Maximizing Security Insights with Nmap
 Umair Maratab
Umair MaratabTable of contents

Nmap, short for network scanner is a network scanning and exploration tool which is used by ethical hackers to analyze the network. It provides a wide range of scanning techniques, including port scanning, version detection, OS fingerprinting, and more.
Installation
sudo apt install nmap
Note:
First of all, make sure that it's your network on which you are running Nmap because using it on someone else's network you are not permitted to is against the law.
Usage
nmap [scan type] [options] [target(s)]
Some commonly used Nmap scan types include:
TCP Connect Scan (-sT): This is the default scan type in Nmap. It attempts to connect to each target port to determine if it is open, closed, or filtered.
SYN Stealth Scan (-sS): Also known as a half-open scan, it sends SYN packets to the target ports and analyzes the responses to determine their status.
UDP Scan (-sU): This scan type is used to identify open UDP ports and associated services on a target system.
Comprehensive Scan (-sC): This scan type combines multiple scan techniques and scripts to provide a thorough analysis of target hosts.
Let's check our wifi device (router) ports using nmap.
For that, we need IP address of our router which you can find by going to connected wifi properties via GUI or you can run this command:
Windows
ipconfig
Linux
Open the terminal and execute the following command:
netstat -nr | grep default
If you got the error netstat not found you can install net-tools via:
sudo apt install net-tools
After the installation, you can output the routing table via the following command:
netstat -nr
Output:

You can see the router's IP 192.168.100.1, yours may be different.
Now let's check this device details using nmap.
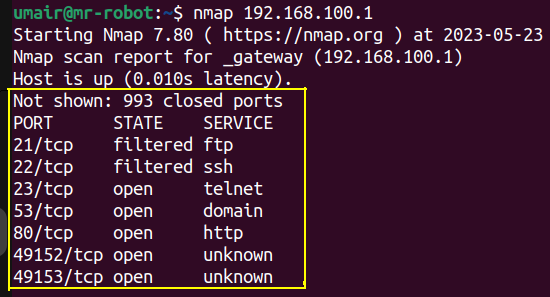
You can see that 23, 53, 80, 49152, and 49153 are open and other are closed.
To learn more about nmap you can do nmap -h on your terminal or you can also check the official documentation https://nmap.org/docs.html here.
UseCases
Network Discovery:
nmap -sn 192.168.1.0/24This command performs a ping scan (
-sn) on a range of IP addresses (192.168.1.0/24) to discover hosts that are online on the local network.
Port Scanning:
nmap -p 1-1000 target_ipThis command scans a target system
(target_ip)for open ports in the range of 1 to 1000.
Service Version Detection:
nmap -sV target_ipThis command detects the version of services running on open ports of a target system
(target_ip), providing information about the software versions and potential vulnerabilities.
OS Fingerprinting:
nmap -O target_ipThis command attempts to determine the operating system of a target system (target_ip) based on various characteristics, such as TCP/IP stack behavior and responses.
Firewall and Security Assessment:
nmap -sS -p 1-1000 target_ipThis command performs a TCP SYN stealth scan (-sS) on a target system (target_ip) to check for open ports. It can help identify potential security vulnerabilities and assess the effectiveness of firewalls.
Please like and comment if you want to add something.
Share you reviews too.
Subscribe to my newsletter
Read articles from Umair Maratab directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Umair Maratab
Umair Maratab
As a computer science enthusiast, I enjoy writing about a wide range of topics, from the latest programming languages to the impact of technology on society.