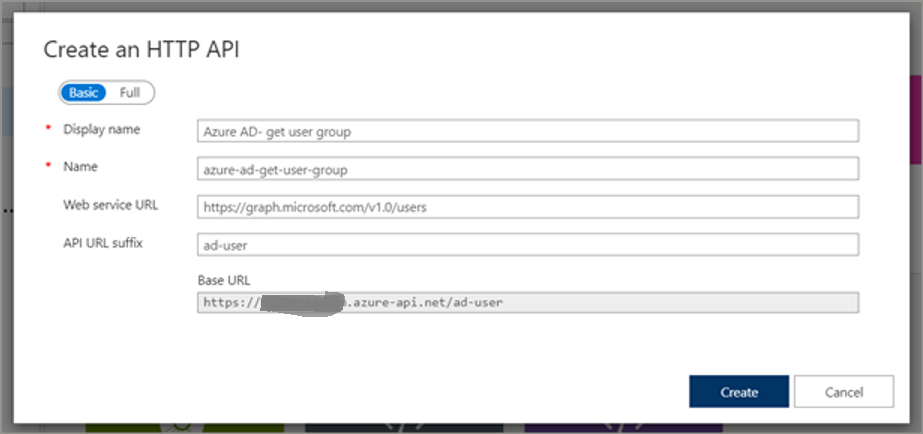
Once API is created, go to the newly create API and click on Add Operation.
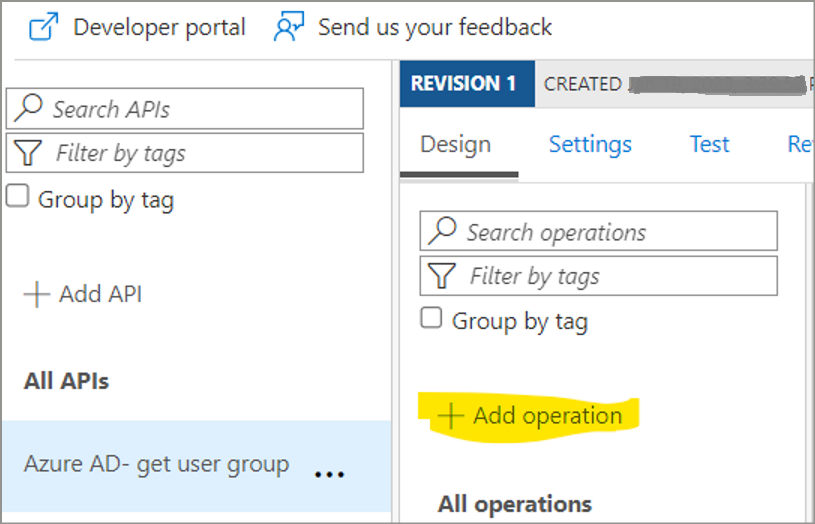
Add Get operation as per the below details.
Note- we have added one template parameter as {memberid}.
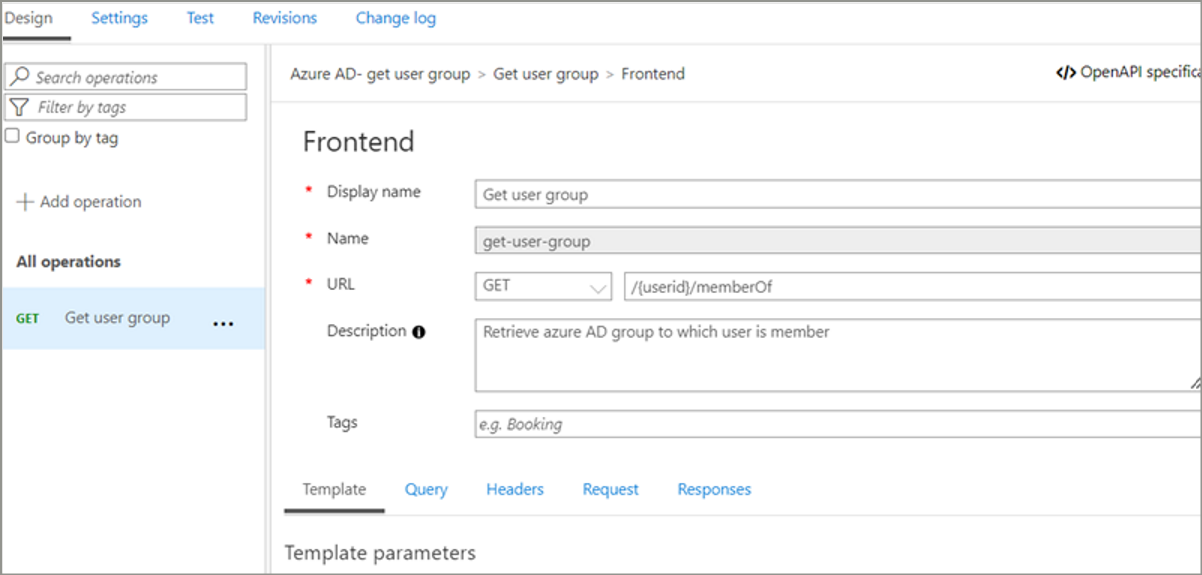
Now go to Inbound processing and click on </>.
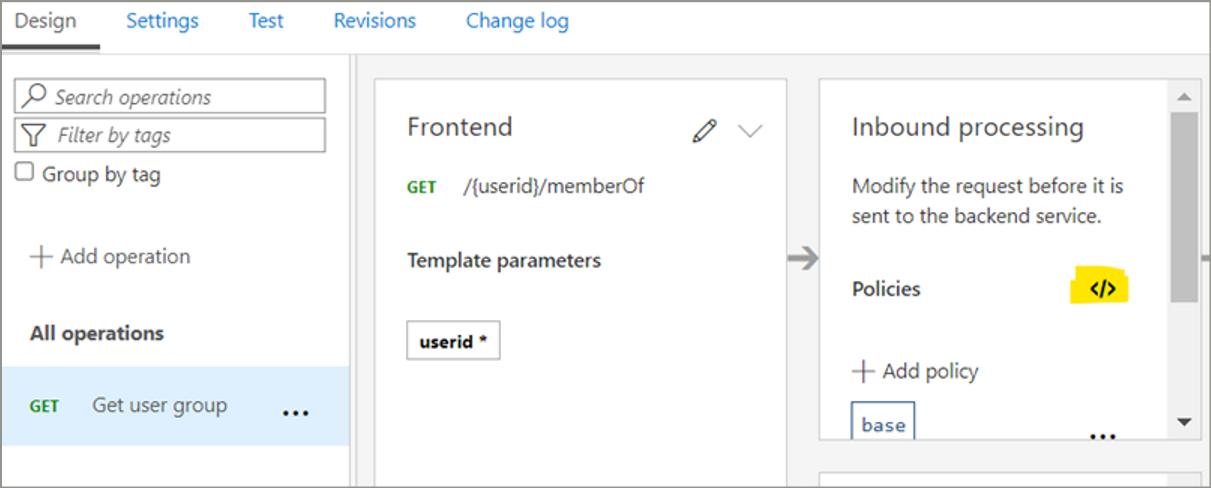
It will open one code canvas. Copy and paste the below-mentioned code in it.
This code will retrieve the bearer token created by the Authorizations configuration and add it to the request header.
Note that provider name and authorizations name configured earlier are used in the below policy.
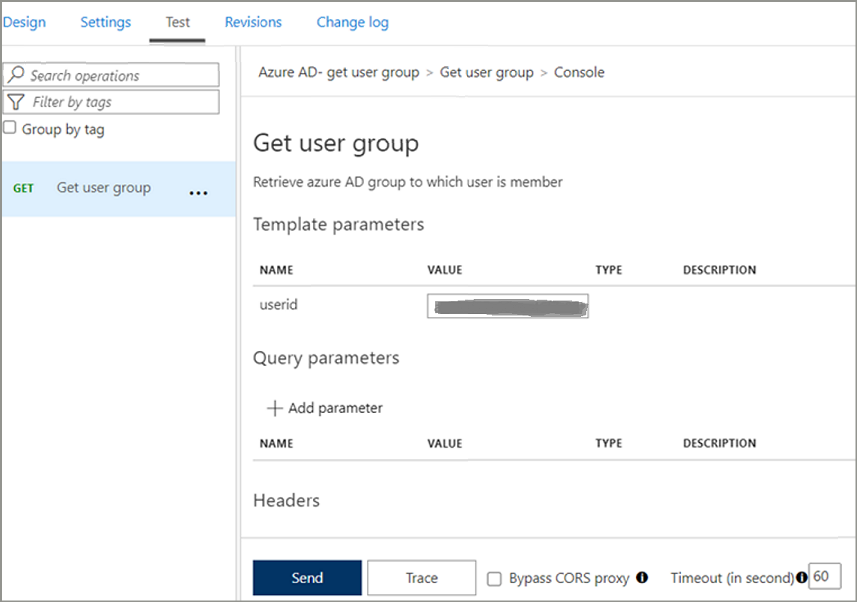
<policies> <inbound> <base /> <get-authorization-context provider-id="azure-ad" authorization-id="azure-ad-auth" context-variable-name="auth-context" identity-type="managed" ignore-error="false" /> <set-header name="Authorization" exists-action="override"> <value>@("Bearer " + ((Authorization)context.Variables.GetValueOrDefault("auth-context"))?.AccessToken)</value> </set-header> </inbound> <backend> <base /> </backend> <outbound> <base /> </outbound> <on-error> <base /> </on-error> </policies>Now, got to the Test window. Provide a valid email id of AD user as userid parameter and hit Send button.
We will get 200 Ok response with all the group details as follows.
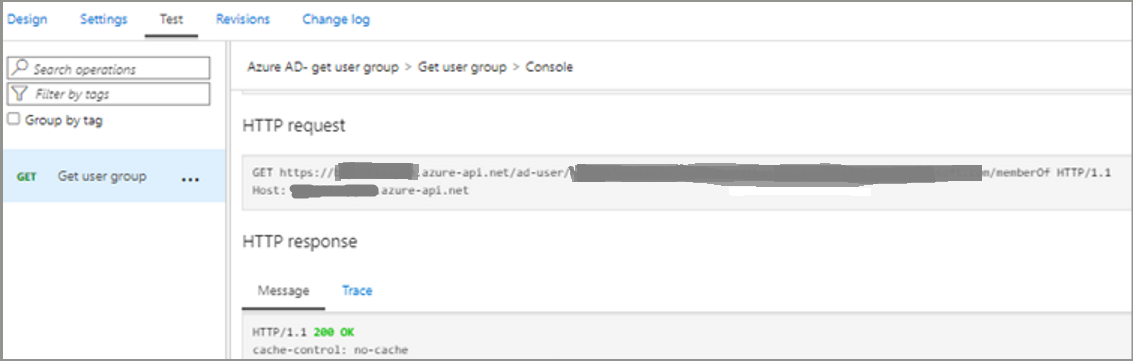
Conclusion- In this blog, we used APIM authorizations to retrieve an access token from Azure AD and use it to authenticate graph API call successfully.
Thanks for reading.
Keep learning!
Subscribe to my newsletter
Read articles from Suraj Somani directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Suraj Somani
Suraj Somani
I am 10+ years experienced IT professional having expertise in various Azure technologies. I am certified Azure Developer & Azure Data Engineer, having vast experience in building cloud solutions.